23.01.b.20230106.0600 IGMP proxy stops TV stream
-
-
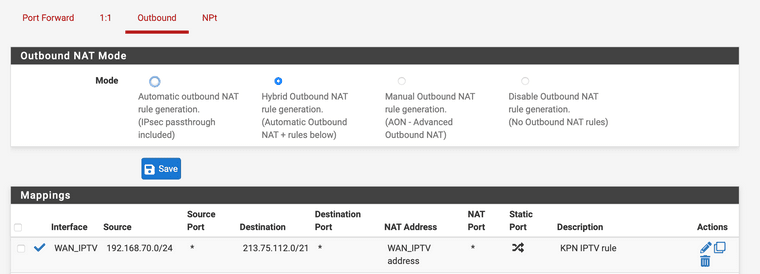
Is the 213.76.112.0/21 too limited?
-
@haraldinho firewall and nat are two separate things.
Can you post your FW rules for IPTV WAN and IPTV LAN?
Via IGMP is the box requesting streams, the streams could be source from multiple subnets. Therefore its way to complex to filter on the sources, software updates comes from 10.a.b.c. and streams from other sources.
Regarding security, it's not the internet. It's a private IPTV vlan within your ISP. That reduces the risk for an attack with a million percentage. But yes hack could occur always, every minute your pfSense instance is attacked on the WAN internet interface.
-
@haraldinho My logs are clean now, no IPTV WAN and VLAN anymore. Pausing of live TV and recorded programma is working. But not at home (holidays...) so no recent experience to share.
The "cat sitter" is mostly streaming YT :). -
-
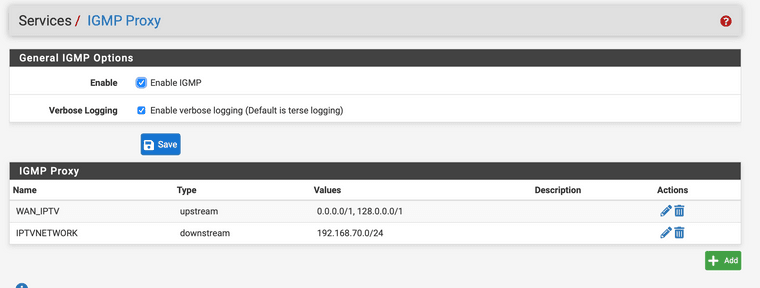
@haraldinho Same as my settings. Are your settings at NAT and IGMP also like mine (I posted them a few days ago).
-
-
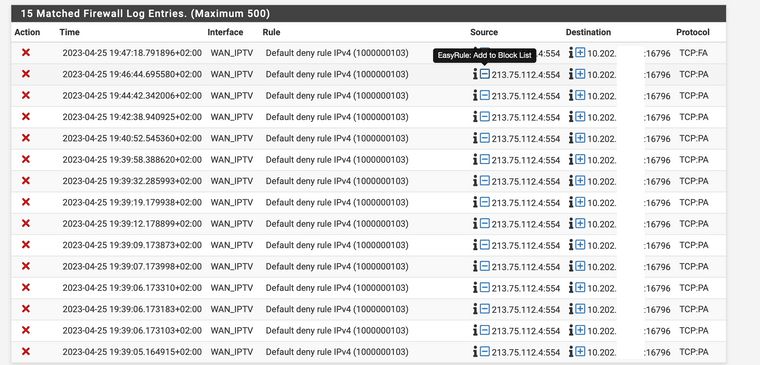
I'm not seeing a mistake in the share configuration parts, don't know where you hitting the default deny log rule. I'm sorry
In generic the fixed the issue in the GUI where we where not able to add 0.0.0.0/0 that's fixed for now.
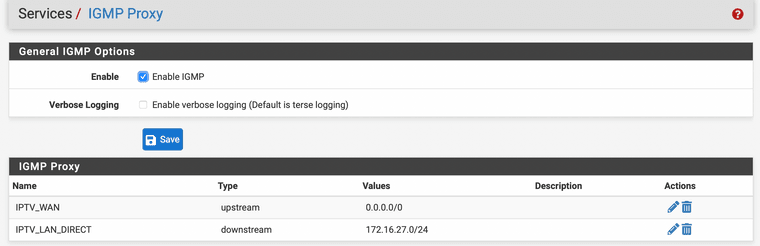
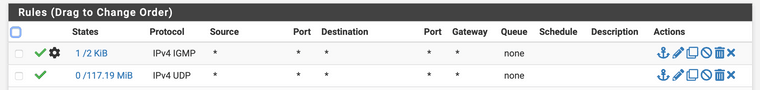
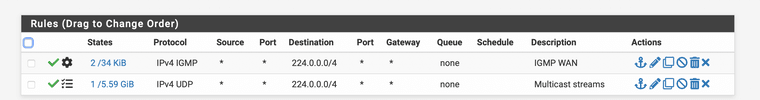
I have added some more security to the ruleset, there is no traffic allowed to the other LAN components when "the hacker" has access to the STB.
WAN
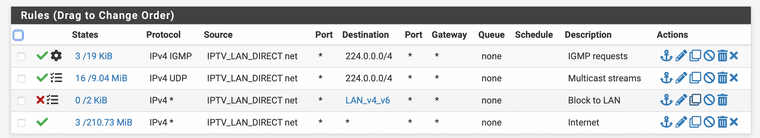
LAN
-
@thebear @haraldinho
I read about solving the GUI issue as well (0.0.0.0/0 is possible now).@haraldinho Perhaps clearing the stating table via the "x" in the firewall rules on IPTV_WAN and IPTV_VLAN solves your issue? Or rebooting the Netgate...
@thebear thanks for the extra security; that's partly going back to what I had. What extra settings do you have in the firewall rules flagged with the 3 thicks in the box; the second WAN rule and rules 2 and 3 at your LAN rules?
-
@michiel said in 23.01.b.20230106.0600 IGMP proxy stops TV stream:
@thebear @haraldinho
I read about solving the GUI issue as well (0.0.0.0/0 is possible now).Way more cleaner to read.
@haraldinho Perhaps clearing the stating table via the "x" in the firewall rules op IPTV_WAN and IPTV_VLAN solves your issue? Or rebooting the Netgate...
Good point!
@thebear thanks for the extra security; that's partly going back to what I had. What extra settings do you have in the firewall rules flagged with the 3 thicks in the box; the second WAN rule and rules 2 and 4 at your LAN rules?
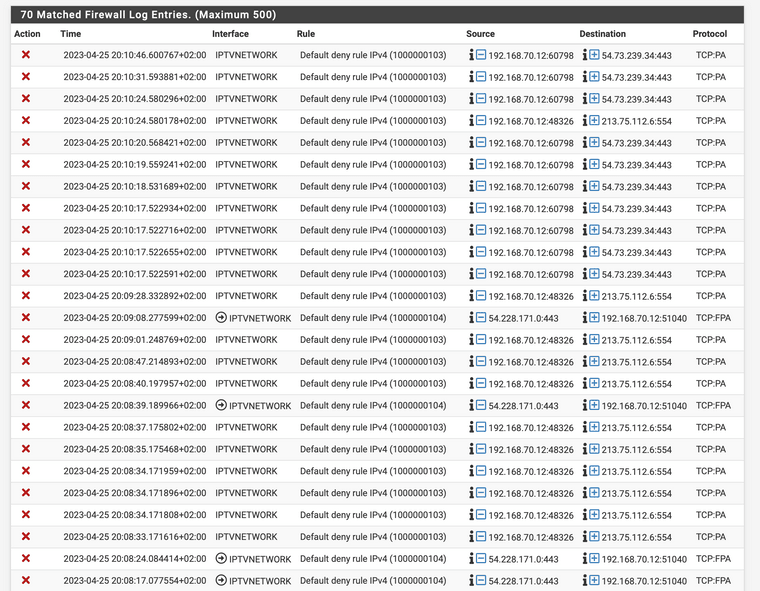
Only enabled logging to see if I can narrow down the rules further more. But don’t want to spend more time at it. The chance of being attacked over vlan4 is almost none by allowing only UDP multicast. With the LAN rule blocking to the other LAN segments, if they where able to take controle over the STB, makes the attacker only look on that vlan. My STB is the only device in that VLAN.
-
@thebear I understand. And what is defined in LAN_v4_v6? My idea was to allow DNS (53) and then block LAN-net…
-
@michiel said in 23.01.b.20230106.0600 IGMP proxy stops TV stream:
@thebear I understand. And what is defined in LAN_v4_v6? My idea was to allow DNS (53) and then block LAN-net…
In that alias are all my other lan subnets v4 and v6.
The STB communicates with the KPN NTP and DNS servers and that’s handled via the last rule. My STB is not using any pfsense service like NTP or DNS. The DHCP sever for this VLAN is handing out the KPN dns servers :)
-
@thebear @michiel I think I figured it out. For some reason asymetric routing seems to happen. So some packets sent by the box through route A return to the box through route B. No clue why. But after reading about this issue in this article on the Netgate website I enabled "Bypass firewall rules for traffic on the same interface". For now, it seems that the logs are now clean.
-
@haraldinho do you have multiple routers in your network?
-
@thebear Nope, only multiple VLANs. The comment with this option is "This option only applies if one or more static routes have been defined. If it is enabled, traffic that enters and leaves through the same interface will not be checked by the firewall. This may be desirable in some situations where multiple subnets are connected to the same interface."
-
@haraldinho do you be sure you did not disable the whole security layer?
Is it a router with one or two ports?
This option only applies if one or more static routes have been defined. Is that your case?
-
This post is deleted! -
@thebear It's a Netgate 6100 with 8 ports. I myself did not define any static routes. I was thinking that might come from KPN DHCP. In all honesty I do not oversee the exact consequences of disabling this option, however from the Netgate pfSense docs I understood that sometimes this option needs to be checked when asymmetric routing is happening... The way they describe it, it came across as quite benign.
-
@thebear As soon as I block "Lan net" in the firewall rules of IPTV VLAN, pausing recorded programs stops working. I defined DNS servers in the IPTV VLAN. Any idea what goes wrong?
You block your other LAN subnets; does that include your default LAN range (in my case: 192.168.1.0/24)?
-
@thebear said in 23.01.b.20230106.0600 IGMP proxy stops TV stream:

I have added some more security to the ruleset, there is no traffic allowed to the other LAN components when "the hacker" has access to the STB.
WAN

LAN

@michiel said in 23.01.b.20230106.0600 IGMP proxy stops TV stream:
@thebear As soon as I block "Lan net" in the firewall rules of IPTV VLAN, pausing recorded programs stops working. I defined DNS servers in the IPTV VLAN. Any idea what goes wrong?
You block your other LAN subnets; does that include your default LAN range (in my case: 192.168.1.0/24)?
Yes it include all RFC1918 address. Did you pay attention to the order, the top down order is relevant. Attached my earlier post as reference.