unable to access ips on vlan after changing Gateway/dns
-
@jarhead said in unable to access ips on vlan after changing Gateway/dns:
Viragomann meant to say a L3 switch, just a typo.
Yes, thx. I correct it above for clarity.
-
@viragomann
@Jarhead
ah ok ill look up this carp.. ill look that up.. and is that what they call high availabilty i heard before.. is that the same?so thats why i was able to access my home assistant and iot devices.. everything is on the LAN so it can communicate.. i just broke my network into segements to isolate things as i didnt have vlan cabablilties.. i did it on the same network... but thats why i cant access other networks you need the pfsense to to from 192.168.0.1 to 192.168.10.1 and vise versa but the subnets they can communicate with each other on the same network.. but not to another..
and do you guys know if the 10gtek network cards anygood? and is there a way to monitor if a pfsense crashes as when i restart Pfsense it doesnt say it crashes.. but i dont have a monitor hooked up to the computer so that doesnt help things
and i cleaned up my lan rules a bit took away some of the grayed out as they were tests... and did i do the camera vlan rules right or mistakes there... and is it possible to make it so if someone unhooked the network cable at a camera and plugged into it.. they cant have access to cameras.. i know odds are never going to happen.. i just curious if thats possible.. like only the cameras id would be allowed and nothing else.. like a a list of there id numbers... i know never going to happen but always learning and figure asking cant hurt too..
-
@comet424 said in unable to access ips on vlan after changing Gateway/dns:
and is it possible to make it so if someone unhooked the network cable at a camera and plugged into it.. they cant have access to cameras.
There are ways to mitigate such action.. You're asking if someone just unplugged a device on a switch, and then say plugged their laptop into the switch would they have access to everything on that switch/vlan via the network right?
With the appropriate smart switch or fully managed switch there are a few things that could be done. Port security is a feature that prevents changing the device on a port, the mac of the device is set on the port, or the mac is learned from the first device plugged in - so that if the mac of the device changes, it wouldn't work.. Ie you unplugged a camera and plugged in a laptop.
You could also setup private vlans if your devices on this network don't really need to talk to each other, say cameras. Then even if some other device was plugged in - it wouldn't be able to talk to any other devices on the this network anyway.
You could setup 802.1x where any device on the network has to auth before its allowed to talk on the network. This would be NAC, and https://www.packetfence.org/ would be a good place to start if that is something you wanted to setup on your network. But the proper switch(es) would be required.
Pfsense wouldn't play a big part in such features. You could leverage say freeradius on pfsense for authing for 802.1x. With a dumb switching environment really the only thing you could do to try and mitigate someone just plugging in a device would be with dhcp limits. Ie don't hand out dhcp to unknown mac addresses.. This might prevent someone on accident plugging in device you haven't ok'd to be on the network. Static arp could be used to prevent someone from just plugging in a device and setting an IP and talking to pfsense, but this wouldn't stop the device from talking to other devices on the network/vlan unless you had setup say private vlans on your switch(es)..
None of this stuff prob makes much sense in a home setup, unless you're wanting to learn - as with any security measures they all come with costs. Be it with complexity, appropriate equipment, time in setup, user frustration or extra steps to get on the network, etc. Then there is the learning curve to implement such things.
-
@johnpoz
oh ok ya i have my cameras outside using those poe's so i was just pondering if you could protect yourself from anyone just unhooking and plugging into it.. i gonna hide the cable .. but was curious if it can be done... ill read up on it... even if i dont do stuff like that least i always learning
and i bet even when your a network administrator it frustrates you guys too.. probably have a team of people so when you get frustrated someone else can give a hand etci have a question i have these reolink cameras.. i set up the rules but its not working for the time sync... ntp in the reolink camera is 123 port it says using pool.ntp.org
my 2 rules doesnt sync.. says failed.. but my grayed out.. allow rule allows time sync is there somethine i did wrong just wont sync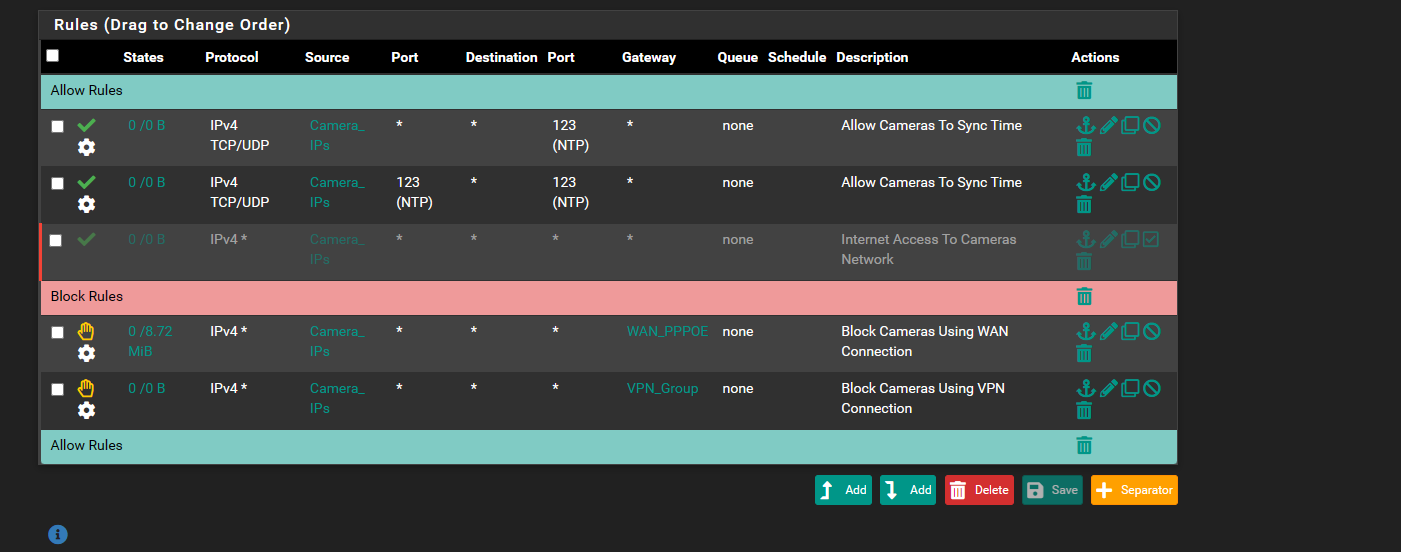
-
@comet424 your ntp rule there on the top. For starters ntp is only ever udp. But those rules show no evaluations, see the 0/0 means nothing has hit that rule. So either your alias does not have the correct Ips of your cameras in them? or they are not using pfsense as their gateway, or they just haven't tried to sync time. If they are trying to use pool.ntp.org - maybe that is not resolving for them. I don't see any rules that allow them to say talk to pfsense for dns. What are the cameras using for dns? I don't see any rules that would allow them to use some external dns either.
your 2nd rule there is pretty pointless setting the source port, since your first rule would allow any source port anyway.
-
@comet424 To add, why not use the NTP server in pfSense and have them sync to it?
-
@jarhead
i have no idea how to set the pfsense one i did try0.pfsense.pool.ntp.org i found in the pfsense services ntp and added it to the reolink camera
it didnt work
here some screen shots
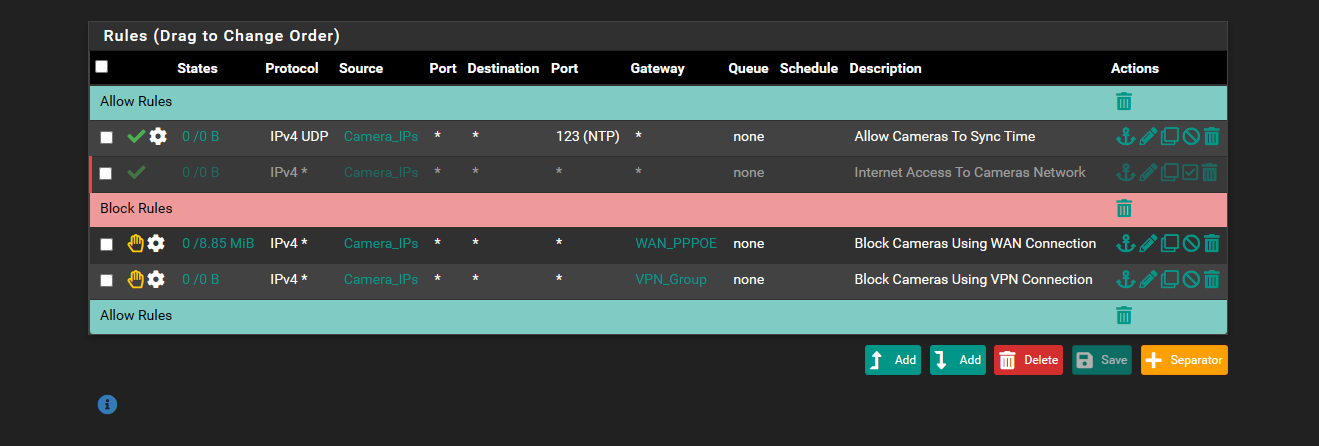
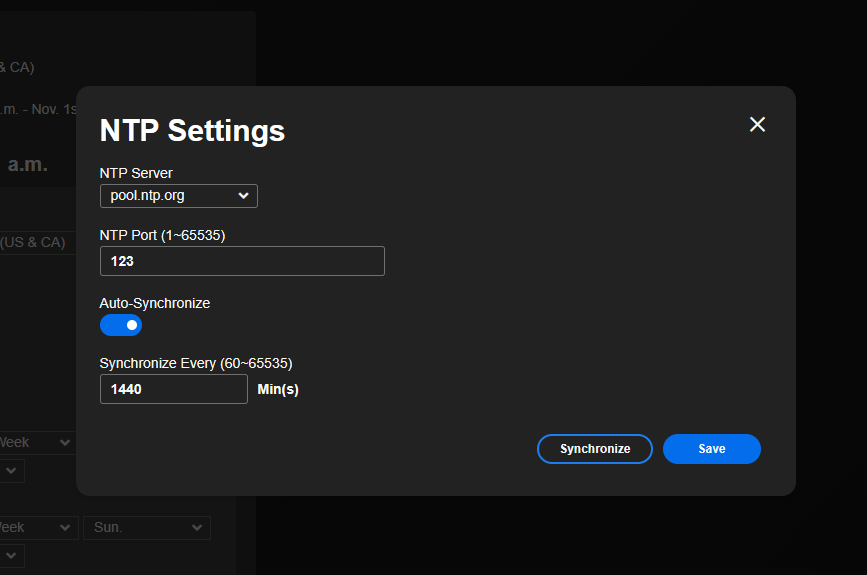
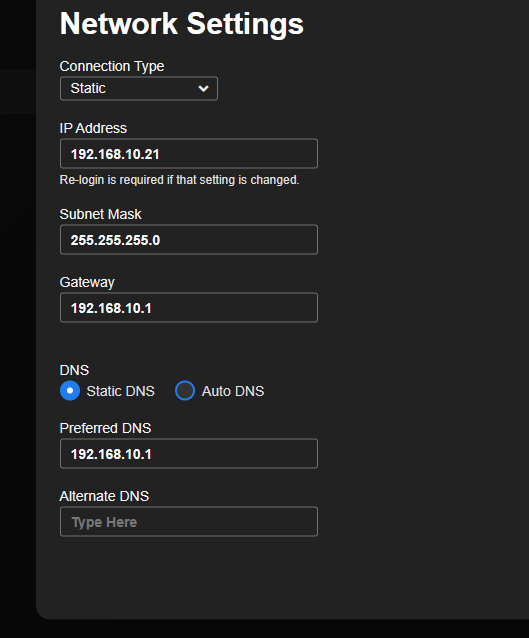
so if ungray the 2nd allow i have.. it will sync when i press the sync button when i re gray it ... and try to sync.. she says failed on syncing does it mean its using a different port then 123 it says its using? as the reject line is increasing
-
@comet424 said in unable to access ips on vlan after changing Gateway/dns:
so if ungray the 2nd allow i have
well that would allow it to resolve pool.ntp.org, your pointing it to pfsense for dns - that 192.168.10.1 address.. But you have no rules to allow dns other than that allow all rule.
If all you want is for them to be able to sync time.. And not the actually use the internet. Might be better to just point them to pfsense IP for ntp. Then they need no dns nor any internet access at all.
But from your screenshot - they don't allow just putting in an IP for ntp server?
-
@johnpoz
ah ok. ya for now only want it to sync time no internet.. it does sync the time if i enable my 2nd line i have that opens up everything... so i figured maybe its really not on port 123?the cameras do have "custom" under ntp server and you can enter a ntp server
do i use 192.168.10.1(camera network) or do i use 192.168.0.1 main address to pfsense?
oh and to get the pool.org id have to add dns port then you were meaning
-
i tried 192.168.0.1 and 192.168.10.1 it says succeded..
are both ok or is 1 the proper way to do it
-
@comet424 Just point it to pfsense IP on the camera vlan, 192.168.10.1 now you don't need any dns, and you could change your ntp rule to only allow to 123 udp on camera vlan address.
Either work because your rule for 123 allows it to go anywhere. But if your looking to block all access to anything other than ntp, only the pfsense IP on that vlan really needs to be allowed.
-
oh ok so get rid of the rejects then? and i can fix that ill point all to 10.1
i have one last question for now with these camears
when i orginaly plugged them in they were all dhcp and host name came up with camera as the host name
i edited each one and set static ips
and i changed each name to like cam1 cam2 cam3 cam4
but it shows up blank now... is there something to run to force pfsense to get the host names.. i know doesnt matter for such a small amount of cameras but would be nice if it show up cam1 cam2 like it did when it was showing up camera as the host nameany special trick? or is a port i need to open like the 123 ntp
-
@comet424 said in unable to access ips on vlan after changing Gateway/dns:
i edited each one and set static ips
You set this were - on the camera or via a dhcp reservation?
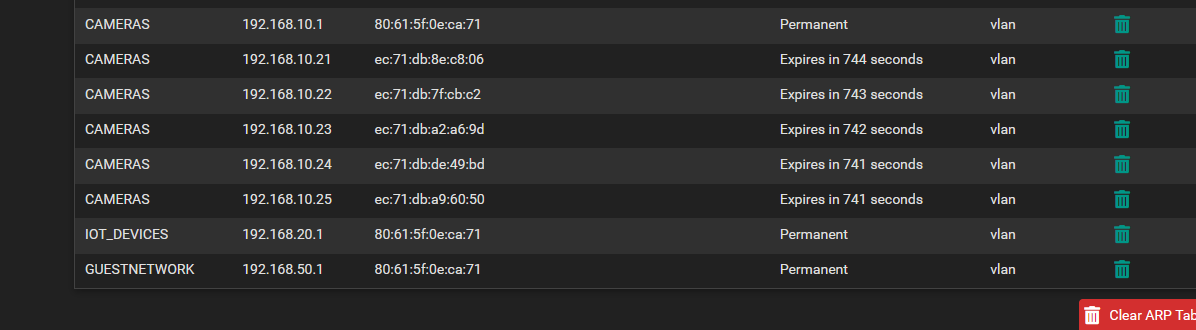
If I look in my arp table stuff I have set for reservations show up with names.
example here are my alexas that all have dhcp reservations to always get the same IP.
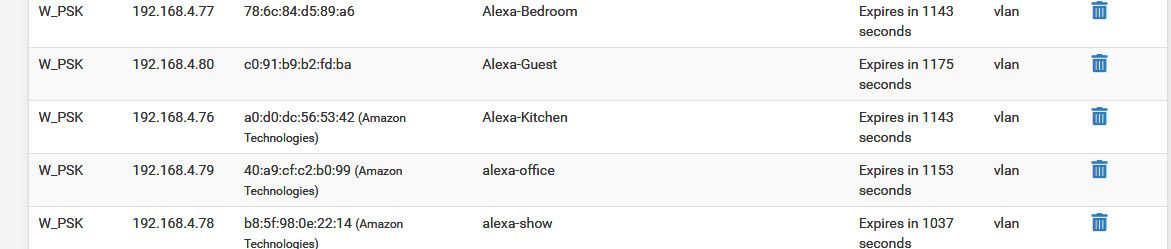
If you want stuff that you setup static on the device to show up with a name, you could always just create a host override in unbound for that specific IP, so that it resolves to the name you want, ie cam1, cam2 etc..
But in the long run dhcp reservations are going to be a better option vs settings specific on the device. dhcp reservations would allow you to easy change the ip in the future without having to touch the device. Or change other stuff you might hand out via dhcp, like gateway or ntp, there are lots of options that might be useful to hand out via dhcp - be it your device takes advantage of them or not is another thing. But if you set dhcp reservations vs on the actual device - in the future if you want to change the whole network IP space its as simple as some adjustments on pfsense without having to touch each device. A simple reboot of the device should all that be required to get say the new IP, gateway, dns, etc. And if they are poe, that can be as simple as turning off poe on your switch for a second, etc.
-
@johnpoz i set the names in the Camera itself.. it has a section called "name" and they were all labeled camera
and the dhcp orginally in the arp table labled them "camera"
but i had changed the names in the cameras to
all from
camerato cam1 cam2 so i figured the hostnames would change from camera to cam1 cam2 cam3
but it didnt especially after i did static ipill look up this dhcp reservation.
-
oh ok so dhcp is better
reason i went static incase pfsense goes down then cameras go down too... but then i learned about CARP
but figured if pfsense is down having static camera ips was better? always learning
and is dhcp reservation same meaning as "dhcp static mapping"
-
@comet424 keep in mind that if your dhcp server (pfsense) goes down... The dhcp client just doesn't magically loose its IP. The device should keep its IP for the length of the lease it has left. So unless you rebooted the device its ip should be good for at min 50% of whatever your lease time is.
So say my lease is 2 days.. At 1 day the device would try to renew, and then lease would be good for 2 days again. So even in a worse case scenario and it was like 1 minute before the 50% renewal mark, your devices IP should be good for 1 day even if your dhcp server is offline.
If your lease is 2 hours, then worse case is 1 hour, if your lease is set for 4 days then worse case is 2 days, etc.
Depending on the device it might even survive a reboot with no dhcp server available and still use its last leased IP, etc.
I have never in all the years using pfsense ever seen an issue where dhcp server went down, and the rest of pfsense was working.. Not saying that couldn't happen - but its a pretty minor thing to worry about ;)
-
@johnpoz
i googled an older article about dhcp reservationsin pfsense you click + button on a dhcp status and it adds it to the dhcp mapping but my dhcp leases dont have a + beside them to add them i normally have to manually just copy mac address... was this + add button removed?
ah and ther reason about pfsense going down.. for around 118 days pfsense was up... but then it started crashing or the network card i dunno.. lost access to pfsense.. reboot no errors..
the on board nic is a realtek and my 4 port card i had in it was a realtek too.. and i remember someone saying realtek not supported by pfsense.. something with the card has an issue i forget... as it was constantly going down.. los of the access to pfsense so i had issues with wifi least i find issues with my TPlink Wifi switchs and plugs they seem to go down as they only dhcp....i not sure how to inscrease dhcp lease longer i think mine set to 1100 seconds
so i replaced the realtek card with a 10gtek card 2 port hoping that s better.. as intel cards on amazon were like 300 bucks for some reason here in canada
-
@comet424 said in unable to access ips on vlan after changing Gateway/dns:
but my dhcp leases dont have a + beside
huh?
What version of pfsense are you using, where are you looking.
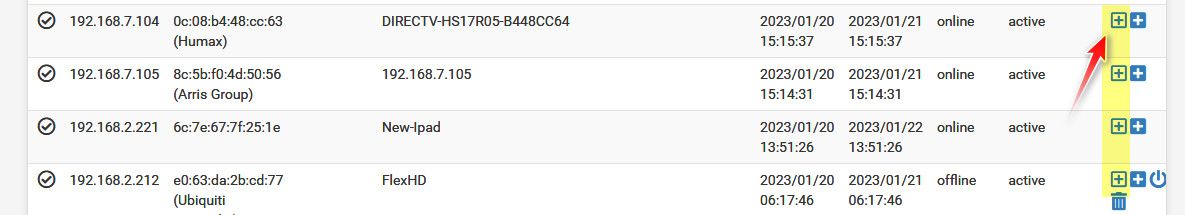
That button would be in the dhcp leases table - only stuff that actually got a lease would be seen there, etc.
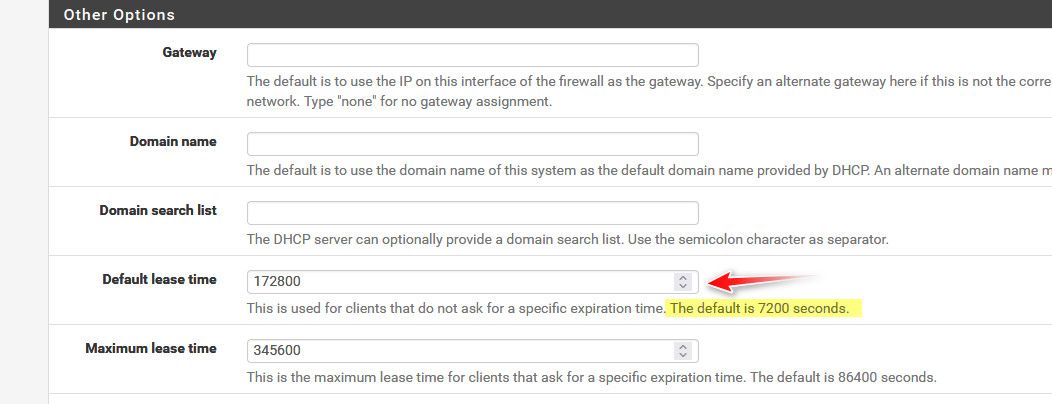
i think mine set to 1100 seconds
Where did you come up with that number, that is not default - which I believe is 2 hours.. 1100 seconds is like what 18 minutes - why would you have set a lease to such a ridiculously low number?
And you have 300 clients on this network - so you have devices renewing their leases every 9 minutes... That is going to be a shit ton of dhcp traffic for what reason??
-
ive never changed dhcp... so i looked at the arp table.. i guess it is 1200 seconds for static ips and dhcp leases... i never set the 1200 seconds thats the default from when i just set it up i dont even know how you change lease time
all i know is all dhcp and static ips says "Expires in 1195 seconds" is the hightest one i seen so i guessing it defaults at 1200seconds
as for the version i have im running 2.6.0-release amd64 freebsd 12.3-stable
and under dchp leases i have same as you minus the two plus's
so heres my moms dhcp lease under dhcp leases no ++and how do i inscrease the dhcp lease time for lans and vlans then from 1200 seconds default to whatever?
ill check the defaul least time from ur post i just seen ur reply as i replied
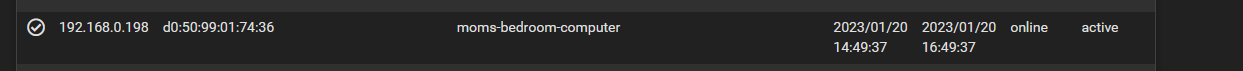
-
@comet424 arp is different than dhcp lease time, they don't have anything to do with each other.. I believe the arp cache timeout in pfsense is like 20 minutes.. 1200 seconds.
edit:
yeah that doesn't look right - did you try with a different browser, are you using anything in browser that might block those?