I'm sick of neer-do-wells hitting my WAN with TCP:SYN
-
@johnpoz
I find a selection of the feeds in pfBlocker relatively specific for my use case. Sad to hear your find them less useful. -
@patch I didn't say that - those are rules that can be very specific for someone wanting to do what he is doing. What I am saying finding an IP and then blocking the /16 that IP come is going to be problematic at best if you actually want to use the internet.
There are maintained lists already, say for example the shodan scanner
https://wiki.ipfire.org/configuration/firewall/blockshodan
And sure the lists in pfblocker - no reason to try and reinvent the wheel here.
Blocking based on AS vs a arbitrarily random cidr of /16 would be a better option..
-
@johnpoz Indeed:-
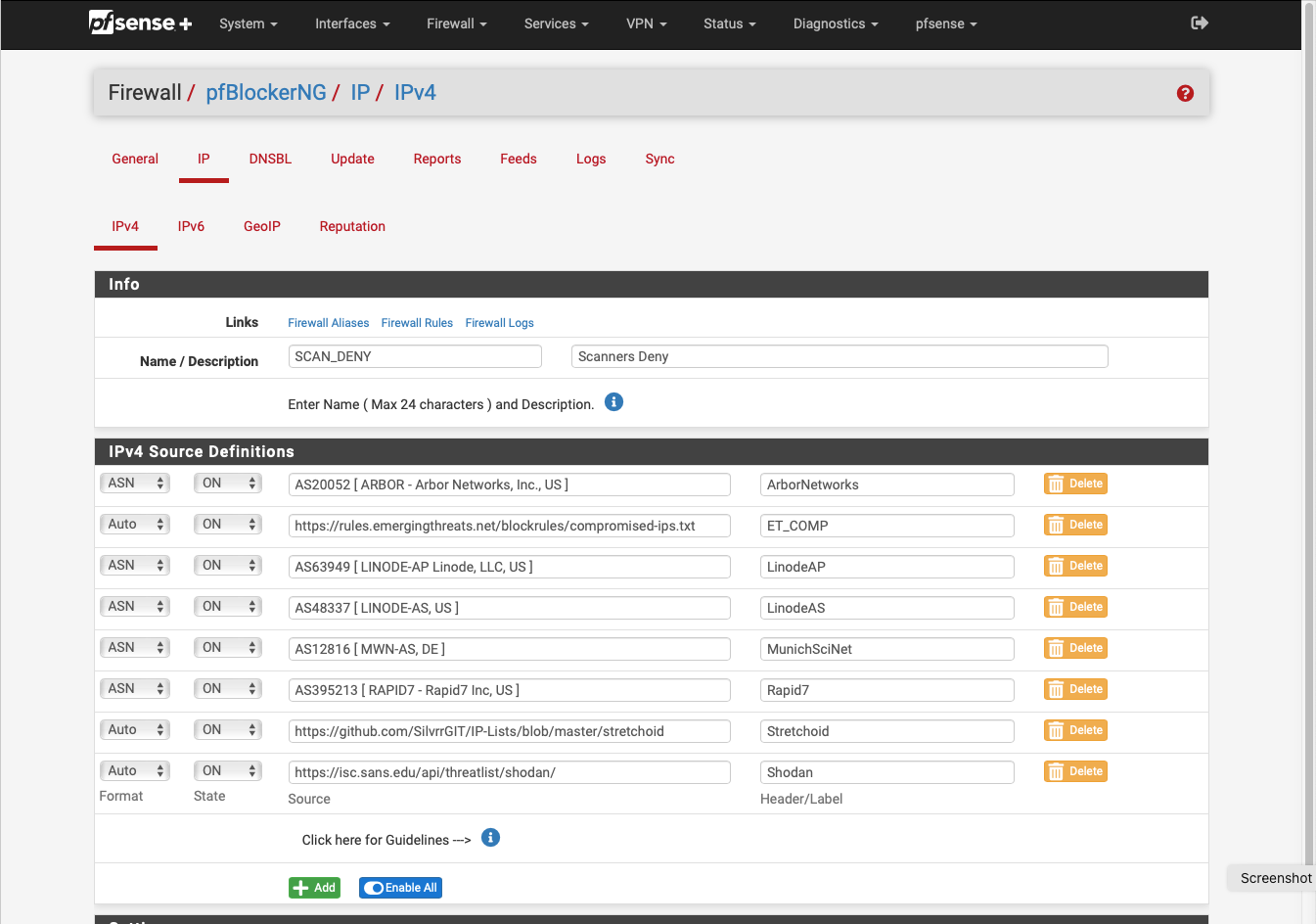
-
@johnpoz OK - I'm convinced. My plan is going to take a lot of work without much payoff.
As you might have guessed by now, I'm pretty much a pfSense NOOB and
I appreciate all of your insights and expertise.It looks like I'll be investing some work in pfBlocker. Can anyone suggest the best (simplest) step-by-step guide to getting a basic pfBlocker setup started?
-
@henderbc Use pfBlocker like my example to create aliases and then use those on the WAN interface.
There is a wizard to do the basic install, you'll also need to sign up for a MaxMind license key if you want to use their GeoIP data.
Install the pfBlockerNG-devel version.
https://www.youtube.com/watch?v=xizAeAqYde4
https://www.youtube.com/watch?v=oNo77CMoxUM
-
@nogbadthebad Here's what running the wizard gave me:
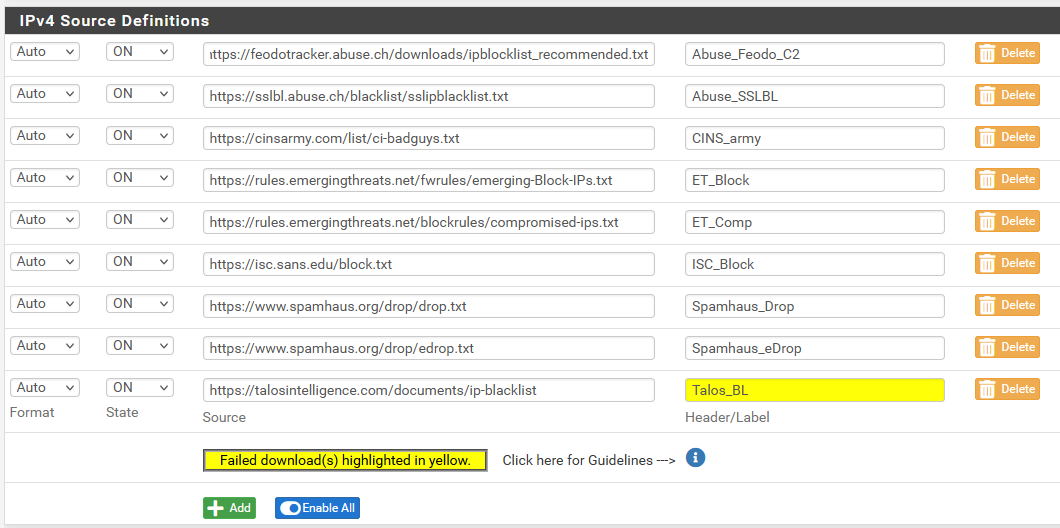
Would you recommend I use your entries instead of these or as well as?
-
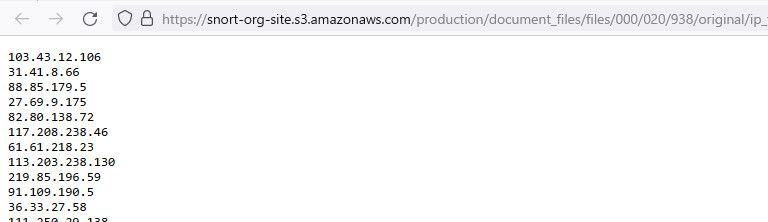
@henderbc I don't seem to have any problem downloading that talos list
https://www.talosintelligence.com/documents/ip-blacklist
Can you open that link in a browser? It redirects to different location, but can get a list of IPs in my browser - does that work for you?
-
@henderbc It's up to you to be honest, I wanted to create my own list rather than the standard one.
I just started looking at what was hitting my WAN interface and built up a list of what was doing a port scan on my WAN.
It started from the shodan list and sort of expanded.
-
@nogbadthebad ^ exactly what I would suggest, what you want to block would be up to you.. But again keep in mind if you have zero ports opens its all pretty pointless other say not logging this traffic to keep your firewall log smaller?
If your phone ringer is off, does it really matter if a spammer calls you - you don't answer the phone anyway because the phone doesn't ring.. But you might not like picking up your phone and see missed calls.
So if you don't want to log these scanners that valid, but if your still going to log them, and you don't have any ports open anyway.. Not sure what the point is? Other than say info on how much traffic is coming from these known scanners. Another big scanner is recyber.net but atleast they have an optout where you can put in your IP and they are suppose to exclude your IP from their scanning.
-
@johnpoz said in I'm sick of neer-do-wells hitting my WAN with TCP:SYN:
If your phone ringer is off, does it really matter if a spammer calls you - you don't answer the phone anyway because the phone doesn't ring.. But you might not like picking up your phone and see missed calls.
My ringer is on as I have an IPSec VPN & SFTP server local
