Port Forward to an OpenVPN client address
-
Hi,
I am having a home setup with a PfSense connected via OpenVPN to another PfSense at the office.
As the home is connected via Starlink, I have not succeeded in setting any kind of DynDNS, I assume it is due to the specifics of PfSense.
On another hand, I have succeeded in setting up an OpenVPN link between my home and office, the office PfSense being server and the home being client.
Office holds lan addresses 192.168.16.0/24 and home holds 192.168.68.0/24.
The OpenVPN works fine without issues.
As my office is fix IP, I want to NAT port 8200 of my office public IP to 192.168.68.3 at home.
I have not succeded in setting this up.
Is there any specific action to take beyond setting up a NAT rule in the office PfSense?
Thanks for your help.
-
@labu73 said in Port Forward to an OpenVPN client address:
As the home is connected via Starlink, I have not succeeded in setting any kind of DynDNS, I assume it is due to the specifics of PfSense.
No. As far as I know, Starlink gives you a CG-NAT IP. It's behind a NAT-router in the providers network. You cannot access this IP from outside.
On another hand, I have succeeded in setting up an OpenVPN link between my home and office, the office PfSense being server and the home being client.
Is this an access server, which can handle multiple client connections or a site-to-site?
Regardless this, you have to assign an interface to the OpenVPN client instance and add a rule to it to allow the incoming traffic from anywhere.
And remove all pass rules from the OpenVPN tab. -
@viragomann, my OpenVpn Setup is just fine as I can reach all the home targets from office and office targets from home.
My home PfSense is taking care of keeping everything alive.
Client side for OpenVPN Client
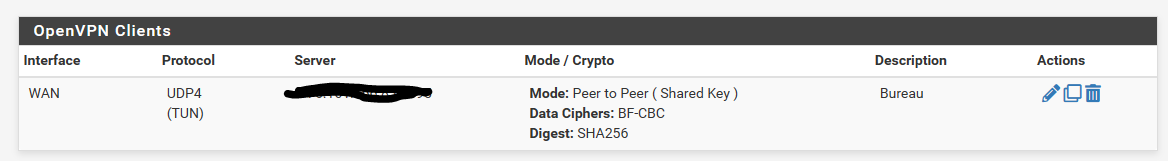
Server side OpenVPN Server

NAT Rule

My supposition is that the Server NAT redirects to OpenVPN Client, but, as the source IP is not from the server local domain, the reply is not passing via the VPN, hence not reaching the external browser.
Could it be so?
-
@labu73
Did you obey, that I suggested above regarding firewall rules? -
@labu73 In order to receive connections forwarded to you from arbitrary addresses you must:
- Assign an interface to the OpenVPN instance at the home site.
- Make sure that the inbound traffic is not matched by rules on the OpenVPN tab, but by rules on the assigned interface tab.
That will get you reply-to functionality at that end.
Peer-to-peer shared key is going to be deprecated soon. You want to take the time to switch that to SSL/TLS with a /30 tunnel network.
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configure-server-mode.html#mode-configuration
-
@derelict That was it, your point 2.
Thanks