LAN Firewall VPN rules leaking
-
@courtalj do you have any floating rules that would allow some traffic?
If not then most likely a per-existing state.. if this .101 box was talking to say 1.2.3.4 on port X, it would continue to use that state until it has been closed, timed out or killed, etc. to talk to 1.2.3.4 on port X
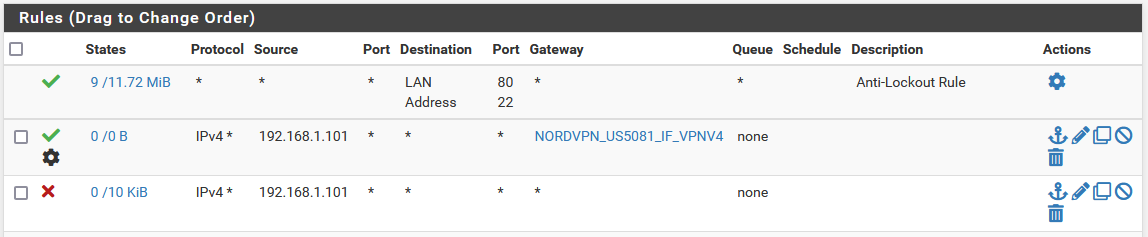
From that posting of your rules - that rule routing traffic out your vpn has never been used - the 0/0 says that rule has never been evaluated. See the 0/0 B
-
@courtalj said in LAN Firewall VPN rules leaking:
but I know for a fact that some non-zero amount of traffic is still leaking out the regular WAN gateway.
Out of the box pfSense is not leak-proof. Also you could mention the "fact" in more detail to speed up things.

-
@johnpoz said in LAN Firewall VPN rules leaking:
From that posting of your rules - that rule routing traffic out your vpn has never been used - the 0/0 says that rule has never been evaluated. See the 0/0 B
Traffic yes, but you can still have evaluations even though that view shows 0/0. They are only visible in the popup...
-
@gblenn said in LAN Firewall VPN rules leaking:
They are only visible in the popup...
What you mean if you mouse over? OK maybe a bad choice of word(s) on my part - I mean the rule has never triggered ;) I from that nothing has gone out the gateway ;)
-
@johnpoz Yes that, the mouse over. But I'm also thinking that perhaps when in trouble shooting mode, you make a lot of changes. Editing the rule resets the counter so, it may very well be working (and it looks correct).
Either way, isn't it so that DNS requests could very well go out via WAN, depending on how the client is set up?! -
@gblenn don't know what he thinks is leaking.. He didn't show any leak,nor did he show any traffic even going out his rule.. For all we know he has a any rule in floating that lets everything out.
-
@johnpoz I agree, more information and detail about what is actually leaking would be prudent. But he sais it "works" when checking "manually from the .101 device". I'm assuming he's looking at something like "whatsmyip" from that device, showing that he's exiting via the VPN.
And 0/0 only shows that the rule has not been used since last changed, not that "a rule" looking exactly the same has never been used.The rules do look ok, including the "killswitch" rule, don't they?
Perhaps I'm completely off here, but all dns requests to the resolver will generate "traffic" on the WAN interface, right? He sais non-zero amount which to me sounds like it's barely noticeable... So perhaps that is what he is seeing then, some traffic coinciding with activity on the .101 device?
-
@gblenn said in LAN Firewall VPN rules leaking:
The rules do look ok, including the "killswitch" rule, don't they?
They do I agree - but we don't really know, with those rules you might make the deduction that he is not even using pfsense to get to the vpn ;) Maybe he is on some phone? and using cell?
Really need more info on what is leaking.. And how his is seeing that it is, and the info on any floating rules, or existing states, etc.
-
You need to set 'Skip rules when gateway is down' in Sys > Adv > Misc.
Otherwise that rule will just pass that traffic without a gateway set when the VPN is down.
Steve
-
Replying to a few things here...
@johnpoz said in LAN Firewall VPN rules leaking:
@gblenn don't know what he thinks is leaking.. He didn't show any leak,nor did he show any traffic even going out his rule.. For all we know he has a any rule in floating that lets everything out.
There was no floating rule at all, and the states/counts were zero because in my investigating before posting, I shut down the .101 device and reset all the firewall states.
@johnpoz said in LAN Firewall VPN rules leaking:
@gblenn said in LAN Firewall VPN rules leaking:
The rules do look ok, including the "killswitch" rule, don't they?
They do I agree - but we don't really know, with those rules you might make the deduction that he is not even using pfsense to get to the vpn ;) Maybe he is on some phone? and using cell?
Really need more info on what is leaking.. And how his is seeing that it is, and the info on any floating rules, or existing states, etc.
I discovered in further investigation that if the VPN goes down, all of the .101 device traffic would go out the normal WAN interface. Verified by (you guessed it) whatismyip.
Which brings me to what may be the missing piece:
@stephenw10 said in LAN Firewall VPN rules leaking:
You need to set 'Skip rules when gateway is down' in Sys > Adv > Misc.
Otherwise that rule will just pass that traffic without a gateway set when the VPN is down.
Steve
I did not have this checked... based on the description and my prior searches, I misunderstood it's function. It seems like this control is non-intuitive at best and at worst is an obscure way to supersede firewall rules that are otherwise clear...
And with more research, I came across the suggestions to specifically NOT rely on the 'Skip rules when gateway is down' control and instead tag all traffic with a match rule at the LAN interface, and then use a floating rule to block all tagged traffic from hitting the WAN interface. That does seem to have the desired effect of not allowing any of the .101 traffic out the WAN if the VPN goes down.
Any recommendations on which method to use?
-
You could do both. Either will work.
-
@bob-dig
@bob-dig said in LAN Firewall VPN rules leaking:
@courtalj said in LAN Firewall VPN rules leaking:
but I know for a fact that some non-zero amount of traffic is still leaking out the regular WAN gateway.
Out of the box pfSense is not leak-proof. Also you could mention the "fact" in more detail to speed up things.

How do you mean? Other than the killswitch setting discussed below, are there other settings to make it more leak-proof?
-
Typically VPN providers will have you remove the outbound NAT rule from the WAN so that it's impossible for traffic from internal clients with private IPs to reach anything that way.
But I wouldn't recommend doing that. There are numerous threads here with users who followed the VPN providers instructions without knowing what they actually do and then ended up unable to connect at all.Steve
-
@courtalj Not really but also check for DNS-leakage.