Traffic through another wan, 2WAN 1LAN 1VLAN
-
@gdsf
You have to policy-route the upstream traffic to WAN2.
This means to have to edit the pass rule on VLAN10, which allows upstream traffic and state the WAN2 gateway in the advanced options.However, to apply this rule to upstream traffic only as said, create an alias for private networks if you don't have any already, call it say RFC1918 and add all RFC 1918 networks to it.
Then in the rule above at destination check "invert match" and state this alias. So this rule is only applied to traffic which is not destined to private IPs.Consider to add an additional rule to allow access to internal destinations like DNS, since the rule above now only cover upstream traffic.
-
@viragomann
thanks for helping me friend Will you not need to do some kind of NAT too?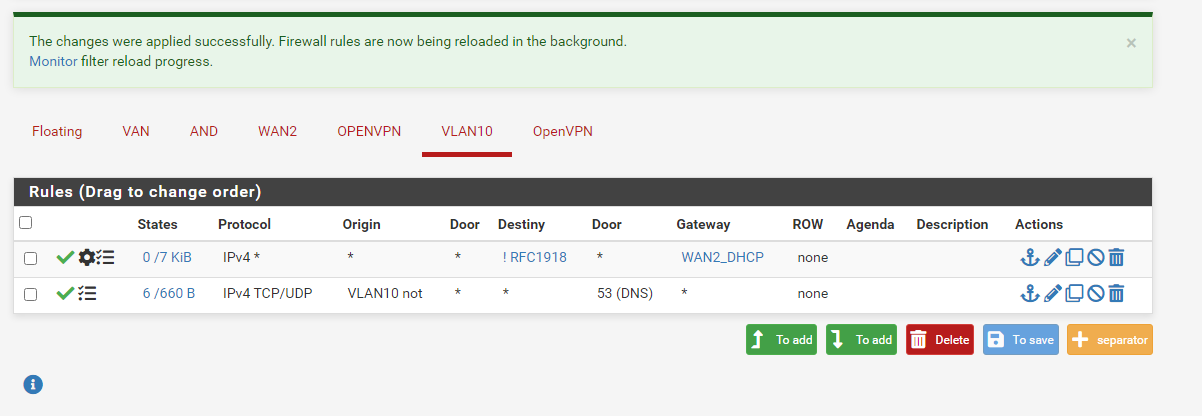
-
@gdsf
Cannot think of any use of NAT in this context. You're simply directing traffic out on a non-default WAN.
You need for sure an outbound NAT rule on WAN2, when directing packets out. But since you said, you're already successfully using WAN2 in the failover group, this should be given already. -
@viragomann yes, in the failover group, if WAN1 goes offline WAN2 works fine.
however, even configuring this VLAN as a default gateway on my WAN2, it continues with the public ip of WAN1
-
@gdsf
Go to Status > Gateway and check if the WAN2 gateway is online. -
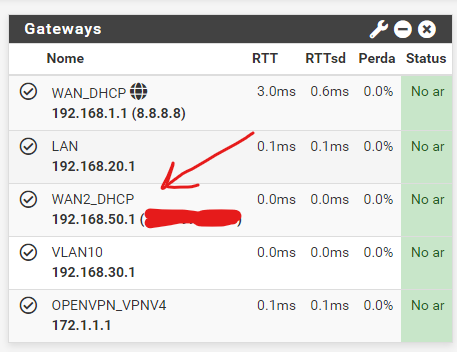
@viragomann yes :( if you want I can print other NAT or Firewall rules for you to have a better view
-
@gdsf
I'm not familiar with your language, but it seems to me that the status there says "not monitored".You have to enable gateway monitoring if using multiple WANs, otherwise the failover group don't work.
-
@viragomann It means that the link is up
-
@gdsf
Ok. Can you please post a sreenshot of Status > Gateways as requested? -
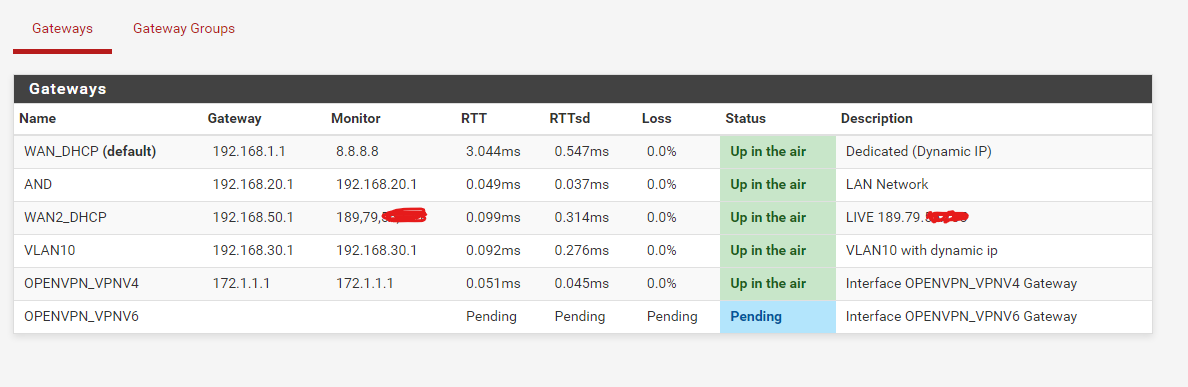
@viragomann here is the table
-
@gdsf
Why are there commas in the monitoring IP?
I don't expect that this can be used. -
@viragomann for some reason google translator put it, but when it left the native language it has dots
-
@gdsf
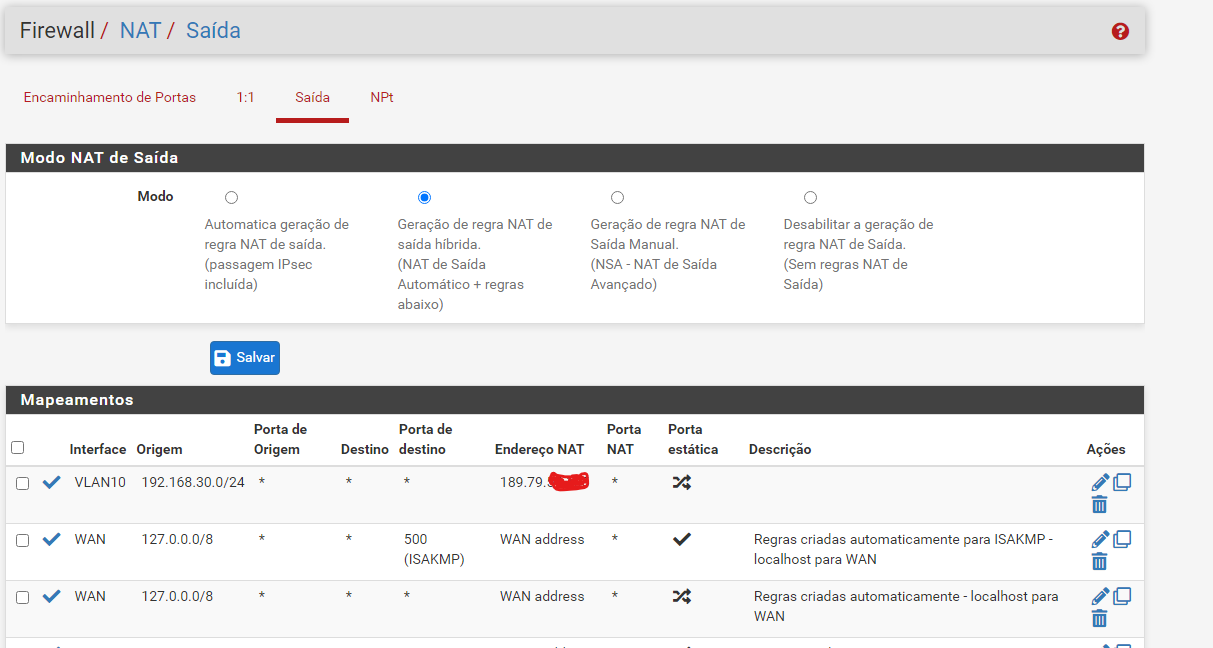
Google translator modifies a screenshot??So the WAN2 gateway is online, but traffic still goes out on WAN1 from VLAN10, even there is a policy routing rule. Or your outbound NAT doesn't work properly.
Can you post a screenshot a screeshot of the outbound NAT page, please?
-
-
@gdsf said in Traffic through another wan, 2WAN 1LAN 1VLAN:
I made an exit rule like this
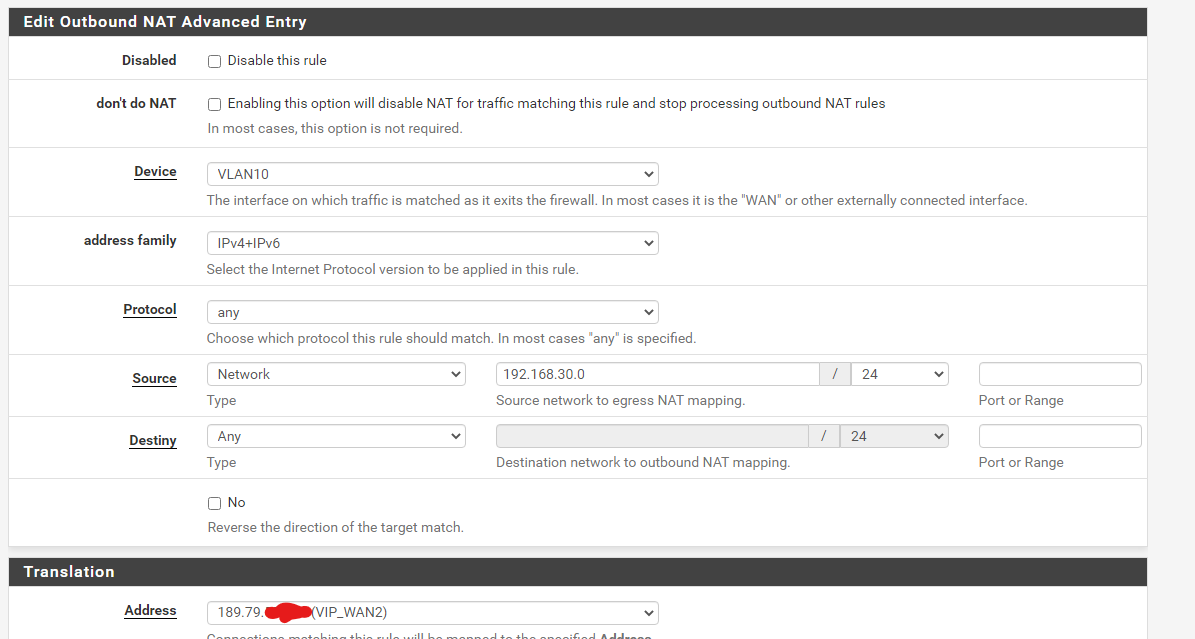
That's the wrong interface. It must be WAN2.
-
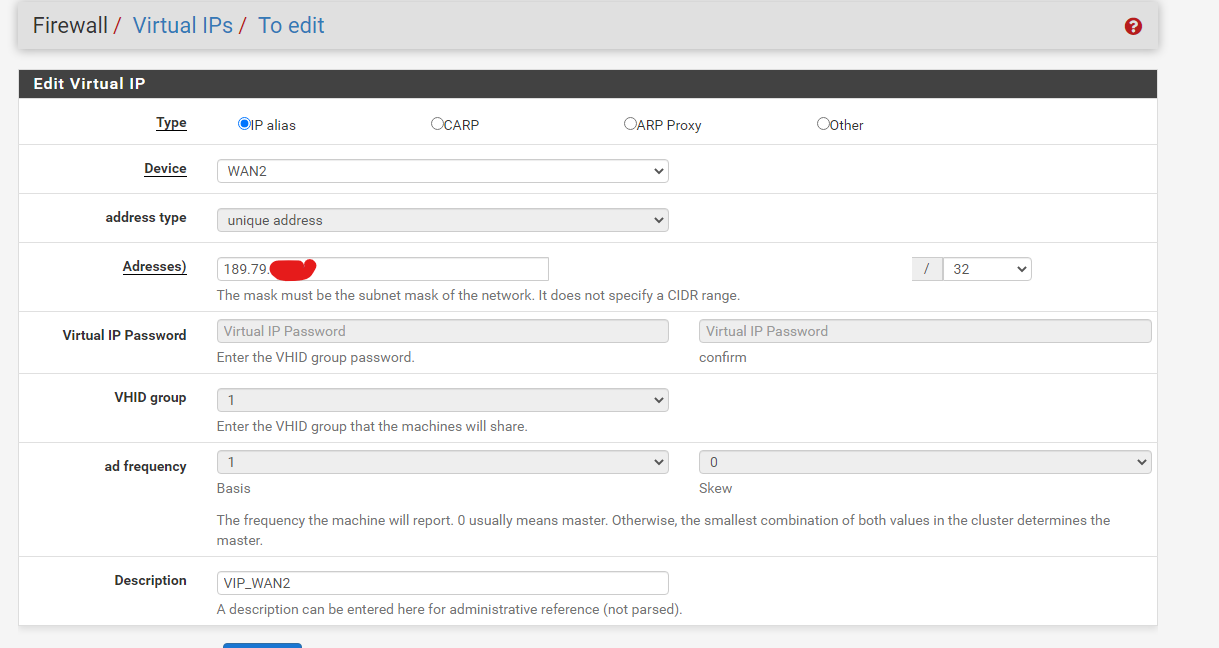
@viragomann I did that, it still didn't work, I have a doubt, does the VIP need to be /29?
-
@gdsf
If you've got a /29 from the ISP you should set a /29 mask, of course.But if that's really an issue depends on the gateway, if it accepts packets from this IP.
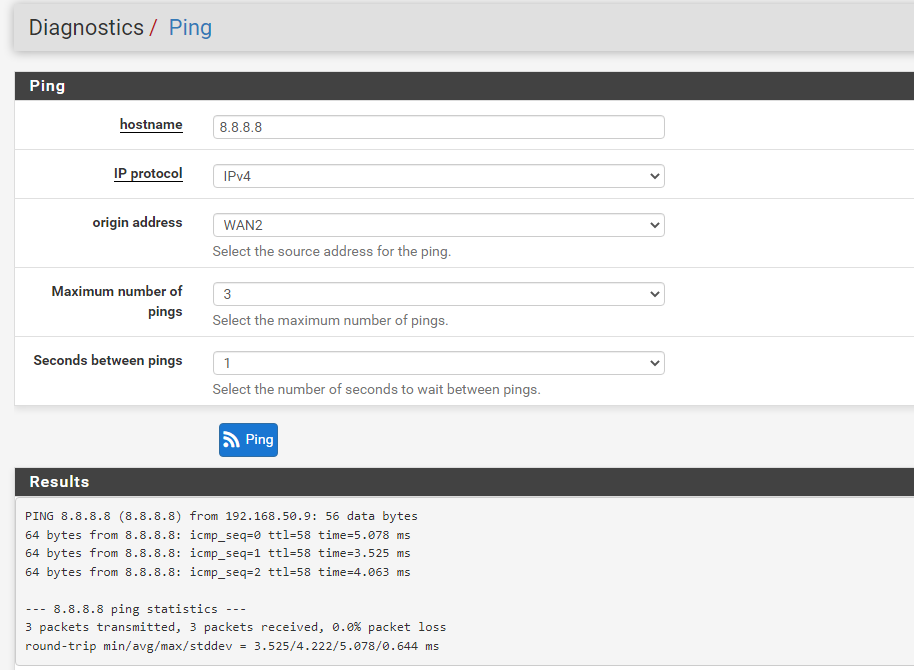
If the gatway responses to pings you can simply try it out in Diagnostic > Ping.
You can select the VIP as source and send pings to the gw from it. -
@viragomann Do you know if there's a way to find this out?
I tried calling my provider but the service is terrible
I got access to the router but I don't know if it's possible to discover the range, but it has the ip, gateway and dns info
I did a test on the https://who.is/whois/ site and it said that my range is /8
-
@gdsf said in Traffic through another wan, 2WAN 1LAN 1VLAN:
Do you know if there's a way to find this out?
As said, ping with source option. Try the gateway and a public IP like 8.8.8.8.
You can capture the packets on WAN2 while pinging to see if pfSense uses the correct source. -