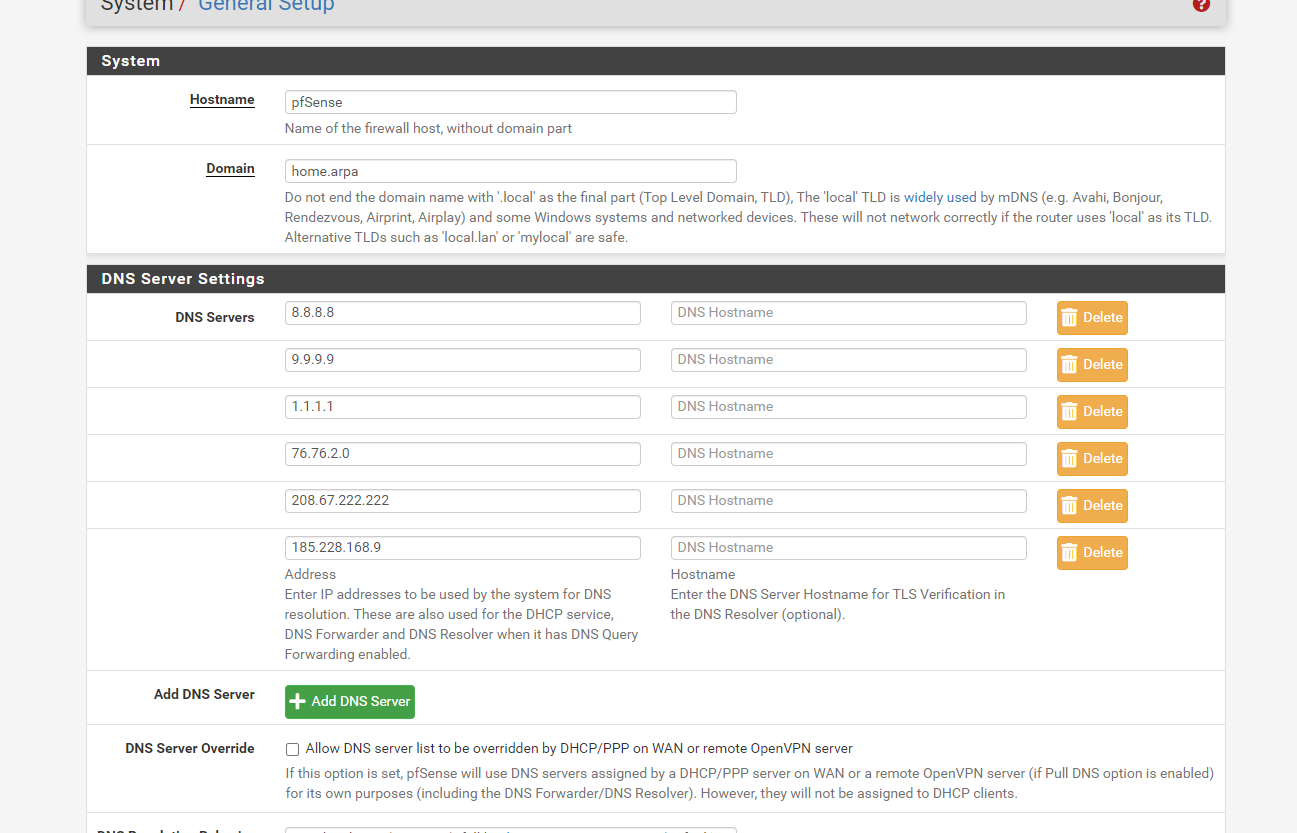
a few website are being blocked?
-
Is it because these are not actual hostnames here?
-
@terryzb do you have TLS enabled? If so try disabling it. If you are forwarding DNS disable DNSSEC.
-
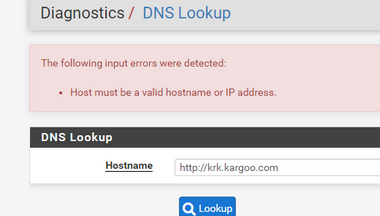
Wrong tests always give wrong answers :
Good test :
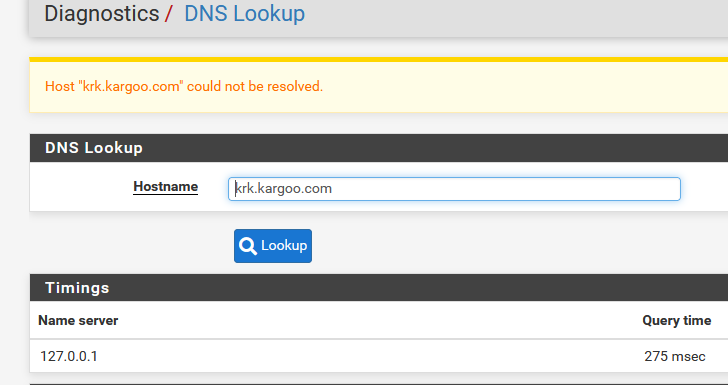
krk.kargoo.com = does not exist.
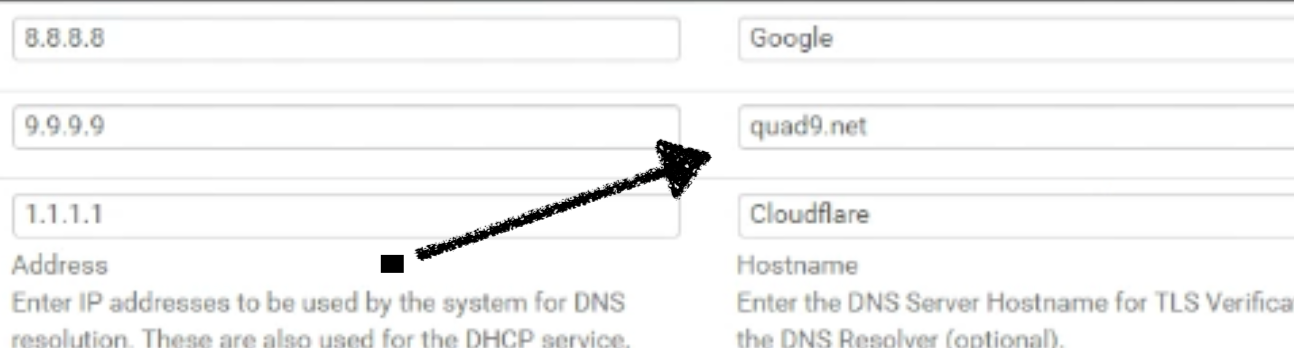
The right colom doesn't say : fill in some random description.
It says :
Hostname
Enter the DNS Server Hostname for TLS Verification in the DNS Resolver (optional).= If you use TLS, enter the host name of 8.8.8.8 1.1.1.1 and 9.9.9.9
No TLS ? You can leave (should ?) these empty.
That will be :
dns.google one.one.one.one and dns9.quad9.net -
Yeah, you entered a url and it must be a hostname there.
But also that hostname doesn't resolve. Not a pfSense issue.
-
-
IDK I have done new Clean installs it works fine if i just use my Linksys router
can I sent you my backup settings?
its just strange that some odd webpages just don't work. I'll just have to deal with it or just though this thing in the trash.
-
So what exactly is not working at this point?
-
These :
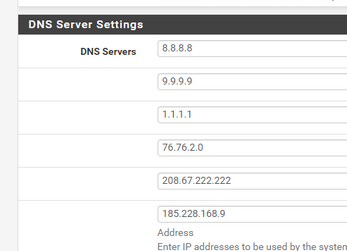
are not needed at all.
For info : Internet worked just fine before these existed - and will work just fine when they go extinct. Keep the DNS Resolver settings page all to default, and DNS will work just fine.Only if your are sure that your ISP is filtering your DNS requests, you might considering DNS forwarding.
-
a2heaven.com is not working. there is some others that I have gotten complaints about before too bout I did not note them down.
i live in a double and rent the other half main reason I'm using this is to split the networks so I can share the internet.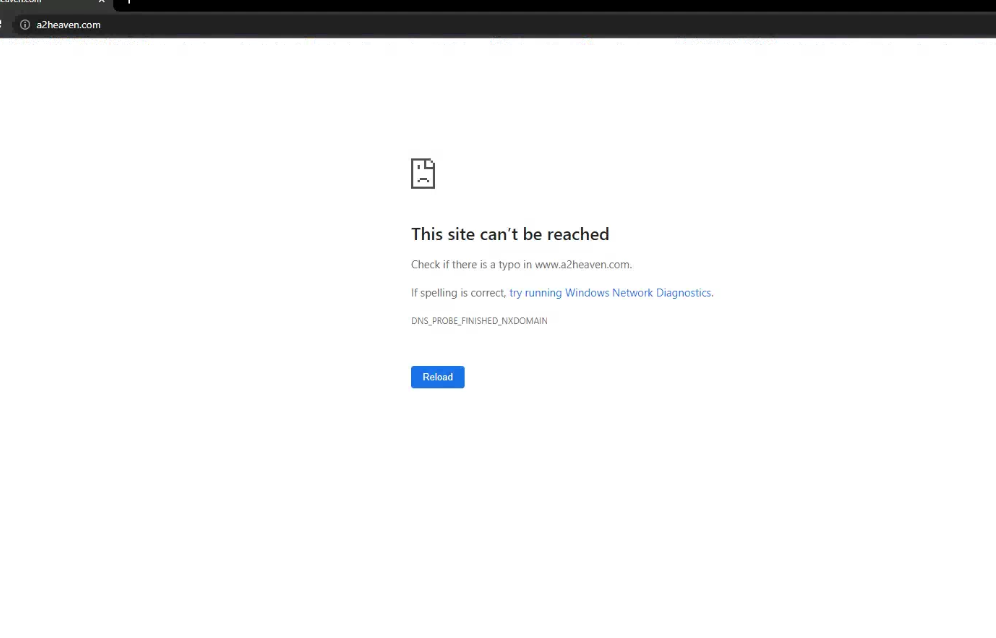
-
@gertjan said in a few website are being blocked?:
are not needed at all.
Exactly... Also that choice is bad anyway even if using them.. google doesn't filter while quad9 does. And so does that opendns one, and 76.76.2.0 is some sort of freedns - do they filter or not?
If your not forwarding those dns settings wouldn't be used by any client on your network, only pfsense if checking for say updates or packages, or trying to resolve something like ntp server or you click resolve an IP in the firewall log, etc.
If your going to forward, you should make sure all that your forwarding to either filter or don't filter.. And to be honest forwarding to different dns that filters differently is bad as well.. Does quad9 filter the exact same stuff that cloudflare does? I doubt it very much.
When you forward to more than 1 ns you have no idea which one might be used.. So they need to be doing the same stuff, be it filter or not filter, etc. If you ask googledns hey you get a response because not filtered, but you ask quad9 you don't get an answer because its filtered.. You really have no control over which one will be asked when, etc.
For all you know browser is using doh..
First step in troubleshooting any dns related problem is actually understanding what name server is being asked.. If your browser is using doh, or the client has their own dns set and not pointing to pfsense - what you have set in pfsense for dns be it forwarding or resolving has nothing to do with the clients problem.
-
yeah I put them all in there to see if it would fix this problem..
I all so did have the DNS settings in windows/Chrome to direct to PFseance. it did not help any thing so I returned every thing back to stock.
this is legit the only problem I'm having with PFseance other then that its been fine I got my 2 Plex server to pass through it and my 24TB TrueNAS server.I'm just going to unhook this thing and get some something else I may mess with it down the road some more.
sorry for wasting any ones time. -
@mkubiak402 well then your resolving.. And if your having an issue with a specific fqdn, do dig with a +trace to see where you might be having a problem.. You never know maybe you can't actually talk to the authoritative NS for domain, or having a problem with some cname or something.. Or maybe it fails dnssec?
I have no issues with a2 heaven fqdn
; <<>> DiG 9.16.36 <<>> www.a2heaven.com +trace ;; global options: +cmd . 77960 IN NS k.root-servers.net. . 77960 IN NS m.root-servers.net. . 77960 IN NS j.root-servers.net. . 77960 IN NS i.root-servers.net. . 77960 IN NS d.root-servers.net. . 77960 IN NS a.root-servers.net. . 77960 IN NS f.root-servers.net. . 77960 IN NS l.root-servers.net. . 77960 IN NS b.root-servers.net. . 77960 IN NS c.root-servers.net. . 77960 IN NS h.root-servers.net. . 77960 IN NS e.root-servers.net. . 77960 IN NS g.root-servers.net. . 77960 IN RRSIG NS 8 0 518400 20230326050000 20230313040000 951 . ao0DYjwvvOKoXPrhDUTbyQZWgMVYFt4XS5pWR/BMO2yDDe9Fs01FJQcP qS35YsulmxYhPavx9tvwMQcQUQwE1YHOqXD7+GRN/SuL06hwe+FOE6c8 yOvNED2P8xifRKiJuelMy2tsgYfc5IqBmzv6KpOkB9tH3hrLG1CnW/Vd IOmXlS/0azMrUinUFmj/iQxC8qzKNBwswvIcxarsbd6NNp03yEoBSbME 2LIMML92G7E2IVc9gxl8l2reTe02PY+GA4nqg+mskjKWGfh1I+/AJLpp JGldLQkVJ2pZDaBbH03YcyfUYRg6mHmQJgoDDQ1AJ+mL486qQfoFlNIz dwNILw== ;; Received 525 bytes from 192.168.3.10#53(192.168.3.10) in 7 ms com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20230326050000 20230313040000 951 . KeFQs/I6By6lClHLQV7pN4cxx9CLFtGSyZZnJ3KpwGJjErFRTczXhMyo emE+tXdBu8hzVDctjEF3JfJpHrnxtuoYdL51tbaGC6YI9ig0eFgWoFko 3DFdjya2wUuA5HdnD1XT9FWTFwdB43AR0XaGYfGiJJeP56bN7SlWbXmU a9uil07hD0KVh66bNvbG/25HgA4oM1OCaknBOSLLi3nVLgqClUQW4cJ+ SoU2jfB/TWDeTzRRPBJ/bZMe7+/058mdY3I4ptPfF6+yZrjcm22D5+wz w53iAbHKtV2tnoV36FsWPBcqli9dI60cd0/OtMra5RYlccautZWaJoIc oCCDLg== ;; Received 1207 bytes from 192.33.4.12#53(c.root-servers.net) in 26 ms a2heaven.com. 172800 IN NS ns12.superhosting.bg. a2heaven.com. 172800 IN NS ns11.superhosting.bg. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20230319042252 20230312041252 36739 com. PDv3EQVRspchRZUm4qtc9fNZ22TRIyIL/qvpZGjpOKgp2HTi/UsEZTBl qFwMH3gDvyqrLyD7y7x8W/+gaC0rdn3MhK+8hEVvz2IuesuJyguQ0LvK iD4d8nIGv7/nKt7Bl75AM478ZRj6bZEjDCxU17IZ8bHQgbpMqCavdSPb VPJvRqMQiuFaEXS6ejhe3/QExRQ0medU60bT5XoWG2nthA== 4SGUF457LQMLV3IDSTMN8IC5JN2AJ5VU.com. 86400 IN NSEC3 1 1 0 - 4SGUT2V2OIP7PKGQH7AHBSCH1SHBGTIF NS DS RRSIG 4SGUF457LQMLV3IDSTMN8IC5JN2AJ5VU.com. 86400 IN RRSIG NSEC3 8 2 86400 20230317043717 20230310042717 36739 com. G2pz2BtebB3GxvibZdlFCsB9kZR3Fxf8e0nXT+sqV0uZTmBL3wnS/EVj B40dSD3vH3+WHL+zK1MzPgUUszHoovqre2GJ+CM9Aw4LbGewwxavjLh7 svSguC1QDSY4mOYt3HgpNpkc1xEyGssKqq2Kj1YiBDe14NFlUbUyr4jA gz/I/t3yHdsitd7/stmpDq8Oqm25SjRUjJrQ3WGtNrx7iw== ;; Received 647 bytes from 192.43.172.30#53(i.gtld-servers.net) in 32 ms www.a2heaven.com. 14400 IN CNAME a2heaven.com. a2heaven.com. 14400 IN A 91.196.124.110 a2heaven.com. 86400 IN NS ns12.superhosting.bg. a2heaven.com. 86400 IN NS ns11.superhosting.bg. ;; Received 156 bytes from 91.196.125.5#53(ns12.superhosting.bg) in 149 ms -
Yup, that^.
Though when we last asked pfSense was unable to resolve that domain directly.
https://forum.netgate.com/post/1086268If that's still the case you might be seeing DNS requests filtered somewhere. Though it obviously can still resolve it against other external resolvers without using DoT so it's not your ISP intercepting all DNS.
-
@mkubiak402 said in a few website are being blocked?:
all in there to see if it would fix this problem..
Well that wouldn't have anything to do with anything unless you actually told unbound to forward, and use those that you setup in general dns.
Just putting them in dns would only have to pfsense itself trying to resolve something and unbound failed to respond.
-
its fixed now... what fixed it was installing the Package "System_Patches"
this showed me there was Patches for pfsense so it indrectlety fixed it..
https://www.youtube.com/watch?v=U-CEpA-D3l4 -
You applied the recommended patches for 23.01?
-
i whent to "Package installer" searched for "System_Patches" and installed the ones for 2.6.0 the video just made me aware of the "System_Patches"
no i did not install the one for 23.01 it just lists the ones for the Ver you have installed.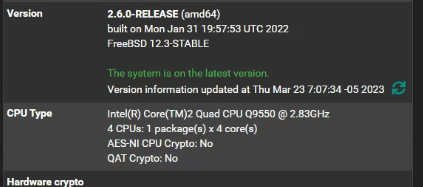
-
I know everybody probably wants this thread to simply die...but I still want to know what the fix was.
The patches package itself does zero.
As far as I can tell there are only a couple dns related patches available, Neither sounding like they apply to this case (DNS over PPP WAN and ACLs for ipv6).
-
@skogs said in a few website are being blocked?:
I know everybody probably wants this thread to simply die...but I still want to know what the fix was.
Ha, yeah I'd like to know exactly what was fixed there. I agree none of the recommended patches look like they would address this directly.
-
LOL me 2
ill have to reload the old settings on the old hardware and load the patches 1 by 1 and see what fixed it i guess.