Sanity check- 7100 vlans+ multiple interfaces
-
Hey folks,
I've been running my local vlans through the Marvell switch/1gbit copper ports over the last few years. 99% of the traffic that goes to any particular vlan stays within that vlan, but some of the traffic needs to be routed across, with specific firewall rules, depending on source and destination.Recently, I've upgraded some of my switching infrastructure and would like to use ix1 as the primary LAN/internal interface, rather than the copper 1gbit ports.
I THINK that by simply adding a new vlan interface in Interfaces/VLANs, then setting ix1 as the parent will allow those vlans to operate on both the marvell switch and ix1, without any side effects (as in vlan4091). I've seen a few people say not to do this but I haven't seen much debate/clarification about it, and am hoping someone could give me a thumbs up/down and help me understand the problems if it's a thumbs down.
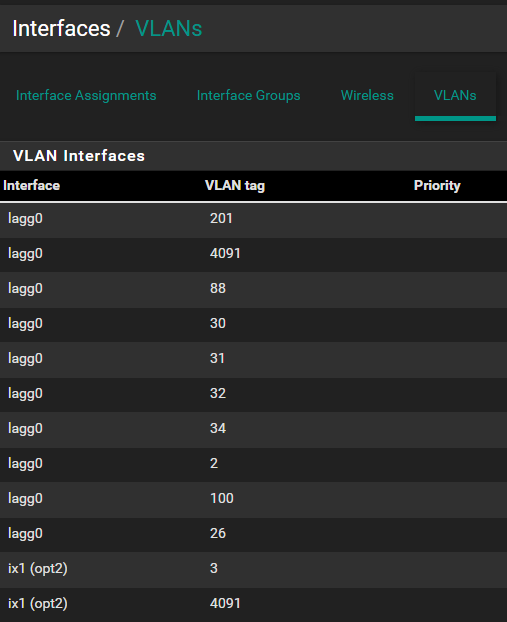
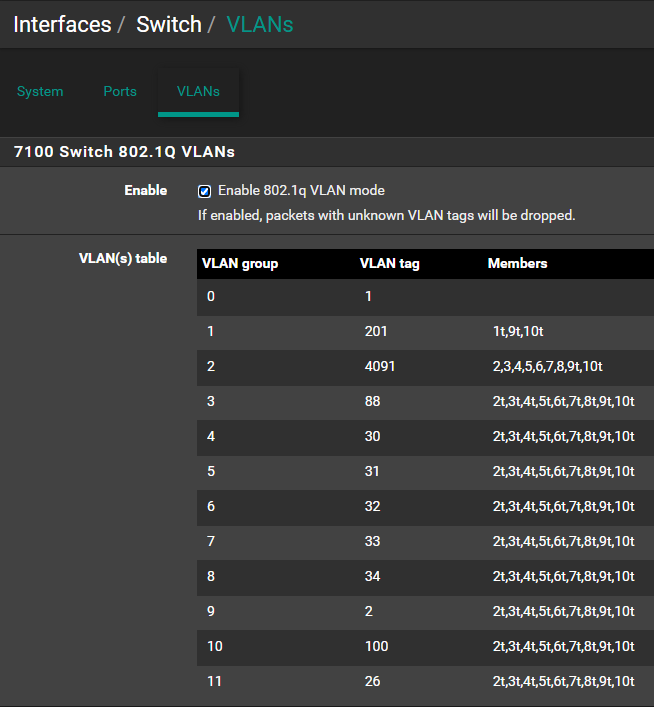
I'm at the beginning of a full rebuild of my home lab, so I just want to make sure I'm looking at things the right way. Thanks for any assistance/clarification y'all can provide!
-
Simply adding ix.4091 will not allow devices on Eth ports 2-8 to connect to it.
The thing to realise here is from pfSense's point of view ix1.091 and lagg0.4091 are two separate interfaces. It will route between them like any two interfaces if there are firewall rules to allow it. However it can only do that if they are using different subnets and I doubt that is the case.
If you need ix1.4091 and lagg0.4091 to appear as a single layer2 segment you would need to bridge those interfaces in pfSense. And that is what is not recommended if you can avoid it.Steve
-
@stephenw10 you described that limitation much better than I did. Thanks for clarifying for other viewers of the post.
Sorry for the delay...I'm trying to rethink how I've approached the network config. In the past, I know I knew how to do these things (hopefully the right way) but I've lost my mental notes. I think I'm going to greenfield this bad boy and cut over to ix1 for LAN, leaving eth1 as WAN, then drop the vLANs on ix1 as needed.
Time to hit the books and make sure I'm not missing details. As always, I really appreciate everything y'all do, both from a device standpoint and your support of the community.