No IPv6 after upgrade to 23.01
-
@maverickws said in No IPv6 after upgrade to 23.01:
my ISP (Altice/MEO Portugal) and it said to enable that option.
This post : https://forum.meo.pt/internet-fixa-e-movel-11/pfsense-ipv6-155245 ?
-
@gertjan I don't think it was that, was another on a tech forum from around which name I don't recall. but in the end the options are basically those yes.
Just noticing I'm not sending a prefix delegation hint, but been working fine since. And I'd say I don't need it actually, looking at the logs, wouldn't you say?
-
@gertjan said in No IPv6 after upgrade to 23.01:
edit : do you need to check "Do not wait for a RA" ?
Yeah, I would disable that and maybe delete the gateway and start over, just to be sure.
-
@maverickws To help rule out a config problem you could try resetting to a default config, see if it's still an issue. If it works, save a copy of that working config, and compare to your saved/backup config. If it's still a problem, just restore your old config.
I totally get "but it used to work"...23.01 skipped an entire FreeBSD version so could well have different behavior. For instance unbound set to forward, with DNSSEC enabled, seems to be causing problems for people now. IPv6 isn't broken for everyone which implies it's something specific to the people having problems.
-
@steveits said in No IPv6 after upgrade to 23.01:
For instance unbound set to forward, with DNSSEC enabled, seems to be causing problems for people now.
But that is only with quad9 I guess, working here fine with google and cloudflare.
-
@bob-dig You know you don't "delete" dynamic gateways, right? Because, well, how interface is configured and DHCP.
And by the way, stop with the "it's working here". Your config isn't everyone's config. There isn't ONE config only. There are many variables, different ISP's, different modes.
Just saying "its working here" is just annoying.
I rebooted after removing the option "do not wait for RA" and it didn't really make a difference. I get the IPv6 addresses the same, and nothing else.
@SteveITS I could if I had the time right now or other similar hardware where I could do AB testing. I will try to do that test, but I got no timetable for it.
It seems to me that this release has been poorly tested, specially in what concerns IPv6.
-
My issue here is: the ISP honors DHCPv6c giving me an IPV6 address on the WAN interface and a delegation to apply on a track interface. Both show up correctly on the matching interfaces. BUT: the RA announcement from the ISP does not follow the RFC convention of setting the "O" or "M" flags on the RA packet when DHCPv6 is available. Thus rtsold() does NOT invoke the -M or -O scripts resulting in gateway of the relevant interface not being defined/assigend (stuck in "dynamic"), dpinger not running and no default route assigned or the interface not eligible in a gateway group. The strange thing is that it worked up to version 22.05 with this same ISP, ceasing to function with the recent 23.01 update. I suspect the inner workings of rtsold() changed with FreeBSD 14 (current), but cannot find any references to any relevant changes.
Another ISP which honors the M+O flags works fine on the same router...
BTW, IPv4 with the troublesome ISP works OK, so no connectivity issue. -
HI all,
I've been following this thread since my upgrade to 23.01 which also "broke" my ipv6 configuration. Very similar to your observations:-
a) My ISP allocates ipv6 address on the WAN interface by dhcp. I get a \56 allocation
b) I'm allocated a \56 which I then distribute to multiple Internal LAN interfaces via "Track" the WAN as \64s. The "prefix" allocates different \64's to the internal LANs.
c) from the router I can ping6 to ipv6.google.com, and various other sites. (but not all)
d) the "test my ipv6" websites just say that I'm not doing IPv6. - These were working previously.
e) Google Ipv6test says my ipv6 is working... it's an outlier - nothing else agrees.
f) I don't know enough about ipv6 to understand the flags on the DHCP on the WAN interface - but I can see that the appropriate \64 ipv6 address, router address and DNS addresses are being advertised on the various internal LANs.
This all did work until 22.05 - same hardware, same ISP - only change is pfsense.
-
See also here : https://forum.netgate.com/topic/174980/fios-getting-56-pd-via-dhcp6-but-no-v6-is-assigned-to-wan/38?_=1677068897922
I've ran the proposed script myself
sh -c '/sbin/rtsol -DF igb0 2>&1'and that shows ' interesting' things :
.... received RA from fe80::46d4:54ff:fe2a:3600 on ix3,Btw : I can't use "tracking" on my LAN interfaces. That fails for me.
My ISP box does hand over one (just 1) prefix, so a /64 and does not want to give me other /64 for other lans, although my box tells me :La plage de préfixes IPv6 attributable est : 2a01:cb19:xxxx:a600::/56I read that as : I have /56 = 256 /64 for you aviable (minus one, as one has been sued for the network BOX-LAN <=> WAN-PFENSE.
And correct :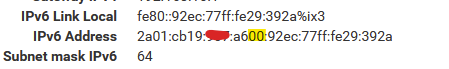
the yellow part means : prefix number '0x00' has been used for the
So I got just one, not '0x01', the next one available, but 0xdc (dono why), so I assigned that one as static IPV6 to my LAN interface :
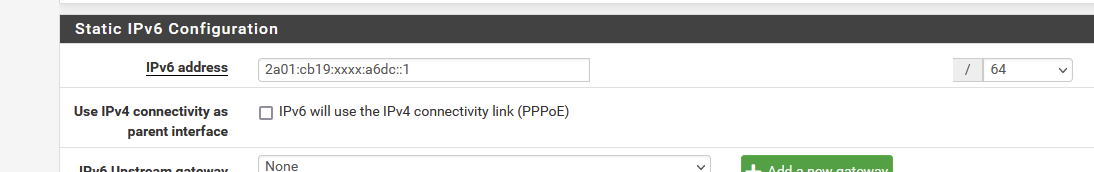
and I called it a day.
You could do the same thing I guess.
The DHCP6 server settings (and pool) have identical IPv6/64 settings - and have to be set manually.
But : this is static, and not 'tracking' my IPv6 prefix(s) at all.
So, if the ISP decides to reallocate my 2a01:cb19:xxxx:a600::/56, or the ISP box decides to give me not 0xdc but 0x11, my entire IPv6 breaks ....
I have to track this ... myself
Sorry for not making your question easier, as I can't pretend that I know (and master) what's going on. IPv6 live with he.net (IPv6 tunnel broker) was easier.
-
@gertjan I only have one observation regarding this,
On my tracking configuration the WAN interface actually never gets a public v6 address. Only a local link fe80.
So I actually never went dip on it why, simply I'd figure it would work it's magic (many IPv6 configs end up using local link as local gw), the LAN and other local interfaces would get their IPv6, all the hosts also got working IPv6 configs, so I was ok with it.
Now I can't do that (setting static) because I've realised I'm always attributed an IP inside a larger /40 network. But the addressing is still kinda dynamic, so putting it static would likely break things. It's kinda like my ISP gives me an IPv4 address and the lease lasts for years. But if I try to put that same IP as static, it denies it and next time I put it on dynamic I get a new one. Dunno why, but it's how it goes.
Nevertheless I found @mhillmann very interesting and it would be quite interesting if we could get some involvement from Netgate on this issue?
-
 M maverickws referenced this topic on
M maverickws referenced this topic on
-
@maverickws I am agreed with you. I have the same issue, for WAN is only local IPv6, because FIOS does not provide IP for the WAN, I have IPv6 for all my LANs, the only think is al my LANs got 64 prefix and not 56 that is suppose to be according to FIOS, anyway I have IPv6 and works.
Because there is not IPv6 on WAN the Configuring CoDel Limiters for Bufferbloat doesn't works for traffic using IPv6 according to the setting on software Configuration Recipes. For make work you have to applied the firewall rule for all LANs and WAN not only the floating rule for WAN.
Luke Hamburg @luckman212 has a script luckman212/assign-gua-from-iapd - GitHub, and also he has a companion patch to make it automatic. We have this problem before 23.01 because of FIOS implementation of IPv6.
-
Another day without IPv6 on 23.01.
-
@maverickws Can't even reinstall and fix the problem goes directly to 23.01 and no ipv6
-
Hi all,
Just replying here in case my recent findings help anyone else. I don't think I have (had) the same problem as @maverickws , but it may help.
To re-cap - My ISP (BT Business - UK) allocates me a static \56 on the WAN interface via DHCP. I then use WAN address tracking to allocate a \64 to each subnet/VLAN via RADV.
Prior to 23.01 - things were all working swimmingly - 10/10 on the various ipv6 Test web-sites. After the 23.01 upgrade, this all stopped.
I did notice that I was still receiving IPv6 Addresses + DNS via RADVD. I noticed that IPV6 DNS queries were still working.
Google IPV6 test said that my IPv6 was still working, but any web-site I tried to access would just hang, SSH sessions would just hang etc. (I couldn't even reliably access this forum)
i.e. I was able to make ipv6 "connections" but not usable ones.
I then fell down the rabbit hole of IPV6 MTUs / Router Advertisements / Packet Too Big ICMP, and all of the Path MTU discovery process.
I also found the Packet Tuesday channel on YouTube - very informative. Packet Tuesday
I found the IPvFOO Chrome plugin which helped by showing me how hit-and-miss the IPv6 was - small packets (like DNS) worked, larger streams (like web-pages or SSH sessions) would stall immediately.
I discovered that the PFSense default MTU of 1500 is advertised in the RADVD advertisement packet. I read a load of stuff about MTU's, and decided to have a play with that...
I dropped the MTU down to 1280 (the minimum IPv6 MUST support) - and everything started working again. I was getting 10/10 on all of the ipv6 test sites, and my SSH sessions didn't hang.
I had a play with wireshark, and saw that the "packet too big" ICMP responses I was getting were suggesting MTU of 1492. These "Packet too big" responses were from the local LAN interface of my router to the end-device I was using... I don't know whether the end-devices (laptops etc) actually paid any heed to these packet-too-big responses and started using smaller packets - as my WireShark-Fu is not that good.
I read some more, and saw that google and others use a smaller MTU than my pfSense 1500 default.
To cut a long story short - I dropped my MTU to 1480 - and confirmed that this is being advertised by RADVD
AdvLinkMTU 1480- and IPV6 is working for me again !!!I'm not sure what the change was in 23.01 that brought this to the fore.
Hope this helps someone.
Lee.
-
@maverickws
I know, it worked for years. But, seeing as many an ISP may be using PfSense themselves and update the same day as you (and bring other changes to the table at the same time to minimize deployments) and because the vast majority of users run from CPEs and won't miss IPv6 for an hour anyway, try that anyway. -
I'm a Verizon FIOS customer for home internet. Like many others, IPv6 stopped working after the upgrade to 23.01. I tried a great many things to get IPv6 working again after the upgrade to 23.01. While I can't possibly recount all the things, I will share the last thing I did that resulted in delegated IPv6 being reassigned to my LAN network.
From the pfSense console I used the 2) Set interface(s) IP address option. Both IPv4 and IPv6 were again set to DHCP. (What I would consider to be no change.)
When the console menu came back up, my IPv6 was present on LAN as I had previous experienced before the upgrade.
Hope this helps someone else.
-
@forresgeek Hi
I tried this: set my MTU to 1480, but unfortunately didn't change the situation.
-
For what it's worth. We've found a permanent solution for our issue for now (meaning no M+O flags set in RA announcements), testing it for long term validity:
We configure the interface as static with the fixed GUA address next hop gateway extracted from Wireshark capture. Then we change the IPV6 interface from static to dynamic and don't delete the static gateway (in ROUTING tab) to use it as default gateway for the interface. Rtsold() doesn't deliver any gateway for the interface BUT we've got one from the static definition, so we can route IPV6 packtes normally. As the unassigned dynamic gateway doesn't interfere with routing but dhcp6c() renews NA+PD delegations on expiration, we think we've got a stable configuration that will endure over time as long as the defined (fixed) next hop gateway with a GUA address stays valid, as it apperently does.
I acknowledge that this is a VERY nonstandard configuration we get from our ISP, but apparently their whole network is configured this way and their own (mainly Huawei) routers respect this arrangement when set to router mode as configured by default, delivering a correctly working IPV6 network on the internal side, RA-wise, meaning the RA sets the M+O flags as the RFC demands and pfSense can work as intended. The whole issue only becomes relevant if trying to use a different router, needing the ONT to be put into bridge mode.
Nonetheless it would be usefull to acknowledge this use case and see if is possible to force a fixed gateway even with DHCPv6. -
@mhillmann hi there,
based on your answer I thought of applying this to our setup and see how it would go.
The approach was slightly different, before when working I knew what was the GW address assigned to the IPv6.
So I simply added a new gateway on the routing tab, used that GW address and selected it as gateway.
So this did change something as now I can ping google ipv6 from Diagnostics > Ping
16 bytes from 2a00:1450:4003:806::200e, icmp_seq=0 hlim=59 time=15.372 ms 16 bytes from 2a00:1450:4003:806::200e, icmp_seq=1 hlim=59 time=15.177 ms 16 bytes from 2a00:1450:4003:806::200e, icmp_seq=2 hlim=59 time=15.382 ms 16 bytes from 2a00:1450:4003:806::200e, icmp_seq=3 hlim=59 time=22.012 ms 16 bytes from 2a00:1450:4003:806::200e, icmp_seq=4 hlim=59 time=15.506 ms --- ipv6.l.google.com ping6 statistics --- 5 packets transmitted, 5 packets received, 0.0% packet loss round-trip min/avg/max/std-dev = 15.328/18.726/30.600/5.971 msMy issue now is that, for some reason, I don't get IPv6 connectivity on local machines. I get IPv6 address but no route.
On my machine
netstatgives me a default v6 gateway which isfe80::abcd:ef01:fe03:bd10being that this is my pfSense LAN interface local-link address. So I can't really figure out now why I have connectivity on the pfSense LAN interface but not on local hosts.If I ping that GW my machine has configured:
# ping6 fe80::abcd:ef01:fe03:bd10%en0 PING6(56=40+8+8 bytes) fe80::8af:1f71:bffc:afc1%en0 --> fe80::abcd:ef01:fe03:bd10%en0 16 bytes from fe80::abcd:ef01:fe03:bd10%en0, icmp_seq=0 hlim=64 time=1.323 ms 16 bytes from fe80::abcd:ef01:fe03:bd10%en0, icmp_seq=1 hlim=64 time=1.381 ms 16 bytes from fe80::abcd:ef01:fe03:bd10%en0, icmp_seq=2 hlim=64 time=1.302 ms 16 bytes from fe80::abcd:ef01:fe03:bd10%en0, icmp_seq=3 hlim=64 time=1.269 ms 16 bytes from fe80::abcd:ef01:fe03:bd10%en0, icmp_seq=4 hlim=64 time=2.170 ms 16 bytes from fe80::abcd:ef01:fe03:bd10%en0, icmp_seq=5 hlim=64 time=2.981 ms ^C --- fe80::abcd:ef01:fe03:bd10%en0 ping6 statistics --- 6 packets transmitted, 6 packets received, 0.0% packet loss round-trip min/avg/max/std-dev = 1.269/1.738/2.981/0.638 msEDIT: This is a temporary (not totally working still) fix not a solution.
DHCP6 should take care of this without the need of having to find out the GW for the next hop and adding static gateways.I am appalled how no one from Netgate is getting involved in this. This was a breaking change as MANY ISP's (and I mean many) will have similar setups and hardware.
Sweep it under the rug, don't talk about it, and it's gone, is that it? -
@maverickws Is the mask correct? There was another post recently where the person was saying devices were getting a /128 mask not /64.
IPv6 is working fine here.