Whats Next?
-
@digiguy said in Whats Next?:
Did I set it up correctly? Am I using the proper private address and mask?
Do you have internet? Guess its setup "correctly" then ;) As to proper private IP and mask - this is pretty broad question.. What space you use in rfc1918 is pretty open to whatever you want to use.. Some suggestions just to lower the risk of possible issues in the future if you plan on setting up say remote vpn into your pfsense while you out and about at different locations.
Don't use the common 192.168.0, 192.168.1 networks - or a mask that would include those.. 192.168.0.0/16 going to be problematic for example.. And no point in using such a large network, when you have say a handful of devices.
Common practice for home networks is /24 as the mask, this allows for lots of devices on a network 254 while not being huge, and makes it easy to determine networks vlans going forward if you end up doing that where the 3rd octet is the network.. So easy to see that 192.168.10.x is different network than say 192.168.11
But really your free to use anything in 192.168/16, 10/8 or 172.16/12 no real wrong answer here..
As to set it and forget it - that is really up to you as well.. It is quite possible to set it up and it will just work.. And really not much to do, until such time as you want to do "something"
As to things to do or look at - I would suggest you check to see if new version of pfsense out on somewhat regular basis.. One thing users coming from your typical soho router can get overwhelmed or shocked by is the vast amount of "noise" on the internet that their soho router didn't show them... Ie hits to your pfsense wan IP from all over the globe at all times and hours of the day on all kinds of different ports.. Doesn't mean anything is wrong, or bad - the internet is a noisy place.
Or even blocks on their lan side for IPv6 or Multicast, or just broadcast traffic, etc. etc.. So prob you want to at least familiarize yourself with what is being logged in the firewall.. Do you want to see all of it all the time, or do you want to create some rules to minimize the amount of noise that gets logged, etc.
As to making sense of the logs - that can be a bit of a learning curve if you don't have a lot of networking experience.. As mentioned all the wan traffic you will most likely see. Or even blocks on your lan side trying to understand what it all is..
Lots of people here happy to explain any questions you might have about really anything - so welcome to using pfsense.. Have Fun..
First thing though is to memorize every word of the manual, and be able to recite it from memory - there will be a test later, just kidding ;)
-
@digiguy Just a suggestion for private addresses, I use the home/business owners birthday with a 10./24.
So if today is your birthday, your subnet will be 10.2.19.0/24.
This leaves the "usual" 192.168 addresses to be used for vpn tunnels and anything else that wouldn't overlap anywhere.
Been doing that for years and still never used the same subnet twice!
Still waiting for it to happen. -
@jarhead that is actually a pretty slick way of coming up with network without having to put much thought into it, and should be unique, etc..
This came to mind when you mention
Been doing that for years and still never used the same subnet twice!
https://en.wikipedia.org/wiki/Birthday_problem
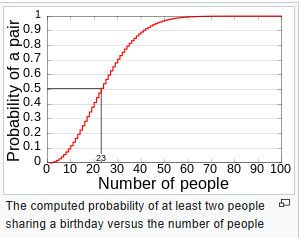
-
@digiguy There is not much maintenance needed. Updates come out 3x/year for plus and apparently less for CE.
Everyone will have their own way of doing things. We turn off logging if the default block rule so there’s very little noise in the logs. (In logs page settings)
Netgate has video “hangouts” if you prefer video.
-
@johnpoz Ha! Interesting graph.
By that, it should've happened by now!
Still wondering what I should do when it does happen, does that warrant buying the owner a beer? -
Great to get such quick detailed responses to such a vague and generalized post! Thank you!!! I have D/Led the pfsense documentation/manual. Will start memorizing all 2000+ pages... LMAO!
For my private address, I have gone away from 192.168.x.x and utilzed 172.16.0.x/16 Its what I used with what I had before won't mention any names but here is the initials (Untangle - lol) Seems to have worked.
One reason I question my configuration is I have had some issues. My wireless access point wasn't working. A power cycle and cable reconnecting looks like it helped. I did notice my wan did go down/up and not sure if that was the start of the issue. Still attempting to read the logs to see if I can determine the issues...
-
@digiguy said in Whats Next?:
utilzed 172.16.0.x/16
/16? You have plans of 65k some devices on this network?
I'm pretty sure /24 would work fine, or /23.. /16 is huge for a single segment..
-
uhh.. no plans to expand that big... lol.. will change it to 24... thanks!
-
@digiguy I see a lot of people using /16's for their LAN. Think of the broadcast traffic that generates alone. It makes no sense at all.
-
Nevermind... doing some reading and I am seeing some of the answers in Dr Google... lol
You are certainly correct on the extra traffic. If I setup another interface for a internal web server, a DMZ(OPT1), do I need another segment? a subnet? What or how should that interfaces IP be setup? Static? dhcp? What should my internal web server's static IP be?
-
@digiguy The answer to all of those questions is "Up to you".
It really depends on what you want but yes, you would use another subnet on another interface and you would set the interface address statically but you can use DHCP for connected devices. Really is up to you. -
You could have a look in, if you find something you may interested or it is matching your needs or fitting the rest of
your network. If you find something configure it out following that docu. -
This post is deleted!