Routing via Site2Site Wireguard for a specific client
-
@thisisagoodfirewall
If you want to use 8.8.8.8 on the client, simply forward DNS requests from its source IP, as already suggested.The masquerading is done with an outbound NAT rule on pfSense.
Switch the outbound NAT on the remote box to the hybrid mode.
Then add a rule for the source of 192.168.2.0/24 (or only 192.168.2.73/32) to the WAN. -
just need a proof of concept. can fiddle with dns later.
added 8.8.8.8 as client dns.masq like this?
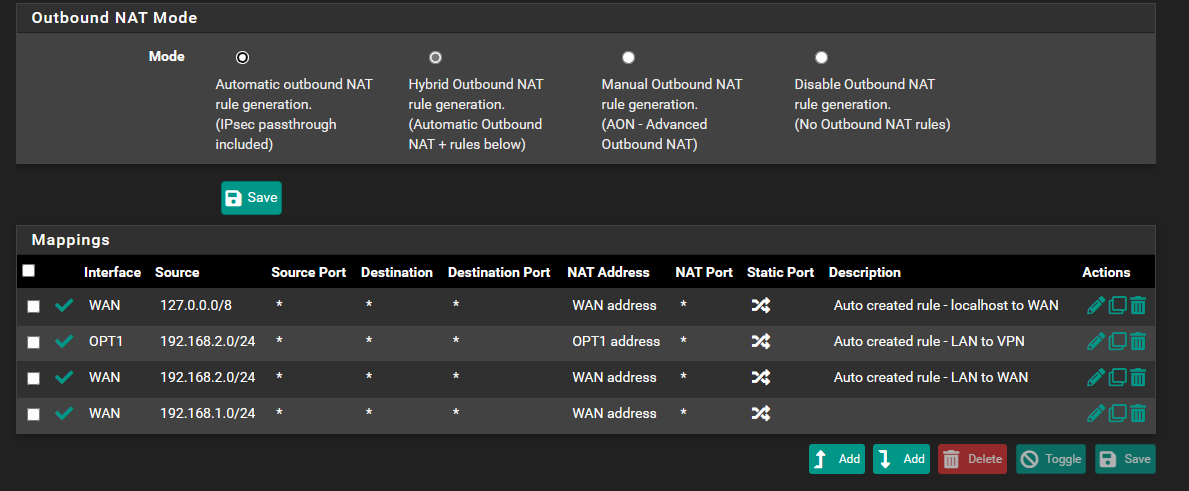
I had those settings before and yet the client 192.168.2.73 can't connect to the internet via tunnel. -
@thisisagoodfirewall
The NAT rules are useless as long as you have the automatic mode enabled. -
@viragomann
I have the Hybrid Outbound NAT mode enabled as visible in the picture.
Am I doing this right? -
@thisisagoodfirewall
I see. Seemed it was the automatic mode.From the concerned client can you ping 8.8.8.8?
-
nope. can not ping 8.8.8.8
can reach the network on SiteA - last trace is a dns server.
I assigned a dns server from Site A.
DNS is working.
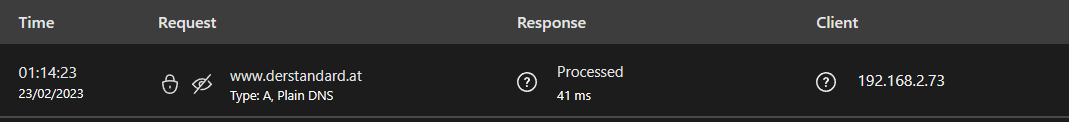
internet is not. can not ping 8.8.8.8
-
@thisisagoodfirewall
So this let me suspect that the outbound NAT doesn't work.To be sure, did you do the outbound settings at A?
-
@viragomann
Site A:
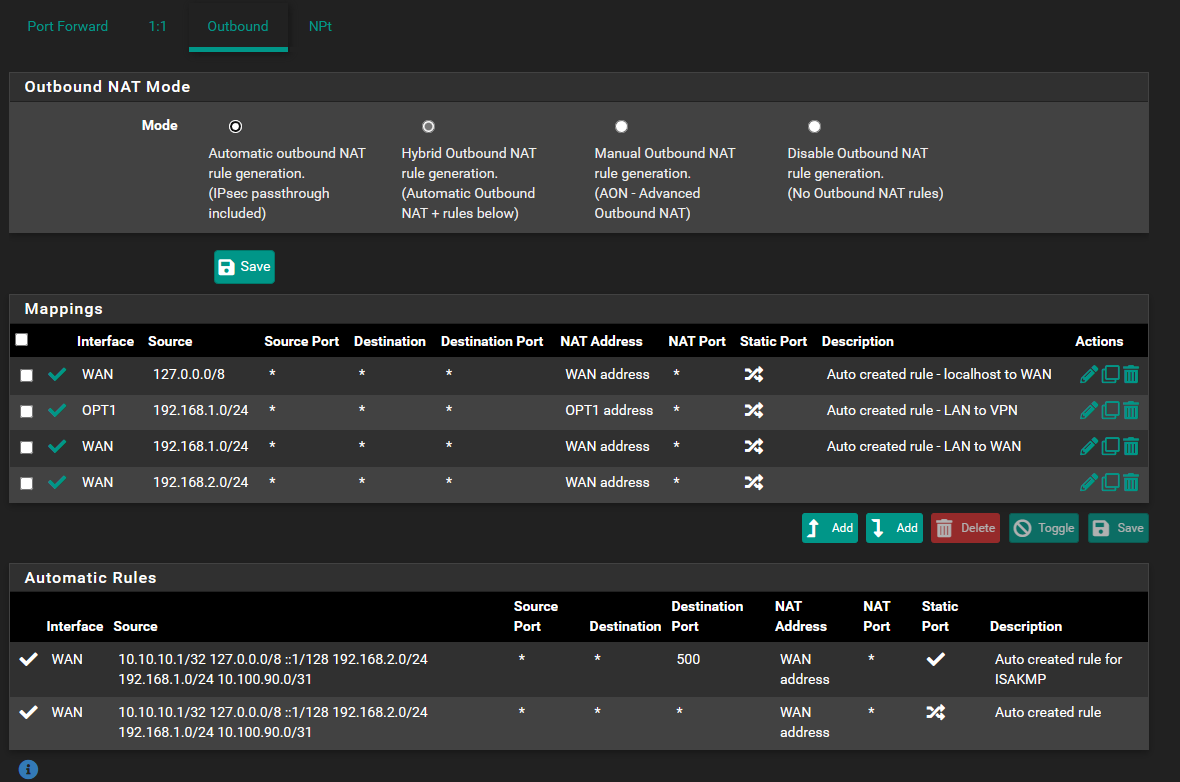
-
@thisisagoodfirewall
This should work from the point of NAT rules.
However, that one on OPT1 should not be needed. It would only impact access from A to B.Do the firewall rules on the VPN interface allow internet access?
-
OPT1 is the mapping for my openvpn service. Local LAN of Site A (192.168.1.0/24) to VPN Provider.
The Gateway of the Wireguard Site2Site tunnel allows all connections.
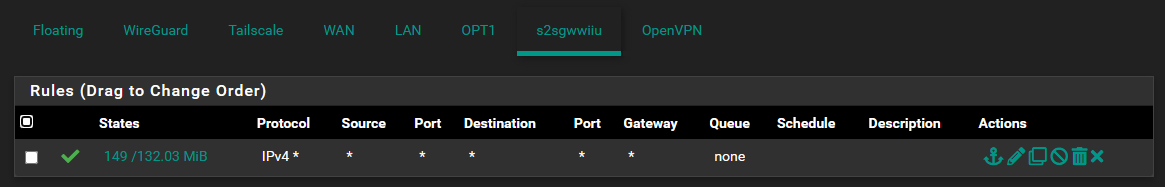
Still can't figure out why Client on Side B can not connect via the Gateway.
-
@thisisagoodfirewall said in Routing via Site2Site Wireguard for a specific client:
OPT1 is the mapping for my openvpn service. Local LAN of Site A (192.168.1.0/24) to VPN Provider.
Ah, I see.
Could it be that the upstream traffic from the client at B is also routed to this VPN provider due to the site A routing table?
-
This could be an issue, lets see.
This is the Outbound NAT of Site B.
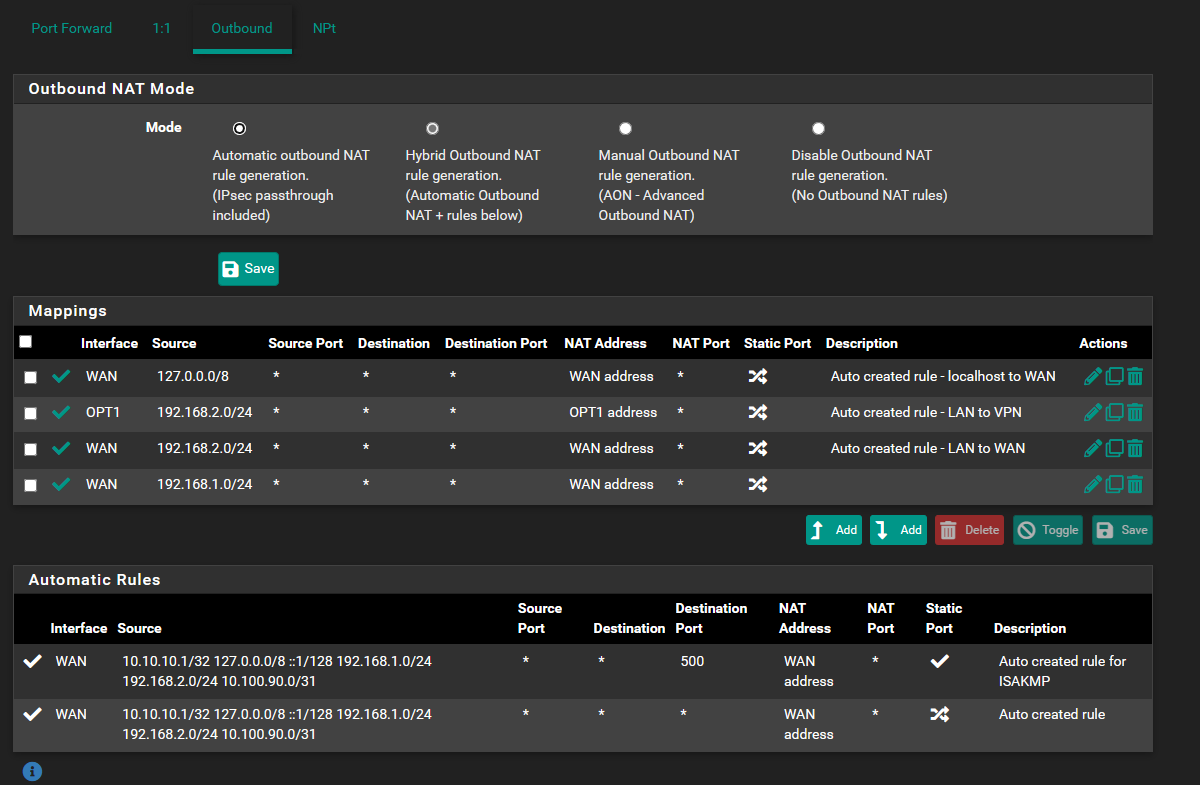
If I create a firewall rule for the Client on Site B I skip the VPN provider and use the WAN instead.
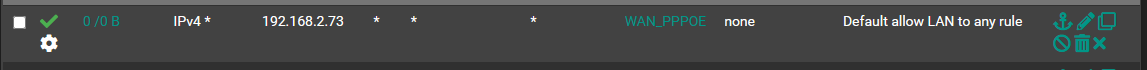
I just want my client to not use the WAN Gateway but the Wireguard Tunnel Gateway s2sgw and have the traffic routed via the Site A internet.
-
@thisisagoodfirewall
Yes, you can do this with a policy routing rule, but consider that you will have to allow DNS access to the local server with an additional rule above of this or even forward DNS requests to a public server. -
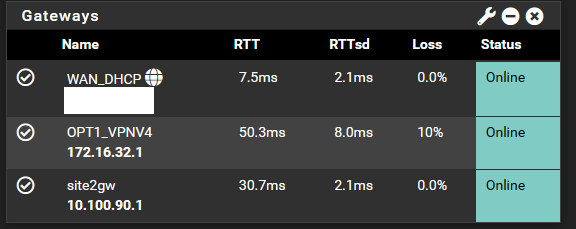
Site B Gateways
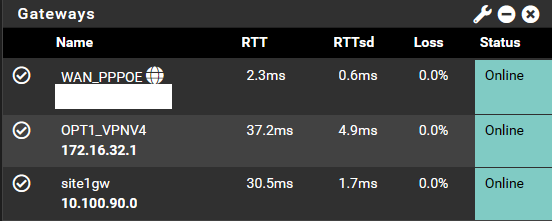
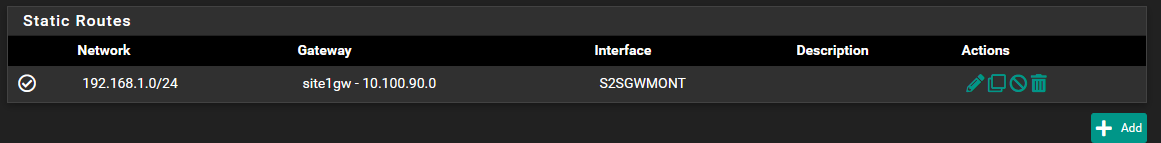
I need to route via site1gw.This is Site A Gateways
Site A static route
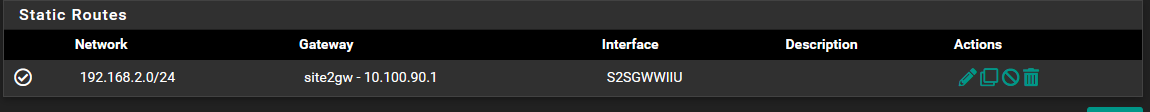
Site B static route