Ad Guard with pfSense
-
@steveits Ok, that makes sense; I just thought ADGuard would see the requests forwarded from pFSense but I suppose not. Thanks :)
-
If your goal is to use AdGuard for all your clients, and be able to see all the stats, you should turn it around so that AdGuard is first in line.
In AdGuard, put your pfsense IP (192.168.1.1) in the box where it sais Upstream DNS servers, under Settings > DNS Settings. You can test that it works using the button further down on the page.
Then you tell all your clients to use AdGuard as their DNS... This is done in pfsense under Services > DHCP Server - Server section. Here you put the IP of your AdGuard server as the first and only item, which will then be provided to all clients in the network.
This way (after IP renewal) all your clients will query AdGuard first, giving you all the stats and data, and of course dropping ads etc. AdGuard will only forward accepted queries to pfsense for further processing.
-
@zululander said in Ad Guard with pfSense:
ADGuard would see the requests forwarded from pFSense
It should but if pfSense returns an answer from cache, Ad Guard won't see that query/response. I would think it should see one query for each hostname though (until each TTL expires).
Reversing it as Gblenn noted would send all queries there.
Also just to be clear when you say "point" you enabled forwarding in the DNS Resolver settings?
-
@zululander Set your DHCP server settings in pfSense to have the clients use the Adguard DNS server IP. Only Adguard, not Adguard and pfSense IP.
Then set the DNS server for pfSense to do it's own lookups or forward to Quad9 or whatever your preferred service is. That's what pfSense will use for itself and you don't want that Adguard filtered.
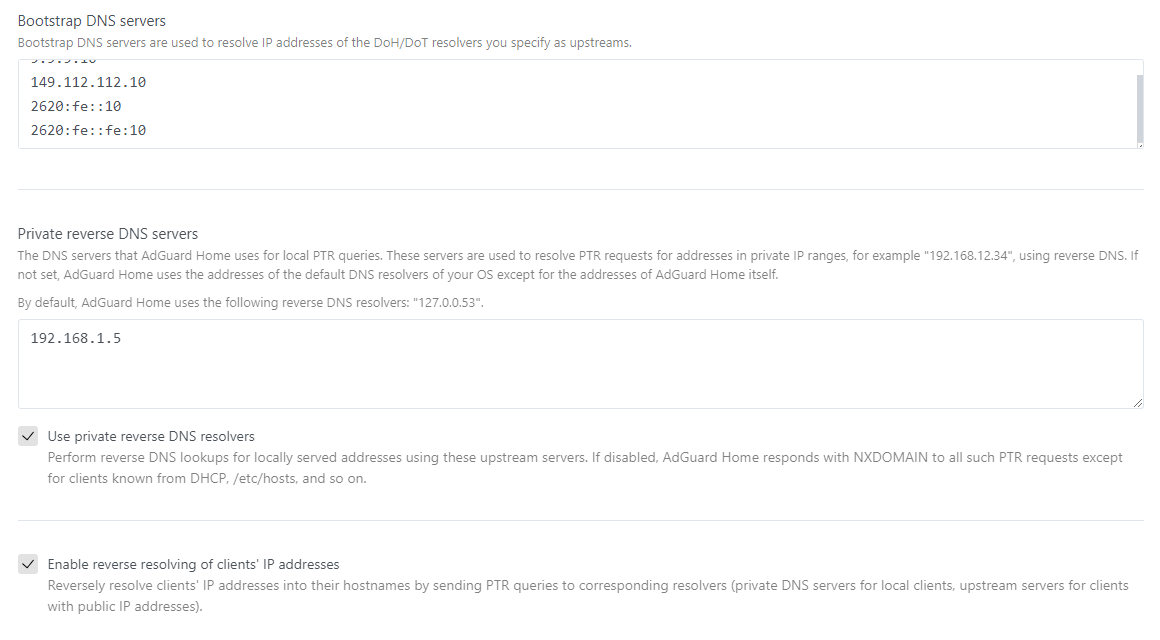
In the Adguard DNS settings I'd configure it to have your local domain requests be forwarded to pfSense since pfSense will know about DHCP entries and Adguard won't. I also have Aduard forward local reverse lookups to pfSense. And have Adguard use DNS over HTTPS.
You'd need to adjust this for your LAN IP, pfSense IP and DNS provider. Something like this replace home.local with your local domain and 192.168.1.1 with your pfSense DNS IP. I usually set Adguard to parallel request and do something like this. The first 3 lines handle sending local info that pfSense would have to pfSense. The last 2 get you the fastest lookup from 2 different services.
[/home.local/]192.168.1.1
[/in-addr.arpa/]192.168.1.1
[//]192.168.1.1
https://security.cloudflare-dns.com/dns-query
https://dns.quad9.net/dns-query -
@steveits, @Gblenn & @Cylosoft Thanks for that. I think I am nearly there.
My router IP is 192.168.1.1 and it has the following DNS servers:
- 9.9.9.10
- 149.112.112.10
pFsense has IP 192.168.1.5 and Adguard 192.168.10.15
AD Guard settings:
Upstream servers- [/home.local/]192.168.1.5
- [/in-addr.arpa/]192.168.1.5
- [//]192.168.1.5
- https://security.cloudflare-dns.com/dns-query
- https://dns.quad9.net/dns-query
Parallel requests
("And have Adguard use DNS over HTTPS", I will set this up later once I have sorted out everything else)
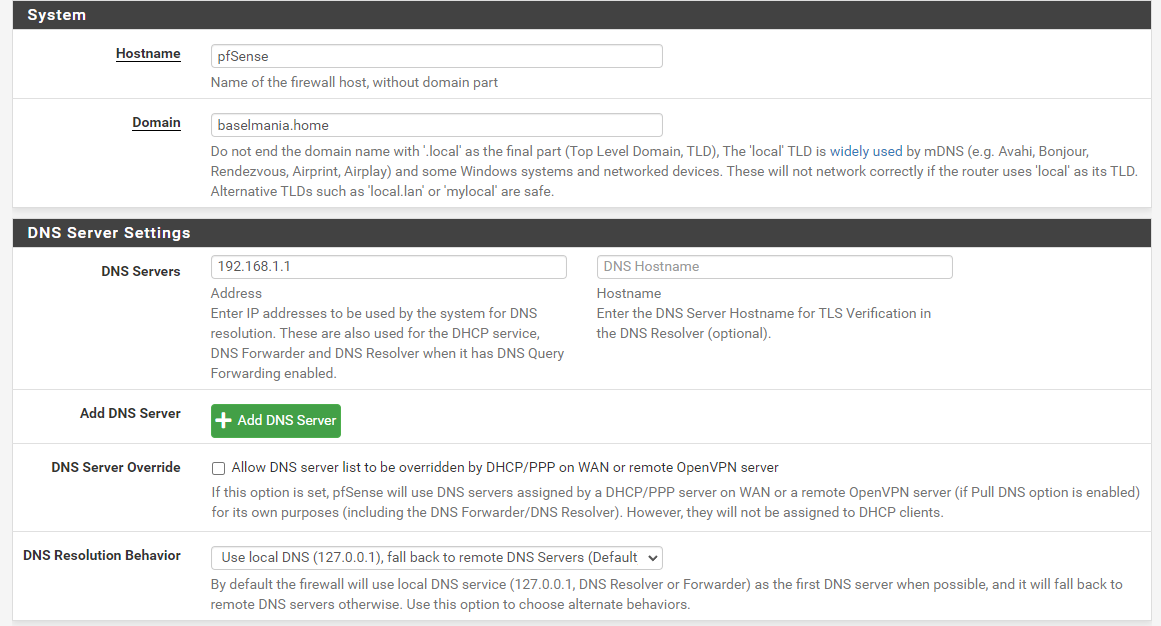
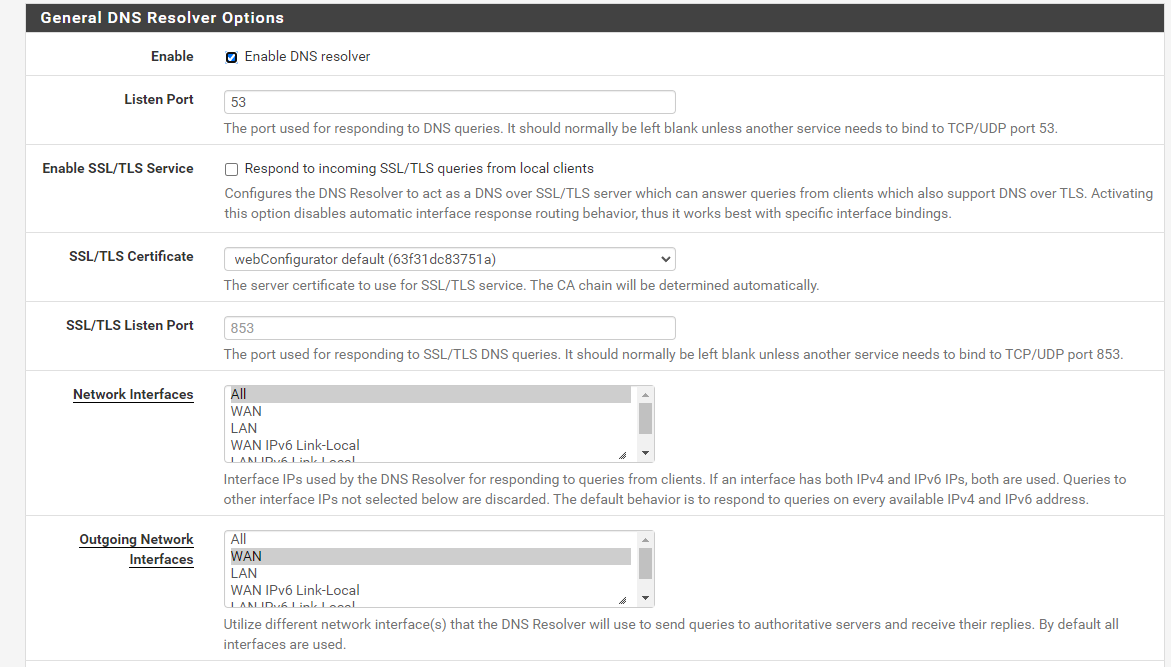
pFsense settings
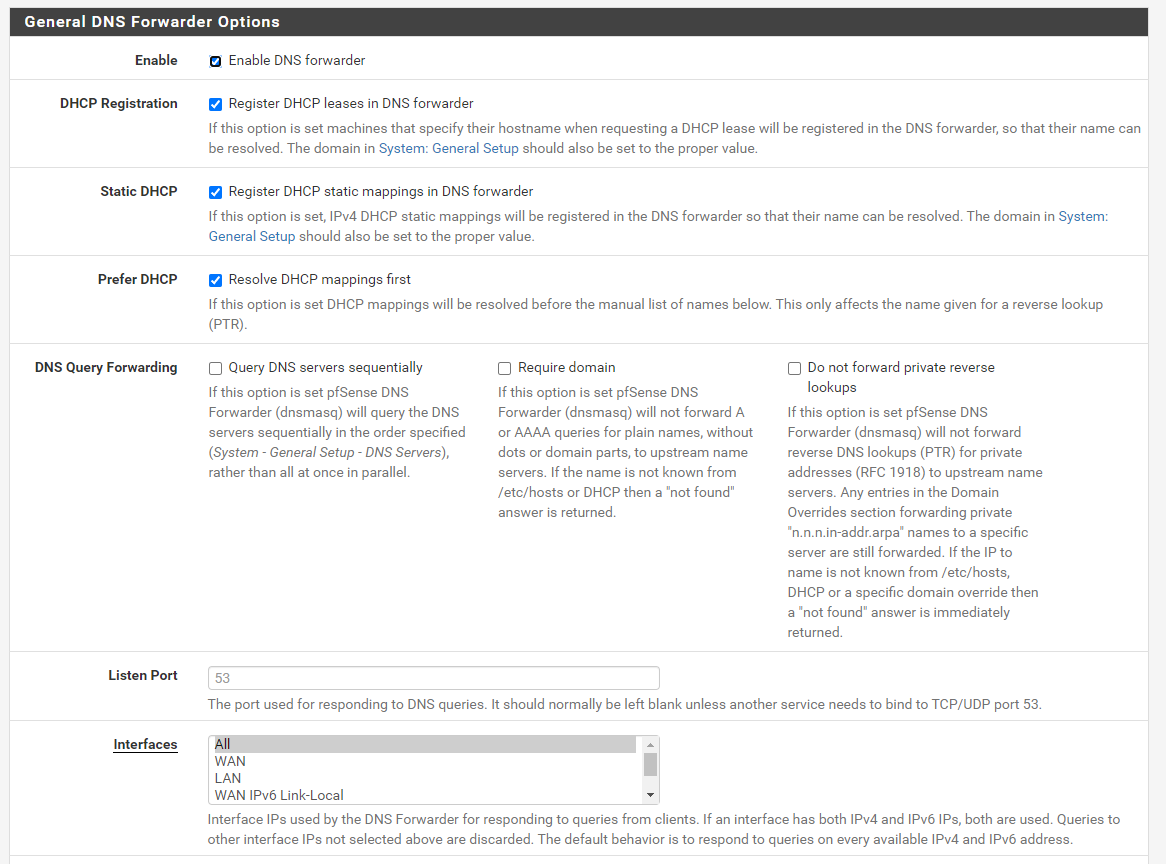
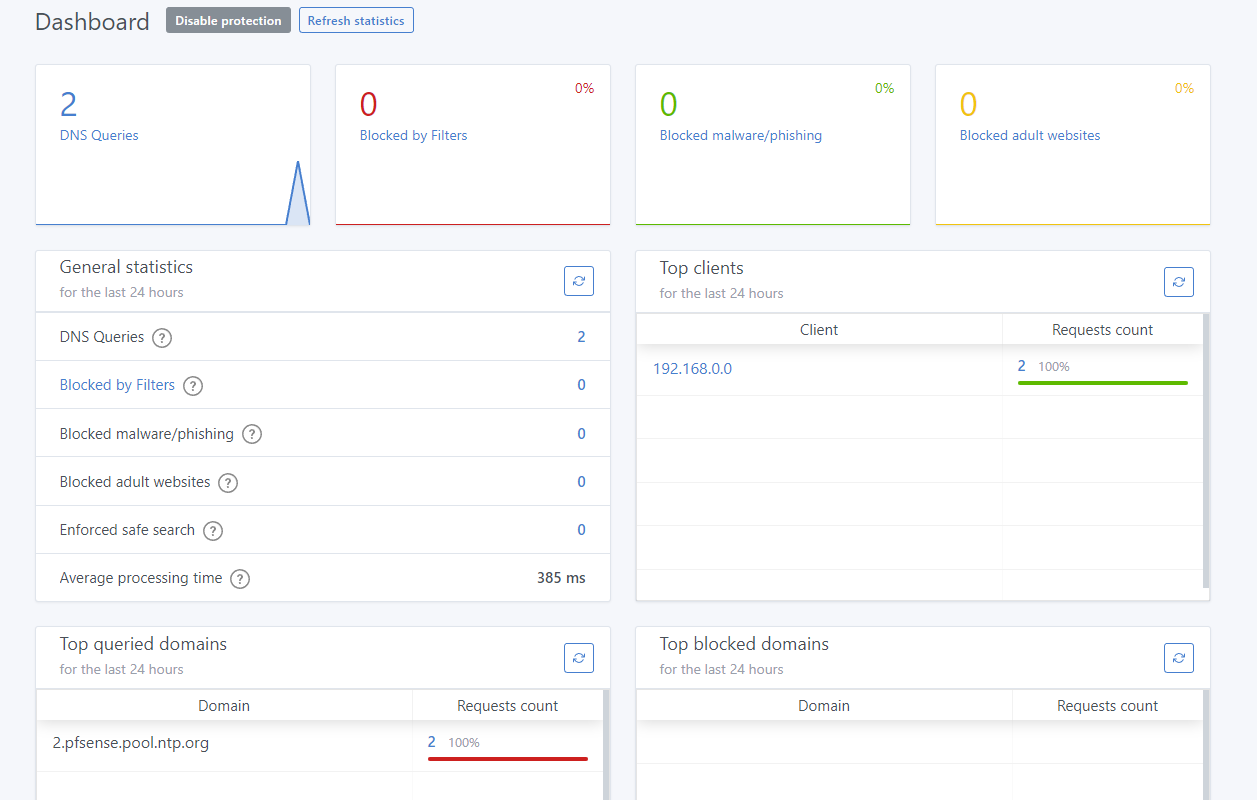
Adgaurd is now reporting more stats and blocking some adult sites, but not all i.e. it blocks www.peachesandcream.co.nz but not https://www.porn.com/
Also it still only lists one client i.e. 192.168.0.0
Also I had a host override (see below) which I can no longer browse to i.e. now need use the IP.
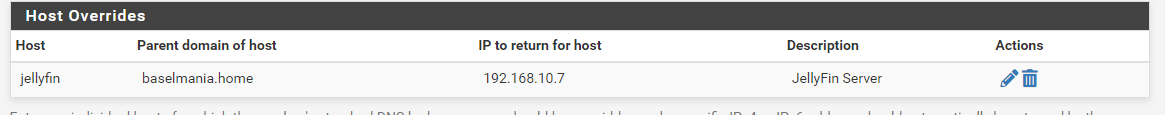
I am obviously still not understanding something :)
-
@zululander said in Ad Guard with pfSense:
My router IP is 192.168.1.1 and it has the following DNS servers:
9.9.9.10
149.112.112.10pFsense has IP 192.168.1.5 and Adguard 192.168.10.15
You are making life harder than it needs to be.
Clients on your network need to only see only he one DNS, which does your DNS filtering (Adguard). If your clients use any other DNS your filtering will not work reliably. Currently they can used- Adguard 192.168.10.15
- pfsense 192.168.1.5
- your router 192.168.1.1
- internet DNS
Imo I suggest
- Put your ISP router in bridge mode and use pfsense as a router.
- Connect all Lan & wifi defices to pfsense (not the ISP router)
- in pfsense block DNS accesses except from Adguard 192.168.10.15
- in pfsense DHCP set clients to used Adguard 192.168.10.15 for DNS
- in pfsense leave DNS resolver with the default configure so it access appropriate internet sources
-
This post is deleted! -
@patch Thanks for this.
- pFsense is using 192.168.10.15 (adguard) for DNS
- pfsense DHCP setis clients to Adguard for DNS
- I am forcing all DNS requests to go via Adguard using: https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html
- I have left the DNS reolver with the default option.
Relavent sites are now blocked although I am still only seeing one client (192.168.0.0) listed on the ADGuard dashboard.
I am not to sure about setting up pFsense as the router. My ASUS-AC58U allows me to change operation mode from Router to AP mode. I am guessing I start with that.
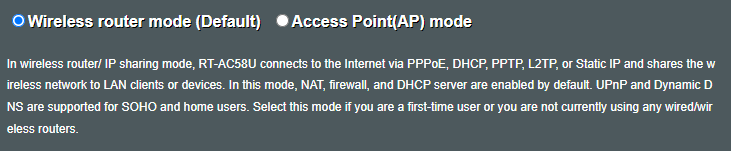
Currently my router is set to WAN connection type: Automatic IP. Looking at pFsense I have the following options
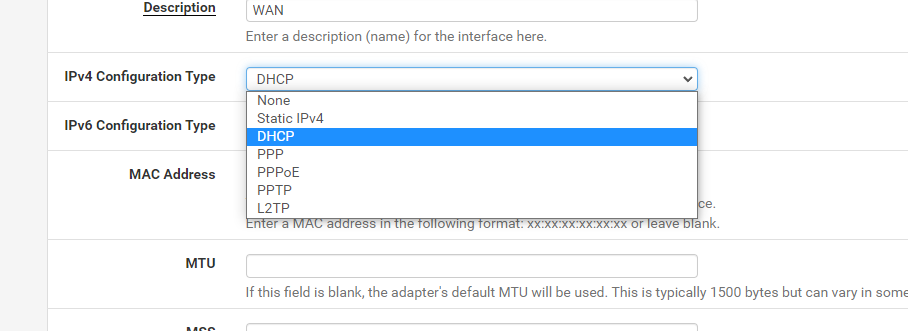
Looking at these options I cannot see where to set the following options required by my ISP:- WAN Connection Type: DHCP (Automatic IP/Dynamic IP/IP over Ethernet)
- list item802.1Q: Enabled
- list itemVLAN ID (802.1Q): 10
- list item802.1P (Priority): 0
- IP Version: IPv4 or IPv6
- MTU Size: 1492 or 1500 (I can find this one)
- NAT: Enabled
-
@zululander said in Ad Guard with pfSense:
I am not to sure about setting up pFsense as the router. My ASUS-AC58U
If you have a ADSL/VDSL wan connection you will need a modem to connect to your ISP.
If you put your all in one router in bridge mode it will become just a modem and can be used for that purpose. (note you also loose access to most other function in your all in one router such as wifi). Your ISP wan parameters are then entered into pfsense Wan settings.
If you put an all in one router in AP mode you can connect it to the LAN side of pfsense and wifi connected devices can be managed by pfsense like all other Lan devices. Note putting your all in one router in AP mode means it no longer needs nor has a wan interface settings
Note the simplified configuration I'm recomending requires your modem is a different hardware device to your wifi AP
-
@patch I have fibre that comes to the ONT and then goes to the ASUS router. Can I plug the ONT directly into the pFsense WAN? If so, then I am battling to find where to put the settings the ISP gave to me.
If not, what modem (make/model) do you recommend for a home lab?
-
@zululander said in Ad Guard with pfSense:
I have fibre that comes to the ONT and then goes to the ASUS router. Can I plug the ONT directly into the pFsense WAN?
Yes
How to do so will depend on:- How many NIC does your computer running pfsense have? At least 2 makes things easiest.
- If only 1 do you will need to use Vlan and pfsense on a stick configuration. Do have a programmable switch (at least level 2)?
When you have at least 2 interfaces to pfsense, one will be Wan the other Lan. The ISP setting are entered via
Pfsense -> Interfaces -> Wan -> (See the Manual)Your ASUS router can then be put in AP mode, connected to the pfsense Lan and used for wifi access.
-
@zululander re: using a VLAN for WAN, I see posts here every few months. I’d search for your ISP and/or VLAN on WAN.
-
@patch I have 3 nics i.e. WAN, LAN & OPT1.
I can only see MTU on the WAN interface and not the rest of
- WAN Connection Type: DHCP (Automatic IP/Dynamic IP/IP over Ethernet)
- list item802.1Q: Enabled
- list itemVLAN ID (802.1Q): 10
- list item802.1P (Priority): 0
- IP Version: IPv4 or IPv6
- NAT: Enabled
Can't see the above in the documents
Sorry for being a little slow with all of this.
Yes I do have a level 2 switch. VLAN 1 is for 192.168.1.0 (WAN)and VLAN10 for 192.168.10.0 (LAN). Lics are patched accordingly.
-
@zululander you’ll have to create it as a new interface
https://docs.netgate.com/pfsense/en/latest/vlan/configuration.html#web-interface-vlan-configurationThen use that instead of WAN. I haven’t done that myself…see if you can find a thread for your ISP. Might be better to start another thread too, so people find it by title.
-
L lightingman117 referenced this topic on