Site-to-Site IPSec w/one side behind NAT?
-
I already have several sites up and running like Remote Worker 1, where I have a pfsense box at the edge of the remote network establishing an IPSec tunnel back to the main office:
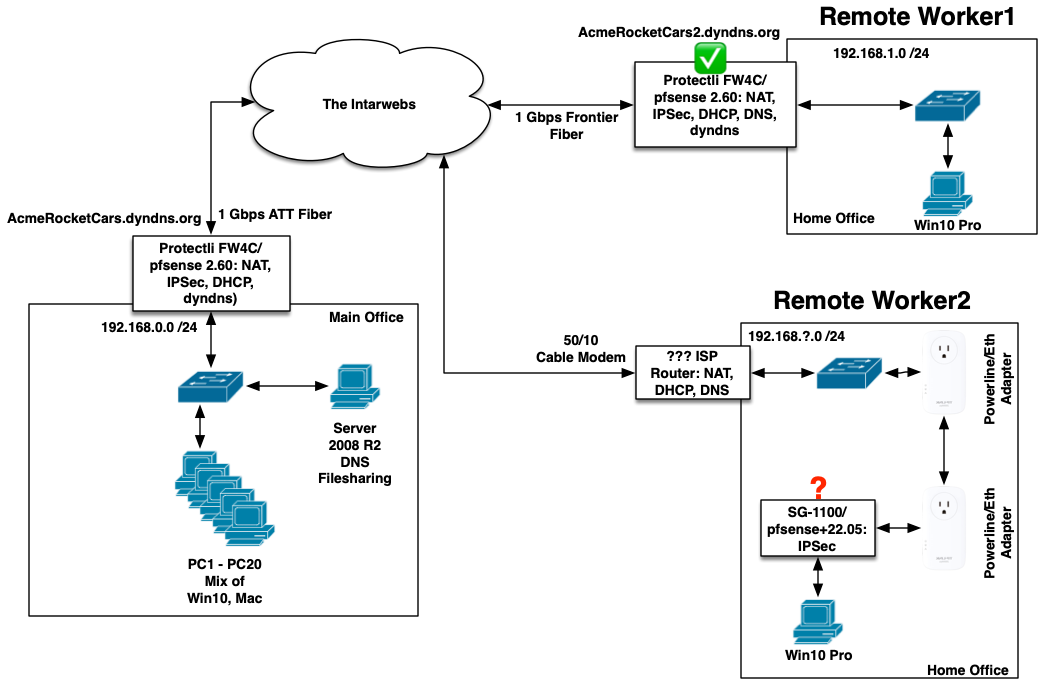
Can I put a pfsense box (SG-1100) inside Remote Worker 2's house, behind his generic ISP router, and establish a tunnel for that one PC?
-
Do I connect the WAN port on the SG-1100 to the remote LAN?
-
Do I use the ISP router's address as the default Gateway?
-
Do I need to port-forward anything in the ISP router if the SG-1100 can initiate the tunnel?
-
Is it a problem if the default LAN in Remote2 is either 192.168.0.0 or 192.168.1.0, e.g. conflicting with any of the other connected LANs?
Setting up a software IKEv2 client in Windows 10 at Remote 2 has not been successful, and I've wasted enough hours to want to try something else, and I have the unused SG-1100 lying around anyway.
I do not understand WireGuard or OpenVPN well enough to want to learn something new right now, but I have set up several IPSec tunnels successfully, so I have a preference to try this if it will work.
Thanks!
-
-
@thewaterbug I have IPSec Site-to-Site where ONE of the sides is behind NAT. No problem at all.
Just initiate the connection from the side behind NAT. Nothing extraordinary to configure. -
@maverickws said in Site-to-Site IPSec w/one side behind NAT?:
@thewaterbug I have IPSec Site-to-Site where ONE of the sides is behind NAT. No problem at all.
Just initiate the connection from the side behind NAT. Nothing extraordinary to configure.Once the tunnel has been initiated by the pfsense inside Remote2 and the tunnel established, could a host inside Main Office be routed out to the internet through Remote2, e.g. so the Geo IP location would identify as being from Remote2?
-
@TheWaterbug
If it's a policy-based IPSec there is no possibility to route certain hosts over it, you would only be able to route all upstream traffic over the VPN.
If it's a VTI you can do this.