Questions about setting up a more secure home- and small business network
-
Hi all,
Currently I have a small home network, all connected to each other by a Synology RT2600AC Router, and every device can connect / talk to each other. I know this is not a secure setup, so I'm planning to do some big maintenance on my network. (With security and management in mind)
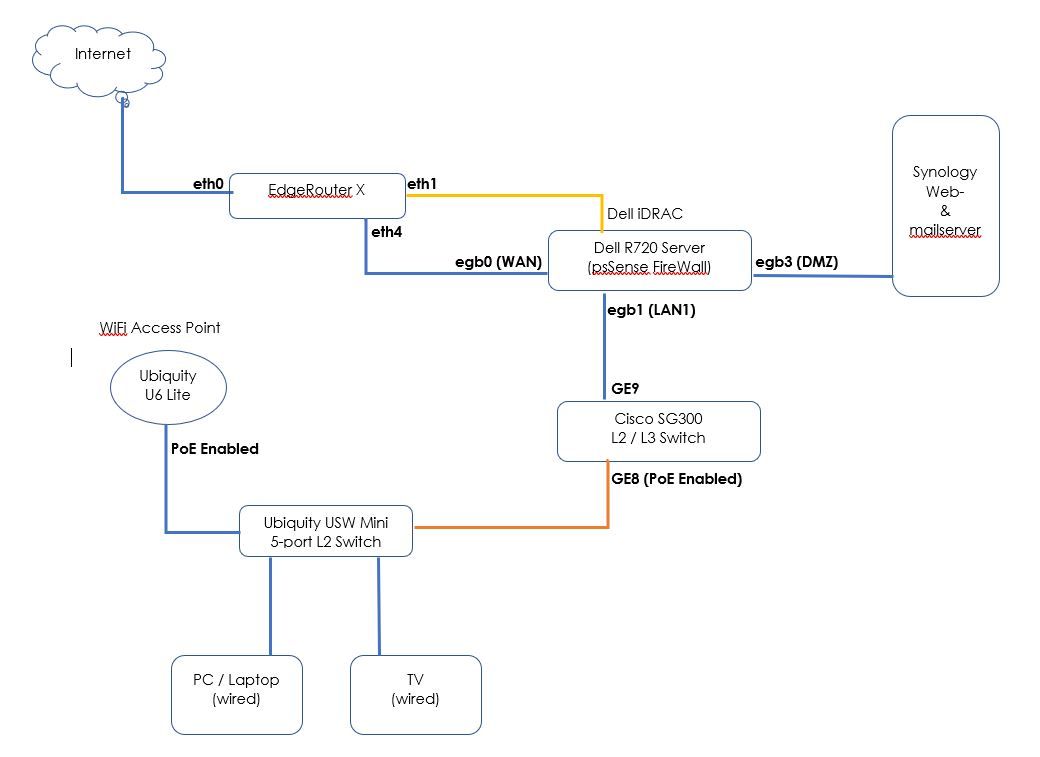
Attached I have made a scheme on how I want to setup thing.
basically, my ISP internet connection enters the EdgeRouter X and will be forwarding all traffic to the main pfSense router / firewall.
I have setup and old Dell R720 Server for my pfSense (way overkill I know but just to experiment with) and I want to control the Server by the iDRAC management port by creating a VPN connection to the EdgeRouter X so I can manage it even when the pfSense firewall is down.
(With iDRAC I can even remotely shut down, reboot or login to the console as if I were directly on the Server).The second thing is I have a Synology Web- and mail server connected to a network port of the Dell server and configured it as a DMZ zone. This way this Server will only have access to the internet and won't be able to connect to any of the other LAN's or VLAN's.
From the Dell Server I have a (trunk) connection to a Cisco SG300 Switch.
From here I will distribute my LAN network, including PoE devices such as a Unify U6 Lite Access Point. In the future I also might connect a second Synology DiskStation or a second Server to the SG300, but for now there's not much to it.I want to setup the following VLANS:
VLAN10 - Management / Server (LAN Only)
VLAN20 - Main WiFi network (WiFi Only)
VLAN30 - Guest WiFi (WiFi Only)
VLAN40 - IoT Devices / Security Cams (WiFi & LAN)Now, my questions are:
- Would you guys think this is a 'good' or logical setup? Or would you, for better security or ease of management, change anything of this setup?
- Which device would be the primary DHCP Server? Would I use the pfSense as DHCP server or better to use the SG300?
Is there a good place to start finding information on how to get started with creating such a home lab setup? I mean with YouTube or other documentation?
Love to hear your thoughts about this!
-
First I would drop the EdgeRouter. It is as likely to go down as pfSense. With the EdgeRouter you are going to end up double NATed and you are adding complexity.
I would have pfSense do DHCP. pfSense can be the DHCP server for LAN1 and DMZ, the Cisco cannot unless the DMZ is logical, not physical as shown.
Otherwise looks fairly typical to me.
-
-
@johnpoz @AndyRH
Thanks for the reply!I have drawn the EdgeRouter in so I could remotely take over the Dell Server by its iDRAC interface, in case the Server is down or pfSense has a problem.
The iDRAC interface will work even when the Server is powered off and by logging into the iDRAC I can remotely power up/down the Server.
Plus I can have a terminal window as I was in front of the physical Server.But maybe there is a better way of having this control over the Server, preferable with bypassing the pfSense firewall itself?
-
@stef_r please tell you don’t have idrac exposed to public internet you vpn into the edge? Or you have it locked down to source ip. Or you ssh in to edge with public key then over to the idrac??
-
@johnpoz said in Questions about setting up a more secure home- and small business network:
@stef_r please tell you don’t have idrac exposed to public internet you vpn into the edge?
I am aware that exposing the iDRAC interface to the public isn't a smart way to do it! :-)
So yes, I have restricted access for only one trusted IP address and only through the VPN connection through the EdgeRouter.