Source IPv6 Address in Multi-WAN is WAN address, not actual LAN IPv6 address?
-
Re: IPv6 WAN IP showing up on 'whatismyip' type sites?
Wanted to bring this up again to see if anybody might be aware of a resolution or at least a few things I could check. Fast forward from my original post (over two years ago), I am now on completely different hardware and v23.01.
The issue is that my source IP address on the public Internet appears to be presented as my actual WAN IP and not the public, static address from my /48 IP on my LAN network -- as if there is some sort of NAT going on like w/IPv4.
I run a multi-WAN setup with a fiber connection on my 'WAN' interface (running dual stack v4 and v6, static IPs with a static /48 routed to me). My 'WAN2' (backup) is a cable modem, and I am utilizing an HE.net Tunnelbroker configuration to 'NPt' my /48 so I don't have an IPv6 outage or become forced to re-IP my IPv6 addresses on my LAN in the event my WAN interface goes down.
I am using Gateway Groups; if I force-down my fiber v4 and v6 gateways, I actually don't get this problem -- when it re-routes my v6 traffic through my HENET tunnel, I can see that my IPv6 address (on the whatismyIP-style sites) become 'translated' bits of my /48 reflect that of the /48 routed to me by HE.net, and the rest of the address is my actual client machine's IPv6 address (not the HENET tunnel IP, or WAN/WAN2).
Between my original post and mid-2022 I've upgraded to different hardware but performed a fresh install and this behavior still persisted. I've also been on 23.01 for a few weeks now and it's still there, I just don't know why. It's not causing any problems per-se, but I'd like to understand why it's doing it if anyone could provide some guidance.
-
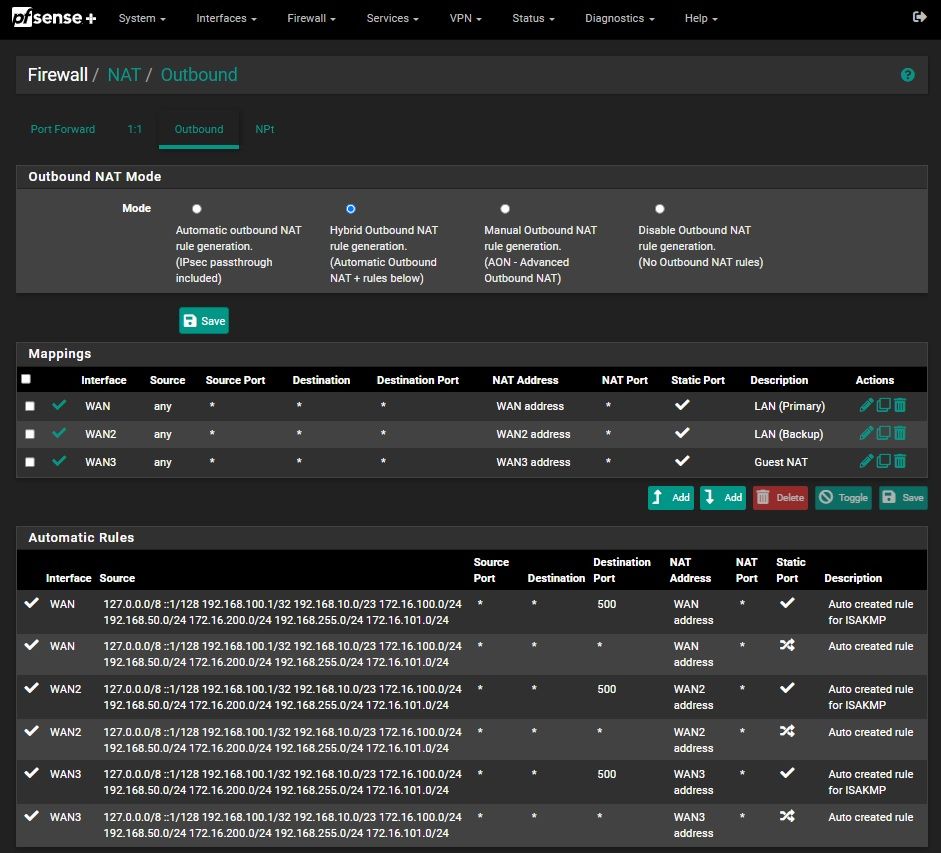
@inferno480 Please show a complete screenshot of > Firewall > NAT > Outbound .
-
@bob-dig
-
@inferno480 Ok, so what is the address family in those three manual rules?
It looks like you are actually NATing IPv6 on your WAN-address. So pfSense does what you told it to do.
The next question would be, why have you created these three rules. I would say, delete them all, they are not needed. -
@bob-dig Interesting, I thought this was all just for IPv4. Glad it was something easy, I will change these to just be IPv4 and that should resolve it, thanks.
But the reason was for the "Static Port" feature -- in my past experience, if you didn't enable that, voice communication apps w/console gaming (Sony PlayStation) would not work right and complain about other players being behind strict/Type 3 NATs, etc.
Will this interfere with my ability to use my HE.net /48 as a backup through WAN2? i.e. would I still need to enable Outbound NAT for IPv6 on that interface?
-
@inferno480 said in Source IPv6 Address in Multi-WAN is WAN address, not actual LAN IPv6 address?:
Will this interfere with my ability to use my HE.net /48 as a backup through WAN2? i.e. would I still need to enable Outbound NAT for IPv6 on that interface?
No, the outbound NAT is only needed for IPv4.
Also I would try to narrow down that static outbound NAT for IPv4 to only some IPs, like your playstation or phonebox.
-
ehhh, so I made the config change and it worked fine, but some time after I made the change (maybe an hour?) my pfSense system crashed and rebooted with a kernel panic/page fault :-/
(haven't had that happen on me ... ever I think? and I've been a longtime user)
Basically I just set my manual Outbound NAT rules to IPv4 only, and only applicable to one of my internal subnets and everything seemed fine until it suddenly crashed. I did check the General and System logs and nothing useful or noteworthy was found there. Maybe the attached debug files are useful to somebody, though (I censored my info)