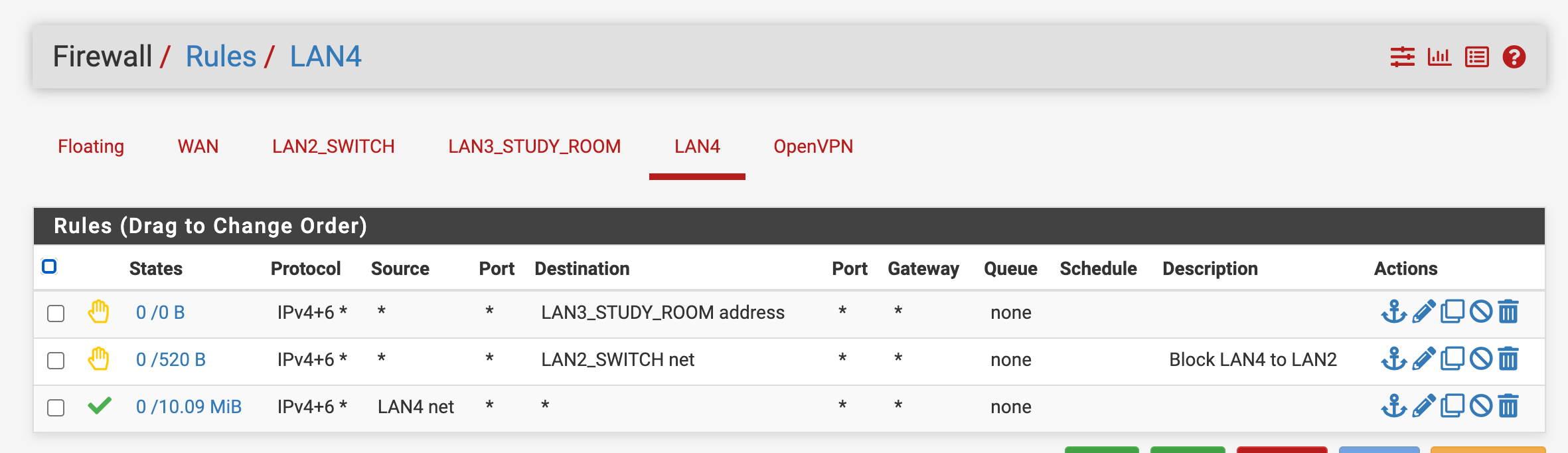
Simplest rule to block LAN4 from accessing LAN2/LAN3
-
Hi guys. Quick question about blocking LAN4 from accessing LAN2/3. Here's my network setup:
- WAN - Internet IP
- LAN2 - 10.0.0.0/24
- LAN3 - 10.0.1.0/24
- LAN4 - 10.0.2.0/24
LAN2 and LAN3 are assigned to home network, LAN4 are used for smart devices. I'd like to block anything in LAN4 from accessing LAN2/3, but allowing LAN2 to access LAN4(thanks to the stateful firewall in pfSense).
Currently, in the firewall rules setting of LAN4 I have two rules, one for LAN2 and one for LAN3, and it worked as expected.
Is there a way to achieve the same effect with one rule? Thanks!
-
@left4apple You could create an alias with the LAN2 and 3 networks in it. Just have to update it if you add LAN5.
Consider blocking from LAN4 net to pfSense (“this firewall” alias) port 22/80/443.
-
@left4apple said in Simplest rule to block LAN4 from accessing LAN2/LAN3:
Is there a way to achieve the same effect with one rule?
While sure you ca do this via the mentioned alias.. What is wrong with 2 rules - do you think it slows down the firewall? Do you feel your list of rules is so long its hard to read?
You have the rules in place already - what is the advantage of spending time creating an alias that has lan2 and 3 in it just to remove these rules and put in one with an alias - sounds like more work for something you already doing anyway with no real advantage, other than if you at some point add another vlan you would just add it to the alias and not create another rule.
What is the point of the rule with IPv6 on them - does your lans have IPv6 on them already? If so you will need to make sure you put those in your alias.
Your first rule there to lan3 is only to the address, not the network. Why do you have source as any? Do you have anything other than lan 4 using this interface. Your blocking, by default if it wasn't lan 4 it would be blocked with your one any rule there on the end, because lan 4 is not the source. Its a bad idea as well to use a network you have hosts on, as a transit network.. So the * as source doesn't really make a lot of sense.
If your goal is blocking lan 4 from going to your other vlans - why not just make a rfc1918 alias that has all the rfc1918 space in - this way in the future if you make some other vlan with say 192.168 or 172.16-31 they would be auto blocked, etc..
As @SteveITS correctly points out if your goal is blocking this lan4 from getting to the rest of your network, you might want to block it from access your pfsense admin ports. The use of the "this firewall" rule would also include your wan IP, which is public most most likely and not rfc1918.
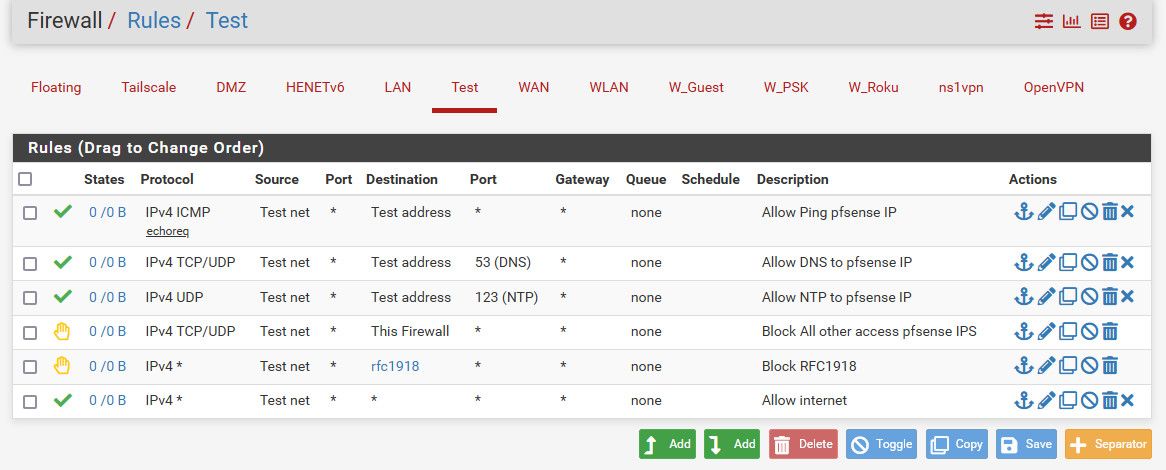
Here is an example of a locked down vlan, say iot stuff..
-