Site to Site VPN - Established and 'Installed'/Connected
-
I am having an issue with my IPsec Site to Site VPN. The connection Establishes and shows as 'Installed' (which I assume is 'Connected'), however, I am not able to ping/communicate with the other site. I have the latest version of pfSense at both ends (2.6.0). Each pfSense box has a /29 block of Failover IP's, however, IPsec is using the standard WAN interface.
I have followed the official NetGate/pfsense documentation on setting up an IPsec Site to Site VPN with a Pre-shared Key. DPD is enabled.
The SAD's are matching on both ends.
I am allowing 500 and 4500 UDP on the WAN interfaces on both ends and have 'Allow All' and 'Any' (for testing) on the IPsec interfaces in the Firewall settings.
IPsec Status on the Initiator side:
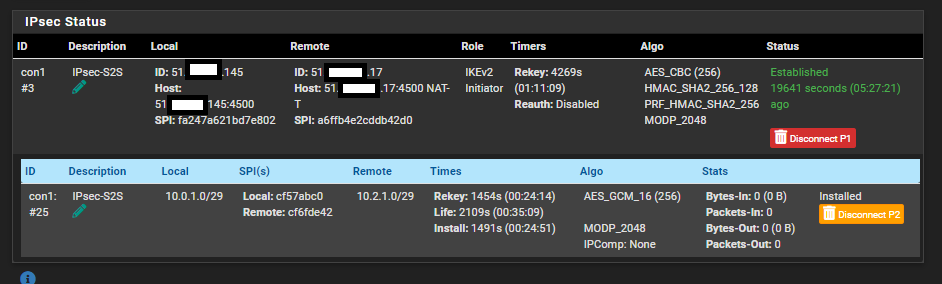
I have enabled logging on all of the IPsec related rules, however, I am seeing absolutely no traffic being passed either on the WAN interface, or the IPsec interfaces, both ends.
This is the output of
ipsec statusall.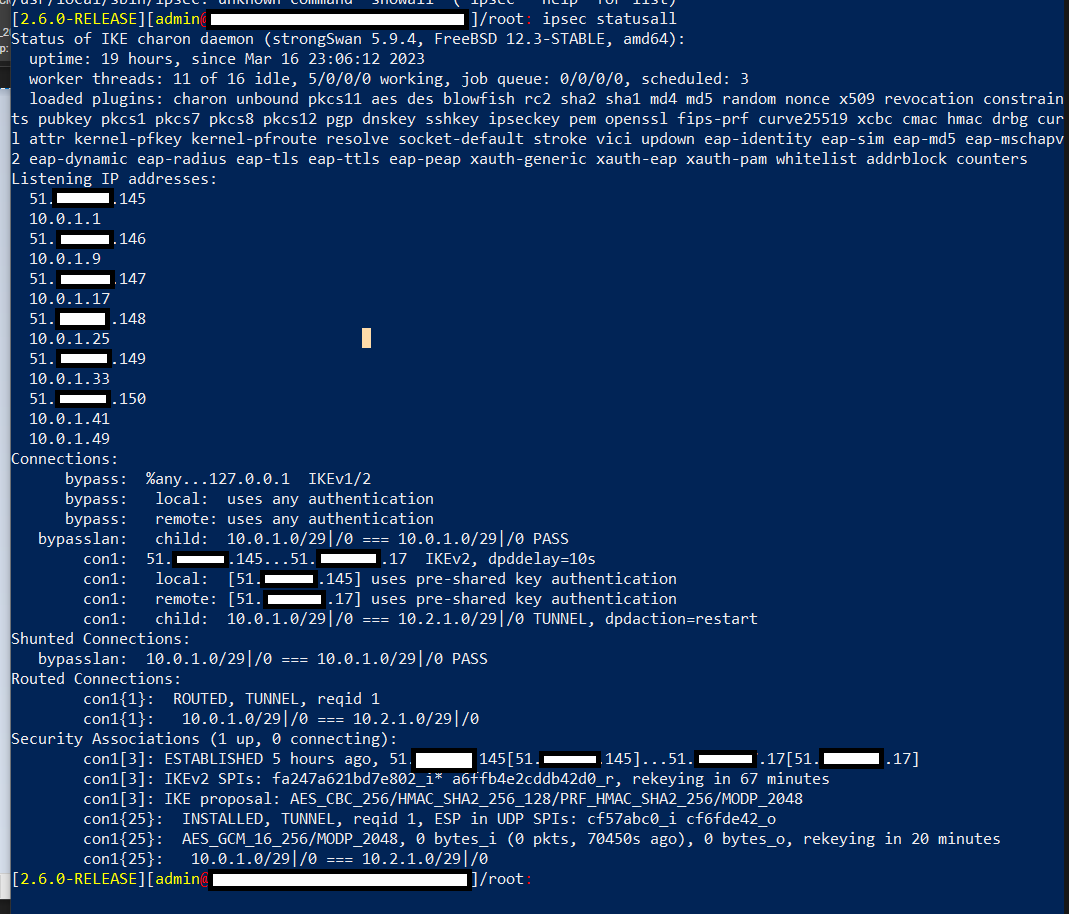
EDIT: Just to follow up... I have rebooted... many times.
-
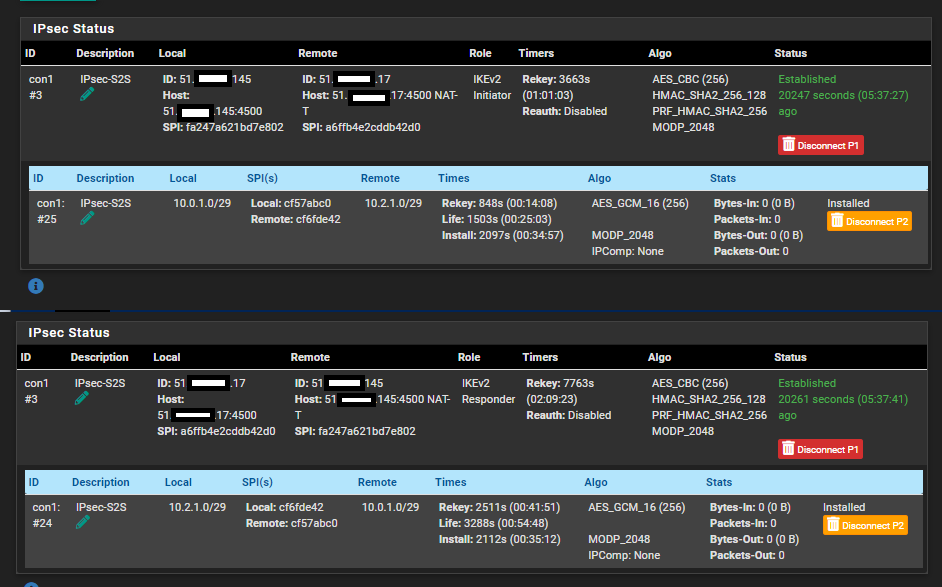
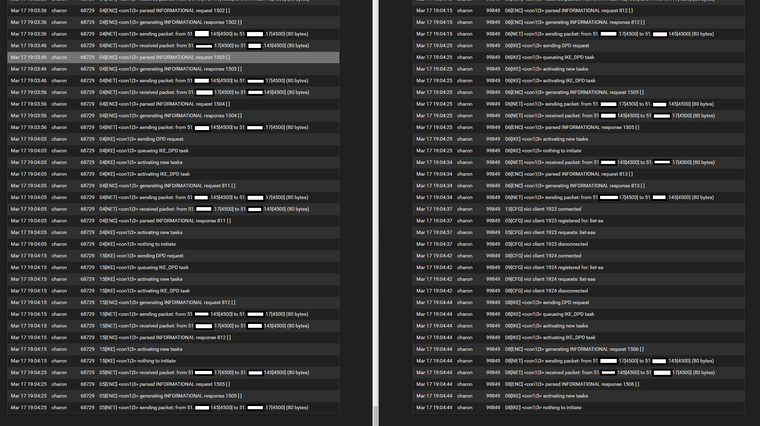
Following up with my P1 and P2 from both ends.
IPsec service system logs (Left - Initiator | Right - Responder):
Firewall > IPsec (Left - Initiator | Right - Responder):

Firewall > WAN_UPLINK (Left - Initiator | Right - Responder):
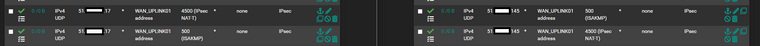
NAT Rules:
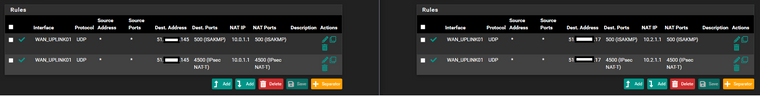
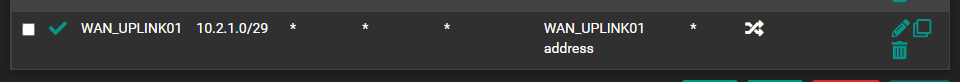
Initiator Outbound NAT rule:
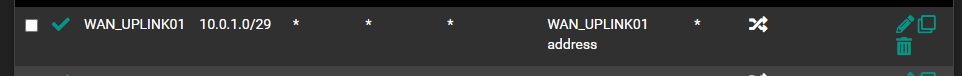
Responder Outbound NAT rule:
-
Hi
The screenshots show that for some reason traffic does not get into the tunnel ( from both sides ) . The traffic counters are 0.To begin with , if I were you , I would check the rules on the Lan interface that
1 on the initiator's side - traffic is allowed for the network 10.2.1.0/29
2 on the responder's side - traffic is allowed for the network 10.0.1.0/29It should also be remembered that traffic from hosts will get into the tunnel
10.0.1.1 -10.0.1.6
10.2.1.1 - 10.2.1.6and I also don't understand the Nat settings (in my opinion, in the case of an Ipsec tunnel, such settings are not needed for Nat Outbound)
-
@konstanti Hi, thanks for coming back to me.
I have an Network Alias with all of my subnets, on both sides, attached to the Alias.
I have Allow All for the alias networks.