problems with nat
-
Hi, I'm trying to expose a DVR behind the firewall. From documentation and from settings of previous firewall I need to forward port 8080 and ports 4250-4254 to DVR's IP address. I made the nats and firewall rules but no response from DVR. From firewall logs I can see that rules are accepted. Other NAT's like RDP are working without problems. On the previous firewall the DVR is exposed as virtual server with the same ports NAT and works.
Any idea of what can be wrong?
Thx -
@zpj61 said in problems with nat:
Hi, I'm trying to expose a DVR behind the firewall. From documentation and from settings of previous firewall I need to forward port 8080 and ports 4250-4254 to DVR's IP address
First things first.
You shouldn't do that.
NAT is old, not save, and when it works for you, it will backfire.The good way of doing things is : you need just one firewall rule, it should let in OpenVPN traffic to your OpenVPN server. This could be the OpenVPN server on pfSense.
@zpj61 said in problems with nat:
I made the nats and firewall rules but no response from DVR.
That phrase probably contains the asnwer.
=> because, if the DVR is a good one, it will not accept connections from other then it's own local network. Like 192.168.1.0/24
Accepting connections from 'all over the planet' would be a security risk.
Most probably you can over ride that on the DVR (shooting in the foot is permitted, but you have to trigger that situation yourself )
For example, my 10 year old DAHUA 16 channel coax does not want me to connect to it from the Internet. If it could, they couldn't sell it to companies where security is a thing.@zpj61 said in problems with nat:
Other NAT's like RDP are working without problems.
This somewhat underlines what I was saying above.
Even (microsoft) RDP, out of the box, does not accept from anything else as its local network (LAN) - see for example another post, posted today.
It's the same thing.@zpj61 said in problems with nat:
On the previous firewall the DVR is exposed as virtual server with the same ports NAT and works.
So, it was working before ?
Was the LAN the same ? The IP is the same ? Gateway IP (pfSEnse) is the same ?
Is there a protection that is MAC based ?You can test your NAT setup with the classic Troubleshooting NAT Port Forwards.
-
Hi Gertjan,
I'm keeping the same configuration used before, except changing the firewall, which is the default gateway also. The lan is the same, the public IP is the same, there is a lot of mobile phones already configured with an app for displaying cameras on DVR that are pointing to this public IP and using vpn is not possible for this reason. I will check the DVR configuration but the person who installed it told me that there are no blocks on incoming connections. -
Then "Troubleshooting NAT Port Forwards" is your way out.
For example : on the WAN firewall page, do you see incoming traffic on the rule(s) that forward to your DVR IP ?
Like :
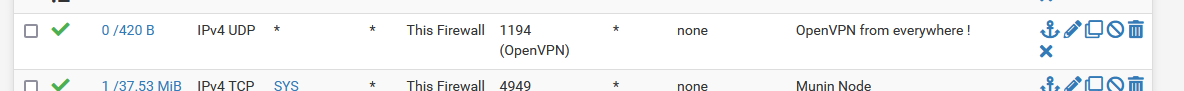
The counters 0/420B tell me that traffic is coming in.
0/0 means : nothing reached pfSense.If not : the issue is up stream, for example : your ISP router, if there is one ? Has it been natted to the WAN IP of pfSense ?
etc etc.
-
@zpj61 said in problems with nat:
I made the nats and firewall rules but no response from DVR
To continue what @Gertjan is saying - the troubleshooting link will point you to where your problem is fairly quickly..
First step really is to validate pfsense actually seeing traffic - quick way to make sure traffic gets to pfsense wan, so it can forward it is using a tool like can you see me . org.. Send some traffic to that port 8080, while you sniff on pfsense wan.. Do you see it hit pfsense wan?
I don't even need a port forward or firewall rules setup to validate traffic from the internet can talk to my wan IP on a port.. Here I just sent some 8080 traffic from can you see me . org, and pfsense sees it on its wan via a packet capture (diagnostic menu)
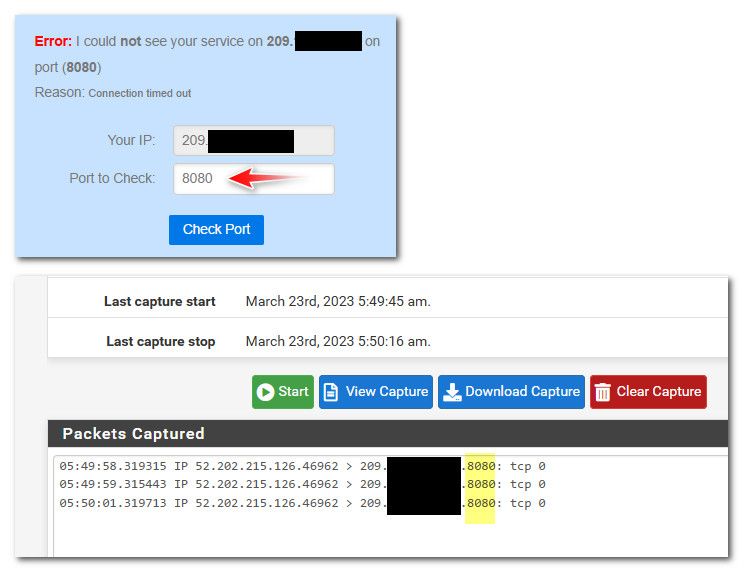
If you do that test, and you don't see the traffic hit your wan - then it would be impossible for pfsense to forward it, because it never sees it in the first place.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
Hi,
as I wrote in the first post loooking at firewall's log I can se then public Ip I'm using to try to connect, the rule I accepted (green check), the incoming counter in incrementing but no outgoing traffic. The request reaches pf but it seems that the problem is after the firewall. -
@zpj61 said in problems with nat:
he request reaches pf but it seems that the problem is after the firewall.
Ok did you sniff on pfsense lan side interface - do you see it sent to the where you forwarding.
-
Never done this before, I know pf offers packet capturing, what is the best way to do it?
-
@zpj61 under diagnostic menu, packet capture - pick your interface, and then any restrictions you want to use for the capture. Like the IP in question, or the port, etc.. If you want to limit the capture to specific number of packets, it defaults to 100, 0 is unlimited and will run until you stop, etc.
In the above example I set the port to 8080, because that was the traffic I was interested in. And didn't want all the other noise hitting my wan.
-
You could also check this by fitering for the public IP you're testing from in the state table (Diag > States). You should see the incoming state on WAN with the NAT applied and an outgoing state on the internal interface the DVR is connected to.
Steve