quick question regarding inboud/outbound(which is which) interfaces after configuring WireGuard
-
I have configured Wireguard on pfsense so that all my clients are begind a vpn (VPN provider is AirVPN). I followed this guide to set this up
https://www.comparitech.com/blog/vpn-privacy/pfsense-wireguard-setup/
I now have a new interface - the AirVPN_Wireguard_Interface.
I am setting up pfBlockerNG and in the set up wizard have to select the following
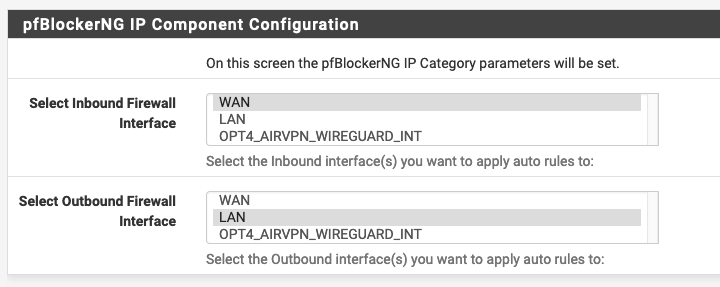
Normally Inboud Firewall interface would be the WAN, but I suppose now it is the Wireguard interface? Can somone please confirm?
Outboud Firewall interface I assume is still LAN?
I hope somone can confirm, many thanks!
-
If all your traffic is going over WG VPN then that is the inbound interface instead of WAN (which carries the encrypted VPN traffic) yes.
However unless you are forwarding traffic across the VPN nothing comes in there anyway because there's no public route to the VPN private IP.
The rule governing outbound traffic is still on the LAN.
Steve
-
@stephenw10 said in quick question regarding inboud/outbound(which is which) interfaces after configuring WireGuard:
If all your traffic is going over WG VPN then that is the inbound interface instead of WAN (which carries the encrypted VPN traffic) yes.
However unless you are forwarding traffic across the VPN nothing comes in there anyway because there's no public route to the VPN private IP.
The rule governing outbound traffic is still on the LAN.
Steve
Thanks for confirming. Sadly it looks like pfblockerNG is unsable to download any lists. Do i have to make explicit rules to allow it? I remember not having this problem prior to setting up the Wireguard VPN.
-
Depends how the VPN is configured. Connections from the firewall itself cannot be policy routed so they always use the system routing. If you have set the system default route to be over the WG VPN it will be trying to use it.
-
@stephenw10 said in quick question regarding inboud/outbound(which is which) interfaces after configuring WireGuard:
Depends how the VPN is configured. Connections from the firewall itself cannot be policy routed so they always use the system routing. If you have set the system default route to be over the WG VPN it will be trying to use it.
I do indeed have the default gateway set as the Wireguard VPN. Is that causing the issues?
edit: I think it is the issue indeed. I just selected the Default Gateway to Automatic and the feed download fine. I wonder what are the implications of this, as I want to make sure that my traffic goes via the Wireguard gateway.Esentially I would like to avoid my clients not being behind the vpn.
-
Well for some reason traffic from the firewall itself is failing. Maybe you have a rule blocking it? Something incorrectly NATing? Check the states while trying to download lists.