Configure FreeRadius & multiples ssids <> users
-
@dvb If you run radsniff -x and auth from two different SSIDs what is the output?
You might be able to add a CHECK-ITEM to user setting in FreeRadius.
For example I have a user defined that can only connect via IPsec as I have the following set as a CHECK-ITEM:-
NAS-Identifier == strongSwan
My Aruba InstantON shows the VLAN & SSID listed as:-
Aruba-User-Vlan = 2
Aruba-Essid-Name = "WiFi RADIUS"Why use Radius auth for your guests?
Also why for IOT, most IOT stuff won't support WPA2 Enterprise.
-
@dvb Yeah, you probably want to add a check-item on users in freeraduis for called-station-identifier (SSID name). You will need to lookup how to make freeradius ignore the AP Mac-address part of the returned ID, but this is the common industry way of filtering this info - so I’m sure there’s a simple way to do it.
https://mrncciew.com/2013/07/22/called-calling-station-id/
However: Since you are authenticating users for access to your SSID’s, why not only have one SSID and let Freeradius return the VLAN the user should be assigned to. That way you have no need to filter checks on users, users are automatically assigned to the correct VLAN, and you only have to broadcast one SSID.
-
@dvb …. And depending on how you want to solve the guests situation, you could either have dedicated SSID for them, or let them use the same SSID as everything else - only, you’ll need to have radius authenticate everyone then - but return the guest VLAN ID for all “not registered” users/devices.
Alternatively, your Accsspoints might have a “default VLAN” feature, where it will assign users to a default VLAN in case they fail radius authentication. -
@keyser To be honest the easiest thing to do with the guest Wi-Fi is use a qr code that the scan with their devices.
It stops people sitting outside the house using the guest Wi-Fi.
-
@nogbadthebad said in Configure FreeRadius & multiples ssids <> users:
@keyser To be honest the easiest thing to do with the guest Wi-Fi is use a qr code that the scan with their devices.
It stops people sitting outside the house using the guest Wi-Fi.
Depends on whether he uses WPA(3)-PSK or WPA(3)-Enterprise. In PSK mode, the guest would still need to know the preshared key.
-
@nogbadthebad But yeah, I agree, if he’s using WPA(3)-Enterprise, the better solution is to stand up a dedicated Guest SSID
-
@nogbadthebad said in Configure FreeRadius & multiples ssids <> users:
@dvb If you run radsniff -x and auth from two different SSIDs what is the output?
Sorry I don't know this tool. Could you please give me the right syntax ?
You might be able to add a CHECK-ITEM to user setting in FreeRadius.
For example I have a user defined that can only connect via IPsec as I have the following set as a CHECK-ITEM:-
NAS-Identifier == strongSwan
My Aruba InstantON shows the VLAN & SSID listed as:-
Aruba-User-Vlan = 2
Aruba-Essid-Name = "WiFi RADIUS"Why use Radius auth for your guests?
It's more for learning. I plan to give a user/pass to all my friends and monitoring / test system (bandwith limitation etc..).
Also why for IOT, most IOT stuff won't support WPA2 Enterprise.
You've right. I thought using automatic mac authentification, but it seems device must nevertheless supports 802.1x protocole. Then I plan to connect iot via wpa2. Is it correct ?
@keyser said in Configure FreeRadius & multiples ssids <> users:
@dvb Yeah, you probably want to add a check-item on users in freeraduis for called-station-identifier (SSID name).
Exactly.
You will need to lookup how to make freeradius ignore the AP Mac-address part of the returned ID, but this is the common industry way of filtering this info - so I’m sure there’s a simple way to do it.
https://mrncciew.com/2013/07/22/called-calling-station-id/
Il will take a look but it seems a little complicated.
However: Since you are authenticating users for access to your SSID’s, why not only have one SSID and let Freeradius return the VLAN the user should be assigned to. That way you have no need to filter checks on users, users are automatically assigned to the correct VLAN, and you only have to broadcast one SSID.
I tried this and it works. But for better monitoring (just personal choice) I prefer to see users in different ssids
@nogbadthebad said in Configure FreeRadius & multiples ssids <> users:
@keyser To be honest the easiest thing to do with the guest Wi-Fi is use a qr code that the scan with their devices.
Yes, good solution to give one same pass to all guests.
I think the better solution is to check login, and reject if it's not on the right ssid.
@nogbadthebad
Could you explain this configuration ?NAS-Identifier == strongSwan My Aruba InstantON shows the VLAN & SSID listed as:- Aruba-User-Vlan = 2 Aruba-Essid-Name = "WiFi RADIUS"I don't know how setup in pfsense/FreeRadius.
-
Re radsniff, ssh onto your pfsense box and type in radsniff -x from the cli.
You’ll see what attributes your Wi-Fi is sending when people connect with WPA Enterprise.
Basically adding a check list item, will add an extra item to check after the user ID and password.
-
@nogbadthebad said in Configure FreeRadius & multiples ssids <> users:
Re radsniff, ssh onto your pfsense box and type in radsniff -x from the cli.
loging from ssid 1 :
sudo radsniff -x ... Called-Station-Id = "mac1:DEBUGpfsense" ...loging from ssid 2 :
sudo radsniff -x ... Called-Station-Id = "mac2:rad_guest" ...You’ll see what attributes your Wi-Fi is sending when people connect with WPA Enterprise.
Basically adding a check list item, will add an extra item to check after the user ID and password.New setup for user "test" :
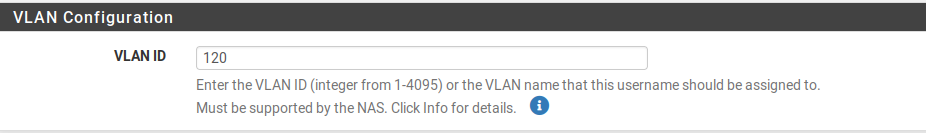
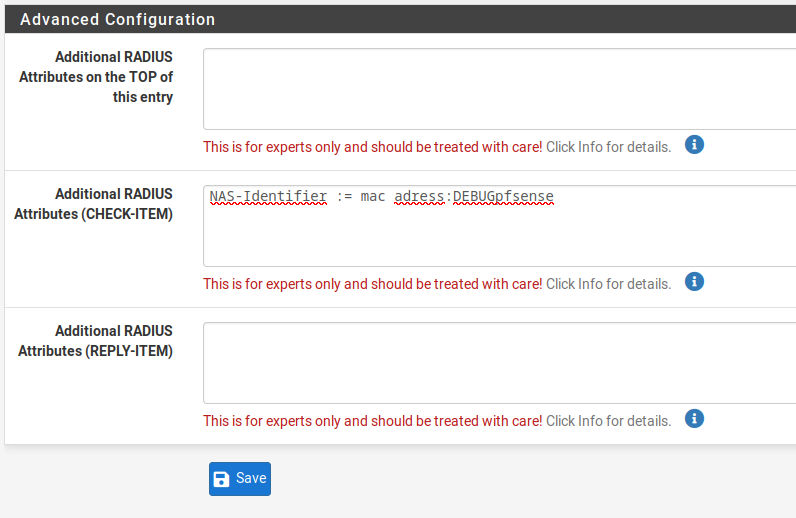
Despite adding this condition, user "test" can already connect to ssid 2. Did I missed something ? My syntax is wrong ?
[EDIT]
Same with :Called-Station-Id := mac address :DEBUGpfsense -
@dvb try removing nas-identify, best you have a look at the freeradius web site for the correct format.
-
For information, here is the right syntax :
Called-Station-Id =~ '.*:ssid_name'or in case you want to catch the complete value (ie > "mac:ssid") :
Called-Station-Id == "aa-bb-cc-dd-ee-ff:ssid_name"-> Now, user is connecting ONLY to one ssid.
Thanks a lot for helping me to fix this setup
