Multiple LAN segments accessed from single IP address
-
@jay209
You should better get a VLAN capable switch for proper network segmentation.
But yes, it would be also possible on a single L2, however, you need to assign an IP of each subnet to pfSense, which is used as gateway on the respective network devices. -
@viragomann If i go to LAN, there are options only for my current LAN segment (192.168.2.x). Should i go to Virtual IP and define there a new network segment? 192.168.100.x , for example?
LE: I just added a new virtual IP (192.168.1.1). I set its type as IP Alias. But when i ping from my computer (i have 192.168.1.12 set by hand) it does not reply back.
-
@jay209
Yes, you need to add virtual IPs of type "IP alias".Also consider to add rules to LAN to allow the desired connections. The default rule might only allow access from LAN subnet.
-
@viragomann I did the following:
I defined a Virtual IP (Type Alias), on interface LAN with address 192.168.1.1/24. This virtual IP should act like a gateway for 192.168.1.x subnet, right ?At least this is what i am trying to achieve.
Then, i go to Firewall -> Rules -> LAN: All traffic is allowed. I even created a new rule stating that from 192.168.1.0/24 there is no restriction to LAN net (this is my current LAN segment that has access to the internet).
Just to be a clear, i want to be able to access the entire /24 segment of 192.168.1.0 subnet from 192.168.2.12 .
There is something i am missing... but i can't figure out what.
-
@jay209 said in Multiple LAN segments accessed from single IP address:
I defined a Virtual IP (Type Alias), on interface LAN with address 192.168.1.1/24. This virtual IP should act like a gateway for 192.168.1.x subnet, right ?
Yes.
At least this is what i am trying to achieve.
Then, i go to Firewall -> Rules -> LAN: All traffic is allowed. I even created a new rule stating that from 192.168.1.0/24 there is no restriction to LAN net (this is my current LAN segment that has access to the internet).
Just to be a clear, i want to be able to access the entire /24 segment of 192.168.1.0 subnet from 192.168.2.12 .Your computer use pfSense as default gateway as well?
Is any of the involved devices multi-homed in both subnets?
Enable the logging in the LAN rules and check if the rules get any hits then.
Also check if there are any blocks in the filter log. -
@viragomann I just ran some tests with latest modifications.
My computer is set to get 192.168.2.7. pfSense is the default gateway.
I set the virtual ip 192.168.1.1/24. With current setting and no restriction rules on LAN i am not able to ping 192.168.1.1.
If i add 192.168.1.2 on my computer alongside 192.168.2.7, i am able to ping the 192.168.1.1.
So this seems like a routing issue and pf does not know that it should be the gateway, translating the requests from both sides.In the firewall logs i can only see messages related to lan and wan, nothing related to 192.168.1.1.
Please bear with me as i am still trying to learn. Maybe i misconfigured something ?
-
@jay209 said in Multiple LAN segments accessed from single IP address:
I set the virtual ip 192.168.1.1/24. With current setting and no restriction rules on LAN i am not able to ping 192.168.1.1.
192.168.1.1/24 is the IP alias on pfSense?
For this to work, it's only necessary, that pfSense is the gateway on the computer (even the LAN address) and that there is the default LAN rule still in place allowing any from LAN net.So this seems like a routing issue and pf does not know that it should be the gateway, translating the requests from both sides.
pfSense is a router by default. It forwards any packet according to its routing table, as long as a filter rule allows that.
If i add 192.168.1.2 on my computer alongside 192.168.2.7, i am able to ping the 192.168.1.1.
If you do this, both are in the same L2. I guess that only this makes the destination device happy. My suspect is, that it blocks the access otherwise.
So maybe you can disable its firewall for testing and configure it accordingly later if that's the reason. -
@jay209 what is the goal of this exercise? Are you attempting to migrate to new IP space? Running multiple L3 on the same L2 is not good practice, and provides no real security.
If your goal is actual segmentation of your network, you should either physical create different L2 networks for your different L3 networks, or use vlans for your isolation.
It works for migration from network space A to B for example - but it is not a good setup for long term.
-
@johnpoz The goal is to learn about network and security. For now, the short term goal is to simplify the access to some devices i use. Later on, the goal is to segment the network using managed switches and vlans.
But for now i want to achieve 1st goal: accessing multiple devices (different subnets) from a single computer using a default ip (192.168.2.7 for my computer).
I know it is not secure but the goal is for me to learn how to interconnect these subnets using pfSense.We can agree on the idea that i can change the ip adress of the devices but these devices, once tested and configured, will be sent in other places.
Then i get a new set of devices, having same default IPs.So, it is important for me to 1st create these additional subnets in the router so i can always access the devices from my default ip.
I already defined the virtual ip for several subnets but i miss the route to them.
192.168.1.1/24 is the first of them. But as i have mentioned in earlier posts i miss something in the firewall and the new subnet is not responding to ping . I have checked the firewall logs but there is no mention about any traffic from 192.168.2.x to 192.168.1.x or reverse.Sorry for my long post but am still trying to describe as much as i can what i try to do. Because, for me doing so, will make sense and i can understand how things are working in networking.
-
@jay209 said in Multiple LAN segments accessed from single IP address:
So, it is important for me to 1st create these additional subnets in the router so i can always access the devices from my default ip.
creating a vip not really creating a new network on pfsense IMHO.. its just multiple L3 on the same L2..
If you have say lan 192.168.1.0/24 with pfsense being 192.168.1.1, and you want to have other devices on this same L2 as say 192.168.2.x/24 then you would create a vip on pfsense..
And you might have to adjust your rules to allow for that traffic that is a different netblock.. But if you put it on lan, than lan net should included the new IP range.
So here I just created a vip on my lan 192.168.14.1/24
You can see that it was added to my outbound nat. I can ping the 14.1 address of pfsense, and I can get to the internet - and viewing states while pinging 8.8.8.8 you can see coming from my PC that I changed to 192.168.14.2/24 that is on my "lan" network..
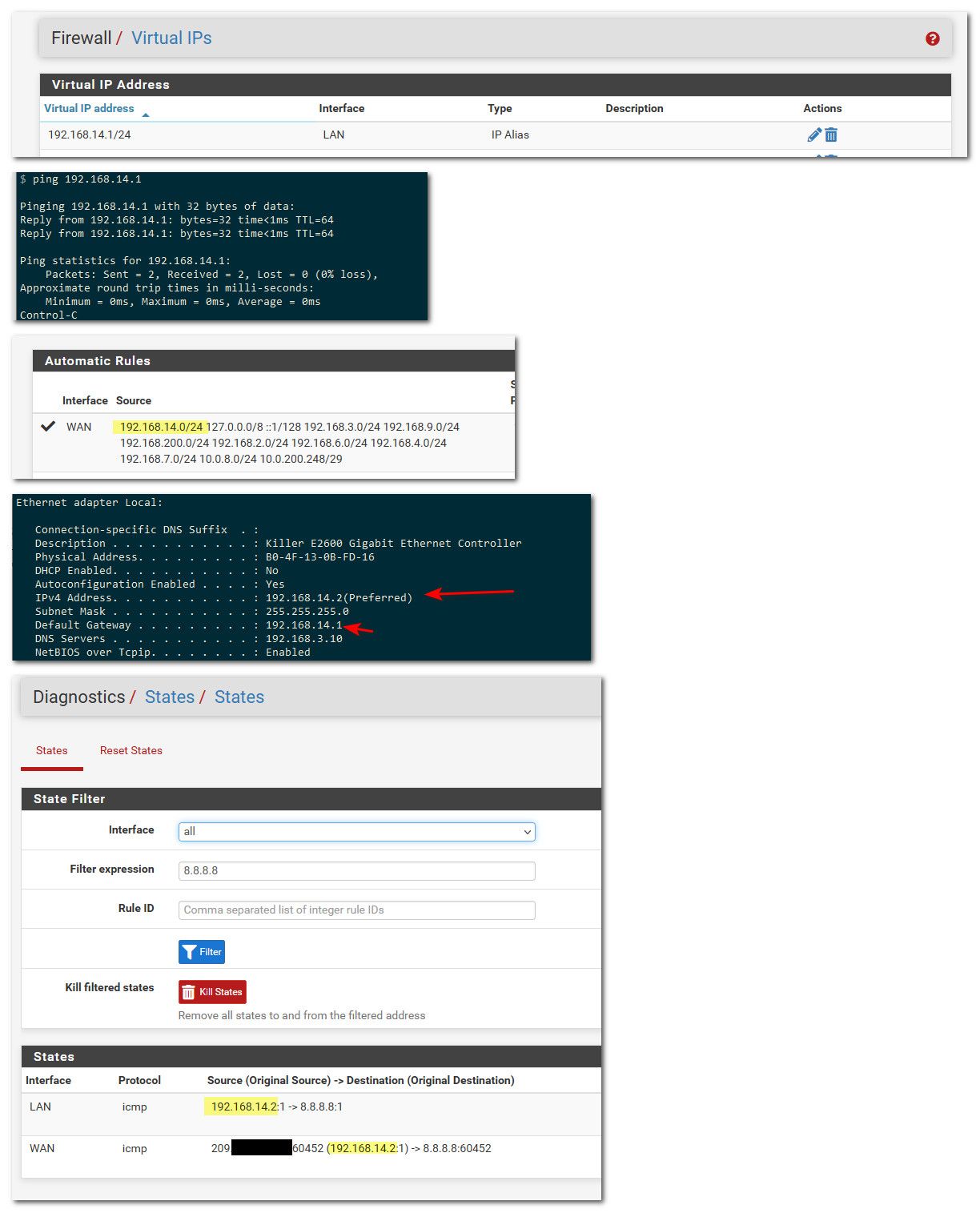
-
Guys, i am still working on this trying to configure it. I think i am doing some kind of progress. Please bear with me as today i don't have that much time. I'll come back tomorrow.
Thank you for all your advises!