NAT for IPsec Host
-
@jacksongrow
So you have a wide /16 local network defined in the P2. I assume that this also includes the IP of your app server. So I'd expect this to work anyway from the IPSec settings.I suspect that there is another reason for the issue.
Is the access to the remote site allowed by a firewall rule in pfSense?
Or more probably, is it allowed in Azure NSG (outbound) for the app server? -
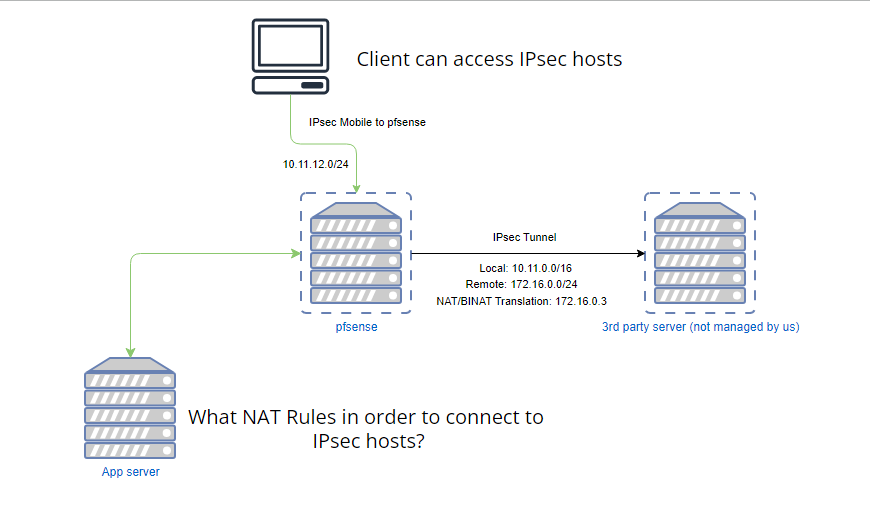
@viragomann No, the app server is not connected to the LAN of our pfsense in any way. It is not apart of the 10.11.0.0/16 subnet. It is purely an external machine that we want to trust.
Basically, I want to open our vendor's database to the public using our pfsense server, but only allow trusted IPs to connect to port 1433.
-
@jacksongrow
It's pretty hard to follow your explanations:We need this so our database (which is in Azure) can query the vendor's database
the pfsense is in Azure
The app service itself needs connection to the remote database.
No, the app server is not connected to the LAN of our pfsense in any way
Now what / where is the "app server"?
What's it's IP, network? -
@viragomann I already mentioned our app server is not connected to pfsense's LAN. The app server has a public IP.
All I want to do is port forward 1433 to a host behind the IPsec tunnel. The app server isn't relevant to the conversation. It is simply an external host.
-
@jacksongrow
So is this SQL connection encrypted? It's not recommended at all to route unencrypted SQL connections over the internet.I would rather run an IPSec client on the app server, connecting to the same server as the road warriors and go through the tunnel.
This would secure the SQL connection and also solve your access problem. -
@viragomann This is actually something I didn't consider and it appears the traffic is unencrypted. The app server is not a server, but an App Service in Azure, so there's no way to setup an IPsec client unfortunately. However, I think we might be stuck with VNet integration, but I'm not understanding how that works.
I guess that closes this issue, though!
-
@jacksongrow said in NAT for IPsec Host:
The app server is not a server, but an App Service in Azure
So you could route the connection inside Azure, however, and need not to pass it over the internet.
I think we might be stuck with VNet integration
I'm not experienced with Azure services, but multiple VNets can be peered to route traffic from one to another inside Azure. I assume, that there might be a similar function for services.
Then you could add an additional phase 2 for the app service.
-
@viragomann I got the Vnet integration working and the App Service can communicate with pfsense. Now, I want to port forward 1433 so the App Service can connect to the SQL server, but I'm still stuck with the same issue. My NAT rules don't seem to be effective.
-
@jacksongrow
So you can see already the packets from the app services arriving on pfSense on port 1433?If so simply forward them on the interface, where the connection is coming in.
In the IPSec S2S settings copy the existing phase 2 and change the "Local Network" to Address and state the IP of the app server and change the BINAT address to the designated one.
-
@viragomann Thank you for the guidance. I couldn't add a ph2 because the other end wouldn't connect, but I was able to configure the local as 10.0.0.0/8 and that covers everything we need.
The port forward ended up working for 1433 and it went through !
Thank you for your help!