Endless spam .... how to get rid of it? Is it a rule change? Is it 2.7?
-
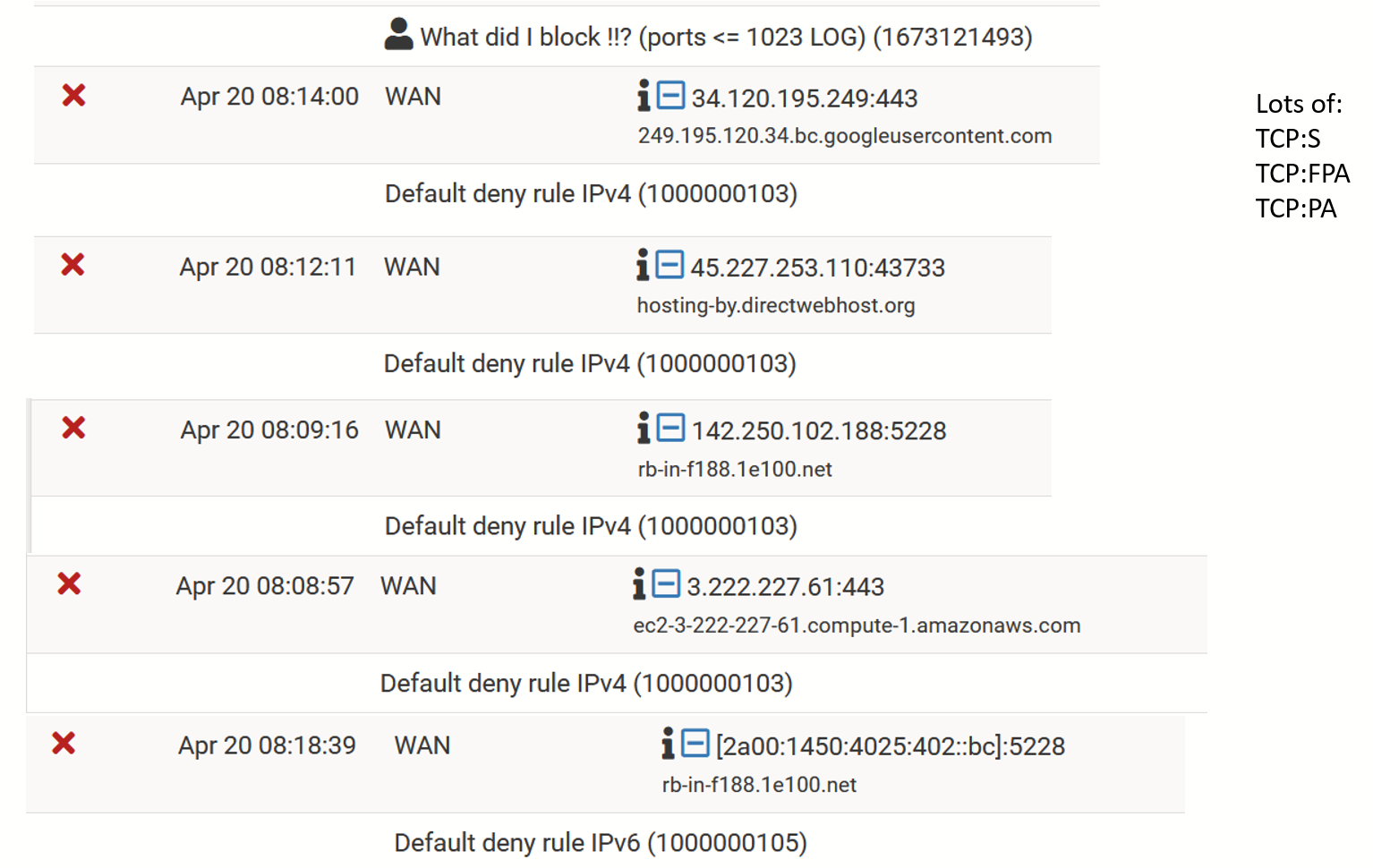
Today I noticed an endless number of spam related warnings in my firewall log. See picture.
I am not really surprised that it is there, but of cause I would like to block it and I do not want to see it in the log.
But what is causing that its in the logs now and in such enormous quantities !?
- did I unintentionally made a change, which causes the FW to generate these messages?
- is the related to the latest builds?
- is there a change in network or browser behavoir??
- is it related to the installed HA-proxy?
I simply do not know!
If some one has suggestions!
-
@louis2
You didn't block anythingAll the log listed messages was "made" by the Default deny rule IPv4.
That rule is a built-in "hidden/invisible" deny/block any any , at the bottom of every interface ruleset.This is "just" the standard "background noise / hacker probes" , coming from being connected to the internet.
I'm surprised you haven't noticed that "noise" before ....
It would always have been there, on a "standard install"AKA ... If it's not handled by one of your rules on the interface, it will be caught by the "default deny rule"
/Bingo
-
No it is not hacking, it is mainly related to data collection and marketing.
I try to block and filter as much as possible. I have not seem this behavoir, which I do not understand at the moment, for a long time.
It are really hundreds of messages flooding my log. Each example shown in the picture does not occur one's, but many times!
-
@louis2
Those messages are unfortunately : the "normal" consequence of having a device connected directly to the internet. There is absolutely nothing wrong with your setup, wrt. logging these.The good news is that pfSense is made to handle precisely that situation (and many other).
Don't worry , and as long as it's incoming traffic from the WAN (Internet), don't worry about the "Flags" you mentioned in the first post. You can't control what flags a packet from the internet has set (the bad guy can ... and will)
Relax , and be happy about how much garbage pfSense is filtering out (& logging), and thereby protecting your devices.
Edit:
If you previously have had an ISP device (L3 router) in front of your pfSense, and now have the pfSense connected "directly to the internet", an ISP L2 connection.
That could explain the "noise" you see. It has always been there , but an ISP L3 router filter it out, before it would reach pfSense.You would often get a L2 connection if you have switched to a fiber based connection.
I'll stop here, there is IMHO not much more to say on this subject.
/Bingo
-
About the "default deny rule IPv4 1000000103" :
Uncheck :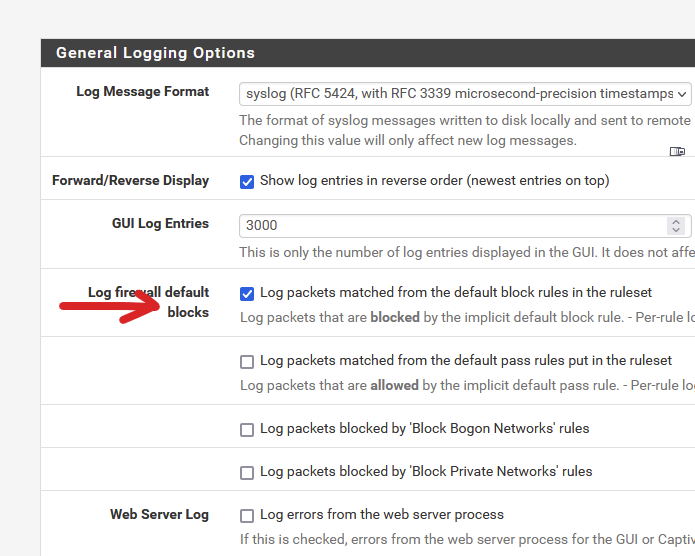
edit : I corrected the image.
and done ^^
Keep in mind : the traffic is still there, on the WAN port.
This is 'normal' as you are connected to a public network (aka : the Internet) that is accessible to many people. We don't have leave our beds to try to access your IP, or my IP, or everybody's IP.To stop it : one solution : rip out the WAN cable.
( or find an ISP that filters for you ... )@louis2 said in Endless spam .... how to get rid of it? Is it a rule change? Is it 2.7?:
I try to block and filter as much as possible
By default, the WAN firewall page is empty.
This means that there is actually one rule : the hidden default rule "1000000103".
And that one does just one thing : block all incoming connection - no exception.
And by default, it isn't logging.
So, by default, nothing to 'try'
-
I changed this setting to off
I wonder if I already did that in the past and that one of the very recent snapshot updates it ^turned on^ again. Or that I did that by accident.
I can hardly imagine, however I did access the page a couple of times to clear the logging (I made significant changes to the FW, because I am changing my internal network and added HA-proxy. -
Covering your eyes - Won't make the Tiger disappear
-
Those look more like out-of-state packets not random probing. Still normal and expected:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html
Something may be causing more states to be dropped from your table faster than expected, but AFAIK there haven't been any changes in the code that would do that, so it may be something in your config or situational. But really those are normal, servers just keep sending packets to old connections in hopes that they're still open because it can be faster than setting up new ones.