pfsense as a client not a firewall.
-
Hello
I have a bit of an odd setup and I can't find any answers online...
Modem -> tp-link omada firewall -> omada switch -> proxmox(vlan 70, 192.168.70.125) -> pfsense vm (192.168.70.11)
I've setup a vlan lan on pfsense (vlan 80 192.168.80.10)
Both proxmox and pfsense get their IP's from tplink omada.
I don't want to use pfsense as my firewall solution, I just want to play around with it for now so it's running as a VM in proxmox. Proxmox is plugged into my switch with its own vlan 70
My computer is plugged into my switch on separate vlan 10 (192.168.10.125)
In order to get to the webconfigurator I have to open a console in the proxmox pfsense vm and type "pfctl -d" to disable the pfsense firewall.
How do I set this up so I can access the webconfigurator (192.168.70.11) from my computer (192.168.20.125) while the pfsense firewall is enabled.
As soon as I enable the firewall in pfsense (pfctl -e) I get locked out of the webconfigurator(192.168.70.11) from my computer (192.168.10.125)
Thanks!
-
-
Yes, just add a firewall rule on WAN to pass that traffic.
If it's just for testing you might just pass all traffic on WAN.
Steve
-
@carsonix if you only created 1 interface in pfsense, the rules to allow web gui access would be on its wan. If you create 2 interfaces, ie wan and lan then wan has nothing open.
But why would not just access web gui from the lan side via one of your VMs or other boxes you put behind pfsense. Not sure how much play you will get on a firewall that is not actually firewalling anything.
But yea as mentioned if you want to access pfsense web gui from the wan side, just create a rule on the wan interface to allow that.
-
I currently have 1 NIC in my server
I do access the webconfigurator through WAN IP.
If I try to access webconfigurator through vlan LAN IP it doesn't work.
**I know I have to change the firewall to allow access to the webonfigurator from my PC but I don't know how or what to do. My PC is in vlan 10, Proxmox (pfsense) is on vlan 70.
Can someone please provide step by step instructions on how to allow access.**
I will be adding a second NIC I'll plug a switch and stuff into and so pfSense will be acting like a firewall to those things, but inside my network.
Once I have it figured out and know what I'm doing Ill feel more comfortable using it as my real firewall.
-
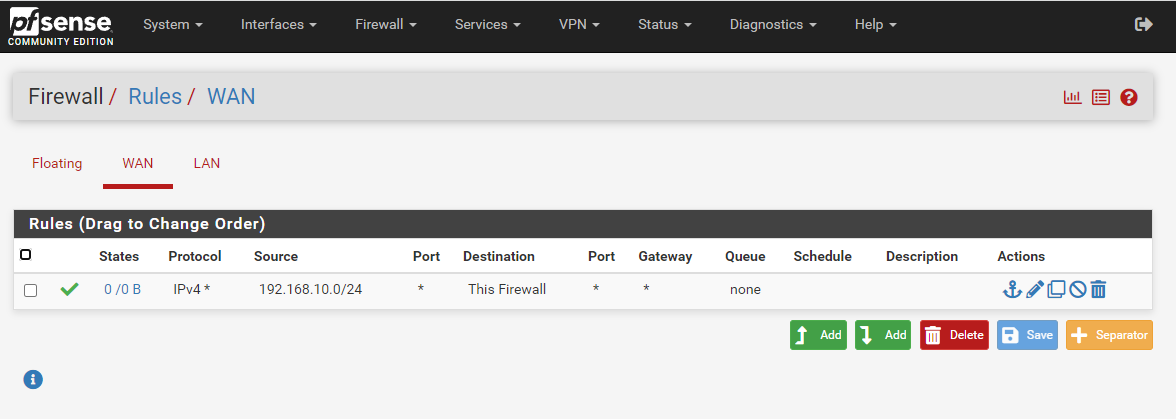
Add a PASS firewall rule on WAN with source 192.168.10.0/24 and destination WAN address on port 443.
That's assuming nothing is NATing that traffic between your client and pfSense.
-
@stephenw10 said in pfsense as a client not a firewall.:
Add a PASS firewall rule on WAN with source 192.168.10.0/24 and destination WAN address on port 443.
That's assuming nothing is NATing that traffic between your client and pfSense.
A slight modification "This Firewall" but works perfectly. Thanks a bunch!
-
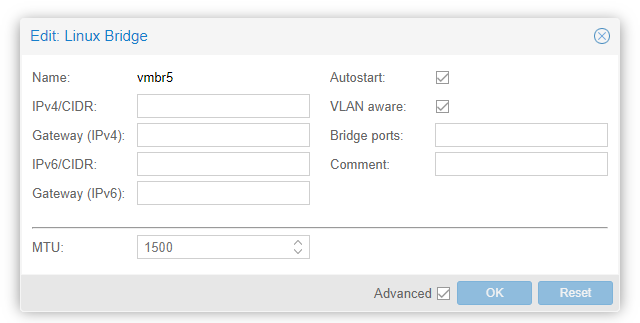
So this "LAN" I created which uses the same physical NIC as WAN, what good is it, what do I use it for? I gave it IP 192.168.80.1 and vlan 80
Nowhere in my omada network equipment is there a vlan 80 setup.
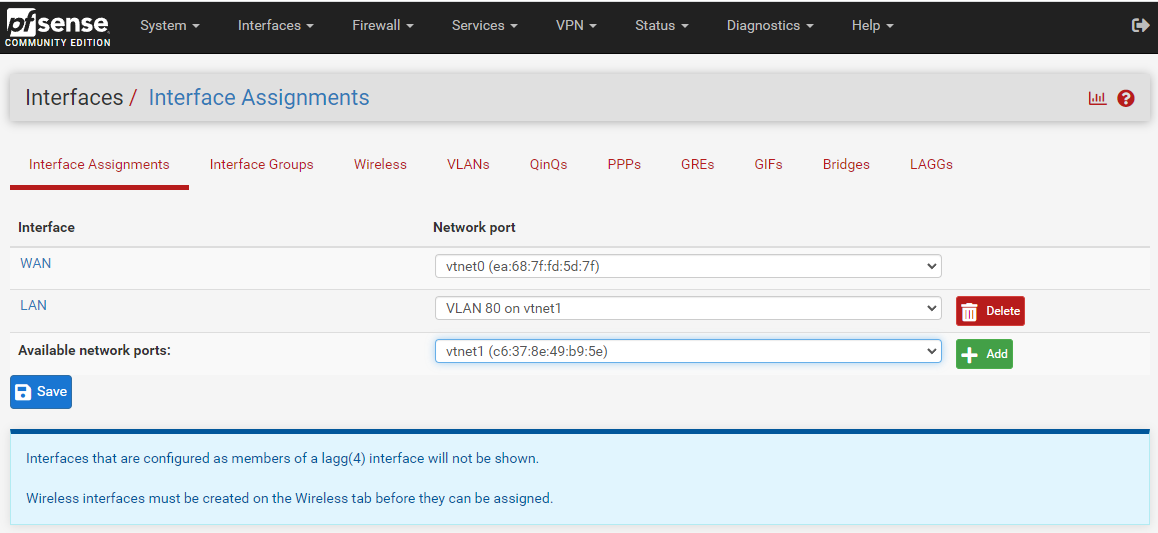
vtnet0 is WAN (vmbr0 in Proxmox)
vtnet1 was just made up in proxmox (vmbr5) and appears in pfsense as vtnet1. I read to do this in some setup guide I found on the internet but it appears to do nothing???
-
In a virtual install like that I'd usually expect to see the LAN assigned to an interface connected to an internal only bridge. Such that other VMs on that bridge use pfSense as their gateway and traffic to/from them can be filtered.
Steve