LAN traffic to internet intermittently blocked
-
I am trying to understand why traffic from LAN to the internet is intermittently blocked by the implicit default deny rule. All the traffic blocked on LAN should have matched the default IPv4 rule that is there but apparently isn't for reasons I don't understand.
Here is an example block on LAN (ie. re0).
4,,,1000000103,re0,match,block,in,4,0x0,,64,4095,0,DF,6,tcp,40,192.168.45.159,52.217.136.177,42902,443,0,FA,2722214640,3511262964,2910,,
My LAN rules are defaults out of the box.
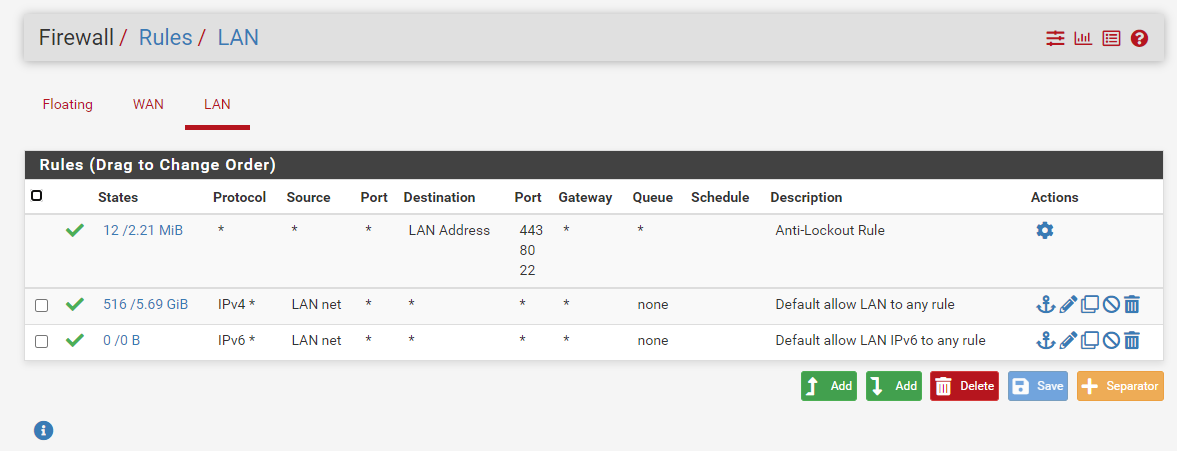
Shouldn't the "IPv4 LAN net to any" rule have matched and allowed this traffic? Why isn't this rule matching resulting in the final default deny rule blocking the traffic?
Also, just to be clear, it is not all traffic that is blocked even from the same client IP. Just some.
My network is very plain. No VMs, no VLANs. Just a normal subnet on the LAN side, and NAT on the WAN going out to AT&T gigabit internet. I am on 2.6 CE.
Let me know if anyone has any ideas. This totally does not make sense to me.
-
If by "LAN traffic to internet intermittently blocked" you mean just log entries you see on pfSense and do not mean you literally cannot connect to certain IP addresses, then most likely you are seeing normal out-of-state traffic being blocked. This is usually the case when the blocked traffic has IP flags other than SYN.
pfSense uses a stateful-inspection firewall engine. Here is a brief technical description: https://www.fortinet.com/resources/cyberglossary/stateful-firewall.
-
Yup that^
That packet in your example is a TCP FIN-ACK. It's a client on LAN ACKing a FIN that has already closed the state. It's nothing to worry about.
Steve
-
I guess that kind of makes sense.
Reason I am even looking at this is because I have a few IOT devices at home that started to fail network connectivity. Initially, I chalked it up to the devices being old and maybe the wifi NIC failing. But I reconfigured a few to get online via a mobile hotspot and found out they work just fine when using the hotspot but not when on the normal wifi at home which goes through the pfsense FW.
So this got me to take a second look at the firewall and that is when I first noticed traffic being blocked on the LAN. Granted I am not 100% positive these blocks are the culprit but definitely suspicious.
I started paying more attention to the TCP flags and all the LAN blocks show flags for FPA, FA, PA, and RA. There seems to be quite a lot of these that I can see over the past hour or so. Is it normal to have this many spurious out-of-state network packets hitting the LAN interface? Have never looked this closely at traffic on the LAN and definitely was not aware this much traffic being blocked. Maybe this is normal.
Still can't explain why the IOTs work if bypassing the pfsense FW.
-
@zenjubo said in LAN traffic to internet intermittently blocked:
Let me know if anyone has any ideas
The most important one :
How should we know :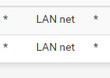
stand for .... what ?
Afaik : "LAN net" is the default 192.168.1.0/24But then :
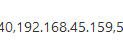
So, if you used the default LAN network, the log line would be normal ..... (actually : nothing would pass).
But ok, your 'intermittently blocked' is also valid info
The solution :
-
You can try setting the firewall optimisation to 'conservative' in Sys > Adv > Firewall&NAT:
https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.html#firewall-optimization-optionsThat will hold states open longer. However TCP states are closed by the TCP flagged packets so it may not affect this.
Seeing packets from stale states blocked like that would not prevent anything connecting out. Are you seeing blocked traffic from the IoT devices?Steve
-
@stephenw10 said in LAN traffic to internet intermittently blocked:
You can try setting the firewall optimisation to 'conservative' in Sys > Adv > Firewall&NAT:
https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.html#firewall-optimization-optionsThat will hold states open longer. However TCP states are closed by the TCP flagged packets so it may not affect this.
Seeing packets from stale states blocked like that would not prevent anything connecting out. Are you seeing blocked traffic from the IoT devices?Steve
If by block you mean blocked SYN traffic, I ran through all of the LAN block filterlogs available and did not see a single SYN block. The main ones I counted were FPA, FA, PA, and RA.
So it looks like the firewall is just doing what its supposed to do.
I just can't explain why suddenly a few of my IOT devices (ie. google smart displays) suddenly are having network connectivity issues and putting at least one on mobile hotspot seems to fix the issue. Maybe they all just received a firmware update with broken network stacks??? I would not write this off as a way for manufacturers to silently EOL devices they no longer wish to support. ;)
-
Check for IPv6. pfSense will provide IPv6 by default if it sees it available and many devices will try to use it by default. If something upstream changed you might have IPv6 when you didn't before.