AES-NI and OpenVPN?
-
@dobby_ Fun stuff.
I get the full 1Gbps if I hit the local speedtest server through the two-NAT two PFsense systems route.
If I hit it through the Openvpn tunnel between the same two systems I am seeing the speed and CPU utilization you see in that screen capture.Thank you for answering all of my questions and I'm a newb at much of this.
I'm still failing to understand why the toggleable options are there both in system\advanced
and within the openvpn client or server items.
Why are there they to turn on/off if it is going to go ahead and use AES-NI anyware regardless of the toggles?
Are there two separate sets of AES-NI software?
One (kernel level) in the module and another in userspace(default if you do not load the module?And what about the other toggle within the client or server ?
Does that just tell the client or server to USE the module or to NOT to use it?Then if you USE the module does it stop using the _not module AES-NI in userspace?
Or does it use a combination of BOTH versus (one or the other) when it is loaded as instructed from system\advanced?Thanks for being patient with me on this and for all of the information.
-Steve -
@n8lbv said in AES-NI and OpenVPN?:
I get the full 1Gbps if I hit the local speedtest server through the two-NAT two PFsense systems route.
You may be then the lucky guy were the VPN will be
done in raw MHz/GHz, and all is fine for you.But there are also other peoples out and they don`t use OPNvpn and/or WireGuard. Or they have special needs,
an other use case and so on.If I hit it through the Openvpn tunnel between the same two systems I am seeing the speed and CPU utilization you see in that screen capture.
May be but others have perhaps the need for IPSec and/or
they are getting a gain from that AES-NI, if it is present
and you have no other things up there such Intel QAT
you have not the need to change, but if it is so you
will be also the lucky one that is able to change and let
us say you say please use QAT or an HiFn Chip or what ever is in place. So in my eyes you are looking at your situation and your hardware and all is fine.Thank you for answering all of my questions and I'm a newb at much of this.
It is more to try out turn your thinking into another
direction, because;- you see only your situation
- you see only your equipment
So you can´t understand it, let us imagine you are a company and given by law or company rules or plain insurance rules you will be pressed as the admin of the network to use something such IPSec, or other hardware
in the company all over the world is not able to use OpnVPN and/or WireGuard, o what will you do now?And for that clients and peoples or plain users it is a nice
catch or nice to have thing, that pfSense is offering to them the ability to change such things fast, to fit their
needs.I'm still failing to understand why the toggleable options are there both in system\advanced
and within the openvpn client or server items.Your CPU comes with AES-NI, but what will be when;
- Your CPU is also sorted with Intel QAT and you want
to change it now? You do you want to realize it then? - Your hole amount of VPN road Warriors will be hard increasing and you may want to change the chip that
or instance that should be used for encryption, how
you want to do this then?
Why are there they to turn on/off if it is going to go ahead and use AES-NI anyware regardless of the toggles?
What is when at one day other things such QAT comes
out and you will be not able to change or say use this
or use that?Are there two separate sets of AES-NI software?
It depends often on other points and more points.
Mostly it is only the way how it is used.
case one:
AES-NI is present in the CPU
crypto dev system from the os uses a driver
and the driver uses the AES-NI instructions set of the cpu
case two:
the software uses the AES-NI directlyBut in real and on top this it comes other benefits by side
like better elliptic curve's, better cycling and so on and so on, because it is all under the heat not visible to see for
us customers we may thinking why is it there.One (kernel level) in the module and another in userspace(default if you do not load the module?
And what about the other toggle within the client or server ?In short it can be answered if you are not needing it makes it not obsolete to be present and let us imagine you must now feed some more 1 GBit/s lines and doing a backup
over them, what then?Does that just tell the client or server to USE the module or to NOT to use it?
I think it is more who and when it will be used;
- OpenSSL will use it even if it is present
- The software only if it is enabled
- And the other benefits from it may be not known from us
because we a re not the software coder, but anyway I will be more lucky with the situation that I am able to change
something, against there is no way to do so.
Then if you USE the module does it stop using the _not module AES-NI in userspace?
Since the change from FreeBSD 12.3 to version 14.0
there will be more changes as we end users would
knowing about. Who knows how things will be
changed and in wich steps this process will be done.Or does it use a combination of BOTH versus (one or the other) when it is loaded as instructed from system\advanced?
Thanks for being patient with me on this and for all of the information.Let us say you are an engineer and you do research for
let us say 1 million $ and now you want to go to the
patent office to get a patent, and then this fancy new OpenVPN or WireGuard comes out and you use it, but
someone was steeling your ideas because there where
a not found whatever Inside, you are done!Other countries will be hard forbit the usage of hardware
accelerated crypto work and now you can show them it
is all done in pure CPU work with an unchecked AES-NI
usage, all is then fine for you! -
@n8lbv said in AES-NI and OpenVPN?:
I'm still failing to understand why the toggleable options are there both in system\advanced
and within the openvpn client or server items.
Why are there they to turn on/off if it is going to go ahead and use AES-NI anyware regardless of the toggles?The crypto hardware option in System > Advanced it to choose which kernel module to load. Those modules are used by the bsd crypto framework for kernel mode crypto operations. So that's IPSec or OpenVPN in DCO mode.
The hardware crypto option in the OpenVPN config is the equivalent of specifiying the 'engine' for OpenSSL operations. In current pfSense versions OpenSSL can't use the AES-NI module for that (and doesn't need to anyway). It exists only for much older crypto offload hardware that may still be use. Most users should not select anything there.
If you're looking for the best OpenVPN throughput the best option currently, by some way, is to use QAT supported hardware and run OpenVPN in DCO mode.
Steve
-
Also in terms of impact with those changes you are working on the down hill side of the change Bell curve. You need a lot of investment of resources to see a difference. That’s the thing being on the down hill side.
You may find the actual real world performance doesn’t change that much between Off and On.
Same reality regarding all the various NIC tweaks. Default results that are not that worse then with all the tweaks.
-
@jimbob-indiana For now the best would be to place a similar processor, same generation/core count and speed that does not have AES-NI.
And run my tests.
It will not be a direct match nor have the exact effect of turning off AES-NI but it will be close
enough for what I am doing or trying to get an idea of. -
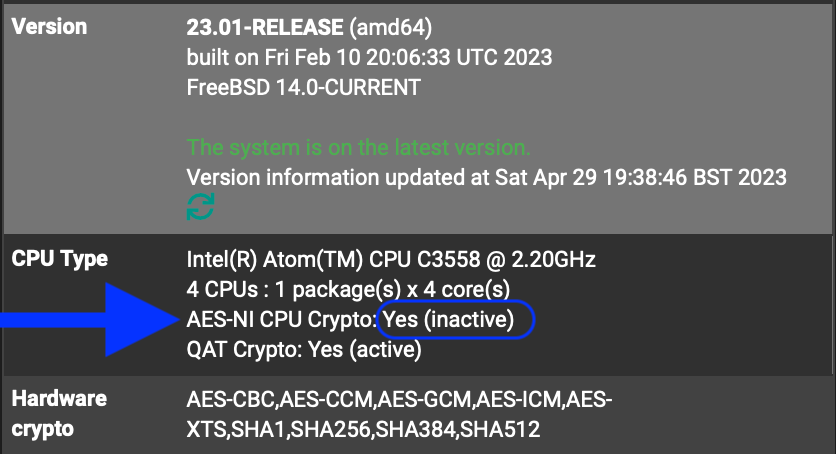
Also on the PFSense dishboard page we see: AES-NI CPU Crypto: Yes (inactive)
If that is not true, it really should be changed.
Or should say module not loaded.
Or should say really is active but is not.
Or is.
Or is not
Or "maybe it is". -
@n8lbv I don’t think it will show “Active” unless you are using it as in VPN, etc.
If not using any of the Apps that use it means “Inactive” is correct.
AFAIK
-
@jimbob-indiana Thanks!
I will test that.
Steve -
The line in the system information widget currently shows if the CPU is reporting it supports AES-NI. It shows as active if the kernel module is loaded.
-
@stephenw10 Yep my testing shows same.
Now for a repeat and continued confused person question...
open VPN uses AES-NI whether you load the module or not?Openvpn uses module if module is loaded.
Does openvpn use AES-NI in a different way if the module is loaded versus if the module is not loaded?
Also openvpn client and server have their own option to or "disable "hardware crypto acceleration"
I wonder if this could be made less confusing in the future once I understand it better.
I hope you understand my confusion a bit and are not frustrated with me asking over & over.
-
@n8lbv said in AES-NI and OpenVPN?:
open VPN uses AES-NI whether you load the module or not?
Correct. Because OpenSSL does, except in DCO mode.
@n8lbv said in AES-NI and OpenVPN?:
Openvpn uses module if module is loaded.
No. Except in DCO mode.
@n8lbv said in AES-NI and OpenVPN?:
Does openvpn use AES-NI in a different way if the module is loaded versus if the module is not loaded?
No. Not any longer. That used to be the case a number of versions back, like in 2.3.X
Steve
-
@stephenw10 Thanks! excellent clarifcations.
-Steve -
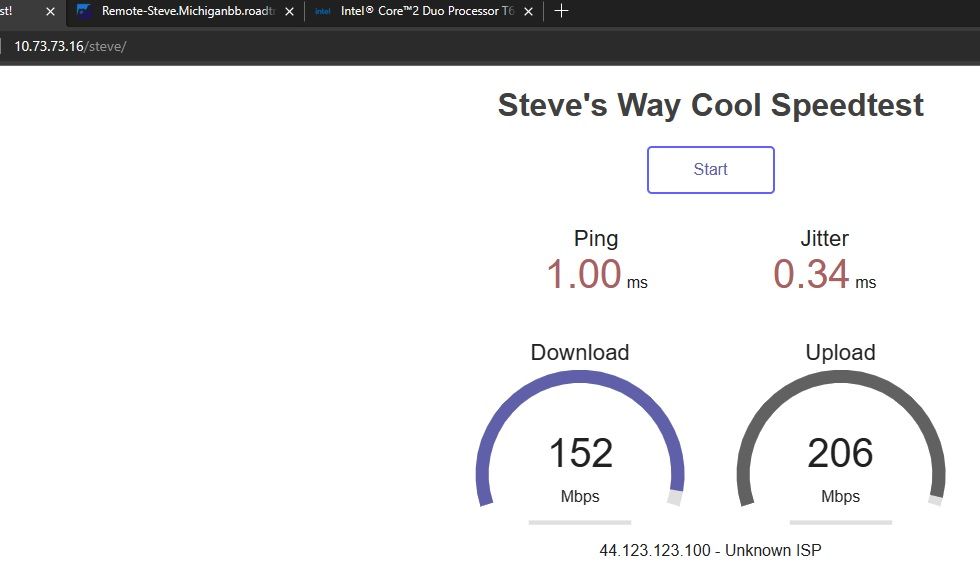
Laptop single nic OpenVPN HTTP throughput test.
35Watt Laptop CPU from Jan 2009. NO-AES-NI.Intel
 Core
Core 2 Duo Processor T6400
2 Duo Processor T6400
2M Cache, 2.00 GHz, 800 MHz FSB
-
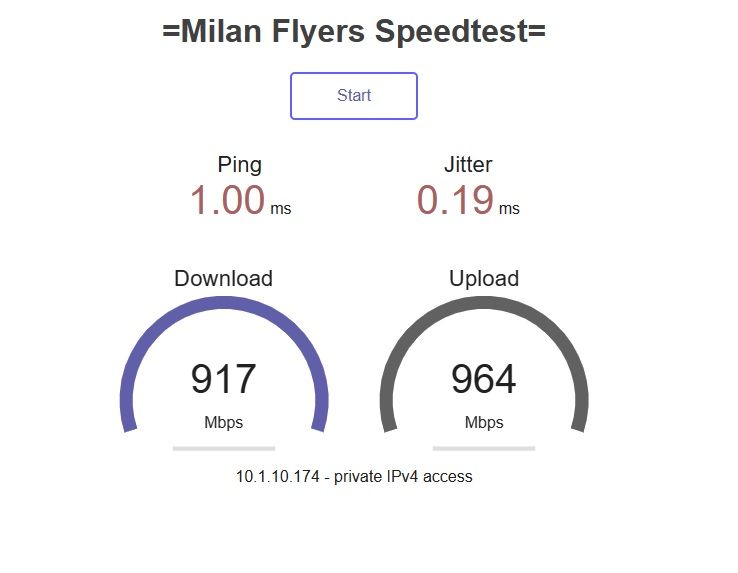
Same test through dual NAT no OpenVPN.
That early 2009 laptop (running PFsense) has a Broadcom NIC on the mainboard.
-
@stephenw10 said in AES-NI and OpenVPN?:
The line in the system information widget currently shows if the CPU is reporting it supports AES-NI. It shows as active if the kernel module is loaded.
Just out of curiosity, why would the kernel module not be loaded?
 ️
️ -
@robbiett Good question. Mine since I can remember said “Inactive”. I played with the VPN configuration options yesterday and today, says “Active”.
I didn’t actually do a VPN.
CPU Type Intel(R) Core(TM) i7-4790 CPU @ 3.60GHz
Current: 2800 MHz, Max: 3601 MHz
8 CPUs: 1 package(s) x 4 core(s) x 2 hardware threads
AES-NI CPU Crypto: Yes (active)
QAT Crypto: No
Hardware crypto AES-CBC,AES-CCM,AES-GCM,AES-ICM,AES-XTS -
@jimbob-indiana I had presumed (and we all know where assumptions lead) was that QAT was being preferred* over AES-NI; now I am not so sure.
 ️
️
*As it is rather excellent
-
please have a look at the Intel QAT, because this is loaded instead of the AES-NI!!!! You can use AES-NI or Intel QAT
but not both!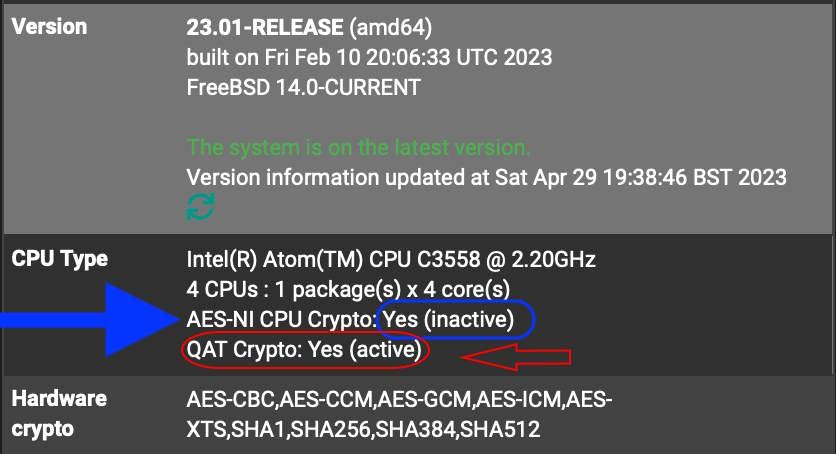
-
@jimbob-indiana said in AES-NI and OpenVPN?:
Good question. Mine since I can remember said “Inactive”. I played with the VPN configuration options yesterday and today, says “Active”.
Mine fresh installed says "active" too!
You can see with no configured VPN actual!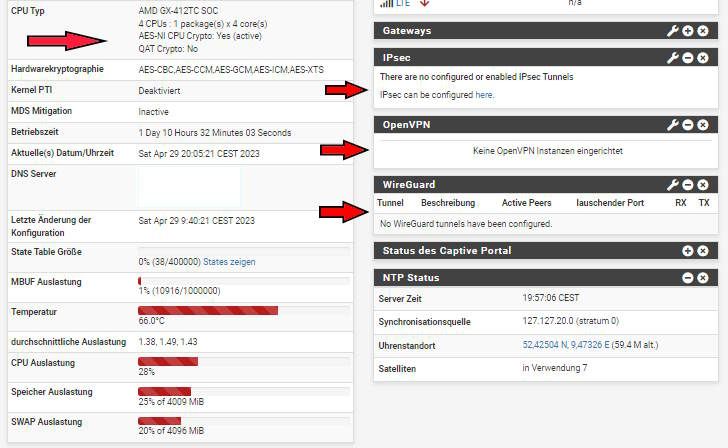
-
@dobby_ said in AES-NI and OpenVPN?:
please have a look at the Intel QAT, because this is loaded instead of the AES-NI!!!! You can use AES-NI or Intel QAT
but not both!Err, I did.
I literally stated my assumption that QAT was preferred over AES-NI and the graphic showing QAT (active) & AES-NI (inactive) is my own (!!!!...?).