Help with site-to-site VPN
-
Hi guys,
Hoping to get some detailed instructions to get this working.
My preface:
I’m trying to plug my parent apartment into my SIP server, I got them SG 1100, it works well. They have senior grade internet which should be okay for this.To the question:
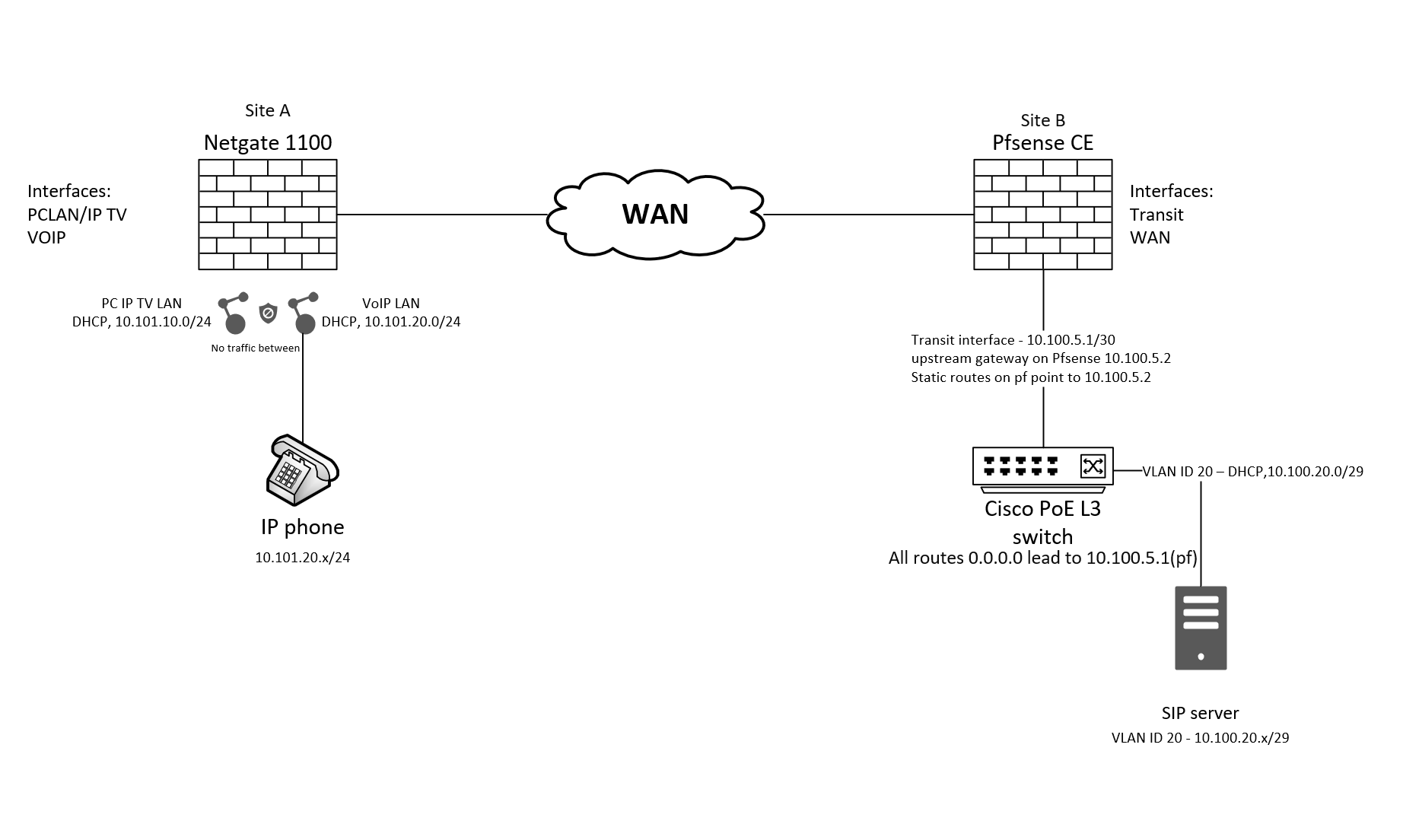
There are 2 sites: A, B. The B site has a VoIP server (VLAN on the switch, not Pfsense), site A wants to register to that SIP server at a B site. The A site doesn’t know about site B VLAN. The A site has Pfsense with VLAN’s, one of them is VoIP.
The Pfsense doesn’t handle VLAN’s on site B, it has an interface – transit to L3 switch.How do I set up a tunnel and specifically if site B Pfsense doesn’t have its LAN?
And how do I route traffic from A to B and to a specific network/VLAN?
Also, what type of VPN would you recommend for this setup; IPSec, Wireguard, OVPN?
Attached a diagram here too!
Thank you!
-
Any VPN type is capable of handling that. I would probably choose OpenVPN but I'd recommend going with whatever you're most comfortable with. You will need to have the right routes and firewall rules in place.
Do both sites have a public WAN IP?
Steve
-
@stephenw10 They do. Both modems are in the bridge mode with firewall facing public IP, hence I didn't include in the diagram.
Why would you recommend OVPN? Due to lightweight? It my benefit it since site A has slower connectivity.
Could you please describe the steps needed to setup static routes on both firewalls? I'm bit confused by the fact how to set a route on site A about Site B switch VLAN 20 (not on Pf).
Thanks!
-
I mean I would expect to be able to use any VPN in that case. OpenVPN I have generally found least problematic. Especially if you have to do any remote support.
If you install the client import package on the 1100 you can install the client export package on the server end and do all the config there. Then simply export a config and import it at the other end.
Because the client gets most of it's config from the server end when it connects you can easily make changes there and propagate them.Steve
-
@stephenw10 Okay, thanks. I will try later today.
Is routing still should be added to packets traverse to the switch? -
pfSense at the server end already has a route to the VLAN20 subnet I assume. The switch and VoIP server will have their default route via pfSense so no need to add anything there.
You will need to pass a route to the client to the VLAN20 subnet.
You will need to add the 10.101.20.0/24 subnet to a client specific override so the server knows that subnet is behind the client.See: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
Except that documents pre-dates the client import package so almost all the client side config can be automated using that.
Steve
-
@stephenw10 said in Help with site-to-site VPN:
You will need to pass a route to the client to the VLAN20 subnet.
You will need to add the 10.101.20.0/24 subnet to a client specific override so the server knows that subnet is behind the client.Hi Steve,
Can you please elaborate where do I set those 2?
For client specific override do I need to use a certificate?
Thanks.
-
The passed route is just added as a local subnet in the server config.
The remote subnet needs to be added to a CSO. The CSOs match against the common name of the client on the certificate. Adding the subnet there creates an iroute in the server so it known that subnet is at that client.
You could create this tunnel using a shared key and just add appropriate local and remote subnets at each end. However shared key tunnels will be removed from OpenVPN in the near future so it's better to use certs now.
-
@stephenw10 I re-followed provided wiki and got it working. One thing I had trouble with, all of the sudden was my Wiregard road warrior user setup stopped providing route. Fixed it by pfsense reboot.
Thank you for your help!!!