PFSense rewriting all traffic?
-
Hello everyone,
I'm sure this has been asked but I searched and was unable to find an answer.
I use Apache + Nginx for Reverse proxy and have recently installed a PFSense Firewall. Since the upgrade, it seems all traffic to a valid domain is redirected to the login page for the router via some sort of rewrite directive.
Can anyone point me in the direction of how to resolve this?
Thank you.
-
If you're testing from inside the firewall it's probably this:
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.htmlSteve
-
@stephenw10 Thank you for your response, Stephen.
I do have my NAT set properly as I did see that as being a potential problem, but this is external as well.NAT Port Forwarding is set properly, rules are in place to match, finally have traffic coming in as I had issues for a week then discovered unlike previously I was required to set WAN IP and not LAN IP as with my previous Firewall...
Now the URLs are reachable, but everything that is a positive hit on a domain is forwarded to PFSense login page, while all subdomains that are not active obviously get an error that they do not exist.
Thank you.
-
@dgarner said in PFSense rewriting all traffic?:
I was required to set WAN IP and not LAN IP as with my previous Firewall...
huh? On a port forward the the destination IP would be pfsense public IP (wan address) - this is where someone would be going to from the internet when trying to get to your service.
When you create a firewall rule, the destination in the firewall rule on the wan would allow to your inside rfc1918 address that you forwarded traffic too. This rule is auto created when you create the port forward, unless you change the default setting on the port forward.
but everything that is a positive hit on a domain is forwarded to PFSense login page
If your trying to go to something.domain.tld that resolves to your public IP while your inside your network - you would either need to setup nat reflection, or its better for devices on your internal network to resolve something.domain.tld to your local server or proxy IP, and not the pfsense wan IP.
-
@dgarner said in PFSense rewriting all traffic?:
Now the URLs are reachable,
In what way? You are able to hit the sites as expected?
Are these sites resolving to the pfSense WAN IP?
-
Hey guys, I apologize about the disappearance. I had a situation that diverted my attention away from everything for a few days. I apologize the lack of professionalism.
@johnpoz Can you explain this last part more?
So yes, that is what I am trying to do. Each node (roughly 10 servers, 3 workstations, etc.) has a hostname, and
hostnane -fresolves to their FQDN, which returns correct. The PFSense hardware Firewall is set as the Gateway and DNS Resolver for each device.Node 1 is the NGinx server which also hosts Apache, which should dictate via nginx where to send traffic via their internal IPs in website.conf
Is that correct, or incorrect?
@stephenw10 Well, as I just discovered because I had not tried before, yes, it appears that's what is happening. My Public IP is hosting the PFSense Admin page.
Coooooooool...
That should probably be changed regardless of all the other problems going on, hahaha.
-
@dgarner said in PFSense rewriting all traffic?:
My Public IP is hosting the PFSense Admin page.
No what is happening is the gui is listening on all IPs, and your able to hit the public IP from your lan.. So yeah you can hit the web gui via your public IP when your on a lan side network.. But you can not do that from the internet side unless you allowed it via a firewall rule
What part did I not explain well enough..
Your public IP lets call it 1.2.3.4, and your inside whatever.domain.tld that you forward to is on say 192.168.1.100.. So when your local setup host override so that whatever.domain.tld resolves to 192.168.1.100
Or setup nat reflection..
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.html
-
Yes so, as described in that first link, if you're using FQDNs that resolve to a public IP on the firewall and have port forwards setup then accessing them from inside the firewall does not hit the port forwards and hence you get the webgui instead, which listens on all IPs.
Use NAT reflection or split DNS so internal hosts hit the expected targets.Steve
-
@johnpoz Okay, I see what you're saying.
I have attempted to resolve this issue by ensuring that Pure NAT was enabled and I have set up Split DNS as well, however, what is being said about 'this will only happen on LAN and not WAN unless Firewall rule.." is not necessarily true? unless the Firewall rule is Port 80 for web traffic.I have transferred all ports from our previous Firewall, I have set up DHCP and Split DNS and I am still having PFSense catch all traffic, even from WAN from my phone.
I must run my children to school and I can post configs of all these, if that would be helpful.
-
@dgarner said in PFSense rewriting all traffic?:
if that would be helpful.
Seeing what you did would help us point out what is not right yes..
-
@johnpoz (PS, Thanks, as well, @stephenw10 for all of your help, gentlemen)
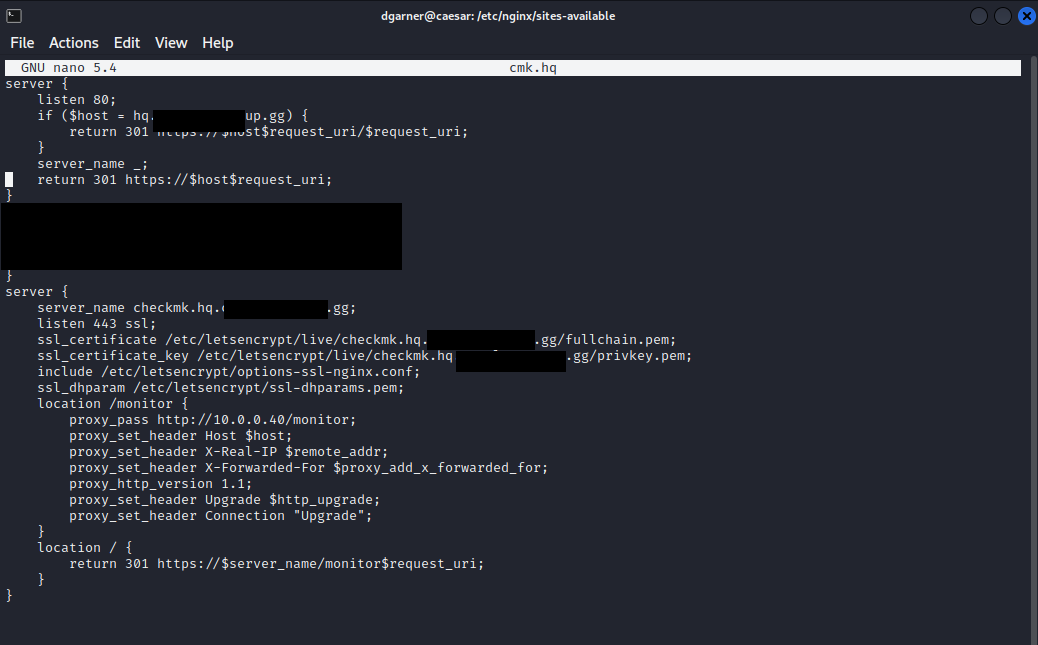
I don't know guidelines on photos, so I will refrain and use only text to display configurations.
NAT Reflection mode for port forwards: Pure NAT (also tried with Helper on LAN interface)
domain: hq.domain.com
DNS Server 1: Local PFSense IP (Not 127)
DNS 2: Google
DNS 3: Alt. GoogleFirewall:
Firewall Aliases IP
Nginx - 192.168.1.10NAT / Port Forward:
HTTP/HTTPS/HTTPd:
Interface: WAN
Dest. WAN Address
Port Range 80 / 8080 / 443 (Respectively)
Redirect target IP: LAN Address (just changed .. turned on Airplane and tried again, nothing.)OMD, Example:
Interface: WAN
Protocol: TCP/UDP
Dest. WAN Address
Dest. Port Range: 6555 - 6559Redirect target IP: Single host - 192.168.1.11
Redirect target port range: 6555Rules to Match.
DHCP Maps out all main nodes, as an example..
MAC Address: [MAC]
Client ID: [MAC]
IP Address: 192.168.1.10
Hostname: Nginx
Gateway: [IP to PFSense Router]DNS Resolver
Network Interfaces: All
Outgoing Interfaces: All
DHCP Registration: Unchecked (Perhaps this would be easier ...)
Static DHCP: Unchecked (Perhaps this should be easier ...)Host Overrides:
Host: Nginx
Domain: domain.com
IP Address: 192.168.1.10Additional Names for this Host:
Hostname: Home
Domain: domain.com
If you want me to take ss or submit an actual conf. file, I would willing to do so.
conf files would have to be redacted some, of course. -
@dgarner said in PFSense rewriting all traffic?:
I don't know guidelines on photos
screenshots are always better - please post screenshots of your portforward and wan rules. Also let us know if you have any rules in floating.
-
@johnpoz Sounds perfect, sir.
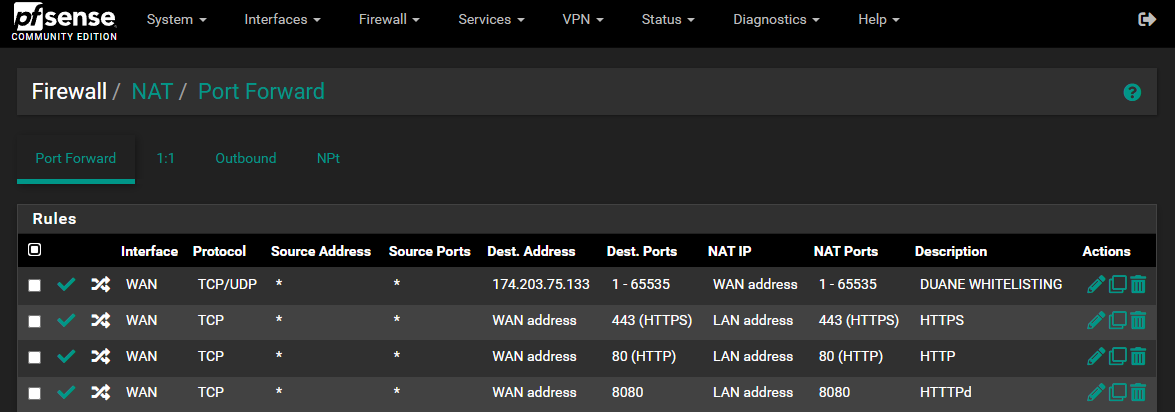
This is an example, as there are roughly 60 ports open at the moment.
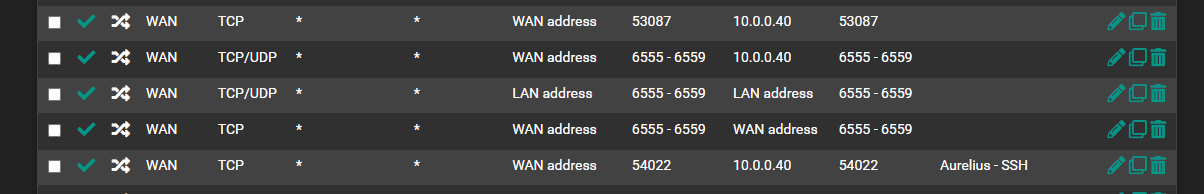
Rules
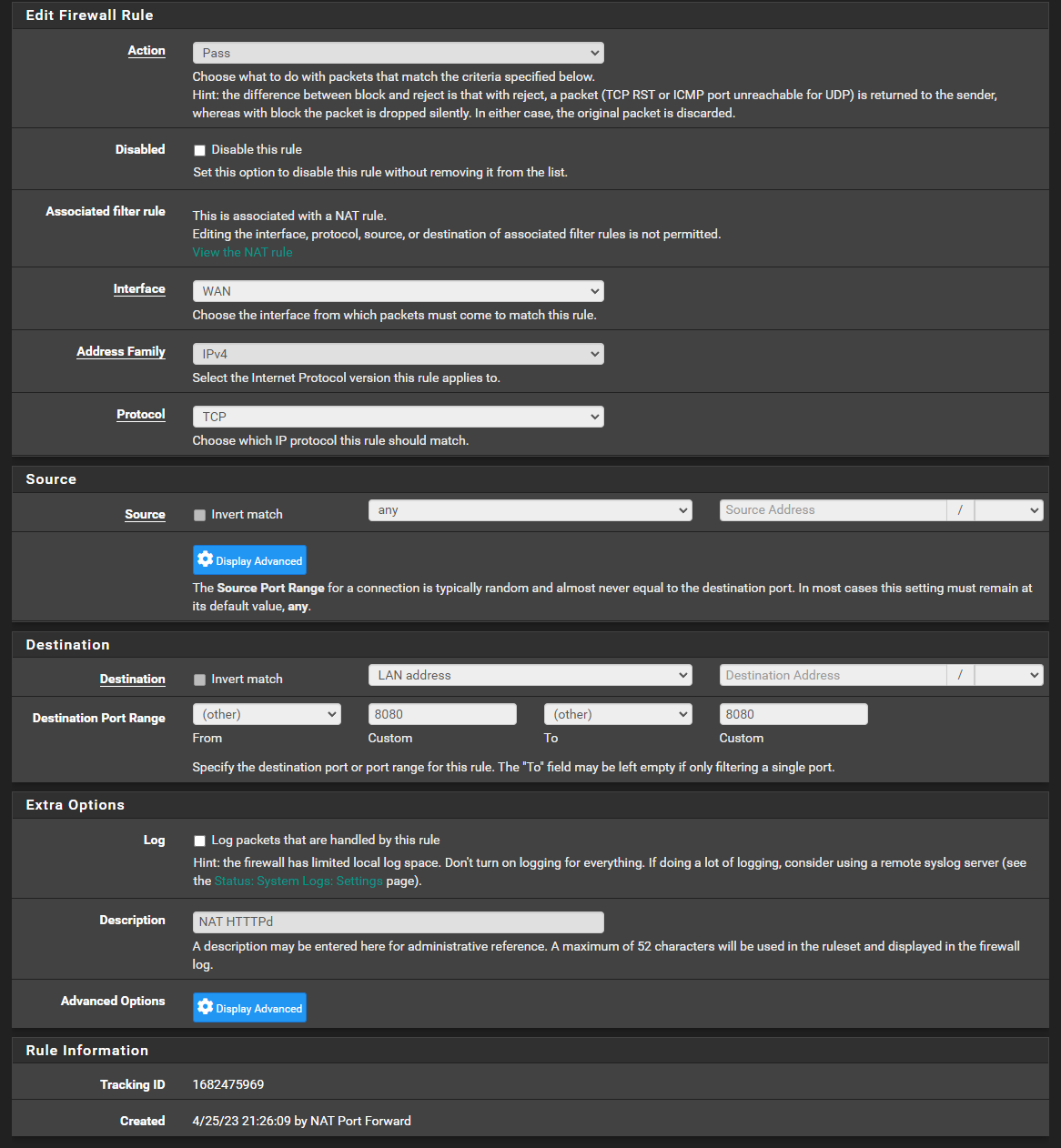
And here is one thing in particular I am attempting to work out ...
DHCP
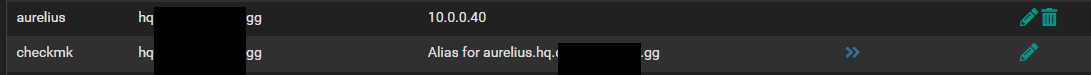
I think this is perhaps a good beginning?
-
@dgarner what are you wanting to do here
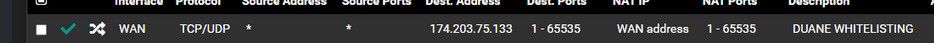
That makes no sense to me..
edit: these make no sense either
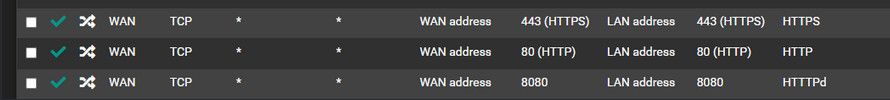
Why would you forward something that is hitting your pfsense wan address to pfsense lan address? Are you trying to get haproxy to reverse proxy something to inside your network?
if your running nginx as reverse proxy somewhere behind pfsense, the forward would go to that specific IP..
-
@dgarner said in PFSense rewriting all traffic?:
Redirect target IP: LAN Address
Yup that's almost certainly incorrect.
-
@johnpoz The whitelisting IP was an attempt to get connectivity to my phone to the network in a rush before I had time to properly install Twingate or a VPN.
This will be deleted now.
Thank you for making me notice this again. :DYes, as I believe I said above, that's exactly the objective.
I am using Nginx by F5 (Not NPM or whatever with the red gem logo) along with Apache as a reverse proxy and am attempting to allow clients to connect on the outside via "web ports."80 = duh
443 = duh
8080 = Ports on which Apache AND Nginx are running same server, Nginx (80) and Apache (8080) should be serving web content to clients, which almost all of my servers have some sort of web content, even if it's something such as an administrative "CPanel" type web interface.I know I have attempted to not use LAN Address before, but I will change back to specific host and see if that resolves it now that things are more configure that previously.
Thank you for the for confirmation @stephenw10 -- it genuinely means a lot from both of you guys, thank you. :D
-
@dgarner what do you think these do exactly?
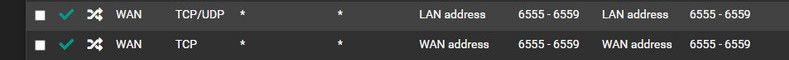
Those are not doing anything..
How many more like that do you have? You mention something about 60 ports?
Not sure why your running a reverse proxy inside your network, why would you not just run haproxy right on pfsense? Much cleaner way to do it imho.
-
@johnpoz said in PFSense rewriting all traffic?:
@dgarner what do you think these do exactly?

Those are not doing anything..
How many more like that do you have? You mention something about 60 ports?
Not sure why your running a reverse proxy inside your network, why would you not just run haproxy right on pfsense? Much cleaner way to do it imho.
Because I have been running a reverse proxy much longer than I have been using PFSense.
I will look into HA but as NGinx is already set up, it's at least preferable to have it working momentarily until I can make time to switch to HA.Those ports were not originally "LAN/LAN" and "WAN/WAN" --those were spaghetti against the wall trying to make this work. Haha.
-
@johnpoz As an example, most of my Port Fowarding/Rules look like this,
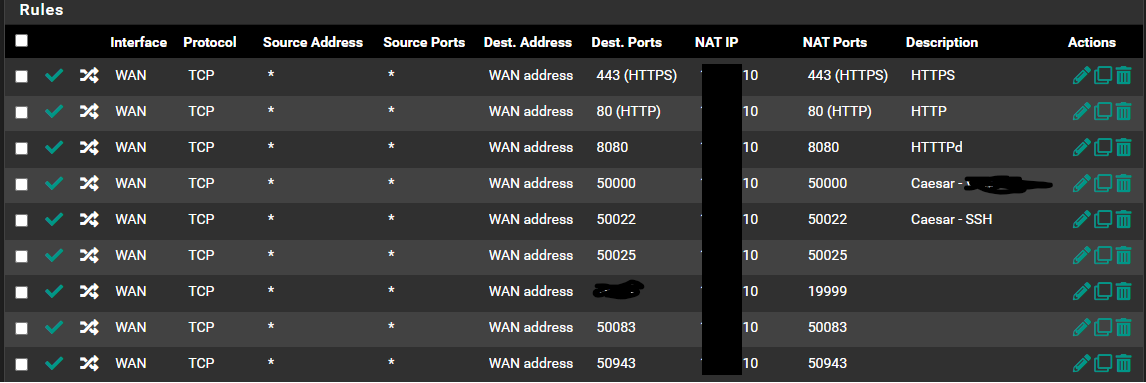
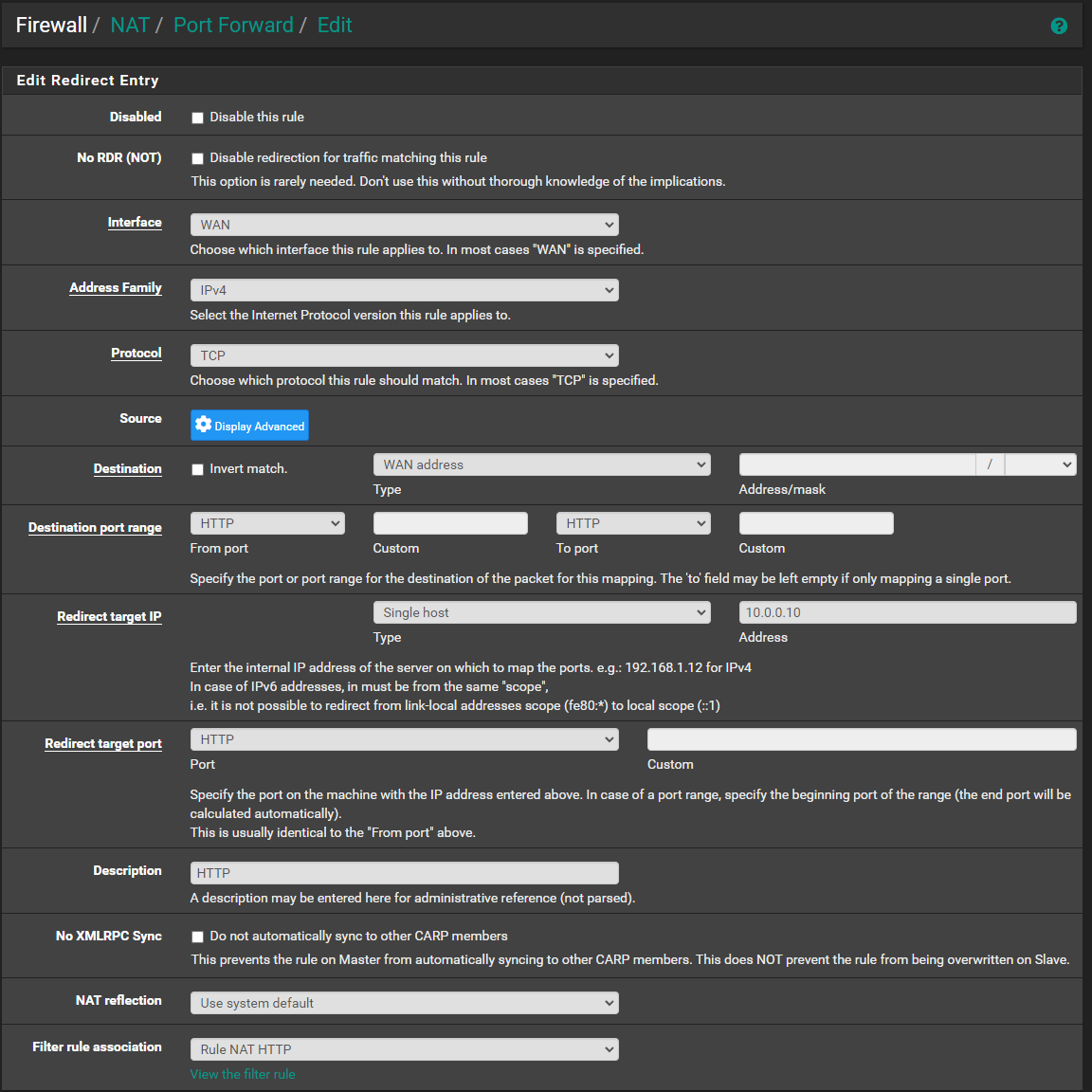
-
@dgarner those look normal - not sure why any reason to hide rfc1918 space? Are those public IPs you obfuscated? Are you routing public IP space to behind pfsense? If so there would be no need for any port forwards.
If they are rfc1918, as long as that .10 address isn't pfsense address, then those should work unless you had blocking in floating, or in wan that blocked?
When troubleshooting port forwards.. Normally couple of minutes running through the troubleshooting guide will find the source of the problem right away.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat-port-forwards.html
spaghetti against the wall trying to make this work. Haha.
Never a good idea ;) just makes a mess.. I taste my spaghetti to know if its the proper al dente hahah