Route traffic through ipsec tunnel
-
Hi,
I have a main office with 6 branch offices.
There are ipsec tunnels from the main office to all branch offices, with two Phase 2 tunnels, one for the LAN 192.168.1.0/24 and one for a badgesystem, 172.16.0.0/16On the main office I made also a tunnel from the main firewall to the badgesystem server which is outside my wan, it is hosted by a 3rd party.
Now, how can I get traffic coming from the branch office to the 3rd party ?
-
I found this on the old firewall?
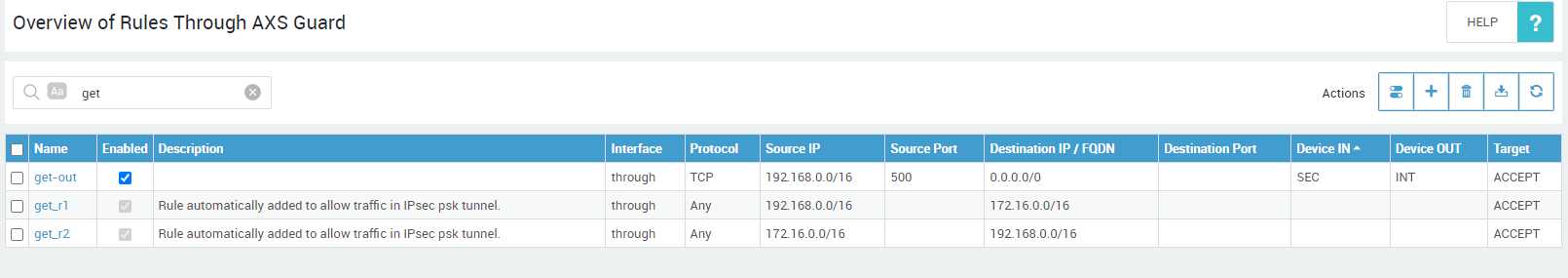
Might this be enough ?
-
@nick-loenders said in Route traffic through ipsec tunnel:
On the main office I made also a tunnel from the main firewall to the badgesystem server which is outside my wan, it is hosted by a 3rd party.
Which settings?
I assume, all the branch LANs and the main LAN lie within 192.168.0.0/16.
So you need to state this a local network in the phase 2 and the badgesystem network as remote. -
This is at the branch office:
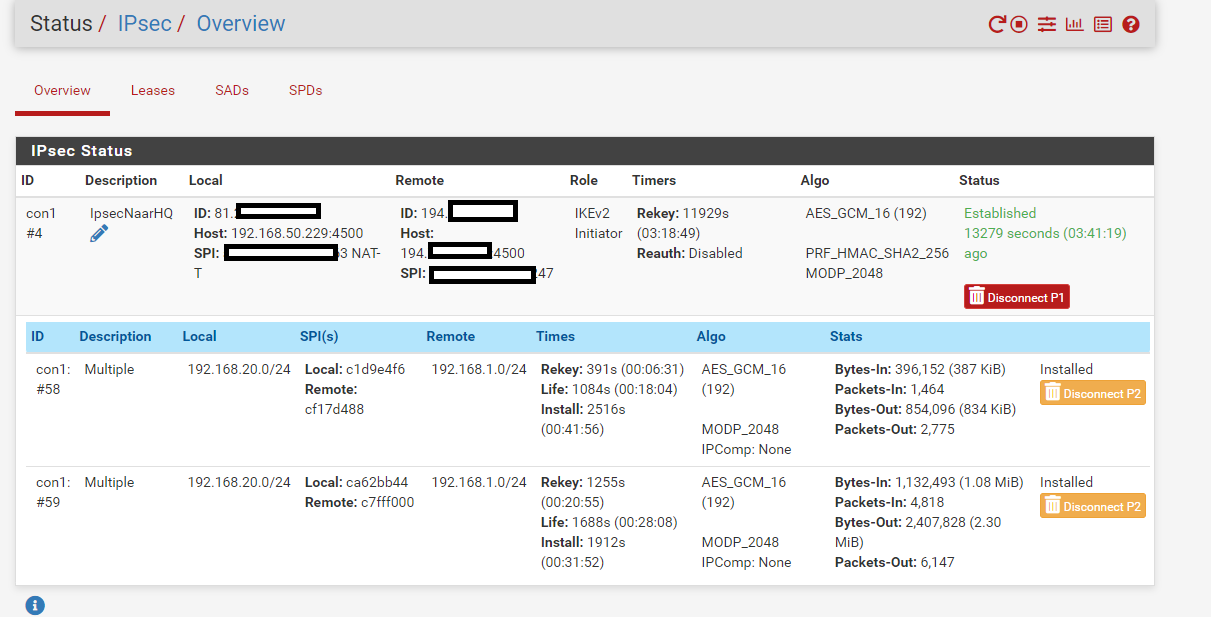
And this is on the Main Office:
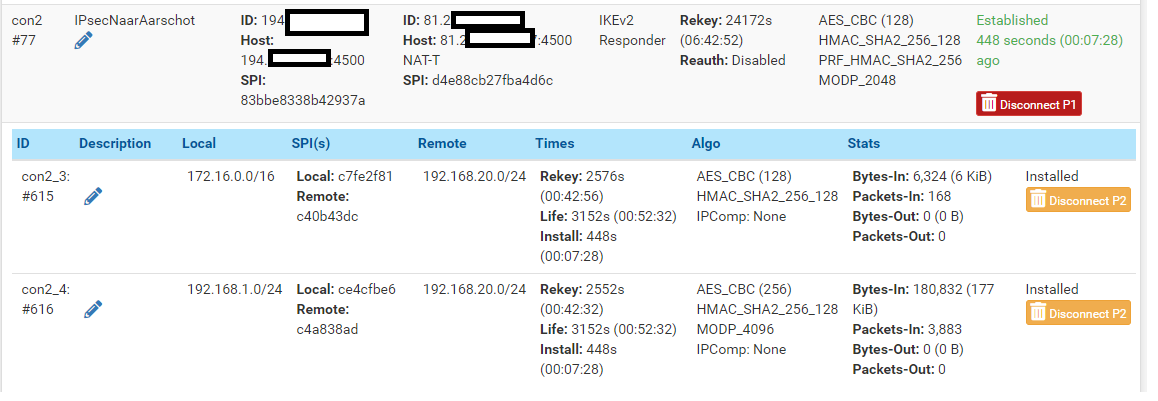
This all looks good.
This one from the main office to the 3rd party side:
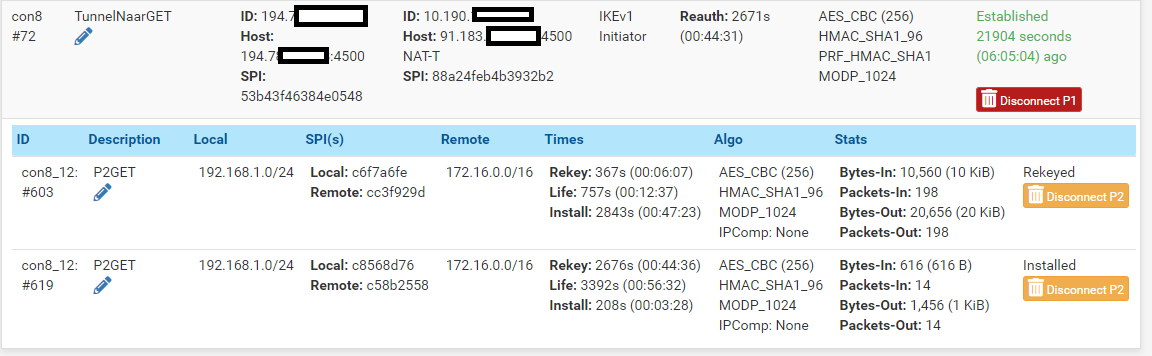
Which also looks connected.
Now at all the offices, there is a badge reader with ip 192.168.1.220 and that needs to send data to the 3rd party 91.183....
But nothing gets there? What am I missing ?
This is the first time ever I need to set this up... :( -
@nick-loenders said in Route traffic through ipsec tunnel:
Now at all the offices, there is a badge reader with ip 192.168.1.220
192.168.1.0/24 is the subnet at the main office. You cannot have this IP at the branches as well.
If you want to access the 3rd party network from the shown branch subnet, which is 192.168.20.0/24, you need to add a phase 2 for this subnet to the main - 3rd party connection or even enlarge the existing p 2, so that is includes all branch subnets.
Remember to make the changes on both sites.If you cannot change this connection you can only nat the traffic into you main subnet.
-
NO, sorry
the branch office have different 192.168.xx.xx ranges. The badgereader just has a .220 at the end , but different subnets.From the main office to the 3rd party (GET-tunnel) it is working.
Now I also noticed that from the branch offices I cannot even ping to a main office device.
Eg I am on 192.168.60.22 and ping to 192.168.1.11. This does NOT respond
If I ping from 192.168.1.11 to 192.168.60.22 , it DOES respond?!?!
-
@nick-loenders said in Route traffic through ipsec tunnel:
Eg I am on 192.168.60.22 and ping to 192.168.1.11. This does NOT respond
Ensure that there is a firewall rule in place on the main IPSec tab, which allows access from the branch.
It's also possible that the destination device itself is blocking access from outside of its subnet. If so you have to configure its firewall properly to accept remote site access.
-
@viragomann on the ipsec tab I allow any to any for all ports.
I also see traffic in the firewall logs....
I am getting crazy
-
@viragomann the pinging on the LAN 192.168.1.0 <-> other 192.168.xx.xx nets works again...
it was blocking BOGON networks on the LAN
Now only still the issue from the 192.168.xx branch office to the GET 172.16.0.0 that I need to solve
-
@viragomann We got it sorted out....
on the main the tunnel to the 3rd party on the local network was using 1.0/24 and this needed to be 0.0/16