block external requests via NAT — destination address "!LAN address" vs. "!This Firewall (self)"
-
the documentation guide says to use "!LAN address" as the destination address. any reason/s, for security or otherwise, to use or not to use "!This Firewall (self)" instead?
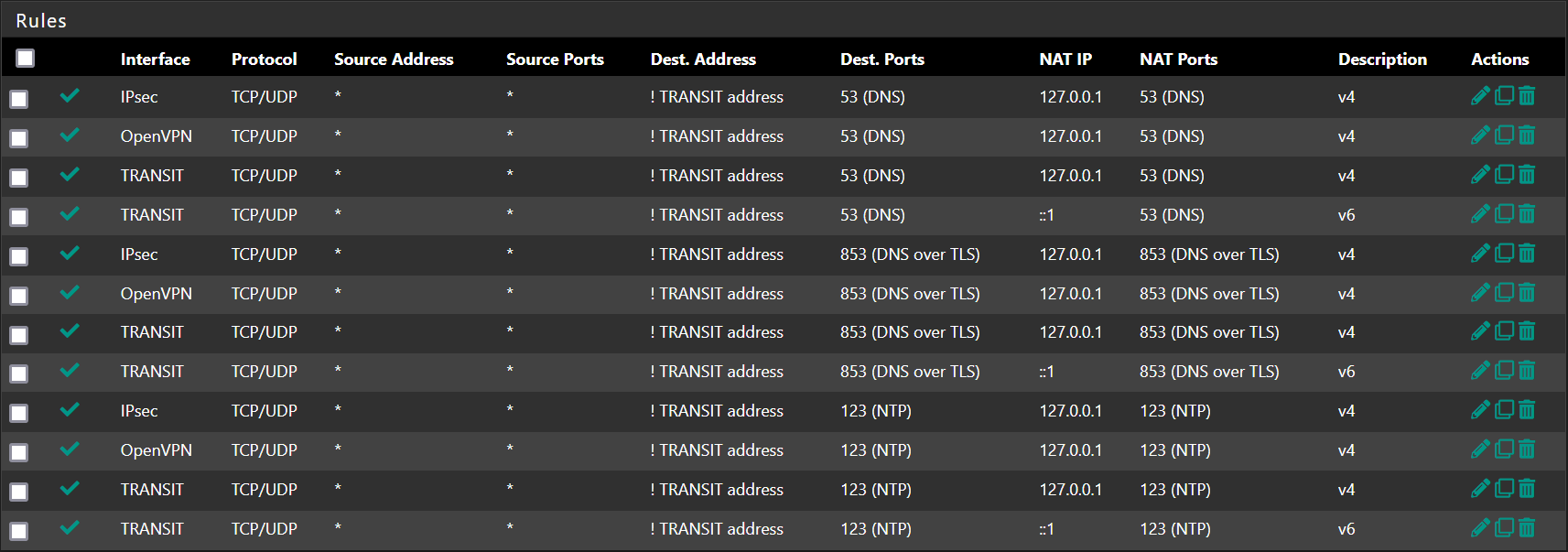
(i understand that "This Firewall (self)" already contains both IPv4 and IPv6 loopback addresses, and also includes addresses not assigned to the selected NAT interface.) -
@cyberconsultants said in block external requests via NAT — destination address "!LAN address" vs. "!This Firewall (self)":
the documentation guide says to use "!LAN address" as the destination address. any reason/s, for security or otherwise, to use or not to use "!This Firewall (self)" instead?
Not that I can think of for this purpose.
If you provide the DNS server by the pfSense DHCP it will use the interface IP with default settings. So basically no client might access any other pfSense IP, but it would be possible of course. I redirect all DNS and NTP requests on all my internal interfaces to my LAN address for instance.
But "This Firewall" should also fit for natting DNS.