2 wan don't work properly
-
Hi,
I have configured 2 WAN (TIM and FASTWEB) and 2 LAN segments (LAN and WLAN), but I cannot access from the internet WAN 2 (FASTWEB) to the WEB server into LAN segment (ALIGHIERO).
From inside WLAN, by DNS Resolver I can reach the WEB server but from outside the pfsense by the WAN 2 (FASTWEB) ... NO! If I try by the WAN1 (TIM) it works.The interface LAN has as gateway the WAN1 (TIM), the interface WLAN has as gateway the WAN2 (FASTWEB).
What can I do to solve this problem?
Thak youI have configured two groups of gateway
one with WAN1 (TIM) as hight priority and WAN2 (FASTWEB) as low priority (INTERNET_TIM)
the second gateway group in opposite priority (INTERNET_FW).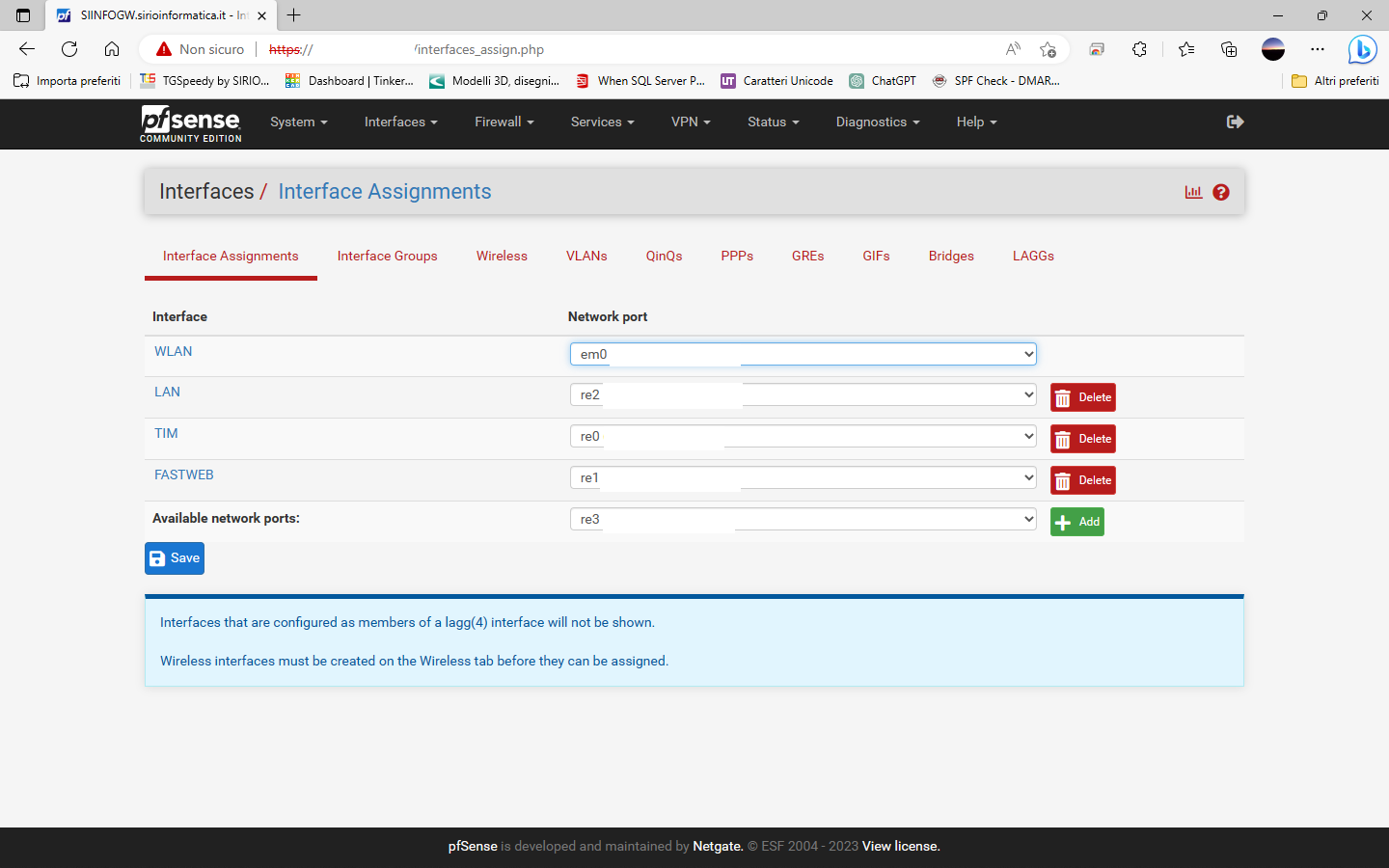
I have defined also a group for the WAN interfaces.
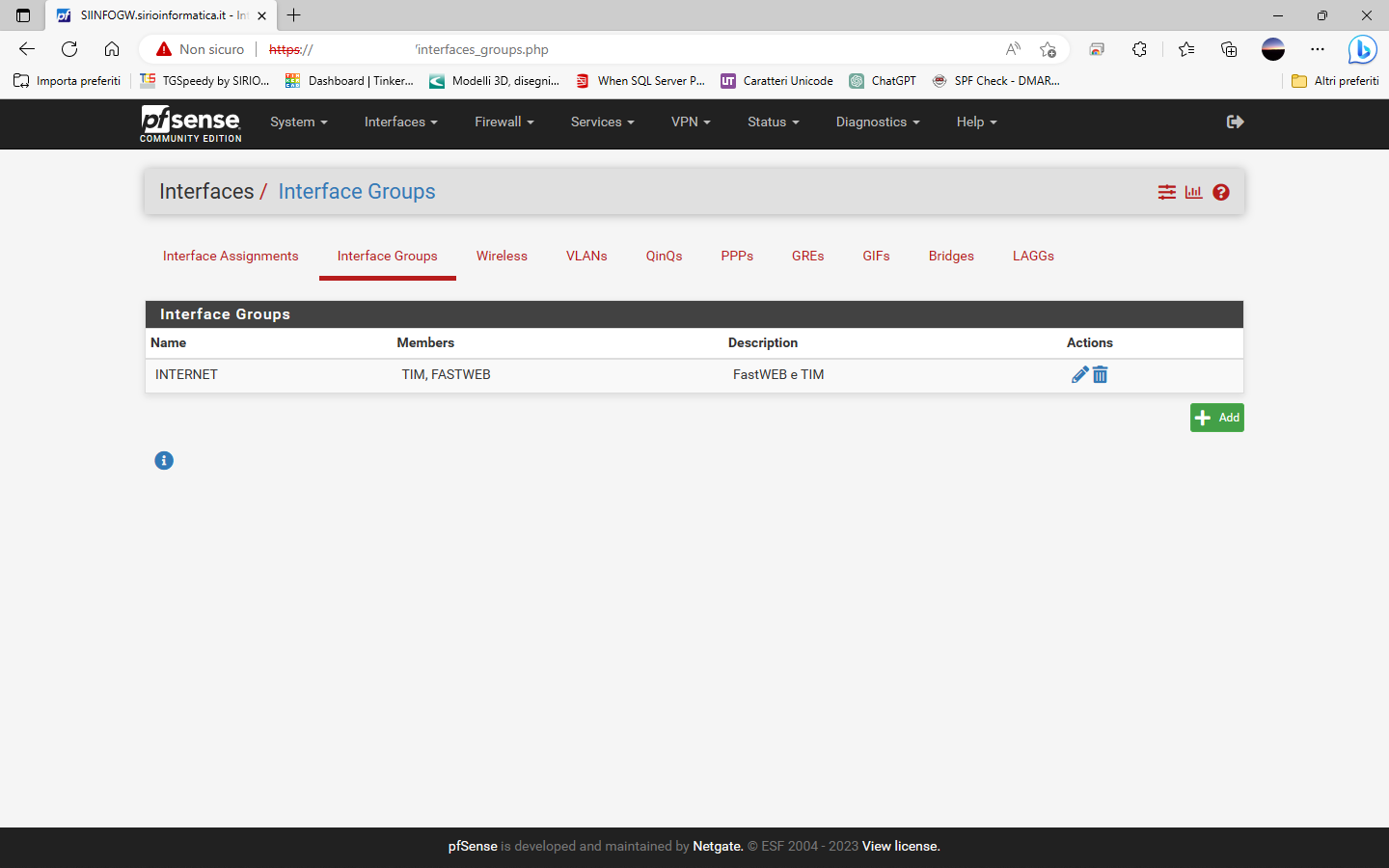
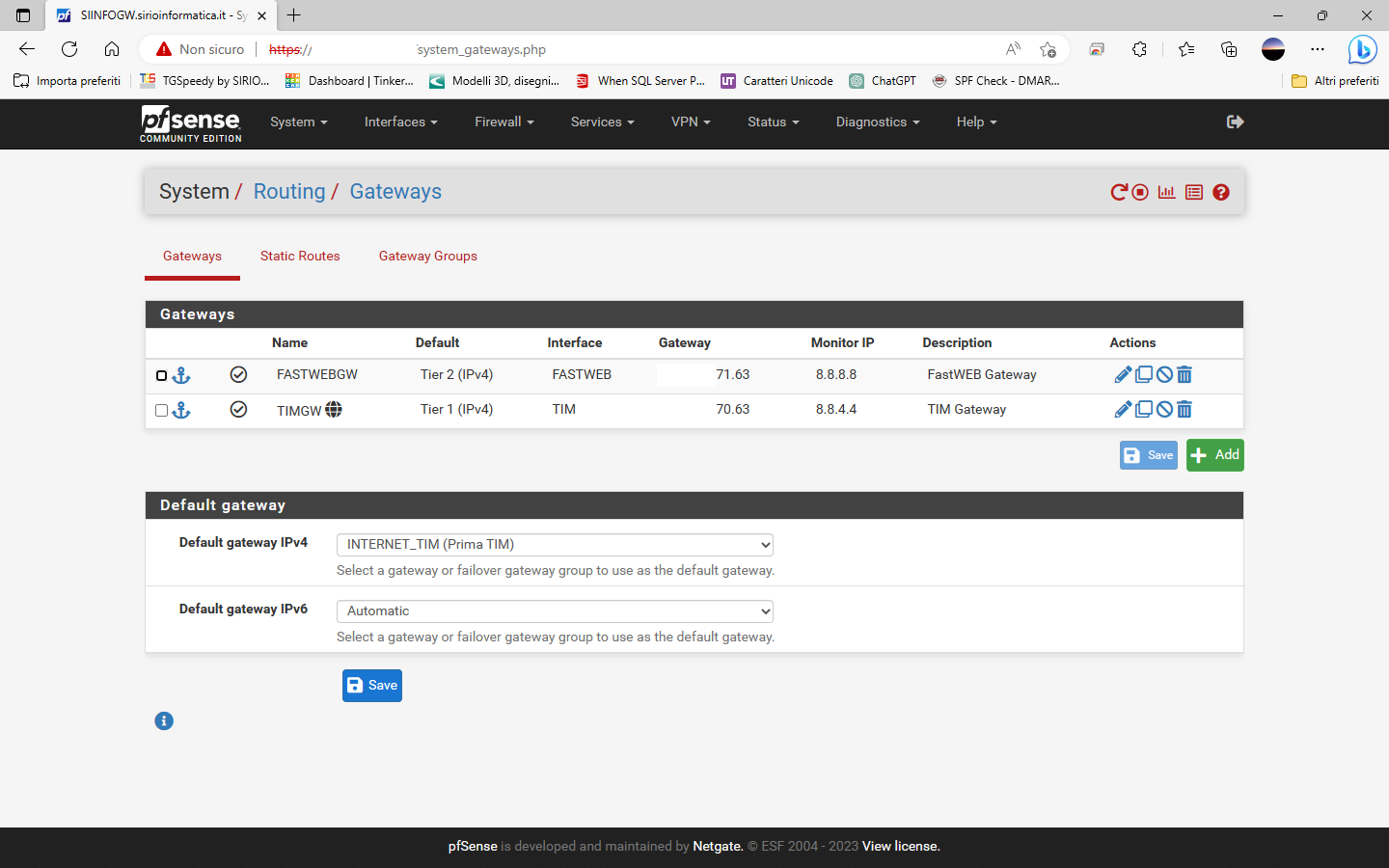
So I have configured all as shown
ROUTING
NAT
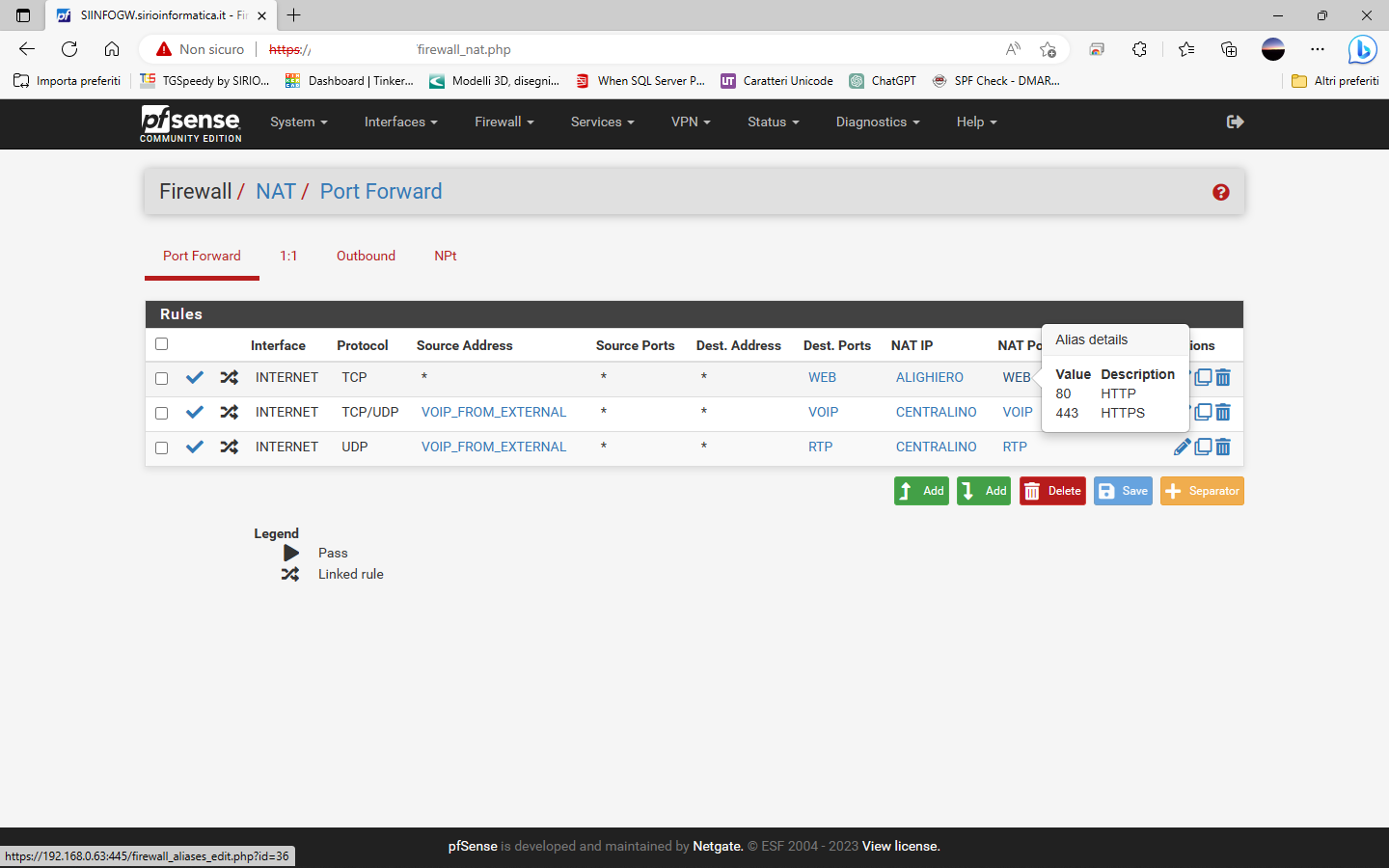
RULES
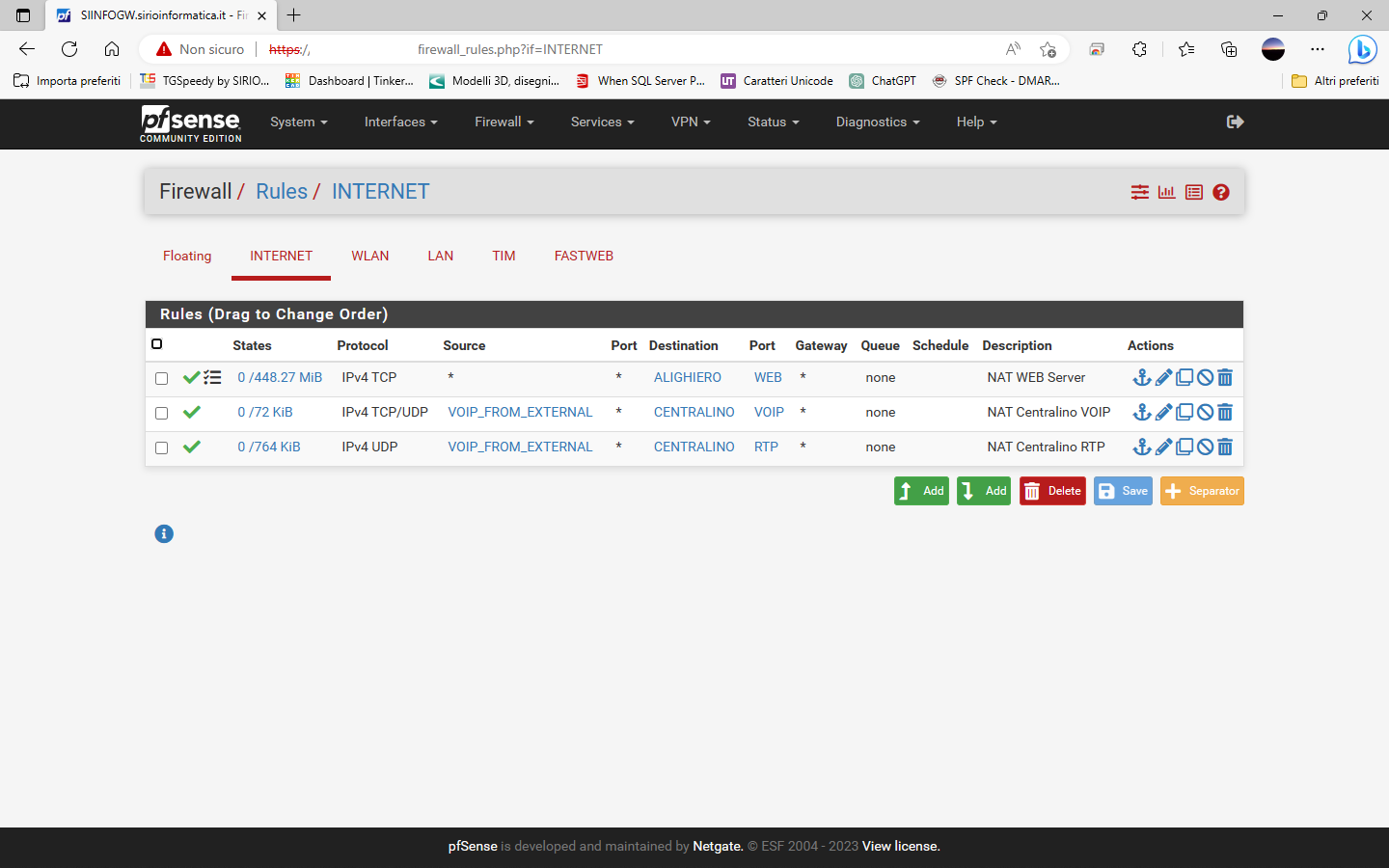
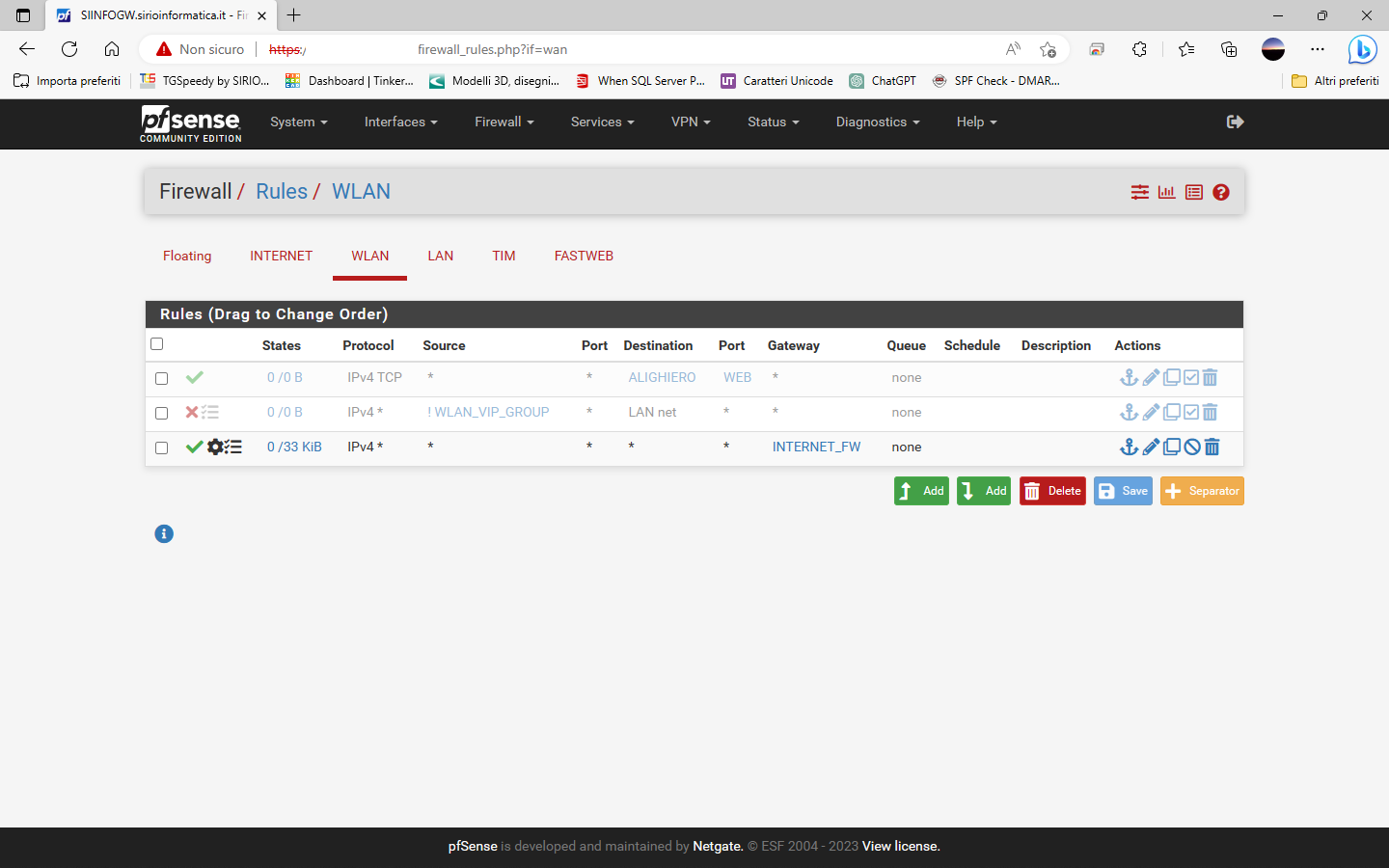
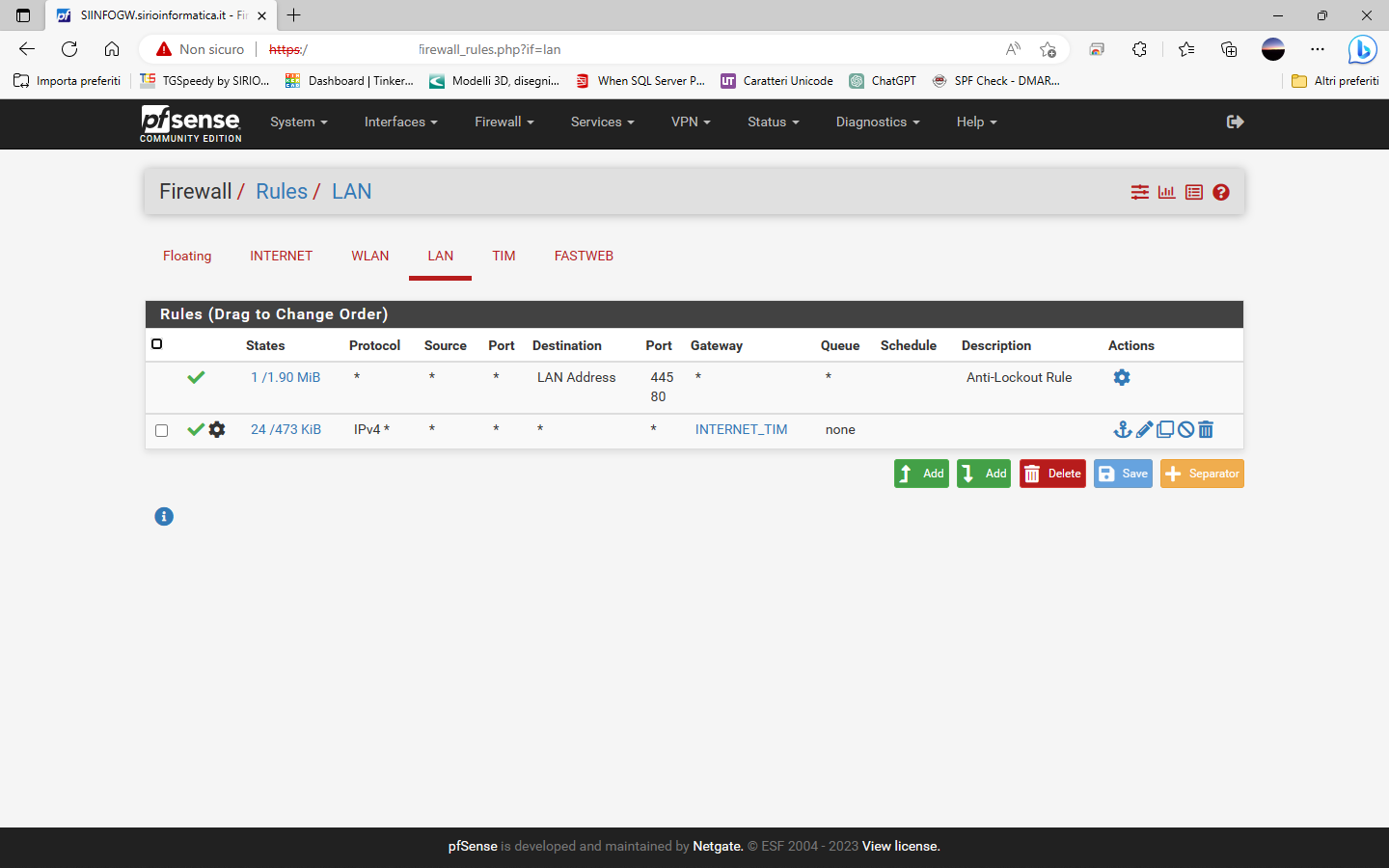
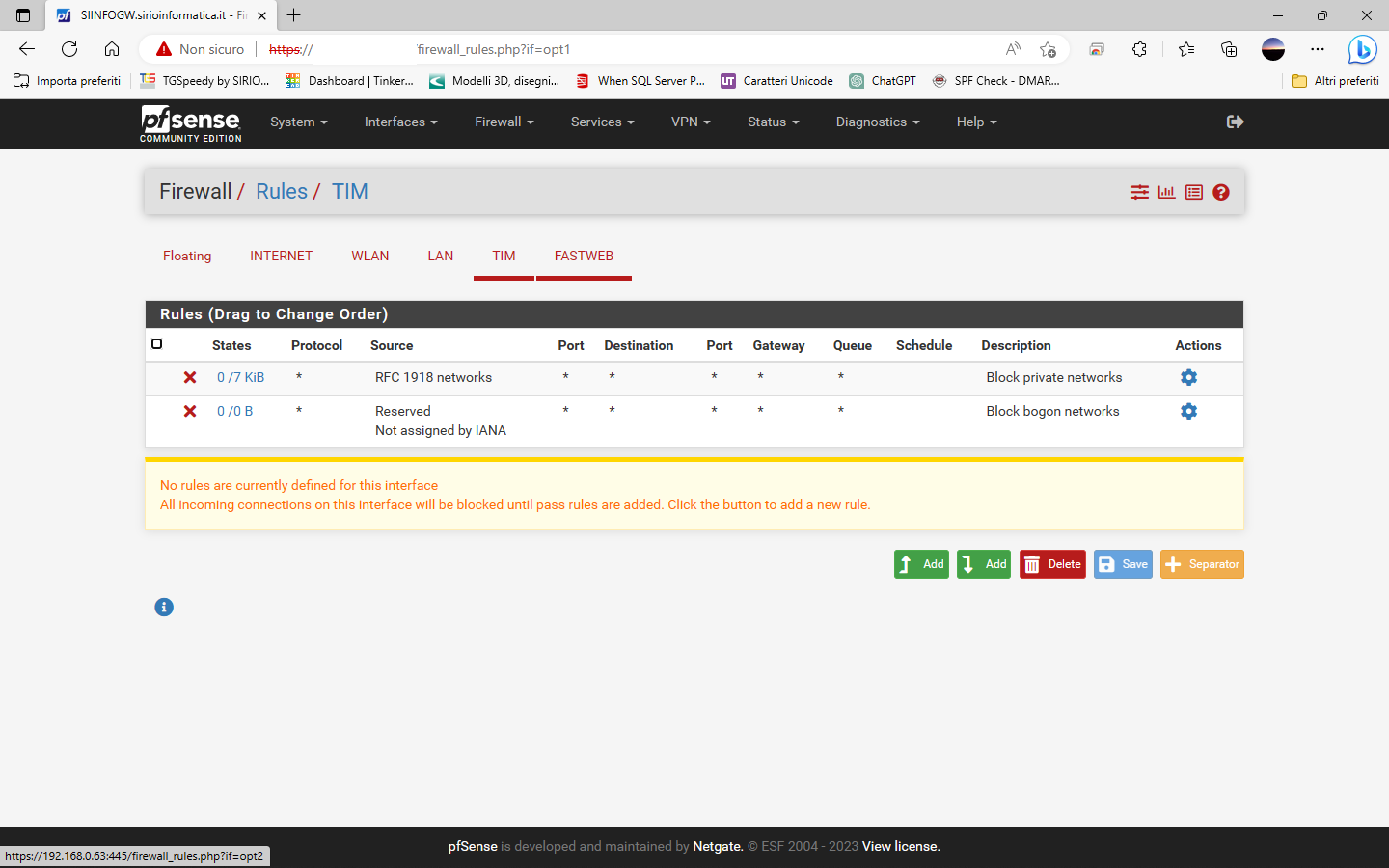
DNS Resolver
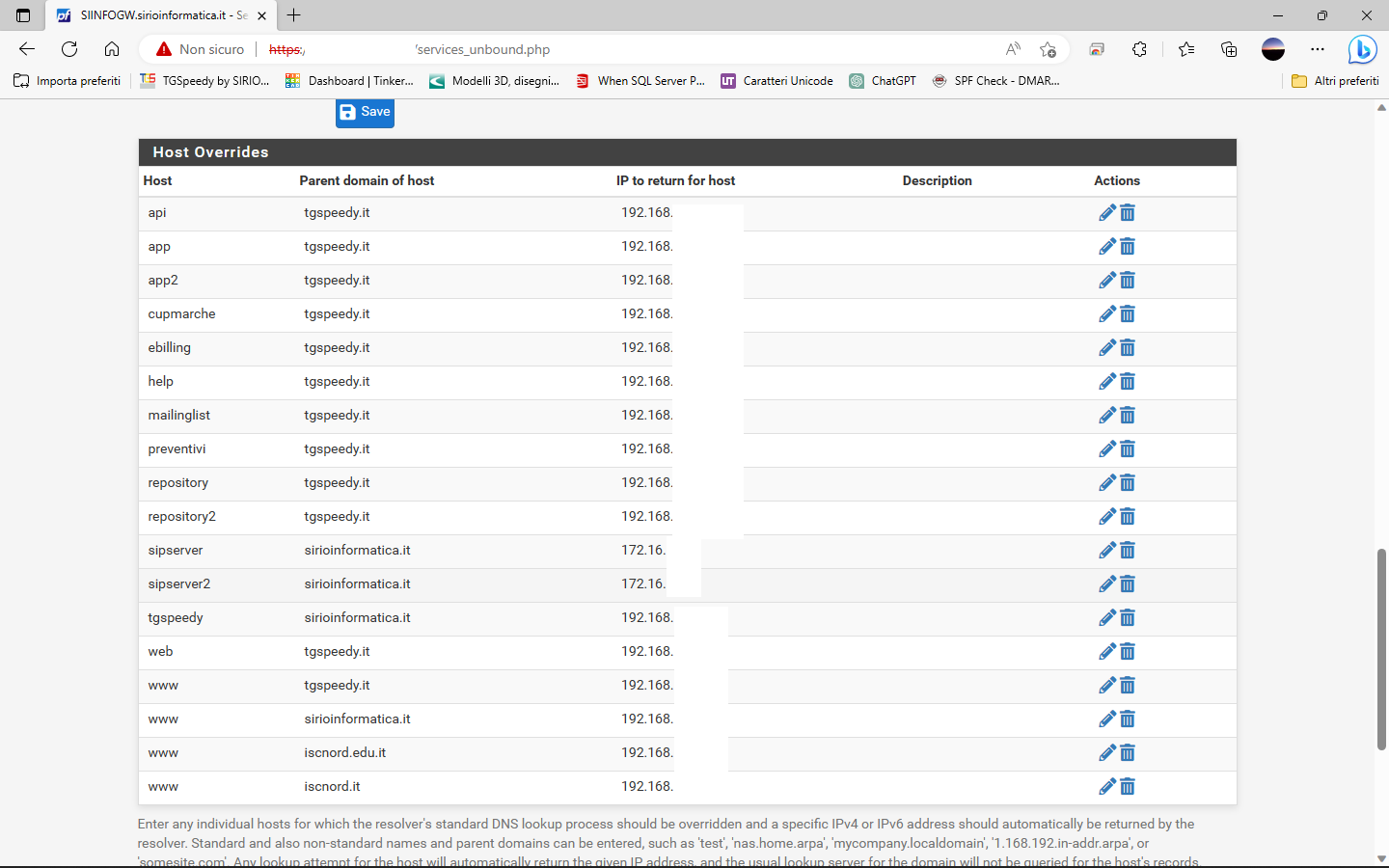
-
@sirioinformatica
Dual WAN doesn't work with pass rules for incoming traffic on the interface group. You have to remove these rules an state them on each interface. -
So, if I set the rule for the INTERNET interface group, pfsense don't applies this rule to all real interface inside the group?
If so, I try soon your way.
Thank you -
@sirioinformatica
It does though and the request will reach the destination device, but reply packets from it will be routed to the default gateway, regardless which interface the request was coming in.To treat this correctly, pfSense use a reply-to tag. This is added to a connection, when the request is coming in on an interface, which has a gateway stated. The tag contains the gateway of the interface. Replies are routed to this gateway then.
The tagging is done by the firewall rule, which passes the request packet in. However, this requires that the gateway is unique and hence so the interface for plausible reasons. But that's not true for a gateway group or a floating rules.
-
@viragomann Greet!!! It Works!
I have only one problem to solve:
i have the domain videosorveglianza.sirioinformatica.it and I have added DNS Resolver to point directly on web server ALIGHIERO (LAN segment) when I am in LAN or WLAN segments.The url is associated with the public IP of WAN FASTWEB.
The WEB Server ALIGHIERO has a rewrite rule that allow me to redirect the request to another server in WLAN segment.
The NAT and FW rules seem to be ok.
When I try from inside the WLAN or LAN segment, the server responds, but when I try from outside the pfsense (from Internet) the server shows the login page but the IIS Rewrite rule don't redirect the traffic to the proper server.
It seems that the IIS WEB server (ALIGHIERO) don't receive the host name when the request came from outside pfsense. How can I do to investigate this issue?
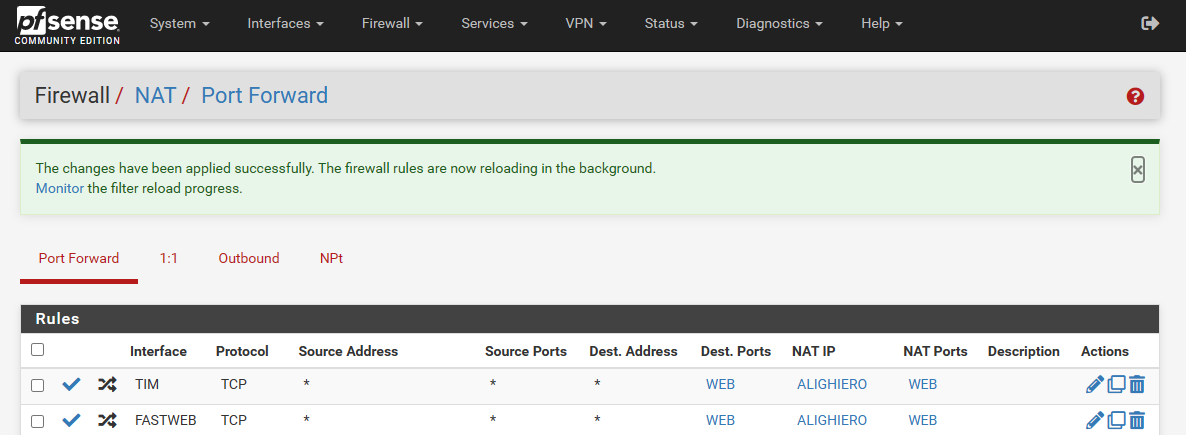
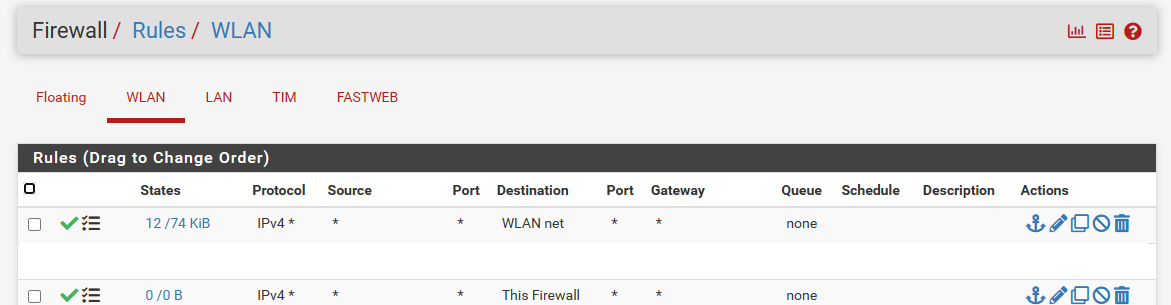
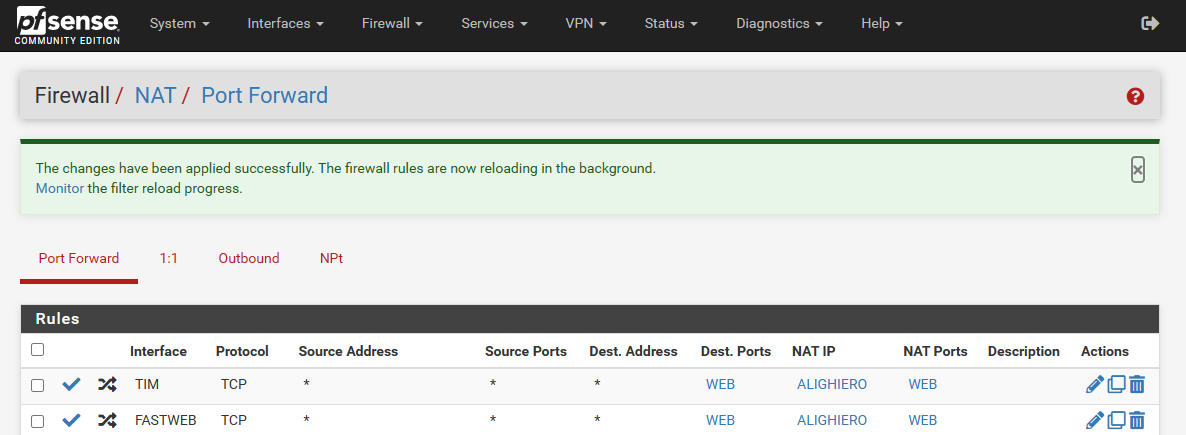
Thank you
-
@sirioinformatica said in 2 wan don't work properly:
The WEB Server ALIGHIERO has a rewrite rule that allow me to redirect the request to another server in WLAN segment.
How does this work exactly?
If this is a client side redirecting (301, 302) to another host name, you need to add it to the public DNS. Did you do this?
-
@viragomann
I use a local (WLAN) IP address as destination address of the true web server. This is the rewrite rule<configuration> <system.webServer> <rewrite> <rules> <clear /> <rule name="ReverseProxyInboundRule1" stopProcessing="true"> <match url="(.*)" /> <conditions> <add input="{CACHE_URL}" pattern="^(https?)://" /> </conditions> <action type="Rewrite" url="{C:1}://IPADDRESS_OF_WLAN_MACHINE:PORTNUMBER/{R:1}" /> </rule> </rules> <outboundRules> <rule name="ReverseProxyOutboundRule1" preCondition="ResponseIsHtml1"> <match filterByTags="A, Form, Img" pattern="^http(s)?://IPADDRESS_OF_WLAN_MACHINE:PORTNUMBER/(.*)" /> <action type="Rewrite" value="http{R:1}://videosorveglianza.sirioinformatica.it/{R:2}" /> </rule> <preConditions> <preCondition name="ResponseIsHtml" logicalGrouping="MatchAny"> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/html" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/javascript" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/css" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/plain" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/xml" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^application/javascript" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^application/xhtml+xml" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^application/json" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^application/ld+json" /> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^application/xml" /> </preCondition> <preCondition name="NeedRestoringAcceptEncoding"> <add input="{HTTP_X_ORIGINAL_ACCEPT_ENCODING}" pattern=".*" /> </preCondition> <preCondition name="ResponseIsHtml1"> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/html" /> </preCondition> </preConditions> </outboundRules> </rewrite> </system.webServer> </configuration> -
@sirioinformatica
This is a sort of proxying and it forward certain requests to another server.I suspect, it is forwarding the requests with the origin source IP and the destination server is responding directly to it. If you're unsure check this out with Diagnostic > Packet Capture.
If this is the case, pfSense will not pass the respond through, since it has no state for the responding server.