Is this possible? Does it make any sense to do so? Is this the right hardware to do it?
-
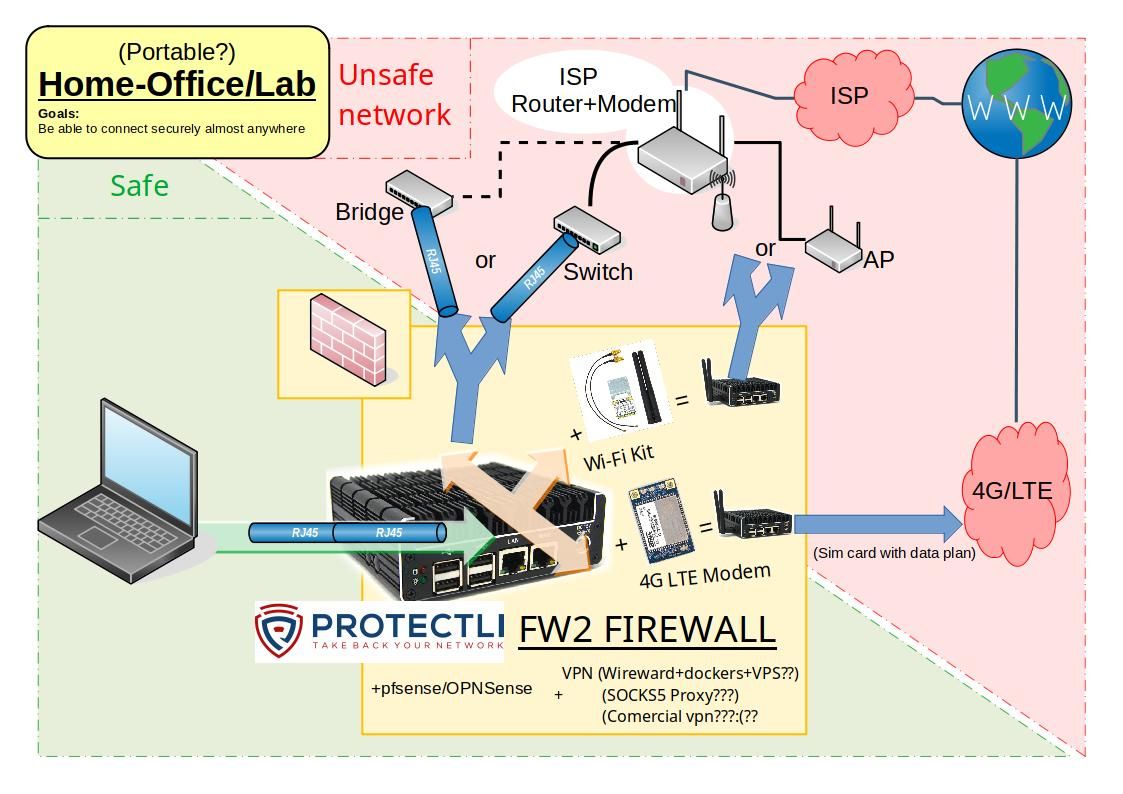
The goal would be to have a security layer between an insecure network and the device I want to secure.Ideally it would be a versatile system, since I plan to undertake a trip (while teleworking, which is not allowed by my company). And I do not know how will be the networks to which I will have to connect, that's why I thought about PROTECTLI, because if I'm not mistaken, using different configurations it is possible to connect either via WAN to the switch or router, via wireless wan to an AP/repeater or to the router itself, or even with a 4G LTE module using a sim card with a data plan.
This is why I have included all possible configurations in the diagram.
Is this true or am I wrong? I am talking about that the protectli would always be behind the router, never before, and in most cases it will not be possible to put the main router in bridge mode...
I was thinking of configuring the device more as a vpnrouter as a firewall, the idea would be to hire a vps to create a vpn itself and configure it in the Protectli, to connect me wherever I go, and that all my traffic would be safe through the vpn, both for security issues when using untrusted networks, and to avoid problems due to geolocation, because when travel, this can be a problem, I would like that my computer not only be completely separated from the networks to which I am going to connect, but also that it thinks that it is always connecting from the same place (the vps in my country). And when the trip ends, i plan to use the exact same set-up (pfsense behind router) in my home, to separate my insecure home network from the important working device.
Any advice? Would it be possible to build something like this? I don't have much if not any experience in networks, but I found it an interesting project and with which I can learn many things.
Any advice on what would be the best way to tunnel all my traffic? -
Take the Protecli for your home with pfSense, but for the journey you should have a look for a
GL.iNet AXT1800 (Slate AX) connect it to your smartphone
and to your computer and you are online, 30+ VPN services will be able to use with it. Small, powerful and all you need. -
@dobby_ Or a GL-AX3000.
Ted
-
- The AP should be on the LAN not Wan side of pfsense (your firewall).
- ISP modem router in bridge mode so is only a modem (not a router or AP).
-
@dobby_ said in Is this possible? Does it make any sense to do so? Is this the right hardware to do it?:
Take the Protecli for your home with pfSense, but for the journey you should have a look for a
GL.iNet AXT1800 (Slate AX) connect it to your smartphone
and to your computer and you are online, 30+ VPN services will be able to use with it. Small, powerful and all you need.Thanks for the advice! i will keep it in mind!!
But the point of this set up was that it can be reconverted, and also have the ability to connect to public wi-fi's (in wireless wan mode) saving me from having to pay for my own data plan.
I haven't stopped to look at travel routers since I don't have enough budget to buy several devices for this project and the protectli seemed to me a very good idea because of its versatility, since I can always end up reusing it for something else, besides instead of a proprietary firmware with a simplistic GUI, I want this project to help me learn about pfsense, vpn's and networks in general.
-
This post is deleted! -
@patch said in Is this possible? Does it make any sense to do so? Is this the right hardware to do it?:
- The AP should be on the LAN not Wan side of pfsense (your firewall).
- ISP modem router in bridge mode so is only a modem (not a router or AP).
The problem is that I pretend to connect to random public WiFi's.
So in this case, the AP is not for me to have wireless connection, it is a random AP to which I want to connect (Wireless WAN). And asking them to put the router in bridge mode I guess that is not going to be an option either...

-
@consistent_plum3631 said in Is this possible? Does it make any sense to do so? Is this the right hardware to do it?:
in this case, the AP is not for me to have wireless connection,
Oops you are correct
You are building a router with 3 WAN connections so all three need to be on the WAN side of pfsense (and not for access by your other devices other than via pfsense). -
I haven't stopped to look at travel routers since
I don't have enough budget to buy several
devices for this projectGL-SFT1200 (Opal) save WLAN-Router for travelers – AC1200 Dualband-Gigabit-Wireless-Internet-Router | IPv6 | USB-2.0 | MU-MIMO | 128 MB Arbeitsspeicher | Repeater-Brücke | Access Point-Modus
45 € Router
20 € BagAs a AP, as a repeater, connect and feed over powerbank, USB C, 3 WAN/LAN Ports WiFi AC small and able to carry
inside of your backpack or a greater pocket!and the protectli seemed to me a very good idea
because of its versatility,It is not able to feed over a powerbank, and is not that
I would prefer to carry the whole day around elsewhere
I go! You sit on a green inside of a park and the GL router
is able to connect you via; WiFi, USB LTE modem, over
your smartphone and can be powered over the Laptop or
a small powerbank. Try this with the Protectli please.since I can always end up reusing it for something else,
You can also that router reuse again. The Protectli is for home usage and the GL ones are for travelers or traveling.
besides instead of a proprietary firmware with a simplistic GUI,
OpenWRT is fine.
I want this project to help me learn about pfsense,
vpn's and networks in general.You could do more by using pfSense at home and OpenWRT in the wild or outside.