freeRadius / Unifi AP / EAP-TTLS ?
-
@nogbadthebad said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom Have you added the AP into FreeRADIUS NAS/Clients page ?
A radsniff-x from a console may point to the problem.
Thanks! I keep forgetting about that! A lot going on right now... I will see if that may give any new leads! :)
I am trying it now, and I have rarely seen less traffic... :)
But I'm thinking, as freeRadius isn't really configured yet, will there be anything for it to find? From the name I'd suppose it only shows radius related traffic, right?
The step I have issues with is to be used with radius, but really a function of basic pfSense as I understands it..?
-
I tried to uninstall everything, including all settings, but even when unchecking the setting in freeRadius v0.15.10
Save settings after deletion "If enabled, the settings will be preserved across package reinstalls. Important: If disabled, all settings will be wiped on package uninstall/reinstall/upgrade."steps;
- unchecked above setting in freeradius/settings - Saved
- uninstalled the package using package manager - rebooted
- installed freeradius
- created a Authentication server for Radius
... discovered all my previous settings was still there...
I can't seem to catch a break with this lately. Can I ssh in and wipe settings there, or are they scattered through out?
I am usually so impressed with Netgate and pfSense, but this is kinda getting to me a little. It just don't feel that robust right now with all things considered.
Maybe a good set of sectioned backups for all I think I need and a hard reset is the answer... But really don't feel much for it tbh. Wonder if other firewalls have similar issues... :/
-
@furom Did you try running radsniff -x from the console ?
-
@nogbadthebad said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom Did you try running radsniff -x from the console ?
Not just that, no. Perhaps I overthink it, but shouldn't I specify an interface? I will give radsniff -x a go as soon as I get SSH setup again... :)
-
@furom I run eap-tls with one of my ssids on unifi, and use freerad on pfsense as auth.. I don't recall any issues with setting it up.. I had it off for a while when my company locked down my phone and prevented me from installing the profile on my phone with the certs. But recently re-enabled it and not having any problems.. if you want I could post my configurations up.
-
@furom If you don’t see any thing output from radsniff -x it’s highly likely that the ap isn’t set up correctly.
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom I run eap-tls with one of my ssids on unifi, and use freerad on pfsense as auth.. I don't recall any issues with setting it up.. I had it off for a while when my company locked down my phone and prevented me from installing the profile on my phone with the certs. But recently re-enabled it and not having any problems.. if you want I could post my configurations up.
I would really appreciate that, thanks!
-
@nogbadthebad said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom If you don’t see any thing output from radsniff -x it’s highly likely that the ap isn’t set up correctly.
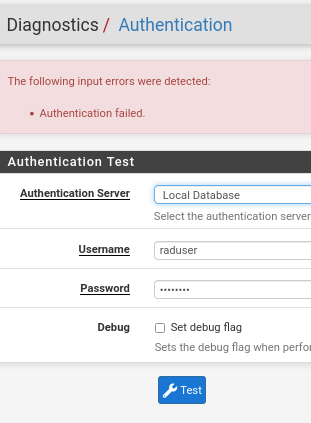
Well, either that, agreed, or something more intricate. As I said before, I set up a user, and am unable to validate it in Diagnostics, no matter how simple secrets & passwords... I don't think a system can be haunted, but sometimes wonder... well, I hope not.
-
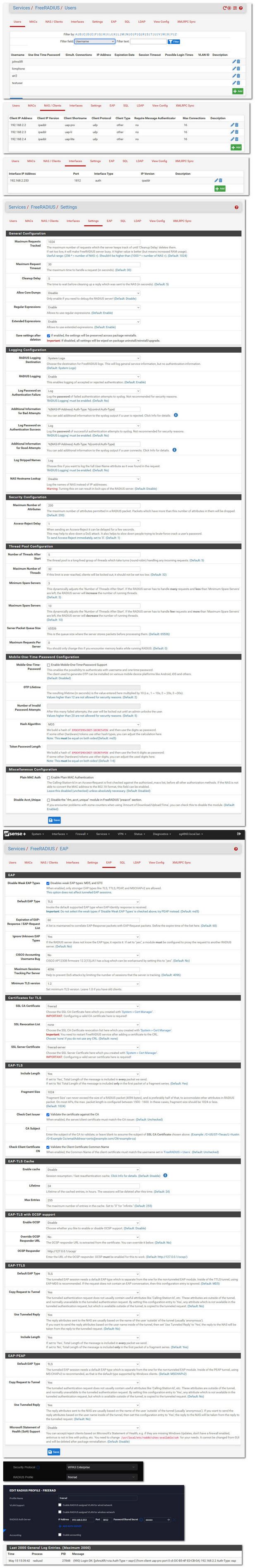
@furom here you go
Config from pfsense freerad, settings for my ssid, and the freerad profile that tells the unifi where to go.. And then at the end you can see my phone authing..
-
@johnpoz OMG. That is so helpful! Much appreciated!! It's a bit late to start with that right now, but will try it out tomorrow! :)
-
@furom if you need any help - just ask... I do like using a secure eap like eap-tls for my trusted devices on my trust wifi vlan.. I just wish iot devices supported wpa enterprise ;)
edit:
keep in mind you do need certs for these users - and getting the profile into say ios can be problematic - it doesn't like no password, etc. so I believe I run it through openssl to create the bundle, etc.edit2: just noticed using old cert for my old phone ;) I now have a 13, but its using my old XR cert heheh
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom if you need any help - just ask... I do like using a secure eap like eap-tls for my trusted devices on my trust wifi vlan.. I just wish iot devices supported wpa enterprise ;)
edit:
keep in mind you do need certs for these users - and getting the profile into say ios can be problematic - it doesn't like no password, etc. so I believe I run it through openssl to create the bundle, etc.edit2: just noticed using old cert for my old phone ;) I now have a 13, but its using my old XR cert heheh
Good points, I do have the certs I need at least, and know they're good. So a starting point at least, and with all this great help I can't think of what could go south... :)
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom if you need any help - just ask...
Hi there :) So much at the sam time, but now finally time for EAP-TLS, after all trouble I'm actually a little hesitant to even try, but I do want it too...
Did you follow any special path or just mended it together? One thing that I see others do, is creating a new separate "Authentication server" for radius, I can't tell if you did so too. This step was one that always failed before...
-
@furom you do need too point to freerad on your unifi setup.. Not even sure if you can fire up multiple configs for freerad on pfsense?
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom you do need too point to freerad on your unifi setup.. Not even sure if you can fire up multiple configs for freerad on pfsense?
Multiple configs? But yes, the Unifi part is clear I think. What is a little unclear is if this is needed or not?
-
@furom This is well, embarrassing. I have done to the letter almost what you have. All the options the same etc.
But... same step relentlessly fails; verifying the user I create for radius... I have tried with a password I would like, with a very simple one, and it just won't work.
Secret is copy/pasted, so is most other duplicated stuff.
I will let it be now as you perhaps may have an idea where to look...I finally ran
[root@netgate ~]# radsniff -x Logging all events Defaulting to capture on all interfaceswhich did not show one single thing, so at least it is a big mistake somewhere...
Thanks :)
-
@furom well if you don't send any traffic why do you think radsniff would show anything?
[23.01-RELEASE][admin@sg4860.local.lan]/: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0) 2023-05-19 07:29:29.633522 (1) Access-Request Id 76 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.000 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400 Called-Station-Id = "92-2A-A8-15-4F-07:eaptest" Calling-Station-Id = "DC-B5-4F-E0-CB-0A" NAS-Identifier = "922aa8154f07" NAS-Port-Type = Wireless-802.11 Acct-Session-Id = "F22A1795681CA8E9" Acct-Multi-Session-Id = "1FBA6C367EEA3D0E" Connect-Info = "CONNECT 0Mbps 802.11b" EAP-Message = 0x0241000c016a6f686e735852 Message-Authenticator = 0x07fa33cc7e4eb7acc79a17fc51b1276f WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027077 WLAN-Group-Mgmt-Cipher = 1027078 Authenticator-Field = 0xdbf20706c363d971214aa2a50eff8e22 2023-05-19 07:29:29.634308 (2) Access-Challenge Id 76 igb2:192.168.2.2:53793 <- 192.168.2.253:1812 +0.000 +0.000 State = 0x4abf79174afd74c05dc342dc6c275b1e EAP-Message = 0x014200060d20 Message-Authenticator = 0xe7b9757cb805f64be57083a81435aa69 Authenticator-Field = 0x61e113e6640f7b6fb3e8cd28e74b1904 2023-05-19 07:29:29.676761 (3) Access-Request Id 77 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.043 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400Here is my phone coming in from trying to talk one of my AP on 192.168.2.2, do you have a firewall rule setup to allow your AP ips to talk to freerad on port 1812?
radsniff would not have anything to do with your setup of freerad, but if stuff is trying to auth to you. You would need to have firewall rules to allow that traffic - sorry if I left that off, but pretty basic that if you have a service listening on 1812, that stuff is going to talk to - your firewall rules would have to allow that.
As to setting up authentication server in pfsense - why would that have anything to do with freerad authing users for other devices.. No you don't need to setup anything there.
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom well if you don't send any traffic why do you think radsniff would show anything?
I set up radsniff and then tried to diag/auth, but didn't exactly show much.
[23.01-RELEASE][admin@sg4860.local.lan]/: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0) 2023-05-19 07:29:29.633522 (1) Access-Request Id 76 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.000 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400 Called-Station-Id = "92-2A-A8-15-4F-07:eaptest" Calling-Station-Id = "DC-B5-4F-E0-CB-0A" NAS-Identifier = "922aa8154f07" NAS-Port-Type = Wireless-802.11 Acct-Session-Id = "F22A1795681CA8E9" Acct-Multi-Session-Id = "1FBA6C367EEA3D0E" Connect-Info = "CONNECT 0Mbps 802.11b" EAP-Message = 0x0241000c016a6f686e735852 Message-Authenticator = 0x07fa33cc7e4eb7acc79a17fc51b1276f WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027077 WLAN-Group-Mgmt-Cipher = 1027078 Authenticator-Field = 0xdbf20706c363d971214aa2a50eff8e22 2023-05-19 07:29:29.634308 (2) Access-Challenge Id 76 igb2:192.168.2.2:53793 <- 192.168.2.253:1812 +0.000 +0.000 State = 0x4abf79174afd74c05dc342dc6c275b1e EAP-Message = 0x014200060d20 Message-Authenticator = 0xe7b9757cb805f64be57083a81435aa69 Authenticator-Field = 0x61e113e6640f7b6fb3e8cd28e74b1904 2023-05-19 07:29:29.676761 (3) Access-Request Id 77 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.043 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400Here is my phone coming in from trying to talk one of my AP on 192.168.2.2, do you have a firewall rule setup to allow your AP ips to talk to freerad on port 1812?
radsniff would not have anything to do with your setup of freerad, but if stuff is trying to auth to you. You would need to have firewall rules to allow that traffic - sorry if I left that off, but pretty basic that if you have a service listening on 1812, that stuff is going to talk to - your firewall rules would have to allow that.
As to setting up authentication server in pfsense - why would that have anything to do with freerad authing users for other devices.. No you don't need to setup anything there.
Ok. And yes, of course I understand I need a firewall rule,
This should be permissive enough... I bet it's just a tiny thingy somewhere... I have to go over everything again...
-
@furom that rule that it has never been used, see the 0/0 do you have some other rule blocking? Maybe in floating or above that?
For unifi to send traffic, you would have to have set up unifi to send to pfsense IP, and then a client would have to try and auth that unifi would talk to your freerad with..
Here I went to my controller and ran a stupid radtest test that I knew would fail - but you can see that radsniff saw the traffic
user@NewUC:~$ radtest test test 192.168.2.253:1812 10 testing123 Sent Access-Request Id 198 from 0.0.0.0:58755 to 192.168.2.253:1812 length 74 User-Name = "test" User-Password = "test" NAS-IP-Address = 127.0.1.1 NAS-Port = 10 Message-Authenticator = 0x00 Cleartext-Password = "test"radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0) 2023-05-19 08:32:13.321600 (1) Access-Request Id 198 igb2:192.168.2.12:58755 -> 192.168.2.253:1812 +0.000 User-Name = "test" User-Password = "test" NAS-IP-Address = 127.0.1.1 NAS-Port = 10 Message-Authenticator = 0xbe0acd5dac7523393e41075bc4372ef1 Authenticator-Field = 0x02eb80a64c53946dfb0a3b65be7baac0 2023-05-19 08:32:18.324176 (1) ** rtx ** Access-Request Id 198 igb2:192.168.2.12:58755 -> 192.168.2.253:1812 +5.002 User-Name = "test" User-Password = "test" NAS-IP-Address = 127.0.1.1 NAS-Port = 10 Message-Authenticator = 0xbe0acd5dac7523393e41075bc4372ef1 Authenticator-Field = 0x02eb80a64c53946dfb0a3b65be7baac0Here this should give you how to test that freerad is running, etc..
edit: you know freerad doesn't even need to be running to test that traffic is actually getting to pfsense with radsniff
Here I turned off freerad on pfsense.
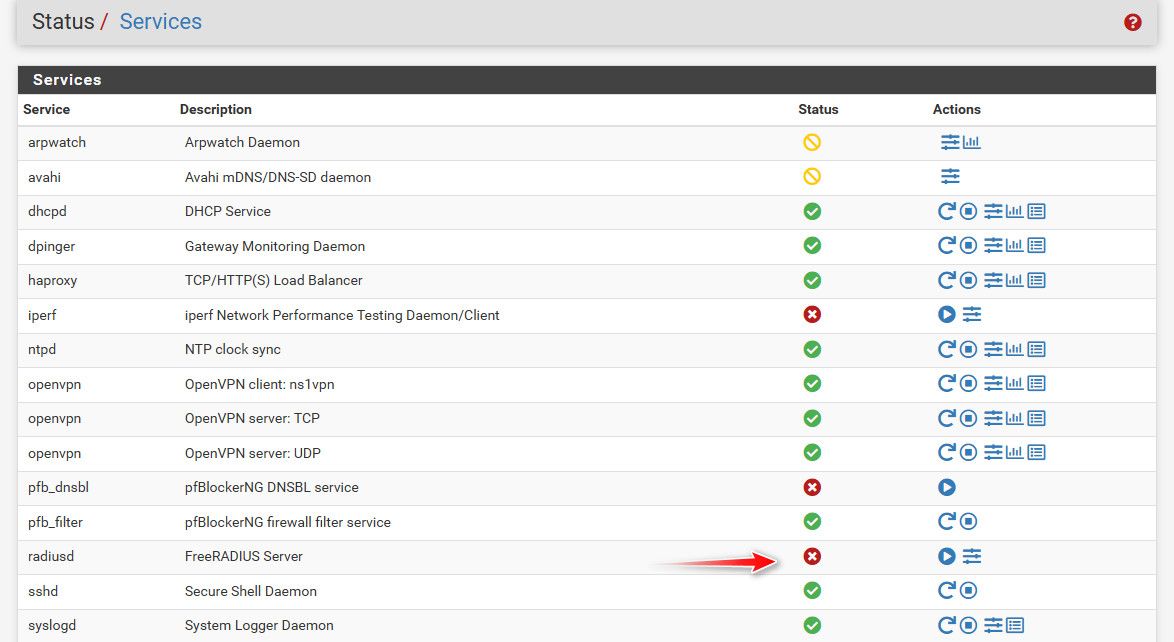
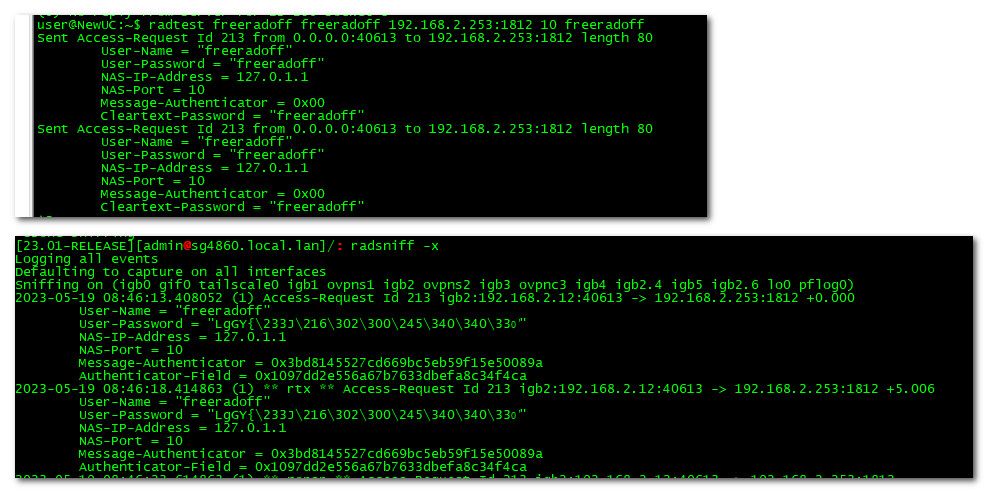
if you are not seeing radius traffic with radsniff then your not allowing it via firewall, or nothing is sending anything, or they are sending it to wrong IP or port..
-
@johnpoz I am about to test my wifi without radius just to see that it actually works... :/ Then add radius.
In floating I have this
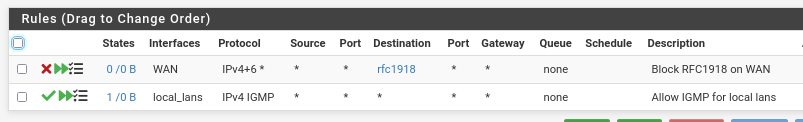
which as I understand shouldn't impact this...But the most basic still must be to get this diagnostic auth to pass, right? If that checks, all the rest will fall into place...