freeRadius / Unifi AP / EAP-TTLS ?
-
@furom you do need too point to freerad on your unifi setup.. Not even sure if you can fire up multiple configs for freerad on pfsense?
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom you do need too point to freerad on your unifi setup.. Not even sure if you can fire up multiple configs for freerad on pfsense?
Multiple configs? But yes, the Unifi part is clear I think. What is a little unclear is if this is needed or not?
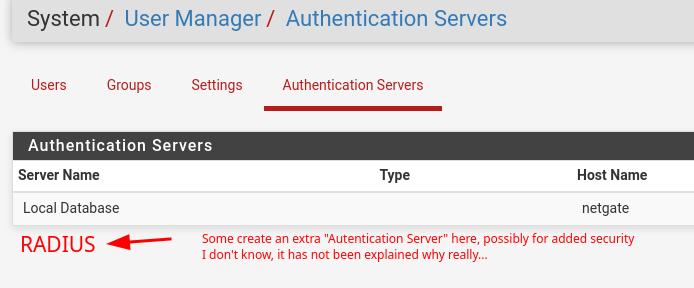
-
@furom This is well, embarrassing. I have done to the letter almost what you have. All the options the same etc.
But... same step relentlessly fails; verifying the user I create for radius... I have tried with a password I would like, with a very simple one, and it just won't work.
Secret is copy/pasted, so is most other duplicated stuff.
I will let it be now as you perhaps may have an idea where to look...I finally ran
[root@netgate ~]# radsniff -x Logging all events Defaulting to capture on all interfaceswhich did not show one single thing, so at least it is a big mistake somewhere...
Thanks :)
-
@furom well if you don't send any traffic why do you think radsniff would show anything?
[23.01-RELEASE][admin@sg4860.local.lan]/: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0) 2023-05-19 07:29:29.633522 (1) Access-Request Id 76 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.000 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400 Called-Station-Id = "92-2A-A8-15-4F-07:eaptest" Calling-Station-Id = "DC-B5-4F-E0-CB-0A" NAS-Identifier = "922aa8154f07" NAS-Port-Type = Wireless-802.11 Acct-Session-Id = "F22A1795681CA8E9" Acct-Multi-Session-Id = "1FBA6C367EEA3D0E" Connect-Info = "CONNECT 0Mbps 802.11b" EAP-Message = 0x0241000c016a6f686e735852 Message-Authenticator = 0x07fa33cc7e4eb7acc79a17fc51b1276f WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027077 WLAN-Group-Mgmt-Cipher = 1027078 Authenticator-Field = 0xdbf20706c363d971214aa2a50eff8e22 2023-05-19 07:29:29.634308 (2) Access-Challenge Id 76 igb2:192.168.2.2:53793 <- 192.168.2.253:1812 +0.000 +0.000 State = 0x4abf79174afd74c05dc342dc6c275b1e EAP-Message = 0x014200060d20 Message-Authenticator = 0xe7b9757cb805f64be57083a81435aa69 Authenticator-Field = 0x61e113e6640f7b6fb3e8cd28e74b1904 2023-05-19 07:29:29.676761 (3) Access-Request Id 77 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.043 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400Here is my phone coming in from trying to talk one of my AP on 192.168.2.2, do you have a firewall rule setup to allow your AP ips to talk to freerad on port 1812?
radsniff would not have anything to do with your setup of freerad, but if stuff is trying to auth to you. You would need to have firewall rules to allow that traffic - sorry if I left that off, but pretty basic that if you have a service listening on 1812, that stuff is going to talk to - your firewall rules would have to allow that.
As to setting up authentication server in pfsense - why would that have anything to do with freerad authing users for other devices.. No you don't need to setup anything there.
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom well if you don't send any traffic why do you think radsniff would show anything?
I set up radsniff and then tried to diag/auth, but didn't exactly show much.
[23.01-RELEASE][admin@sg4860.local.lan]/: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0) 2023-05-19 07:29:29.633522 (1) Access-Request Id 76 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.000 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400 Called-Station-Id = "92-2A-A8-15-4F-07:eaptest" Calling-Station-Id = "DC-B5-4F-E0-CB-0A" NAS-Identifier = "922aa8154f07" NAS-Port-Type = Wireless-802.11 Acct-Session-Id = "F22A1795681CA8E9" Acct-Multi-Session-Id = "1FBA6C367EEA3D0E" Connect-Info = "CONNECT 0Mbps 802.11b" EAP-Message = 0x0241000c016a6f686e735852 Message-Authenticator = 0x07fa33cc7e4eb7acc79a17fc51b1276f WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027077 WLAN-Group-Mgmt-Cipher = 1027078 Authenticator-Field = 0xdbf20706c363d971214aa2a50eff8e22 2023-05-19 07:29:29.634308 (2) Access-Challenge Id 76 igb2:192.168.2.2:53793 <- 192.168.2.253:1812 +0.000 +0.000 State = 0x4abf79174afd74c05dc342dc6c275b1e EAP-Message = 0x014200060d20 Message-Authenticator = 0xe7b9757cb805f64be57083a81435aa69 Authenticator-Field = 0x61e113e6640f7b6fb3e8cd28e74b1904 2023-05-19 07:29:29.676761 (3) Access-Request Id 77 igb2:192.168.2.2:53793 -> 192.168.2.253:1812 +0.043 User-Name = "johnsXR" NAS-IP-Address = 192.168.2.2 Service-Type = Framed-User Framed-MTU = 1400Here is my phone coming in from trying to talk one of my AP on 192.168.2.2, do you have a firewall rule setup to allow your AP ips to talk to freerad on port 1812?
radsniff would not have anything to do with your setup of freerad, but if stuff is trying to auth to you. You would need to have firewall rules to allow that traffic - sorry if I left that off, but pretty basic that if you have a service listening on 1812, that stuff is going to talk to - your firewall rules would have to allow that.
As to setting up authentication server in pfsense - why would that have anything to do with freerad authing users for other devices.. No you don't need to setup anything there.
Ok. And yes, of course I understand I need a firewall rule,
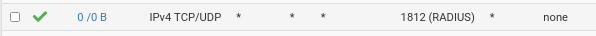
This should be permissive enough... I bet it's just a tiny thingy somewhere... I have to go over everything again...
-
@furom that rule that it has never been used, see the 0/0 do you have some other rule blocking? Maybe in floating or above that?
For unifi to send traffic, you would have to have set up unifi to send to pfsense IP, and then a client would have to try and auth that unifi would talk to your freerad with..
Here I went to my controller and ran a stupid radtest test that I knew would fail - but you can see that radsniff saw the traffic
user@NewUC:~$ radtest test test 192.168.2.253:1812 10 testing123 Sent Access-Request Id 198 from 0.0.0.0:58755 to 192.168.2.253:1812 length 74 User-Name = "test" User-Password = "test" NAS-IP-Address = 127.0.1.1 NAS-Port = 10 Message-Authenticator = 0x00 Cleartext-Password = "test"radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 gif0 tailscale0 igb1 ovpns1 igb2 ovpns2 igb3 ovpnc3 igb4 igb2.4 igb5 igb2.6 lo0 pflog0) 2023-05-19 08:32:13.321600 (1) Access-Request Id 198 igb2:192.168.2.12:58755 -> 192.168.2.253:1812 +0.000 User-Name = "test" User-Password = "test" NAS-IP-Address = 127.0.1.1 NAS-Port = 10 Message-Authenticator = 0xbe0acd5dac7523393e41075bc4372ef1 Authenticator-Field = 0x02eb80a64c53946dfb0a3b65be7baac0 2023-05-19 08:32:18.324176 (1) ** rtx ** Access-Request Id 198 igb2:192.168.2.12:58755 -> 192.168.2.253:1812 +5.002 User-Name = "test" User-Password = "test" NAS-IP-Address = 127.0.1.1 NAS-Port = 10 Message-Authenticator = 0xbe0acd5dac7523393e41075bc4372ef1 Authenticator-Field = 0x02eb80a64c53946dfb0a3b65be7baac0Here this should give you how to test that freerad is running, etc..
edit: you know freerad doesn't even need to be running to test that traffic is actually getting to pfsense with radsniff
Here I turned off freerad on pfsense.
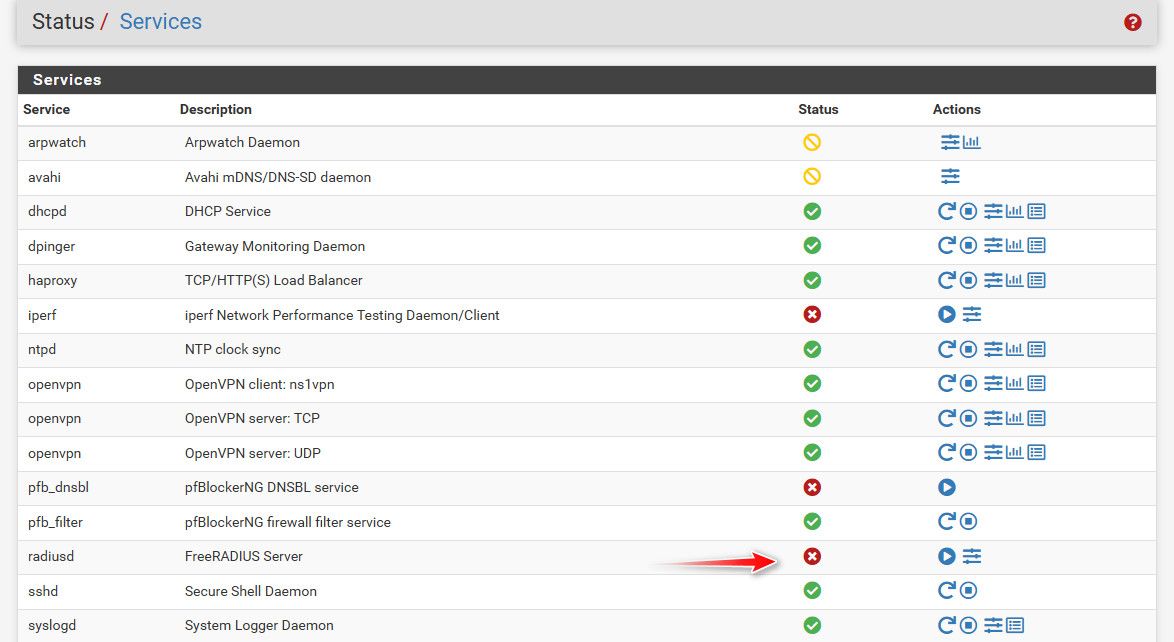
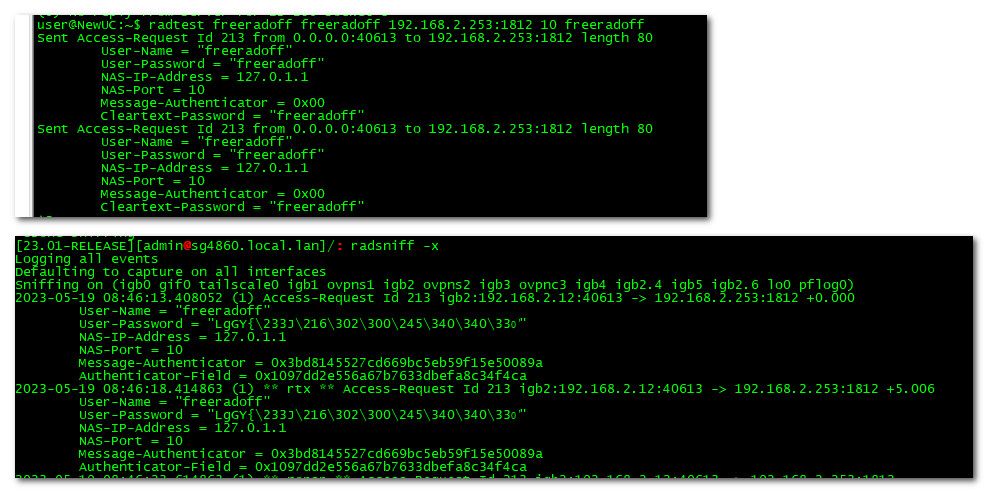
if you are not seeing radius traffic with radsniff then your not allowing it via firewall, or nothing is sending anything, or they are sending it to wrong IP or port..
-
@johnpoz I am about to test my wifi without radius just to see that it actually works... :/ Then add radius.
In floating I have this
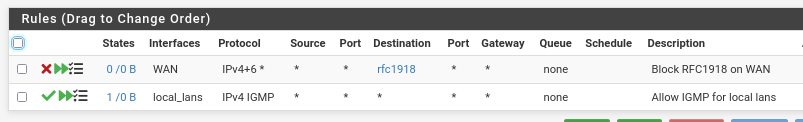
which as I understand shouldn't impact this...But the most basic still must be to get this diagnostic auth to pass, right? If that checks, all the rest will fall into place...
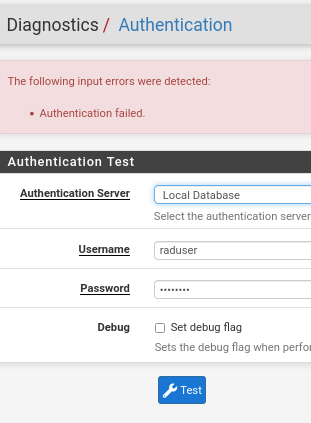
-
@furom said in freeRadius / Unifi AP / EAP-TTLS ?:
diagnostic auth to pass
Again - who cares... I would actually validate that traffic hits pfsense via radsniff.. if your network connectivity is not there then doesn't matter if users could auth or not via whatever method.. because it would never work..
Do a simple radtest and radsniff test like I did - does radsniff see the traffic - if not not then no matter what you setup or don't setup on pfsense for authing methods its never going to work.
-
Why do you have raduser in local db? you understand the users in freerad don't have to match up to local users.
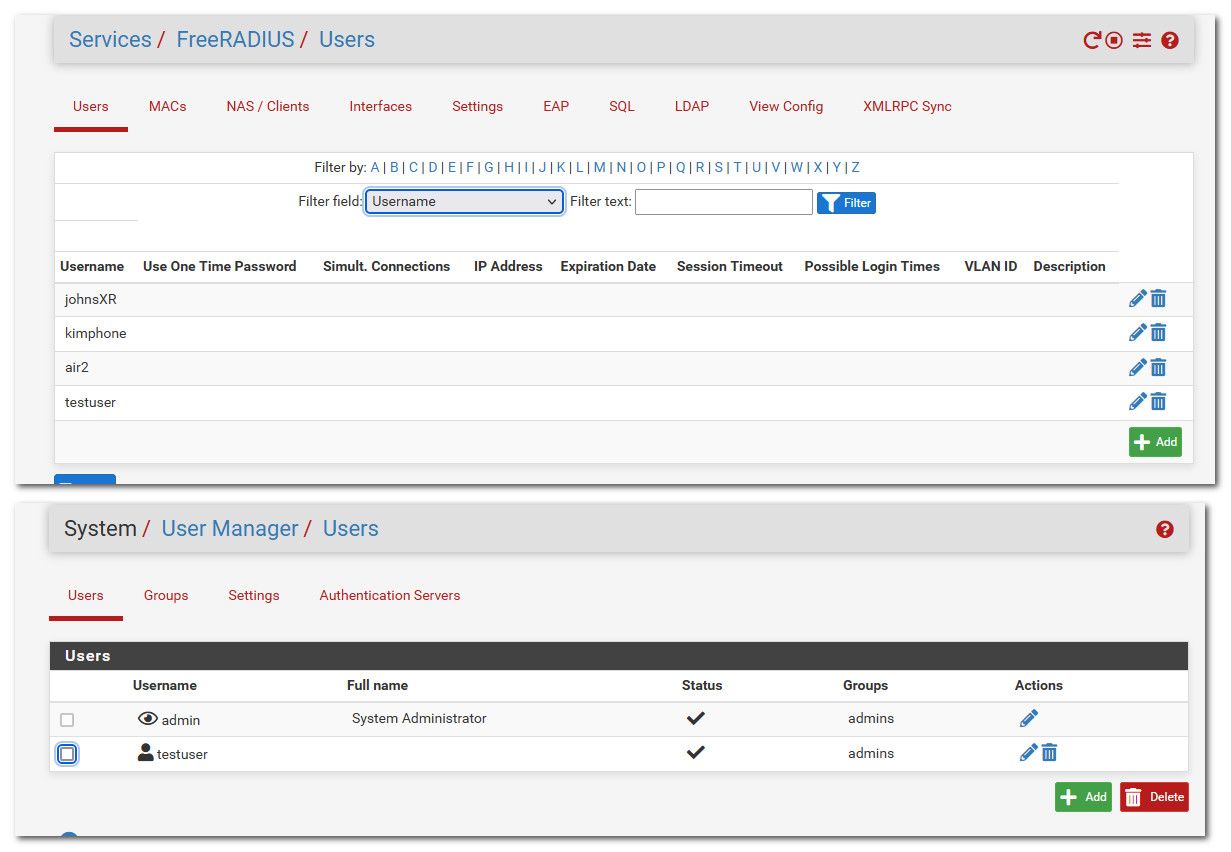
Notice the johnsXR I am authing with my phone isn't in my pfsense users, only that testuser account matches up - and I don't even recall why I had created that.. Going to delete it now ;)
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
Why do you have raduser in local db? you understand the users in freerad don't have to match up to local users.
Hrm... No, I actually didn't. That is why I was nagging about diag/auth. Now I understand why you didn't care about that then.
But on the positive side, I got a reaction from radserver when trying auth from the tablet. I now need to copy over the cert and retry :) -
@furom guess its time I update all my stuff as well - create like certname that matches my iphone13.. And get my wifes new phone and new ipad - and my cheap android tablet all using eap-tls.
-
@johnpoz Got stuck on some extraction password for the p12 cert, but found an old post from you (2017) where you said to add a password wi openssl, so will try that now...
link textAlso got a firmware update for the well over 10 yr old tablet... I will verify with the vendor before applying that at least... Seems more than unlikely they should update so many years after eol... lol
-
@furom ok... I created a new CA for my freerad server cert.. So using new ECDSA for both CA and Cert... Created new user cert from for my phone off new CA.. And all connected without any issues.
Since iphone will not install a new profile without a password.. And something to do with iphone and openssl version 3 I think I had to add the -legacy flag in my command to create the .p12 to load on my phone
openssl pkcs12 -legacy -export -certfile NewFreeRad-CA.crt -in JohnsIphone.crt -inkey JohnsIphone.key -out johnsiphone.p12So I download the new CA cert, and my new user cert and key... Joined them up into a p12 with password "test" and imported just fine into my iphone.
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom ok... I created a new CA for my freerad server cert.. So using new ECDSA for both CA and Cert... Created new user cert from for my phone off new CA.. And all connected without any issues.
Since iphone will not install a new profile without a password.. And something to do with iphone and openssl version 3 I think I had to add the -legacy flag in my command to create the .p12 to load on my phone
openssl pkcs12 -legacy -export -certfile NewFreeRad-CA.crt -in JohnsIphone.crt -inkey JohnsIphone.key -out johnsiphone.p12So I download the new CA cert, and my new user cert and key... Joined them up into a p12 with password "test" and imported just fine into my iphone.
Nice, I am about to test, but unfortunately did the RSA, so will redo if working, but at least things are lighting up a bit! Thanks for all your patience!

-
@furom also - keep in mind unlike browsers there isn't any issue with making this stuff good for long time. I set 10 years on my CA and certs ;)
Got my ssid changed to something a bit better than eaptest, and phone connecting to it without any problems. Now just to create certs and my other trusted devices...
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom also - keep in mind unlike browsers there isn't any issue with making this stuff good for long time. I set 10 years on my CA and certs ;)
Got my ssid changed to something a bit better than eaptest, and phone connecting to it without any problems. Now just to create certs and my other trusted devices...
So true. But something very strange just happened... Network just died and my client were offline. Unifi server died too.. So had to restart and got some weird websocket error, then Unifi didn't load, showed 404 for a while, but then came too... :/ Seems to work now, but don't like when it just locks up for no apparent reason...
-
@furom Weird. Shouldn't I get a password prompt too? I installed CA and the tablet cert I made... says password may be wrong so still something funny here... But at least it responds, so there is hope :)
-
@furom said in freeRadius / Unifi AP / EAP-TTLS ?:
Shouldn't I get a password prompt too?
For why? But yeah you can add that if you want.. I think its completely pointless in such an auth setup... Your sending a cert signed by your own CA.. And this cert is only installed on your trusted devices.. Why would you want to have to put in a password as well?
How would anyone get these certs? How would they create their own cert that also matches up with a freerad user you created..
-
@johnpoz said in freeRadius / Unifi AP / EAP-TTLS ?:
@furom said in freeRadius / Unifi AP / EAP-TTLS ?:
Shouldn't I get a password prompt too?
For why? But yeah you can add that if you want.. I think its completely pointless in such an auth setup... Your sending a cert signed by your own CA.. And this cert is only installed on your trusted devices.. Why would you want to have to put in a password as well?
How would anyone get these certs? How would they create their own cert that also matches up with a freerad user you created..
I don't want it surely, but as it says "Password may be incorrect"...? I'm googling this not, or trying... Found out my nice ISP just revoked my old IP and gave me a new one... Strange...
-
@furom where is it saying that - and what are you putting the certs on exactly.. I do have a android tablet, just haven't gotten around to connecting it to this eap-tls network yet..