ldap user manager
-
Is it possible to use LDAP with User manager but not define a username on the firewall first.
For example, anyone in my CN=Admins group would be given admin rights to the firewall?
Would help in scalability as having over 10 firewalls to manage is a task. -
Yes. Only the user group has to exist on the firewall if you want remotely defined users to inherit permissions.
-
@stephenw10 Really? Burying the lead here Stephen :)
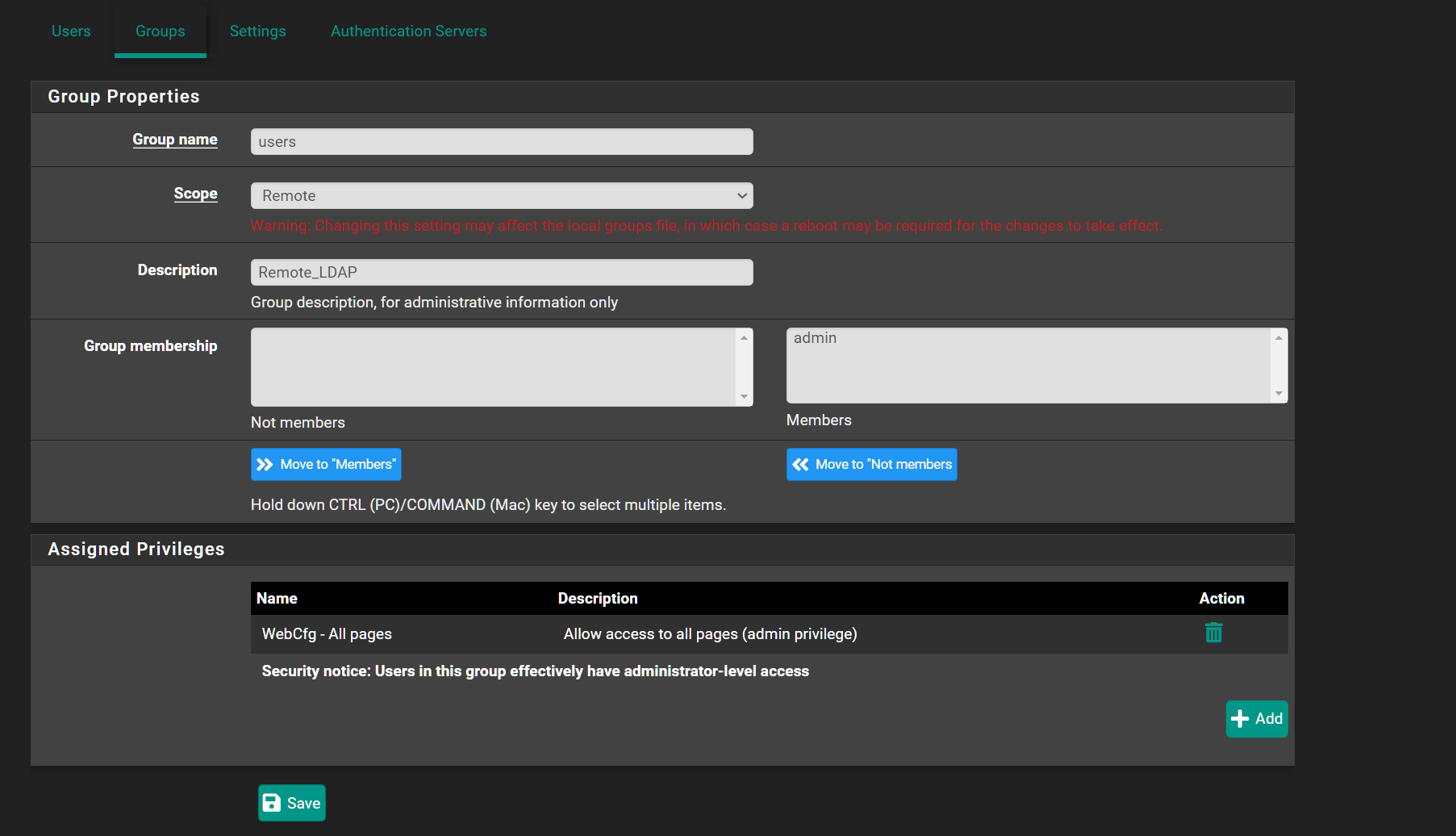
So what do i have to do here?I assume scope is Remote.
Group Name is my ldap DN?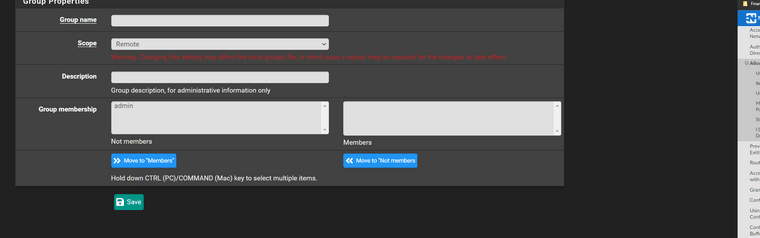
-
It seems to work but i get a page that says no
Message from syslogd@GAFW at May 15 20:43:03 ... php-fpm[85968]: /index.php: Successful login for user 'michael' from: 192.168.50.241 (LDAP/LDAP-SYNOLOGY)
-
@stephenw10 I think i solved it. The ldap group has to be the exact same group created on the firewall.
So i created cn=firewall_admins in ldap.
I created a group on the firewall called firewall_admins and assigned it to be a member of the admins group locally. -
Yes the group name has to match exactly. Nice.

-
@stephenw10 Curious, but could something like this be added to the documentation as a recipe? Using the Netgate youtube official video on LDAP/RADIUS along with the documentation did take me over the finish line.
I noticed that only one LDAP server is able to be used for user manager authentication. My thought process is then to put my LDAP servers behind HA Proxy (tcp mode). What do you think? Pfsense should in theory get the ldap requests, send to the front end and get them delivered to one of my backends.
-
I've seen people use LDAP load balancers but I'm not sure I've seen HAProxy used for that.
-
@stephenw10 Well..it works

I created a VIP on the pfsense.
Created my backend pool
Created my tcp front end.
Created an ACL matching 0.0.0.0/0 and using the default pool for ldapWorks like a charm.
Obviously, for larger implementations, i wouldn't do this but if you are a small to midsize operation with a need for ldap, why not use pfsense with built in proxy to handle it.