No DHCP on pfSense VLAN with Cisco Smart Switch
-
@cannondale never been a gui guy with most switches.. Other than the cheap 40$ vlan ones - so not sure how quirky cisco gui is, these sg300s are the first cisco switches have used a gui with.
I don't recall coming across and weirdness in the sg300 gui, even with previous firmwares - I think there was awhile that one specific feature page wouldn't work with firefox.. But don't recall if that went away with update to firefox, or update to firmware.. This firmware is dated, this switch is nearing eol, and its firmware has not been updated in quite some time. At least your sg250 firmware is recent..
-
@cannondale Can post the full running-config from the switch and the firewall rule(s) on the VLAN10 interface?
-
@marvosa he says he did post the config - but doesn't look full to me at all, maybe he snipped out stuff? Cuz its clearly missing a bunch of info..
Maybe maybe a "sho tech-support" would be good thing to take a look.
As to his rules on his vlan 10 interface, doesn't really matter at this point what those are - if his dhcp is enabled then their would be hidden rules to allow that, and doesn't matter what rules are there when he did his tcpdump -e and didn't see anything with vlan 10 tag.
-
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
he says he did post the config - but doesn't look full to me at all, maybe he snipped out stuff? Cuz its clearly missing a bunch of info..
Yeah, I saw that. Agreed, it's clearly missing tons of info... was hoping to take a peek at the "full" config if possible. As mentioned, if a sh run doesn't get us there (and idk why it wouldn't), try attaching a show tech.
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
As to his rules on his vlan 10 interface, doesn't really matter at this point what those are - if his dhcp is enabled then their would be hidden rules to allow that, and doesn't matter what rules are there when he did his tcpdump -e and didn't see anything with vlan 10 tag.
I don't disagree. I'm more curious than anything... considering on occasion... what's been stated doesn't always match up with what's actually been configured.... so putting eyes on it can be helpful.
TBH, if we're not seeing tagged vlan 10 traffic from the PFsense capture, then nothing's leaving the switch (or the capture was taken on the wrong interface). I'd personally do a write erase and re-configure the switch from the CLI. However, still curious to see the full config and the firewall rules regardless ;)
-
@marvosa said in No DHCP on pfSense VLAN with Cisco Smart Switch:
write erase and re-configure the switch from the CLI.
It sure couldn't hurt - its not like he has anything fancy already on there - looks like everything is just vlan 1.. So not like he would have to take down his whole network while he redoes some crazy config.
-
marvosa, thanks for chiming in. I copied the previously posted from a backup made in the GUI Administration | File Management | File Operations. If there is another way to produce a more complete file, let me know.
VLAN10 firewall rule below:
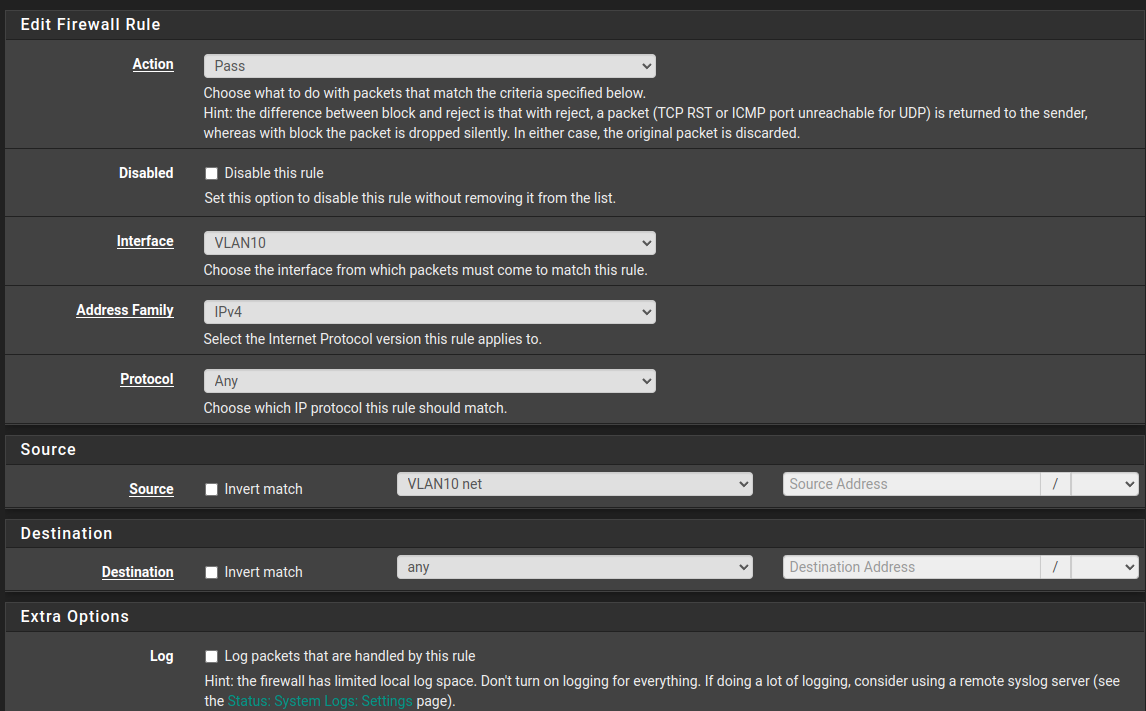
-
@cannondale said in No DHCP on pfSense VLAN with Cisco Smart Switch:
produce a more complete file, let me know.
a show run should give you the whole config..
Or a show tech-support would spit out everything..
So it doesn't page on you, not sure if works on sg250, but works on my sg300 I do a
term datadump
This prevents long outputs from stopping and have to hit key to see more, etc.
-
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
a show run should give you the whole config.
Output from show run:
Roth-SG250-50P-1#show run config-file-header Roth-SG250-50P-1 v2.5.9.16 / RCBS3.1_930_871_108 CLI v1.0 file SSD indicator encrypted @ ssd-control-start ssd config ssd file passphrase control unrestricted no ssd file integrity control ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0 ! ! unit-type-control-start unit-type unit 1 network gi uplink none unit-type-control-end ! vlan database vlan 10,20 exit voice vlan state auto-triggered voice vlan oui-table add 0001e3 Siemens_AG_phone________ voice vlan oui-table add 00036b Cisco_phone_____________ voice vlan oui-table add 00096e Avaya___________________ voice vlan oui-table add 000fe2 H3C_Aolynk______________ voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone voice vlan oui-table add 00d01e Pingtel_phone___________ voice vlan oui-table add 00e075 Polycom/Veritel_phone___ voice vlan oui-table add 00e0bb 3Com_phone______________ no boot host auto-config no boot host auto-update no bonjour enable bonjour interface range vlan 1 hostname Roth-SG250-50P-1 line telnet exec-timeout 30 exit username jer password encrypted $86$5/Jf/f1pY8/95XGv$kPRdzeRMBXmEdsjyTZ1l4+OqCg9fuZ7uKSe5I7LV9IbcgUpUgGQXoGLMEO1AZF52onsZ3HTShH3OYBSXslXbVA== privilege 15 username jer2 password encrypted $86$Jd6VBm9YYE9hsEqS$Wr7/T+o2oqDACWSHr0SNJrmwXG2QQ3MS+4EG1j6BknUM6Z8LMYb1/kokfIc3KefDaW5JkhtnW3+gJTnr3sbDJA== privilege 15 username cisco password encrypted $86$/AkLn2WkB5AHHhIy$e/TgE126IBbIHLLsdMMw6ozjTovM1bR132PxH3lGmJeltzZ4U3ug9F3ZaUl+BclKIcE60h2j7Sn6o7RYksS53g== ip ssh server ip http timeout-policy 0 clock timezone J -4 clock dhcp timezone ip telnet server ! interface vlan 10 name "VL10" no snmp trap link-status ! interface vlan 20 name "VL20" no snmp trap link-status ! interface GigabitEthernet1 switchport mode trunk switchport trunk allowed vlan 1,10,20 ! interface GigabitEthernet22 switchport access vlan 20 ! interface GigabitEthernet24 switchport access vlan 10 ! exit Roth-SG250-50P-1# -
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
Or a show tech-support would spit out everything.
show tech-support output attached as file.
-
@cannondale ok this would explain why not working..
Port : gi22 Port Mode: Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 1 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 20 VL20 Untagged SPort : gi24 Port Mode: Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 1 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 10 VL10 Untagged SNotice the
Ingress UnTagged VLAN ( NATIVE ): 1This is the PVID.. So your untagged traffic coming into the switch from your device would be on vlan 1, so no it would never go out port 1 tagged for the vlan 10 or 20 on these ports.
And your ports would be egress untagged on 10 and 20 of these ports.. But the answer from pfsense on its lan for dhcp would would be on vlan 1...
You should of been seeing the dhcp from these devices - just on the wrong dhcp server.
Port : gi1 Port Mode: Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 1 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 1 1 Untagged V 10 VL10 Tagged S 20 VL20 Tagged Sedit: notice one of my ports that I have a device on vlan 6, which is one that is tagged to pfsense, see the native vlan or pvid for that port is set to 6
sg300-28#show interfaces switchport gi18 Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN Port : gi18 Port Mode: Access Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 6 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 6 W_Guest Untagged SAlso curious why all your ports mode is just blank
Port Mode:
It should be showing trunk or access.. see mine above for gi18, and then on the one that goes to my pfsense
sg300-28#show interfaces switchport gi5 Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN Port : gi5 Port Mode: Trunk Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 2 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 2 Wlan Untagged S 4 W_PSK Tagged S 6 W_Guest Tagged SSo your port 1 looks ok, other then the missing port mode that is odd. But your ports 22 and 24 should have the native vlan (pvid) set to vlan 10 and 20 etc..
-
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
Notice the
Ingress UnTagged VLAN ( NATIVE ): 1
This is the PVIDI do not see where PVID is exposed in the GUI for Access Mode on the membership screen in order to modify.
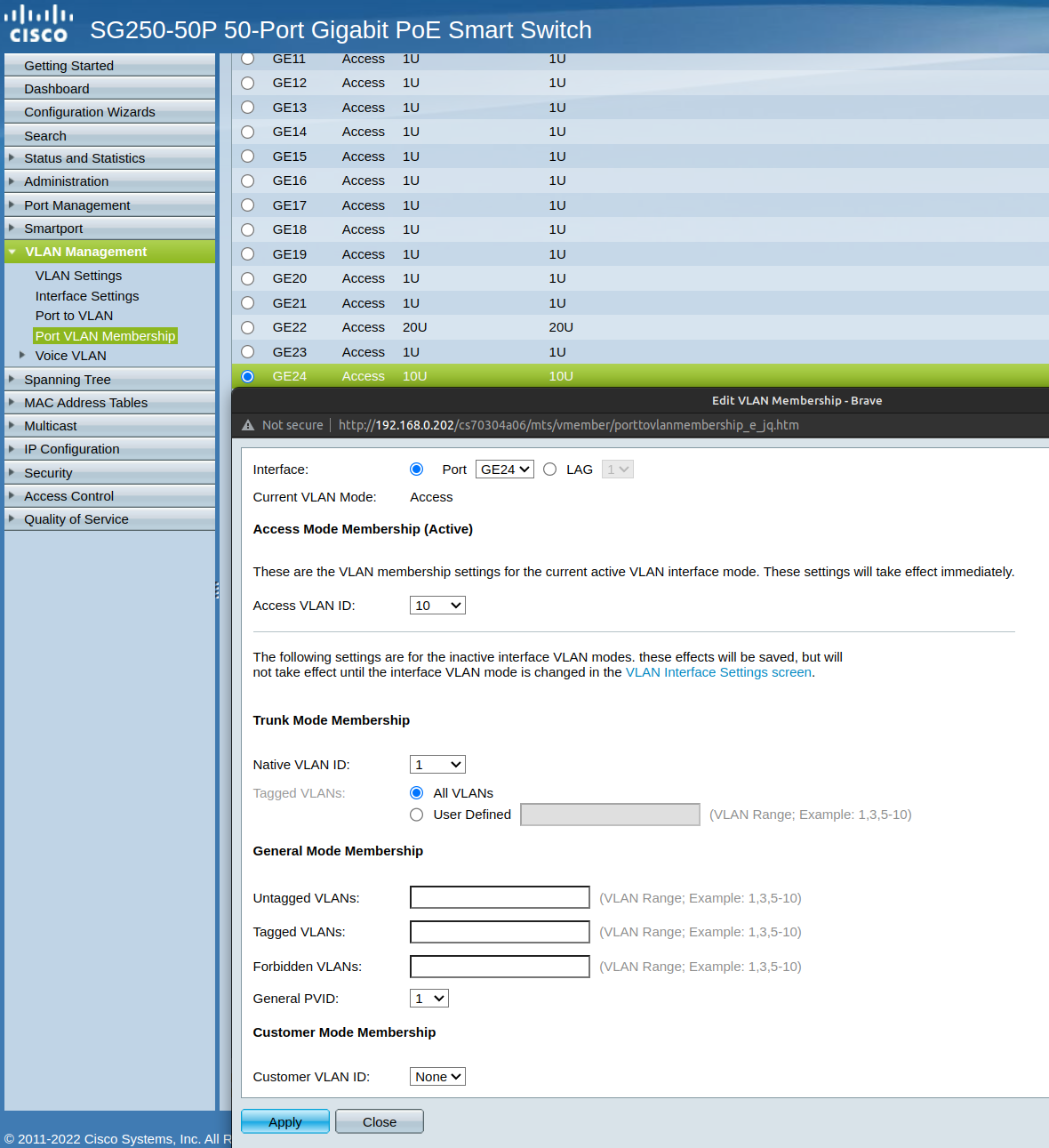
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
Also curious why all your ports mode is just blank
As marvosa previously mentions, it may be a Cisco firmware thing. The GUI shows "Access" for all ports except port 1, which is "Trunk".
Can the PVID be changed in the CLI?
-
@cannondale said in No DHCP on pfSense VLAN with Cisco Smart Switch:
Can the PVID be changed in the CLI?
I don't think so not for a access port.. On my sg300 if I change the access port vlan it auto changes the pvid..
example here is port 28
sg300-28#sho interfaces switchport gi28 Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN Port : gi28 Port Mode: Access Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 10 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 10 disabled Untagged SIf I then put in say vlan 6.. via the with the little arrows to remove it from 10 and add 6 while picking untagged..
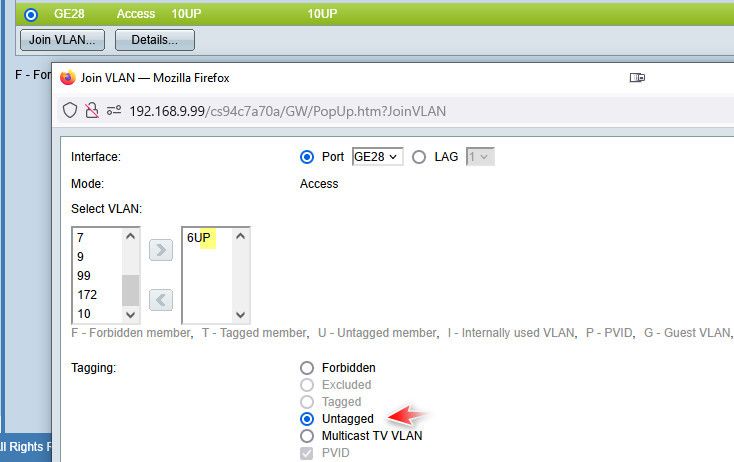
sg300-28#sho interfaces switchport gi28 Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN Port : gi28 Port Mode: Access Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 6 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 6 W_Guest Untagged SYou could try putting it in vlan 10 or 20 from the cli and see if that works..
example - here is me moving it back to 10
sg300-28#sho interfaces switchport gi28 Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN Port : gi28 Port Mode: Access Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 6 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 6 W_Guest Untagged S Forbidden VLANS: Vlan Name ---- -------------------------------- Classification rules: sg300-28#conf t sg300-28(config)#int gi28 sg300-28(config-if)#switchport access vlan 10 sg300-28(config-if)#exit sg300-28(config)#exit sg300-28#sho interfaces switchport gi28 Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN Port : gi28 Port Mode: Access Gvrp Status: disabled Ingress Filtering: true Acceptable Frame Type: admitAll Ingress UnTagged VLAN ( NATIVE ): 10 Port is member in: Vlan Name Egress rule Added by ---- -------------------------------- ----------- ---------------- 10 disabled Untagged S Forbidden VLANS: Vlan Name ---- -------------------------------- Classification rules: sg300-28#I don't really like that your gui doesn't show mode, nor the P that it has in its legends that should mark what the pvid is, etc. Maybe you want to roll back in the firmware.. Maybe there is something wrong with this firmware.. But it for sure is not going to work if untagged traffic coming from your device is going on to vlan 1 vs 10..
maybe you could just put 22 or 24 into trunk mode or general mode.. And be able to set the pvid, and just set vlan 10 or 20 to be untagged..
You might want to ask on the cisco forums.. I doubt you have support from cisco ;)
-
johnpoz, this is the output of sho interfaces switchport gi24 (VLAN10 port):
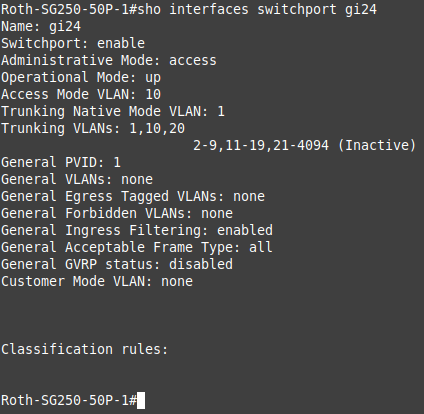
You are the expert here but it doesn't seem reasonable to not expose the PVID in the GUI for Access Mode ports if it is required for VLAN configuration.
-
@cannondale it doesn't need to be expose really since access port can only ever be in 1 vlan, and the pvid should be switched to the vlan you put the access port in.
But seems yours is not doing that..
Try toggle the vlan via cli and see if it switches the native (pvid) if it doesn't then its borked for sure. Not just gui, and I would try rolling back to previous firmware.
A work around would be to put it in general mode where the pvid should be able to be changed.. or set to trunk with just using untagged for egress of vlan and native you can set..
Mine exposes in that it shows what the pvid is in the gui..
-
I would say that those differences what the switches are showing are caused by the different way that the firmwares show stuff.
My CBS250 switch shows config more or less the same way as Cannondale's and my network is working fine VLANs and all.Also these so called business/small business switches don't have the full IOS and different generations seem to behave differently from each other...
-
Thanks for all your help johnpoz! You get the gold star for hanging in there on this issue!
I think I'll try to roll back the firmware as a first step.
When I acquired the switch, it had fw v2.4.0.94, which I upgrade to the latest (v2.5.9.16).
It's possible that it was not upgraded for a reason! -
@mvikman said in No DHCP on pfSense VLAN with Cisco Smart Switch:
business switches don't have the full IOS
Very true - but its close enough that if you are cisco guy in the enterprise, its damn close ;)
The basics all pretty much the same.. When I first got mine I didn't even use the gui, but figured what the hell lt has it - lets give it a look see.
I do recall having impossible time trying to get the gui to load a ssl for https, had to do that from the cli.
-
@cannondale said in No DHCP on pfSense VLAN with Cisco Smart Switch:
I think I'll try to roll back the firmware as a first step.
Did you try just changing the vlan from the cli, maybe its just a bug in the gui, and if you change the vlan at the client it correctly sets the pvid.
Also prob look in the cisco forums - I will do a quick little gui now that we know its not changing the native vlan for access ports.
-
interface GigabitEthernet1 switchport mode trunk switchport trunk allowed vlan 1,10,20I'd remove vlan 1 from the allowed line on your trunk (Gi1).
Too many odd things that aren't adding up. Rolling back the firmware may work, but if it doesn't, I'd still recommend rebuilding the config from scratch from the cli. You'll likely save yourself countless hours of more troubleshooting.
-
Thanks for the suggestions guys! You both have given me some additional options to try.