pfsense Snort is blocking traffic to/from google server. Best way to avoid this event (false positive)?
-
Dear Users,
I just noticed that pfSense Snort is blocking an IP address belonging to Google servers pool.
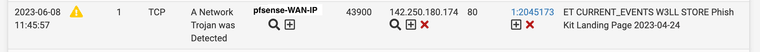
When this event happens, LAN clients are not able to use Google drive and other Google services.
As you can see from the picture above, the outbound traffic from pfsense WAN IP to google is blocked.
Could you please help me to understand the best way to fix it?Moreover, I think that the same problem can occurs contacting the other IP addresses belonging to the same pool.
(I can add the google server IP to the whitelist, but I think that I should add every google server as well...and I don't know how to do it .... and if it is safe...)Many thanks in advance for your help.
Mauro -
If it were me, I would temporarily disable that rule. I suspect the rule creator will make an edit in the near future to address the false positive.
Another method is to use the Suppress List option. You can suppress by a single IP or by a netblock. If you know the Google netblock you want to protect, then you can create a custom Suppress List entry. Scroll all the way to the bottom of this page and read about alert (event) suppression: https://www.snort.org/faq/readme-thresholding.
Here is an example of suppressing alerts for a given CIDR block:
#Suppress this event to this CIDR block suppress gen_id 1, sig_id 2045173, track by_dst, ip 10.1.1.0/24However, I suspect you will have problems finding all of the required netblocks. It would be easier in my opinion to simply disable that rule for now.
-
@bmeeks many thanks for your kind reply. sorry for my late answer.
