ntopng showing over 50 ghost WAN networks, and i can see random computers not belonging to me
-
@ekkzorzizten said in ntopng showing over 50 ghost WAN networks, and i can see random computers not belonging to me:
Destination was always 224.0.0.251:5353.
This is a multicast address.. So anything on the same L2 would see this traffic. May an isp run multiple networks over the same L2..
While they prob shouldn't do that.. if you see the traffic then yeah ntop prob going to report it and not really know what to do until you tell it.
Here for example - 1000 arp packets in just like 10 seconds. Without showing too much of my IP, mine starts with 209, you can see 2 completely no way part of my subnet there
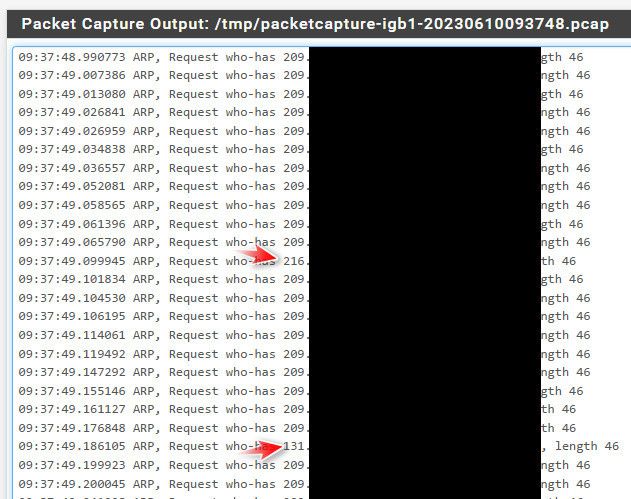
Many of those others are not actually in my /20 my IP sits in..
-
@johnpoz Okey, so its working as intended then? I never thought my or anyone elses traffic could be seen by others on the same L2, that there would be some kind of port isolation and that one could only talk to the gateway, if not explicitly told to visit the neighbours website or alike.
Can they see my hosts if they would run ntopng? If so, how can i deny/reject that? And how can i get rid of all that nonsense in my firewall log, create a reject on WAN for all 224.0.0.251:5353? Is there any documentation on how to setup ntopng to not give false alerts? I read a referenced post (https://www.ntop.org/ntopng/detecting-hidden-hosts-and-networks-on-your-shared-lan/) but did not get any smarter.
Thanks for replying to my incoherent, panicing mumble!
/Erik
-
@ekkzorzizten said in ntopng showing over 50 ghost WAN networks, and i can see random computers not belonging to me:
It began with alot of strange entries in the firewall, showing random WAN IP addresses blocked by default deny rule IPv4 (1000000103) to destination 224.0.0.251:5353.
Source interface was WAN, but not my WAN IP. Destination was always 224.0.0.251:5353.It looks like some upstream DNS server...
-
@ekkzorzizten said in ntopng showing over 50 ghost WAN networks, and i can see random computers not belonging to me:
anyone elses traffic could be seen by others on the same L2
Why would you think that, this isn't unicast traffic it it multicast - so yeah every device on the same L2 would see that. So unless they have like private vlans setup to isolate client from client - that is how broadcast and multicast works..
So for sure you would see stuff like arp - I have never seen any mdns - that would seem like some idiot has their device directly plugged into the isp network vs being behind a nat router..
Why would you have ntop listening on your wan side interface in the first place?
-
I haven't done this for years, but I used to run Wireshark on my WAN connection and see lots of stuff for other customerers. Don't forget, the Internet is a shared service, so don't be surprised if you see stuff from/for your neighbours.
-
@JKnott said in ntopng showing over 50 ghost WAN networks, and i can see random computers not belonging to me:
stuff from/for your neighbours.
They sure should not be seeing any unicast traffic, but sure anything that is broadcast/multicast in nature - prob going to see this... And sure there will be lots of just plain noise sent to your IP from the internet.
Again why would you run ntop on your wan interface - makes zero sense to run it on that interface in the first place.. Unless you want to see all the noise and have ntop try and make sense of it?
-
I just did a Packet Capture for a couple of minutes. Here's just a bit, showing both IPv4 & IPv6 traffic.
16:03:27.321883 ARP, Request who-has 99.246.152.60 tell 99.246.152.1, length 46
16:03:27.322870 ARP, Request who-has 99.246.133.92 tell 99.246.132.1, length 46
16:03:27.327898 ARP, Request who-has 99.246.136.92 tell 99.246.136.1, length 46
16:03:27.334256 IP6 2001:558:fd00:30::25c.10068 > 2607:fea8:4c82:5900:cd36:782c:bc02:8e9a.56290: tcp 31
16:03:27.334444 IP6 2607:fea8:4c82:5900:cd36:782c:bc02:8e9a.56290 > 2001:558:fd00:30::25c.10068: tcp 0
16:03:27.350917 ARP, Request who-has 38.80.105.170 tell 38.80.105.161, length 46
16:03:27.351195 ARP, Request who-has 99.246.221.74 tell 99.246.220.1, length 46
16:03:27.351852 ARP, Request who-has 99.246.219.228 tell 99.246.218.1, length 46
16:03:27.355123 IP6 2001:558:fd00:30::25c.10068 > 2607:fea8:4c82:5900:cd36:782c:bc02:8e9a.34646: tcp 31
16:03:27.355282 IP6 2607:fea8:4c82:5900:cd36:782c:bc02:8e9a.34646 > 2001:558:fd00:30::25c.10068: tcp 0
16:03:27.357632 ARP, Request who-has 99.246.151.20 tell 99.246.150.1, length 46 -
@JKnott and clearly that 99.246 and that 38.80 are for sure not the same L3 network.. That that IPv6 looks like unicast either from you or too your address, and your answering..
-
My ISP has multiple subnets on the cable. That may be due to having Internet, TV, phone and security systems all on the same cable. Of course, some of my traffic may be in there too, as I have pfSense on there. Regardless, my point is it's a shared system.
-
@JKnott which is exactly what I was saying as well ;)
The correct fix for the OP problem is not to be running ntop on his wan - have no idea why anyone would want to do such a thing, it makes no sense to do that..