FTP server behind firewall: additional public IP on WAN interface + NAT or existing public IP on WAN + NAT ?
-
Dear Users,
it is the first time I need to create an FTP server behind my pfSense instance and some doubts come up.
In your opinion, should I use the existing public IP defined on the WAN interface starting presenting the FTP service to internet using NAT or it is not a good practice?
I read that you can add an additional public IP to the existing WAN interface and present the FTP service to internet using NAT.Please, note that we don't want to implement the FTP service in the DMZ (since it doesn't exists yet, at least in this first phase).
Could you please give me some feedback/suggestion about this use-case?
Many thanks in advance,
Mauro -
@mauro-tridici You'd be better using sftp as it only uses port 22, pfB_SSH_PERMIT_v4 & pfB_SSH_PERMIT_v6 contain country codes to restrict access any further and h_ipv4_sftp is the non NAT address of the server.
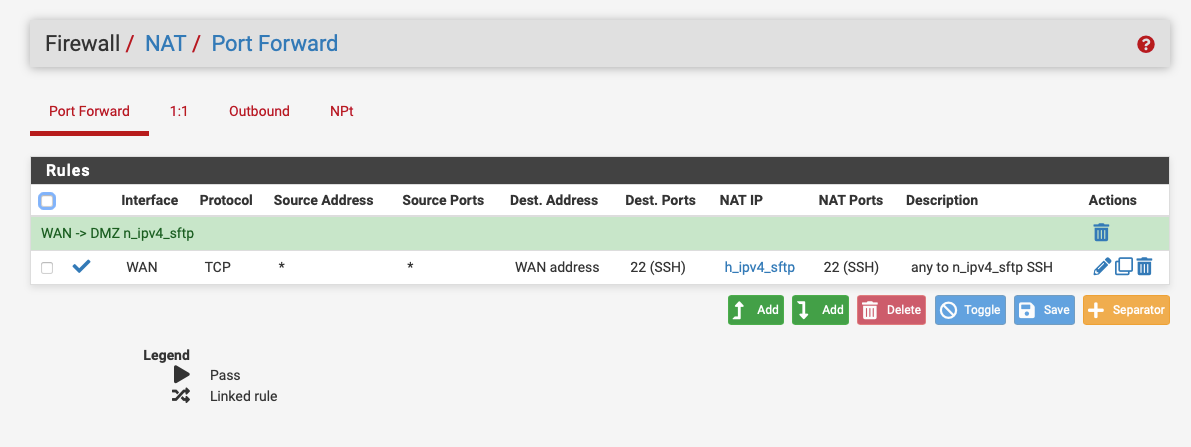
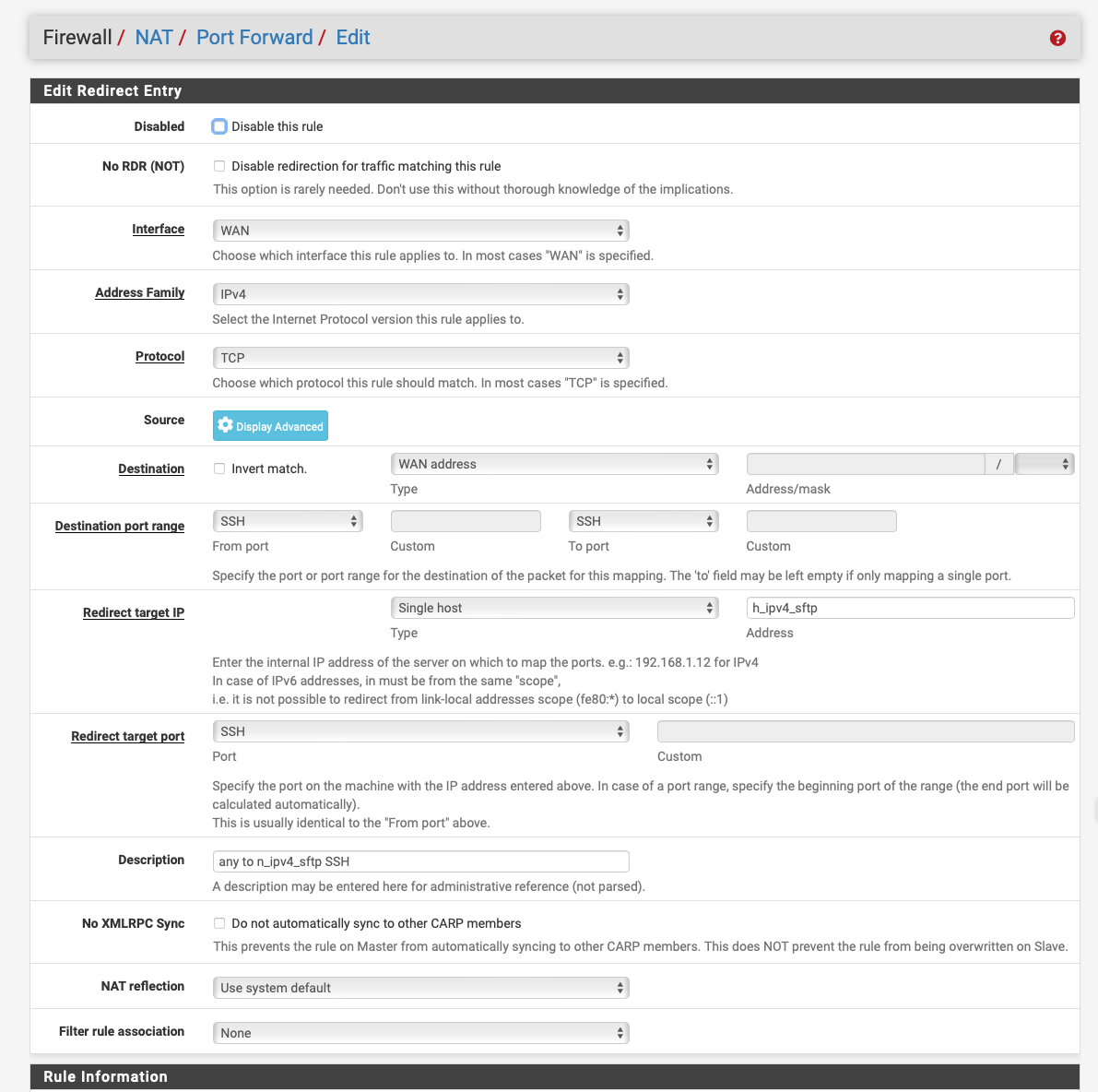
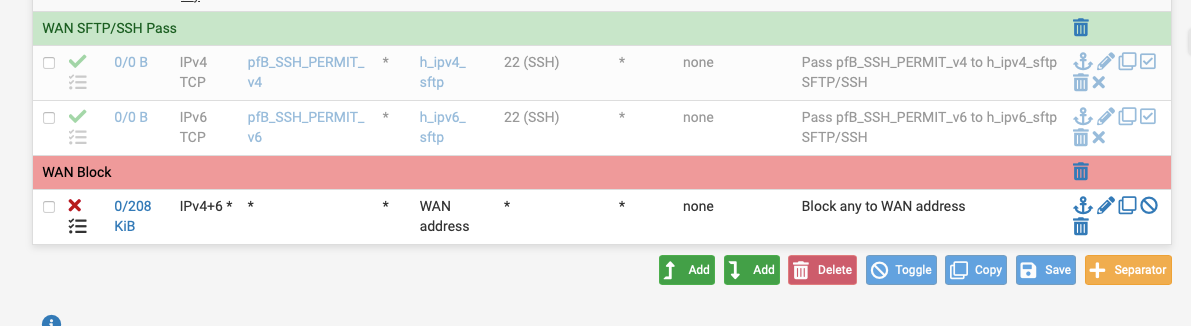
You can also block brute force attacks if the sftp server is running FreeBSD:-
https://www.cyberciti.biz/faq/freebsd-openbsd-pf-stop-ftp-bruteforce-attacks/
-
@NogBadTheBad many thanks for your reply.
I really appreciated your suggestions.Anyway, my question was related to the following choice:
- use the existing public IP assigned to the WAN interface or assign an additional public IP to the WAN interface and use it for the port forward?
Sorry if I didn't explain my needs clearly.
Thanks,
Mauro -
@mauro-tridici what does it matter? Not sure why it would make any difference.. Are these IPs going to be on the same connection, if they were different connections then it might be worth putting traffic A on connection A and traffic B on B for spreading load across your connections.
But if on the same connection - what IP is used doesn't really matter, other than your state tables.. If you have so many sessions going to or from IP A, then using another IP for other traffic would give you more states to work with.. But this would really only matter if you were running into an issue with state exhaustion, or this new traffic might cause you issues with states..
I would agree with sftp vs ftp as well - ftp should of died off 10 some years ago.. That it is still used blows my mind..
-
@johnpoz Stupidly when my connection changed to ADSL I didn't take up my ISP offer for free extra public IP addresses, wish I'd have done it now

-
@NogBadTheBad said in FTP server behind firewall: additional public IP on WAN interface + NAT or existing public IP on WAN + NAT ?:
free extra public IP addresses
If your isp is going to give you more IPs - then yeah for sure would take them, even if you currently have no use for them ;) Having more than 1 public IP can make it easier to run the same service you want going to different devices. www.domainx.tld goes to IPA and sent to 192.168.1.100.
www.domainy.tld goes to IPB, and gets sent to 192.168.1.101 for example..
This removes the need of having to use say a reverse proxy to accomplish that, or using different port, etc.
But unless the OP is wanting to do something like that for multiple FTP servers, what public IP is used wouldn't really matter unless could be used for different connection and load distribution of traffic, or problem with state utilization.
-
Yup, it really makes no difference what public IP you use here. I would probably use a different one if you have unused IPs though.
But be aware of the issues running FTP behind NAT. You will need to be sure the server is configured correctly for it.
https://docs.netgate.com/pfsense/en/latest/recipes/ftp-without-proxy.html
Steve
-
@stephenw10 thank you for your reply and for the link you provided.
Thank you to all of you, guys, for sharing with me your experience.
Mauro