pfblocker IP list bypass
-
@michmoor said in pfblocker IP list bypass:
My expectation is that I see it in the Floating Rules list. If i create a custom IPv4 list do i have to use it as an Alias?
I've not actually tried that so don't know the answer. If you create your own rules using aliases you can order them as needed and create a rule above it to bypass the blocks, and not try to have pfB generate that allow rule. It's at least, one way to do it.
-
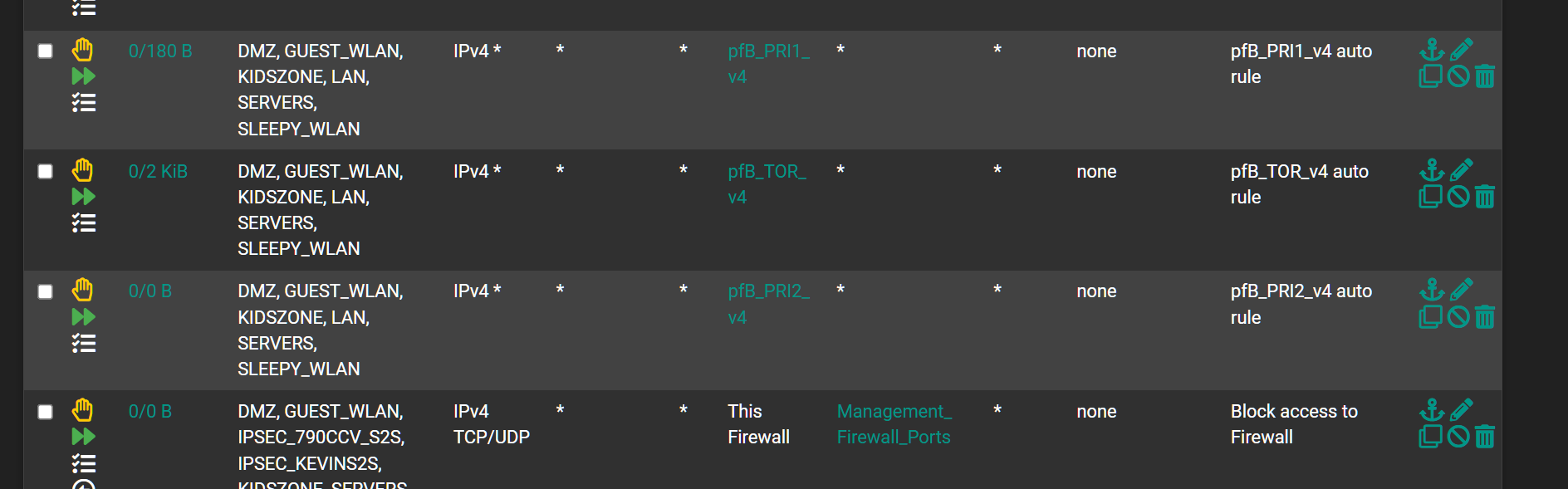
I assume you do see rules for the other 4 lists?
-
@stephenw10 Yep. Those are there. Screen Cap of that.
This is starting to look like a bug. The custom group just isnt being processed.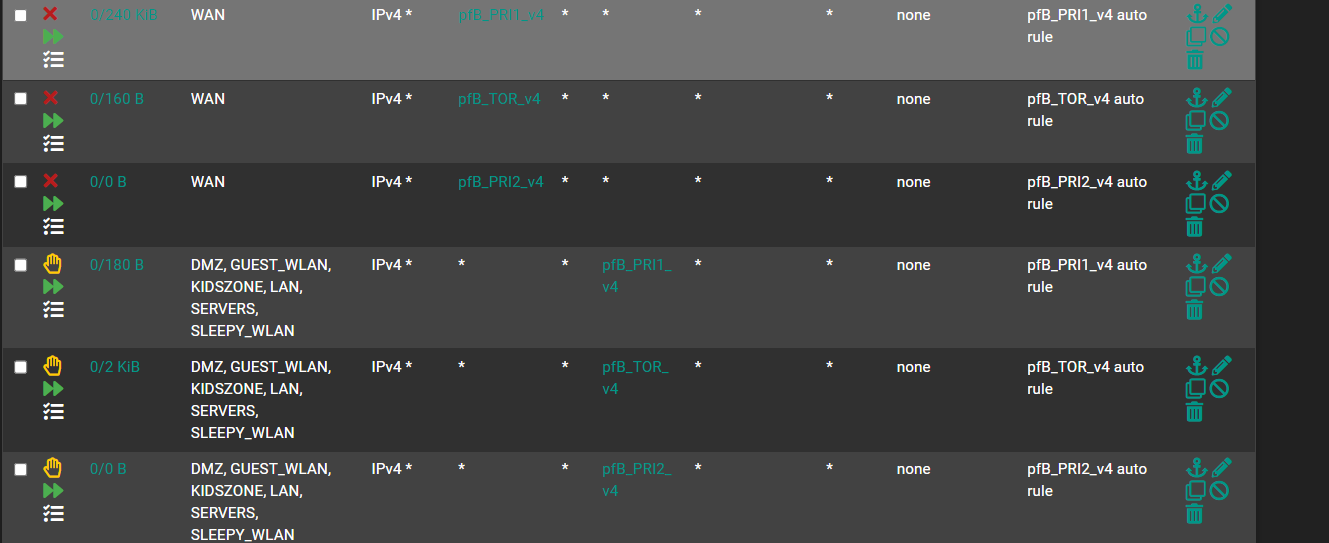
Logs
===[ DNSBL Process ]================================================ Loading DNSBL Statistics... completed Loading DNSBL SafeSearch... disabled Loading DNSBL Whitelist... completed [ MPatrol ] exists. [ 06/15/23 17:23:25 ] [ PhishingArmy ] exists. [ OISD ] exists. [ URLhaus_Mal ] exists. [ CoinBlocker_All ] exists. [ Abuse_ThreatFox ] exists. [ 06/15/23 17:23:26 ] [ CustomBlockList_custom ] exists. ===[ GeoIP Process ]============================================ [ pfB_NAmerica_v4 ] exists. [ 06/15/23 17:23:28 ] ===[ IPv4 Process ]================================================= [ Abuse_Feodo_C2_Agr_v4 ] exists. [ Abuse_SSLBL_Agr_v4 ] exists. [ CINS_army_v4 ] exists. [ ET_Block_v4 ] exists. [ ET_Comp_v4 ] exists. [ ISC_Block_v4 ] exists. [ Spamhaus_Drop_v4 ] exists. [ Spamhaus_eDrop_v4 ] exists. [ Talos_BL_v4 ] exists. [ BDS_TOR_v4 ] exists. [ DMe_TOR_All_v4 ] exists. [ ET_TOR_All_v4 ] exists. [ PROJECT_TOR_EN_v4 ] exists. [ Alienvault_v4 ] exists. [ AS714_v4 ] exists. [ AS15169_v4 ] exists. ===[ Aliastables / Rules ]========================================== No changes to Firewall rules, skipping Filter Reload No Changes to Aliases, Skipping pfctl Update ===[ Kill States ]================================================== No matching states found ====================================================================== UPDATE PROCESS ENDED [ 06/15/23 17:23:30 ] -
As a workaround for now I created a a floating rule and set it to the top. Then changed the rules processing order in pfblocker.
Maybe its the better way to do it but the pfblockerNG is my preferred way of handling it but IPv4 custom rules set up like this doesnt work.Can anyone reproduce this on their end?
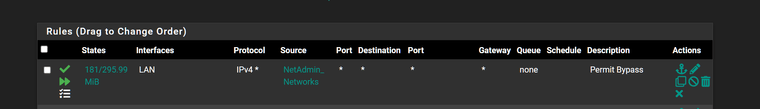
-
If you set it as block in pfBlocker does the rule get created?
I don't see that custom list in the update logs...
-
-
Ok, so it's probably not populating the list. Or it's not enabled or similar.
-
@stephenw10 Yeah for some reason it just doesnt see the custom group. I'll open a redmine
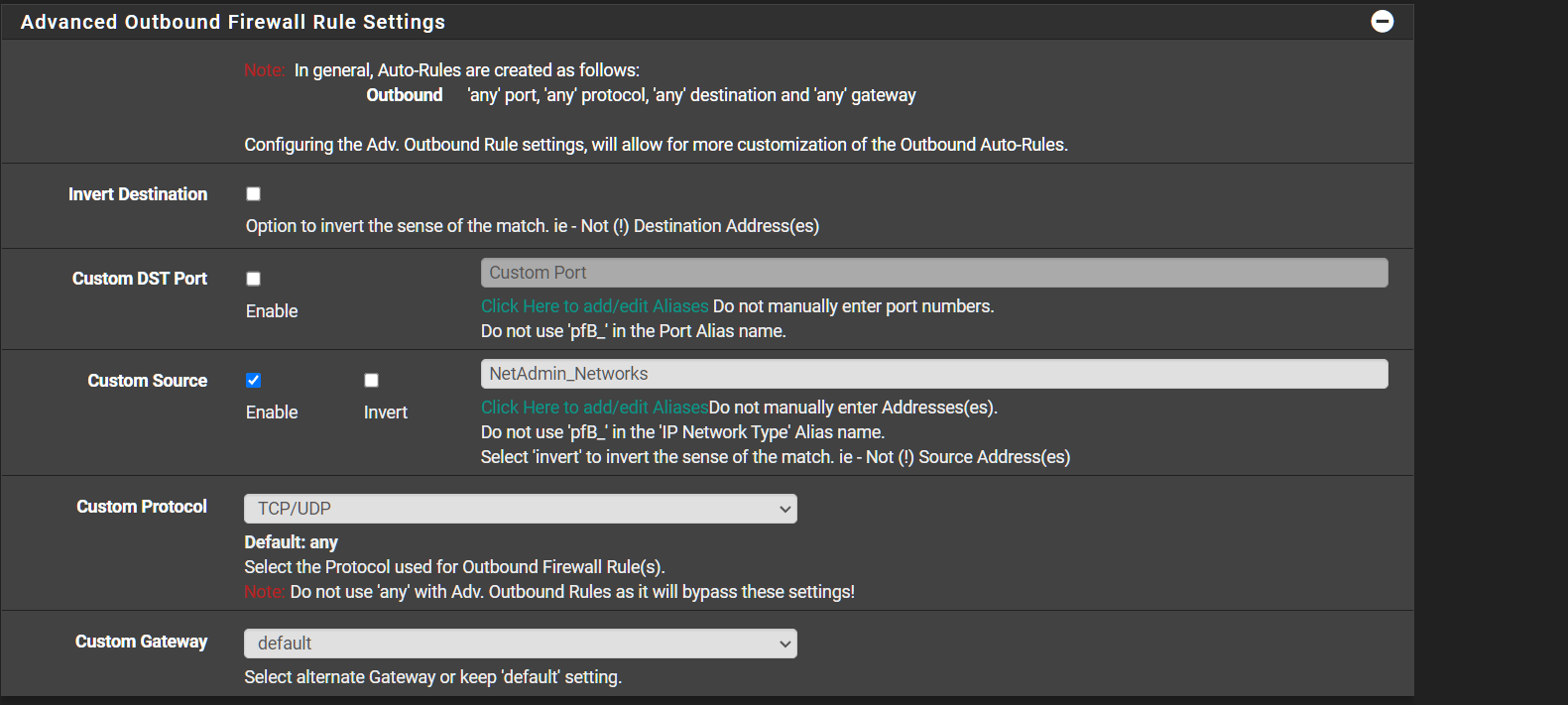
Also i do have an Ports Alias that i use in an Inbound Firewall rule in conjunction wtih GeoIP thats processed without issue.
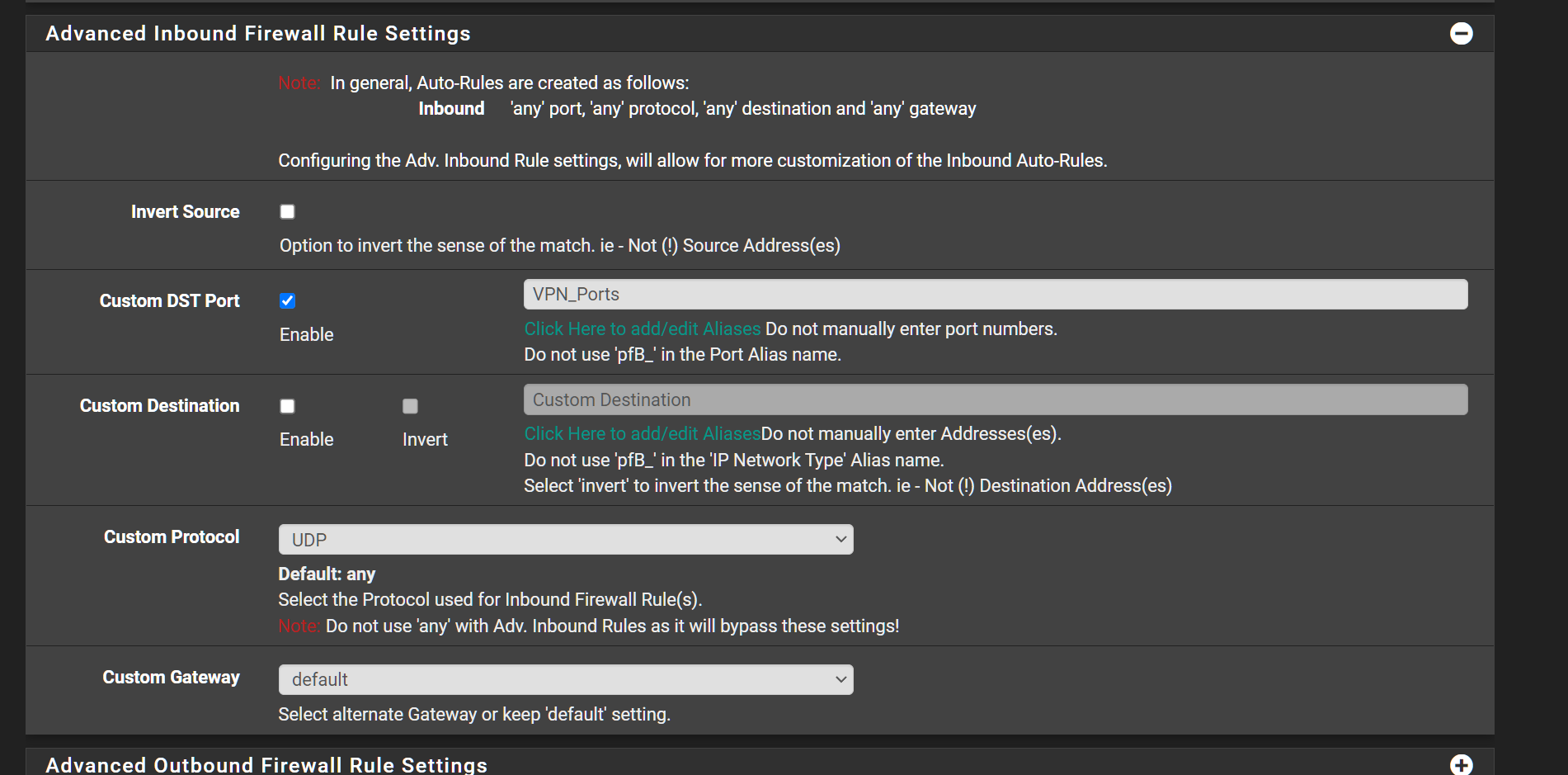
-
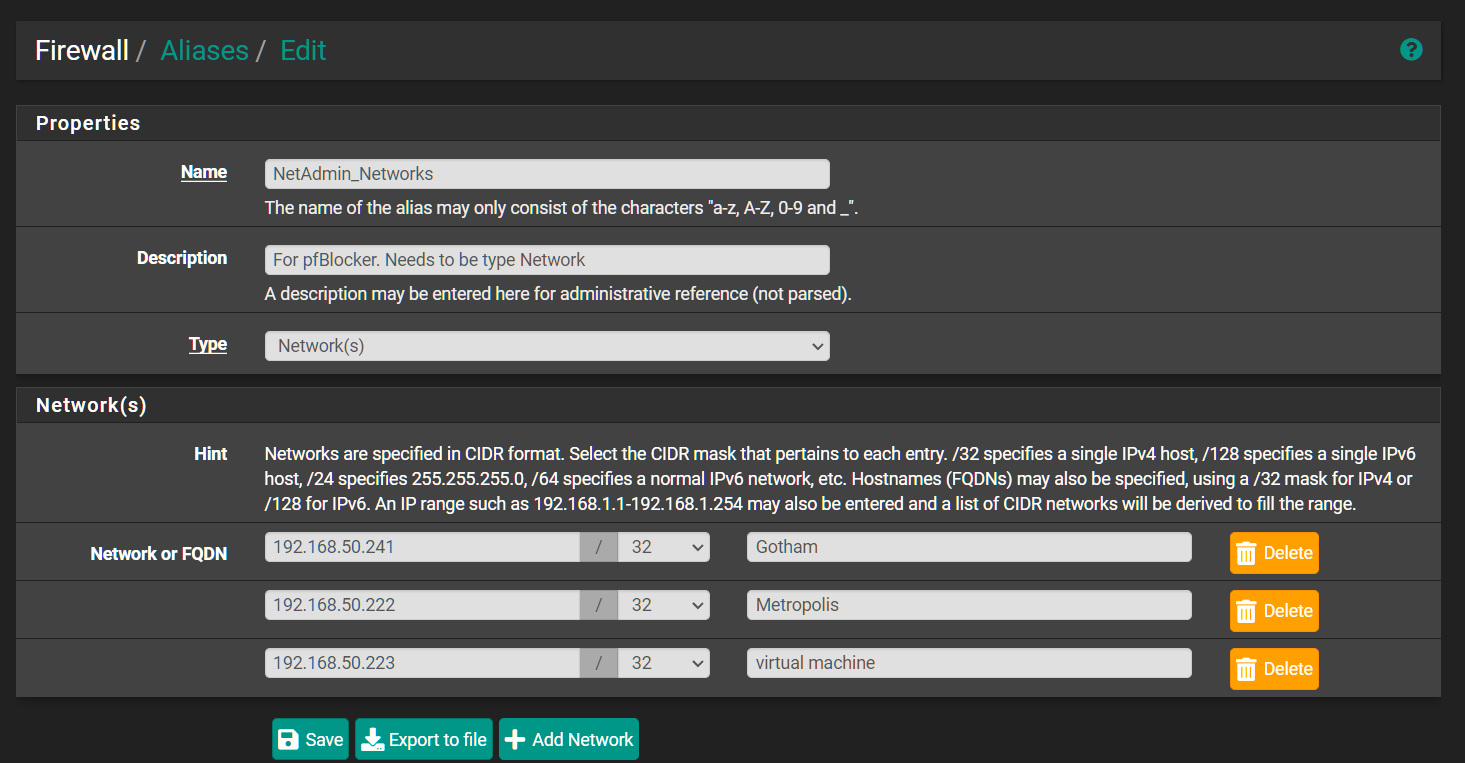
This seems like it might just be the list isn't configured correctly. What is in that list apart from the custom firewall source?
-
Yes, in fact re-reading this it looks like you might have created an empty list and just added the alias the firewall rules section as a source to use?
That won't create any rules since nothing is actually listed.You probably want to add the IPs directly in the 'IPv4 Custom_List' section.
-
This post is deleted! -
@stephenw10 Ok I see what you mean now. My logic was faulty.
But when i add it to the custom IPv4 list those IPs show up as Destinations. I suppose setting it to Alias Native would work but anyway to have the IPs listed in my field set to sourceEDIT: Figured it all out...
Going out for a drink. haha.
@stephenw10 @SteveITS Appreciate yallEDIT2: For future me or anyone else who looks back at this.
- Create the custom group with the IPv4 Custom_List IPs.
- Set to Alias Permit
- Under Floating Rules , create a Pass rule.
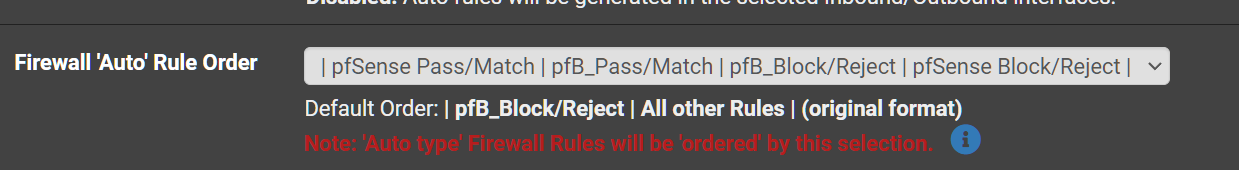
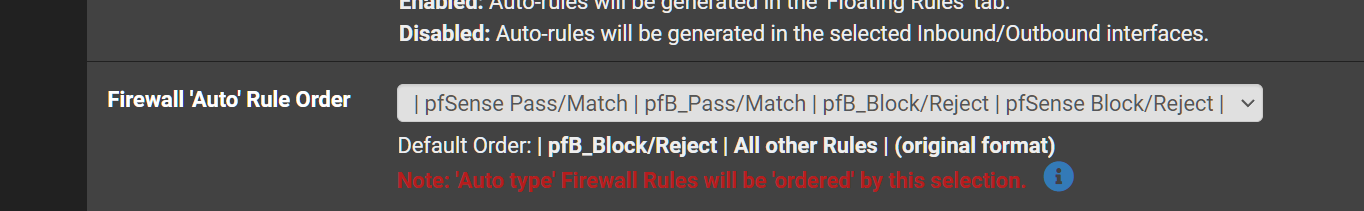
- Set the Firewall Auto Rule Order to pfSense Pass...
- Adjust accordingly.
My rule is at the top exactly where I needed it to be.
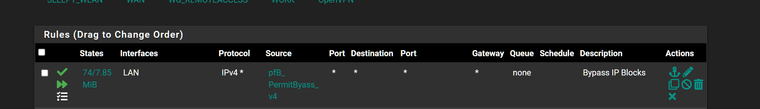
-
Yup, that's probably how you'd have to do it.
My only concern there is that the pfBlocker auto-rules might get moved above that when they are reloaded. You should check that.
-