Prevent hosts from using their own dns
-
Hello to everyone from Greece. I've finished a couple days ago my pf Sense+ project in the Office along side with 4 Cisco 3550 switches. Every floor has its own vlan, everything works fine as accepted.
I have set as dns servers in the general tab those of cloudflare, 1.1.1.3 and 1.0.0.3 to prevent hosts from malware and visiting adult sites. Im not using dns resolver or forwarder.
The ip addresses obtained by the hosts are in dhcp mode.
What i would like to do, is to prevent a user from using its own dns , like 8.8.8.8. I would like to "force" them to use only dns from the general tab that i have set.
Thanks in advance.
-
@drivth well create a simple block rule to block all access to dns udp/tcp 53
Rules are top down, first rule to trigger wins.
So allow to your dns on udp/tcp 53 1.1.1.3 and 1.0.0.3 and then below that block all other access to 53..
Kind of like this - I allow dns to pfsense IP on test..
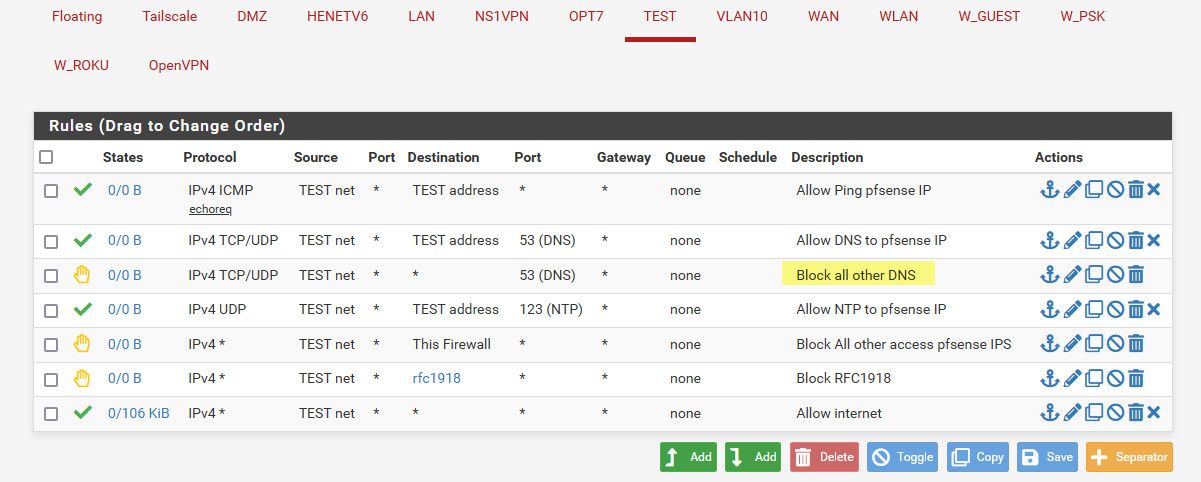
Then right below that I have a rule that blocks any other dns..
Your allow would just include the IPs you want to allow - you can use an alias if you want more than 1 IP, etc.
-
@johnpoz i think i might have tried something similar, ending without access to internet at all when i used static dns 8.8.8.8 of my own in a host.
I have a spare hardware ready with pf Sense+ for emergency, i will try my tests there and get back with the results.
Just to be clear, if i apply those rules, a host with other static dns applied would still have access to the internet or no?
Just trying to prevent some users who think they can bypass pf sense dns settings.
-
@drivth if they don’t have dns how would they have internet? Keep in mind browsers love to do their own dns over 443 hiding in normal ssl traffic so blocking just normal dns over 53 won’t prevent a browser from using dns over https (doh)
-
@johnpoz my thought was that even if a more advanced user decided to put static dns in his computer , such as 8.8.8.8, that maybe there was a way that he could surf the internet with pf sense's dns's 1.1.1.3 and not resolving addresses with the static dns that he might put.
-
@drivth Devices can be set with their own DNS and browsers use DoH.
The "pfsense" document here is very detailed but might be of help in blocking others:
https://github.com/jpgpi250/piholemanualYes you can block from LAN Net to (alias of DNS IPs):53 but you'd have to keep the list up to date, which they do in that github account.
In rare cases some devices are hard coded for DNS, for example the "on demand" software/app in my Dish DVR only uses DoH even though the DVR uses normal DNS.
-
Here is a link to how I did it.
https://forum.netgate.com/topic/156453/pfsense-dns-redirect-to-local-dns-server?_=1663853296484