Manual Outbound NAT in HA deployment with CARP VIP for WAN - best practice advice needed
-
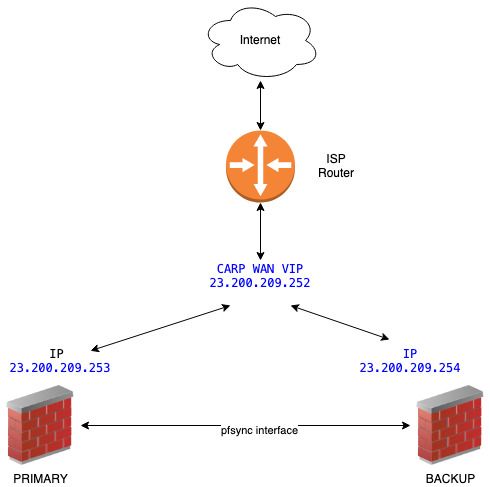
This is the network scheme of my deployment (IP's are fakes)
Based on this "Configure Outbound NAT for CARP" section of pfSense documentation, I have selected "Hybrid Outbound NAT rule generation.
(Automatic Outbound NAT + rules below)" mode on my pfSense, and the system auto-created the rules for me for each and every of its interfaces.
Note: (to be precise, at first I've selected "Manual Outbound NAT rule generation" and pfSense itself auto-created the rules for all of its interfaces. Only recently I've switched from manual mode to hybrid mode)My doubt arises from this warning statement on pfSense documentation, which says:

I'm not sure if the first 4 rules in the manually created NAT are ok or not: reading the before amended warning those 4 rules shouldn't be there, maybe?
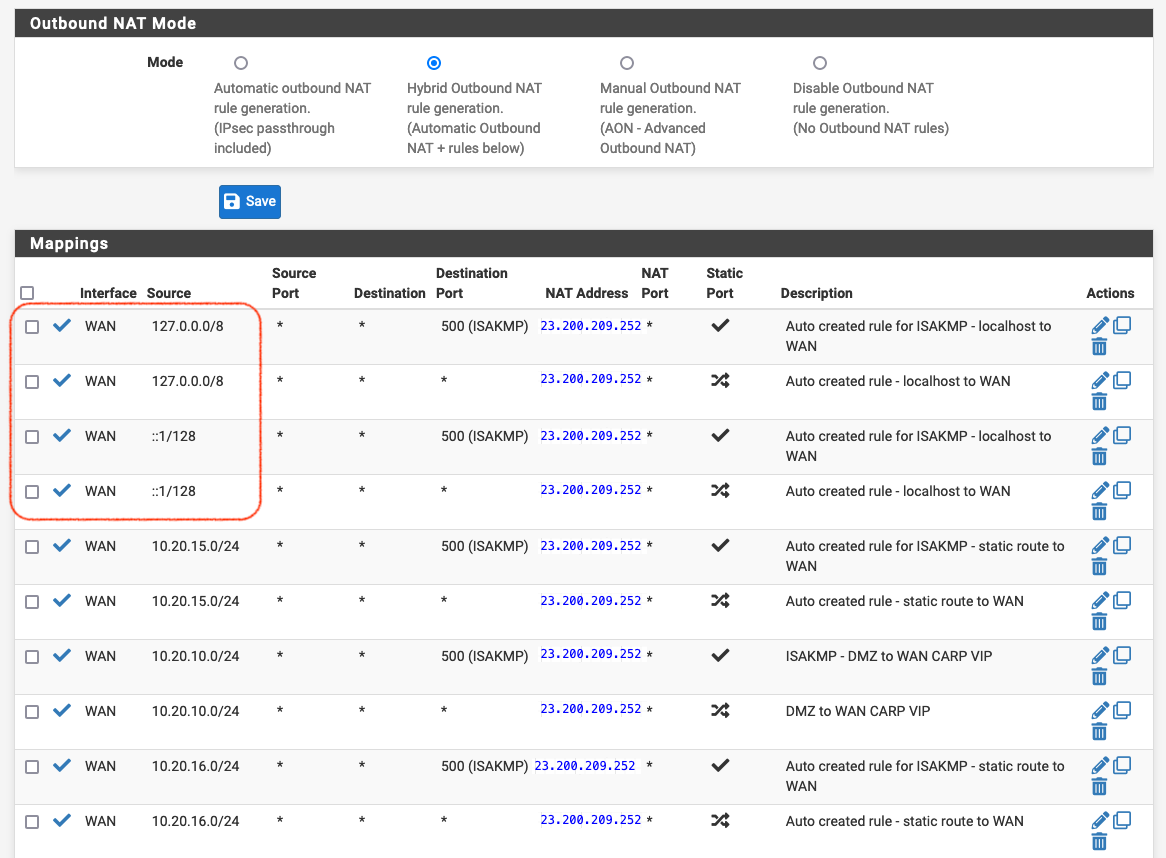
In the Automatic Rule section I have the following:
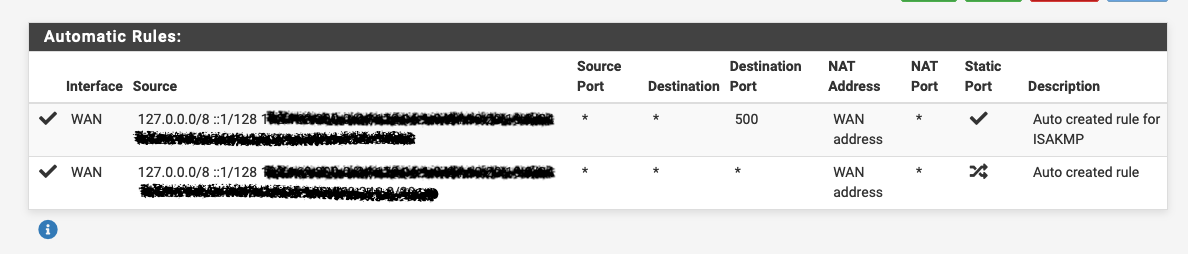
Before removing those first 4 manual NAT rules I'd just like to have an advice from you, also because everything seems to be pretty ok ....I can ping both my pfSense's via their WAN IP's, they can reach Internet for their own services, etc etc.
Thanks a lot
-
@sheprador
Yes, this is exactly what the warning addresses. You shouldn't use the VIP for outbound traffic from pfSense itself. You should use its interface address instead.
This is already done by the automatic generated rules, if it's in hybrid mode. So you can remove the top four manual rules. -
@viragomann Ok, thank you.
Before removing that 4 rules, I'm just wondering 1) why the system seems to be working ok and 2) if this could be used as a way to go when dealing with a single public WAN IP (when maybe you should set the 2 WAN's address-less and setting only the CARP VIP)...I know it's a bit off-topic, but this is the next thing I'll need to deal with very soon.
-
@sheprador
The CARP VIP and any alias hooking on the VIP is occupied by the master. Hence the backup node cannot use the VIP and will not have access to the internet, e.g. to pull updates or DNS resolution.- if this could be used as a way to go when dealing with a single public WAN IP (when maybe you should set the 2 WAN's address-less and setting only the CARP VIP).
If you've read the documentation you might know that it is recommend to have at least 3 available IPs on each interface for running pfSense in HA. But basically you can also use private IPs for the interfaces of both nodes and hook up the single public IP as CARP VIP with the same effect: only the master can use it and has access to the internet.
However, there is a 'dirty' workaround to get internet access also on the backup with some drawbacks. Even discussed recently here, but sadly the TO didn't respond if he succeed with the recommendations.
-
Thanks @viragomann