use port 80 for port-forwarding when using ssl for pfsense interface
-
Big issue here..
I only have one public IP by my internet provider.
I need port 80 for automated ssl using lets encrypt on a service in my lan.
when I create a port-forwarding for port 80 it just doesnt work as pfsense itsel fis listening there.
I changed my pfsense to use port 9443 instead of 443 for https so I0m able to reach my server using the port-forward on port 443 form the internet, but port 80 just doesnt work. -
@uz890ed
Go to System > Advanced > Admin Access and check WebGUI redirect (Disable webConfigurator redirect rule). Save the settings. -
@uz890ed said in use port 80 for port-forwarding when using ssl for pfsense interface:
I need port 80 for automated ssl using lets encrypt on a service in my lan.
Why not just use DNS method to get your acme certs?
You sure your isp is not blocking 80? Go to say can you see me . org, send traffic to port 80 do you see it on your wan via sniff?
example.
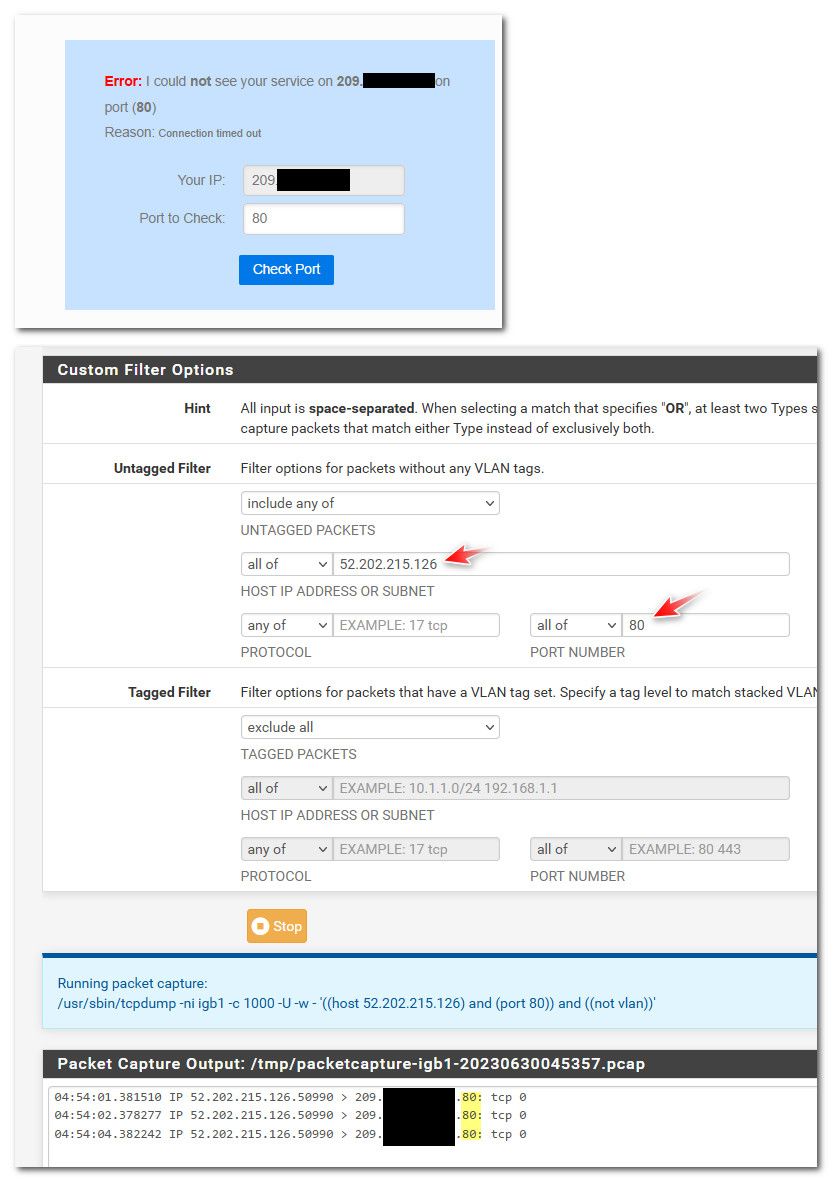
You might not want to filter on the source IP like I did, until your sure you know what IP the traffic will come from - not sure if they use multiple source Ips.. I first did a capture - see noise to 80, and then ran it again to filter on the specific IP..
If your seeing other traffic to 80 at all then you kind of know your isp isn't filtering.
-
@viragomann said in use port 80 for port-forwarding when using ssl for pfsense interface:
@uz890ed
Go to System > Advanced > Admin Access and check WebGUI redirect (Disable webConfigurator redirect rule). Save the settings.I tried -> doesn't work.
-
@johnpoz
Hey there
I just tried thisit tells me Success: I can see your service on mypublicip.. on port (80)
but it doesn't work. -
@uz890ed it sees a service on 80, it could be pfsense. or it could be device(isp) in front of pfsense.
you really need to know that pfsense actually sees the traffic, and sends it where you want it to go.
So you would sniff and validate pfsense actually sees it, and then sniff on the lan side interface your using to port forward the traffic - while you do the same test. You should see the traffic get sent on, or you could look in your state tables and validate the traffic was forwarded.
if you see it sent on correctly - then where its sending it maybe is not doing whatever your want to do with amce.
But again - why not just use the DNS method for your acme certs, no you don't have to worry about port forwarding.
-
@johnpoz the traffic is not blocled by my isp as the pfsense forwards me when connecting via mobile network to it's ssl port which then doesnt load as the ssl port of the pfsense gets blocked as it should
-
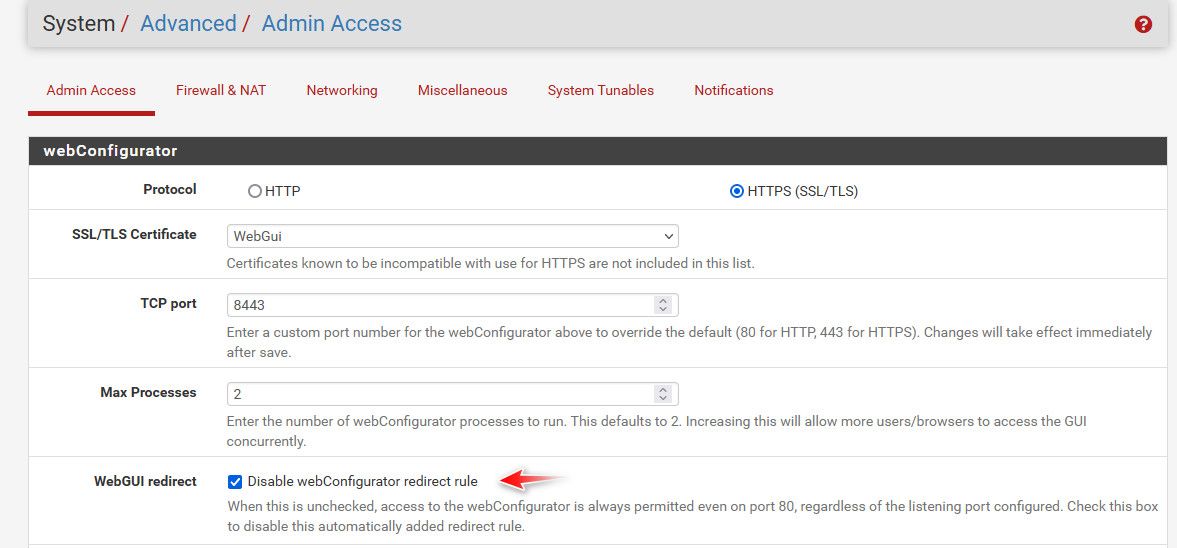
@uz890ed so you disabled the 80 redirect on pfsense?
Validate that pfsense is not listening on 80, simple sockstat
[23.05.1-RELEASE][admin@sg4860.local.lan]/var/unbound: sockstat -l | grep :80 root nginx 90402 9 tcp4 *:80 *:* root nginx 90402 10 tcp6 *:80 *:* root nginx 90166 9 tcp4 *:80 *:* root nginx 90166 10 tcp6 *:80 *:* root nginx 90115 9 tcp4 *:80 *:* root nginx 90115 10 tcp6 *:80 *:* [23.05.1-RELEASE][admin@sg4860.local.lan]/var/unbound:I then turn off the redirection..
[23.05.1-RELEASE][admin@sg4860.local.lan]/var/unbound: sockstat -l | grep :80 [23.05.1-RELEASE][admin@sg4860.local.lan]/var/unbound: