NAT forwarding into WireGuard Interface as LAN Interface
-
@Bob-Dig said in NAT forwarding into WireGuard Interface as LAN Interface:
Please show your Port Forward on your VPS and also the config of your WG Interface for both. Outbound NAT for both should be automatic, nothing else. It is that easy...
Site-A (VPS):
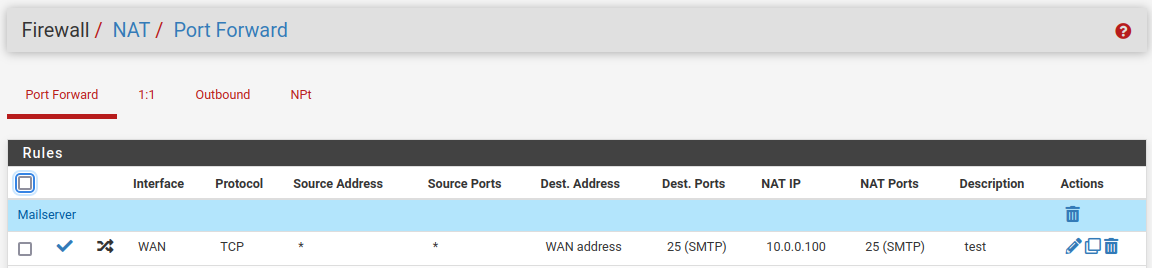
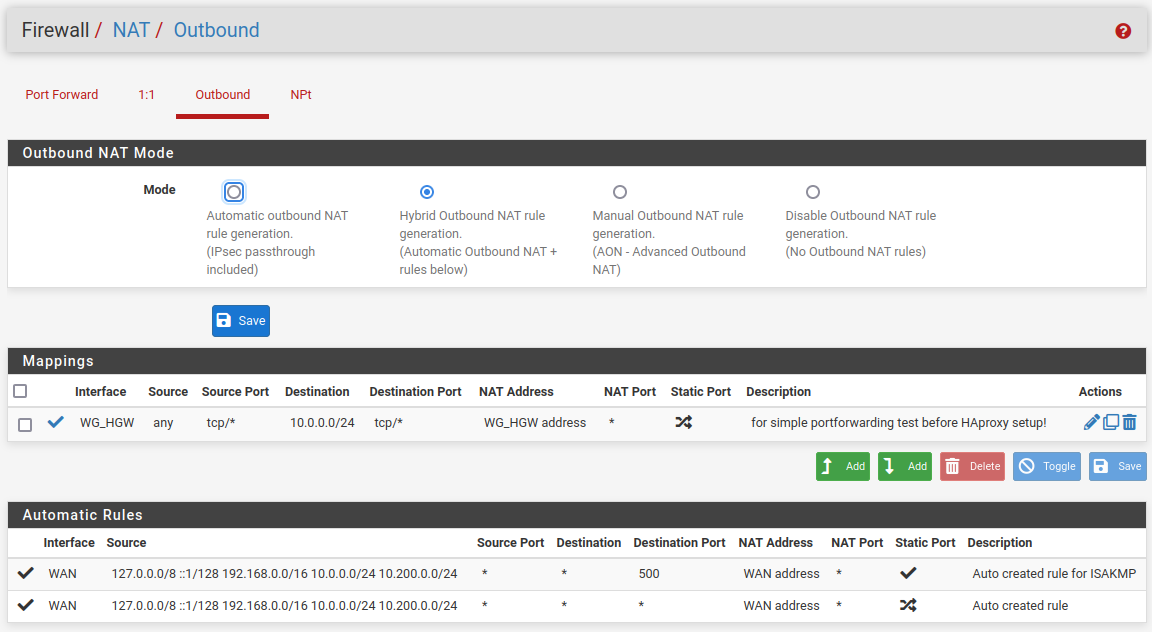

Site-B (home):
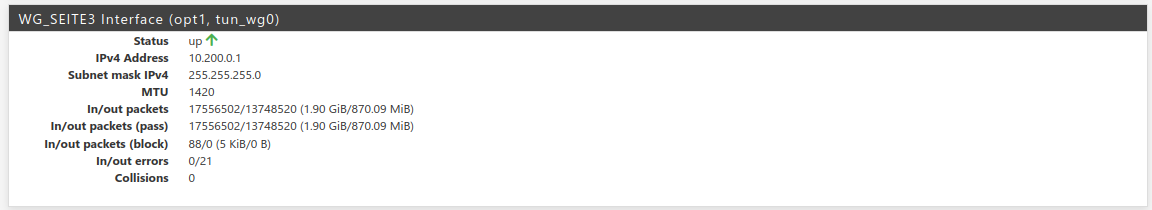
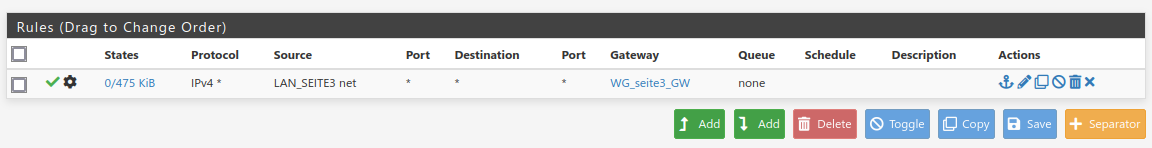
As mentioned, mail server at home - machineMX (at LAN_SEITE3) - is working for in- and outbound mails, but the replaced source ip of incomming mail server connections.
@viragomann said in NAT forwarding into WireGuard Interface as LAN Interface:
If you direct this connection over HAproxy read again, what I wrote above.
Will double check it but to use HAProxy as a reverse proxy for the Postfix SMTP server, you need to enable Postscreen in Postfix. This doesn't worked for me at the first run...
-
@Bronko I meant the complete IP-config from those interfaces, not their status.
Also remove the manual outbound NAT rule and forget haproxy.
And what rule is the last one? For the tunnel use an allow any rule for testing. -
@Bob-Dig said in NAT forwarding into WireGuard Interface as LAN Interface:
I meant the complete IP-config from those interfaces, not their status.
The tunnel is working fine, no problem here... isn't it?
@Bob-Dig said in NAT forwarding into WireGuard Interface as LAN Interface:
Also remove the manual outbound NAT rule and forget haproxy.
Without this rule @viragomann (above) incomming conntections via VPS at Site-A to machineMX at Site-B doesn't work.
@Bob-Dig said in NAT forwarding into WireGuard Interface as LAN Interface:
And what rule is the last one? For the tunnel use an allow any rule for testing.
An allow any rule for wg_tunnel is in place. These last one is policy routing for server net (LAN_SEITE3). Without these the outgoing traffic at server net is routed via default gateway at Site-A.
-
Let's have a picture here, port forwarding, outbound NAT and policy routing via rules from above:
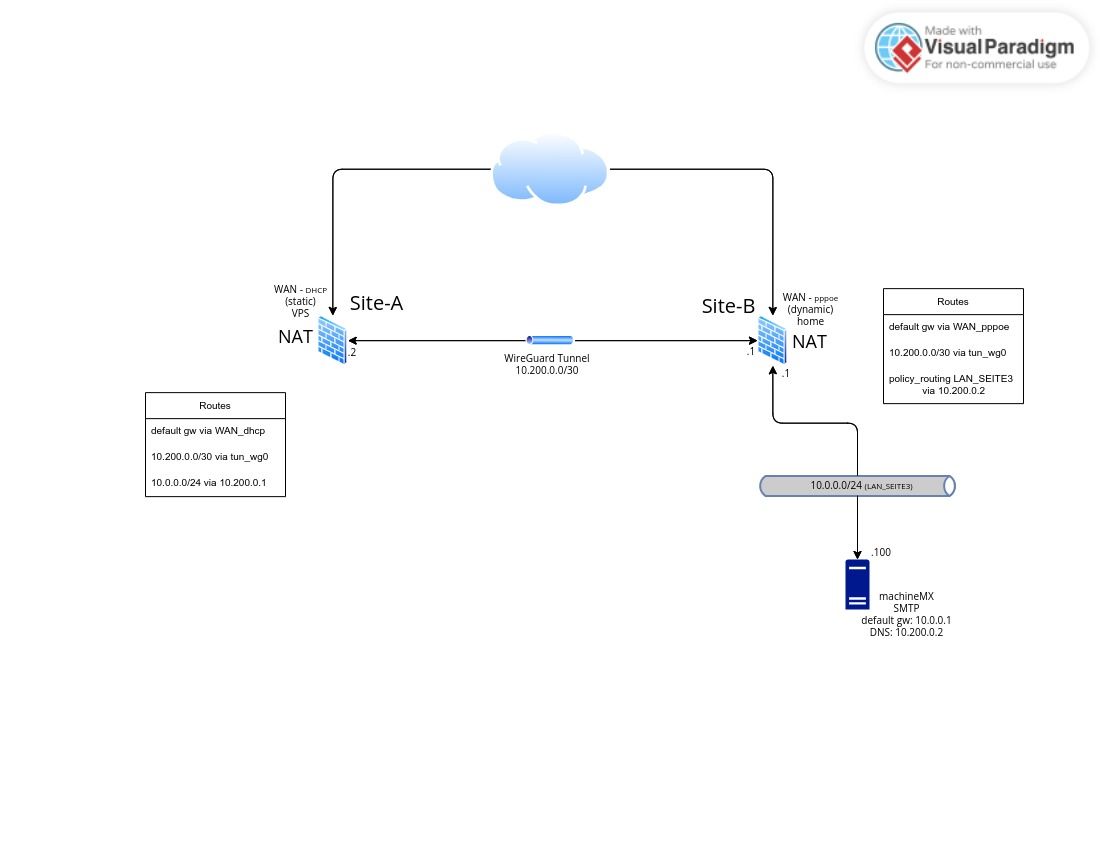
Described above:
Site-A
tun_wg0: 10.200.0.2
netstat -rn Routing tables Internet: Destination Gateway Flags Netif Expire default xxxxxxxxxx UGS vtnet0 10.0.0.0/24 10.200.0.1 UGS tun_wg0 10.200.0.0/24 link#6 U tun_wg0 10.200.0.2 link#3 UHS lo0 xxxxxxxxx/22 link#1 U vtnet0 xxxxxxxxx link#3 UHS lo0 yyyyyyyyyyyyy link#1 UHS vtnet0 yyyyyyyyyyyyy link#1 UHS vtnet0 127.0.0.1 link#3 UH lo0 192.168.0.0/16 10.200.0.1 UGS tun_wg0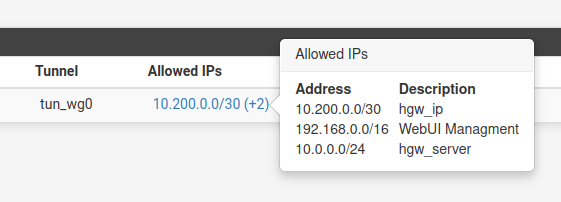
Site-B
tun_wg0: 10.200.0.1
netstat -rn Routing tables Internet: Destination Gateway Flags Netif Expire 0.0.0.0/8 link#12 U re0.8 default xxxxxxxxxxxxx UGS pppoe0 10.0.0.0/24 link#18 U re2.301 10.0.0.1 link#5 UHS lo0 10.0.1.0/24 link#21 U ovpns1 10.0.1.1 link#5 UHS lo0 10.0.2.0/24 link#25 U ovpns2 10.0.2.1 link#5 UHS lo0 10.0.3.0/24 link#22 U ovpns3 10.0.3.1 link#5 UHS lo0 10.0.4.0/24 link#23 U ovpns5 10.0.4.1 link#5 UHS lo0 10.0.5.0/24 link#24 U ovpns6 10.0.5.1 link#5 UHS lo0 10.200.0.0/24 link#8 U tun_wg0 10.200.0.1 link#5 UHS lo0 xxxxxxxxxxxxxx link#19 UH pppoe0 yyyyyyyyyyyyy link#5 UHS lo0 127.0.0.1 link#5 UH lo0 192.168.1.0/24 link#2 U re1 192.168.1.1 link#5 UHS lo0 192.168.2.0/30 link#1 U re0 192.168.2.2 link#5 UHS lo0 192.168.3.0/24 link#17 U re2.106 192.168.3.1 link#5 UHS lo0 192.168.6.0/24 link#20 U bridge0 192.168.6.1 link#5 UHS lo0 192.168.8.0/24 link#10 U re2.201 192.168.8.1 link#5 UHS lo0 192.168.9.0/24 link#16 U re2.105 192.168.9.1 link#5 UHS lo0 192.168.21.0/24 10.0.2.2 UGS ovpns2 192.168.178.0/24 10.0.4.2 UGS ovpns5 192.168.179.0/24 10.0.5.2 UGS ovpns6 zzzzzzzzzzzzzz link#19 UHS pppoe0
Server on Site-B (first post) located at 10.0.0.0/24
machineMX log for incomming smtp connection:
postfix/smtpd[31491]: connect from mail.example.org[10.200.0.2]How to disable NAT to achieve this?:
postfix/smtpd[31491]: connect from mail.example.org[...real_IP...] -
@Bob-Dig said in NAT forwarding into WireGuard Interface as LAN Interface:
Don't NAT, like I said before and don't use haproxy for email.
Ok, but NAT on Site-A WAN interface is necessary for sure.
@viragomann said in NAT forwarding into WireGuard Interface as LAN Interface:
Anyway you would have to obey my suggestions regarding interface assignment and filter rules at B above.
I'm full in trust with you and and it's right in place....
-
@Bronko said in NAT forwarding into WireGuard Interface as LAN Interface:
what I would like to reach?
Still not clear, what this is and what you're doing exactly, even I requested several times. So I'm out here.
-
@viragomann said in NAT forwarding into WireGuard Interface as LAN Interface:
Still not clear, what this is and what you're doing exactly, even I requested several times. So I'm out here.
Oh, I'm sorry... my picture above should it sum up.
Recap: How to log on machineMX real source IP here:postfix/smtpd[31491]: connect from mail.example.org[...real_IP...] -
I have been take some packet sniffs...
With outbound NAT rule @viragomann from above the source IP is replaced by pfsense tun_wg0 at Site-A (10.200.0.2) and machineMX reply is flowing back to Site-A; it works.
Without outbound NAT the real source IP is kept (what I would like to reach) and the machineMX is replying too (sniffed at LAN_SEITE3), but the reply doesn't dive into tun_wg0 back at Site-B, means only the smtp requests from real source IP are sniffed at tun_wg0. No firewall drops in system logs. "Allow any rules" are placed at tunnel and server net (LAN_SEITE3) as required.
How can I find where the smtp replies are dropped? -
@Bronko
You mentioned above, that you run the SMTP traffic over HAproxy at A. Is that still the case??? -
@viragomann
No isn't:@Bronko said in NAT forwarding into WireGuard Interface as LAN Interface:
.... but to use HAProxy as a reverse proxy for the Postfix SMTP server, you need to enable Postscreen in Postfix. This doesn't worked for me at the first run...
SMTP port forwarding for now, and it only works with outbound NAT rule at Site-A... (my last post).
-
Because I'm going off topic here, I'm resuming what is still the problem at a new Topic and it solved there.