DoH redirect to unbound resolver?
-
Hello fellow Netgate community members,
Can you please help?DoH and DoT accomplish the same thing right? Just use of TLS. DoH uses port 443 while DoT use 853. My question is if I want to let the unbound DNS resolver resolve both requests can I? I want to configure DoH over the unbound DNS resolver nust to learn how to it. Do I just add in the loop back to custom options @443 or other items for this? I have root SSL certificates installed. The reference said it needs the libnghttp2 library, is that already installed in PfSense? My goal here is to take my huge squidguard DoH list and redirect it over to the unbound resolver that way when the proxy gets hits on the DoH requests the DoH can run on the firewall It should work right just like Nat? I have a proxy running, all other traffic not resolving to DoH servers should just pass normally. I should see both DoH 443 and 853 DNS info on the Squid proxy and keep doing inspection of bad guy traffic that way. I have noticed no matter what I do for DNS nat and all browsers and even Apple software attempt their DoH to bypass the proxy. Goal here is to redirect requests for some DoH sites right back to unbounds DoH DNS resolver, while still running my 853 and 53 options.
Any thoughts?
DoH can be resolved by unbound resolver see below.
Ref:
Https://blog.nlnetlabs.nl/dns-over-https-in-unbound/ -
@JonathanLee said in DoH redirect to unbound resolver?:
Hello fellow Netgate community members,
Can you please help?DoH and DoT accomplish the same thing right? Just use of TLS. DoH uses port 443 while DoT use 853. My question is if I want to let the unbound DNS resolver resolve both requests can I? I want to configure DoH over the unbound DNS resolver nust to learn how to it. Do I just add in the loop back to custom options @443 or other items for this? I have root SSL certificates installed. The reference said it needs the libnghttp2 library, is that already installed in PfSense? My goal here is to take my huge squidguard DoH list and redirect it over to the unbound resolver that way when the proxy gets hits on the DoH requests the DoH can run on the firewall It should work right just like Nat? I have a proxy running, all other traffic not resolving to DoH servers should just pass normally. I should see both DoH 443 and 853 DNS info on the Squid proxy and keep doing inspection of bad guy traffic that way. I have noticed no matter what I do for DNS nat and all browsers and even Apple software attempt their DoH to bypass the proxy. Goal here is to redirect requests for some DoH sites right back to unbounds DoH DNS resolver, while still running my 853 and 53 options.
Any thoughts?
DoH can be resolved by unbound resolver see below.
Ref:
Https://blog.nlnetlabs.nl/dns-over-https-in-unbound/No, not without some serious complications. DoH and DoT uses sertificate infrastructure to validate you are talking to whom you want to be talking to. So if you do a proxy redirect (or NAT redirect), the clients will no longer see the hostname and public certificate they expect when "calling" upon the DoH/DoT DNS servers.
The only way it perhaps will work is if you have control over the clients and can install your own root CA certificate on them, and then have your proxy do MITM (man in the Middle) and issue a fake certificates based on your own Root CA for the intended DoT/DoH servers. I'm not even sure that will work as Google, Apple and MS might have built in which SPECIFIC CA in their own browser should answer the DoT/DoH sessions - regardless of what you do. -
@keyser sorry I forgot to mention, I have root CA installed on all of them. They are all my hardware. SSL intercept is enabled and in use for the proxy. Not "fake" certificates, it's approved certificates, the public ones end at the firewall, and private certificates are issued use after. That link does it with root CA certificates. I am starting to wonder what other privacy violation fines will be issued once someone figures this out. Last month Google was hit with a 23 million dollar fine for privacy violation with users data, maybe they are back at it with new ways to play hide and seek. It seems like some browsers all the sudden want to avoid the DNS they are set to use with private ca root certificates installed set to trust. Now all the sudden they keep asking for DoH to flat bypass the firewalls security. So DoH SSL intercept may be the next tool for cyber security. It's not fake certificates they are approved certificates don't get me wrong.
The Unbound DoH directions use SSL intercept, I just wonder do I add in the ones I am using already.
-
@JonathanLee Yeah I know fake might be the wrong word - lets call them replacement certificates instead.
But otherwise you are correct. It’s a slippery slide we on to be completely owned by the 5 big IT corps in the world - they have no limits or morale other than $$$.
I would be interested in knowing if you can get it to work. I haven’t tried it myself.
-
@JonathanLee We will know when they are really going all in. That’s when their DoH/DoT servers gets relocated to their primary customer URL (fx. Google.com/gmail.com and microsoft.com/office.com).
That way it gets REALLY hard to filter them out because simple SNI URL bloking or IP address blocking will no longer cut it. -
@keyser Have you seen dns.google yet? I have been seeing all the time as of a couple months ago. I went to Edge because of it. They got to have options for security requirements in Chrome. Firefox you can add all sorts of setting to it. Edge just uses the root CA and works.
dns.google ?? why not use my DNS I have configured on the OS with my root ca?
-
@JonathanLee said in DoH redirect to unbound resolver?:
why not use my DNS I have configured on the OS
Because they know better than you ;) and you should be using their dns - you know to protect your privary <rolleyes>
Many browsers love to default to doh - and you have to jump through hoops to turn it off quite often. I don't have a problem with a browser offering to do doh, but it should be a very explicit opt in, not opt out..
The user should have to on purpose click to use it.. Which is why I block the shit out of it..
-
@johnpoz I also block it I have a huge list in Squidguard as well as a Blacklist provided list. Check it out,

(DoH block list for Squidguard)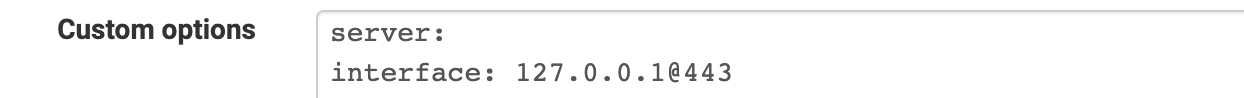
(Using the interface add for DoH for research)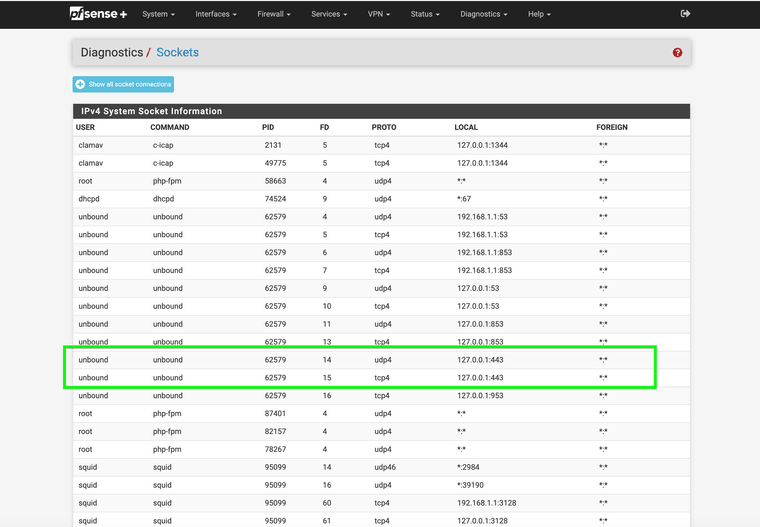
(Unbound to 127.0.0.1 at 443 working)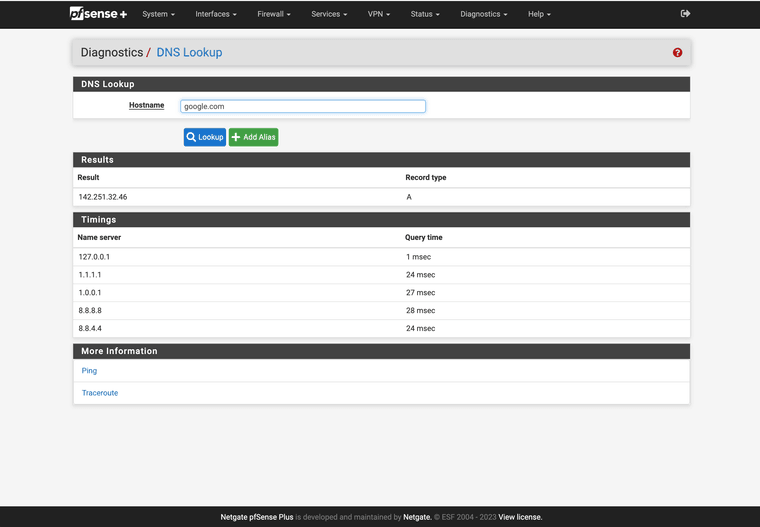
(Fastest resolver now is 127.0.0.1 it seems )Again I wanted to share this too as I am a bit confused here.
( I think I should have some entries as I used dnsfail urls to test yesterday) -
@JonathanLee when your forwarding? Why would stuff be lame? Lame has to do with delegation and is used when you resolve.
You normally even when resolving shouldn't have stuff there.. Other than maybe edns lame..