Windows 11 VPN Connects and pings, but nothing else (web, shares, etc)
-
So I have a strange VPN issue going on that I was just troubleshooting for an hour and basically got nowhere… Client is the built in Windows client. Windows 10 machines work, the one and only Windows 11 box doesn’t.
VPN connects fine, ping, tracert, all that stuff looks great. But web browsing, shared folders, etc., don’t work - all of those requests just timeout. No idea why, or where to even look. I tried flushing dns, uninstalling wan miniport drivers for the vpn connections, added a new vpn connection, all the low hanging fruit basically. It's acting almost as if there is a firewall preventing anything other than ICMP. However, this machine worked fine prior to updating pfSense from v.21 to v.23.05
The only thing that changed was the newest pfSense update disabled an insecure protocol that the vpn was using, so I updated the connection to use a higher level of security, and ran a powershell script on all of the clients to update their existing VPN connection. Not sure if it’s a windows 10 vs 11 issue or not, but all the Windows 10 clients work fine.
Here is a screenshot of the VPN settings:
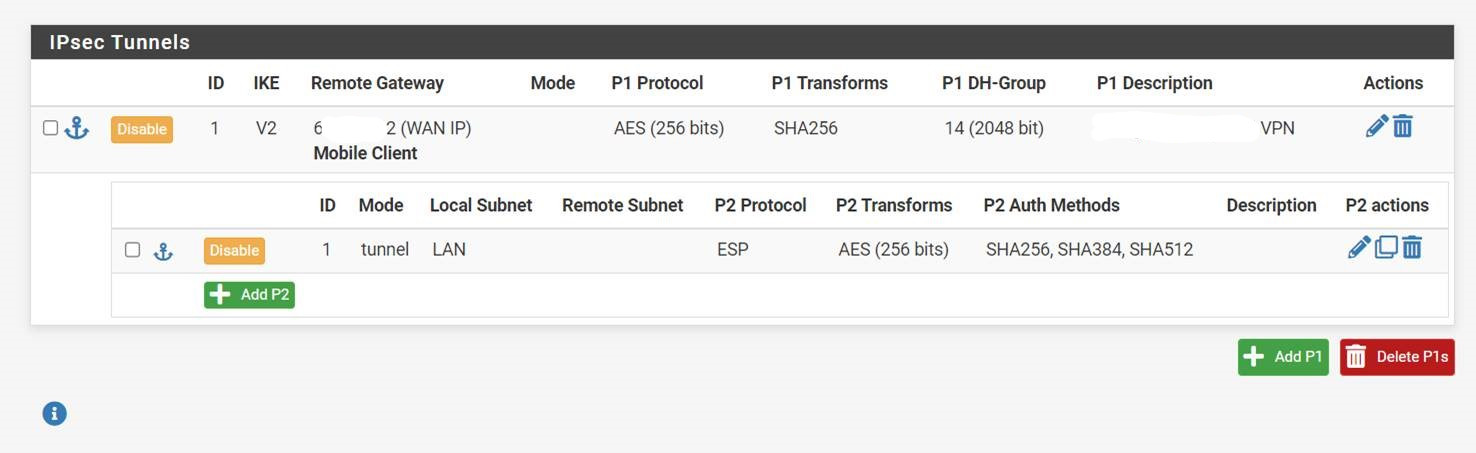
Here is the powershell command I ran on the windows 11 client:
Set-VpnConnectionIPsecConfiguration -ConnectionName $connectionName -AuthenticationTransformConstants SHA256 -CipherTransformConstants AES256 -DHGroup Group14 -EncryptionMethod AES256 -IntegrityCheckMethod SHA256 -PFSgroup PFS2048 -ForceCurious if anyone has experience something like this before, or if I'm just missing a setting somewhere, thank you!
-
@cto_frank No solution from me. But 99% of the issues I've ever had with IPsec I managed no narrow down, work around or even solve by using
- IPsec Log on pfSense (Loglevel Highest) -> Are there errors or events while using 445/tcp instead of ICMP? etc.
- Packet capture on pfSense (Interface IPsec) -> How far do the packets go? Where do they go? etc.
- Last but not least as dumb as it sounds: Check other Logs as well like Firewall, Suricata etc. Especially Suricata can allow one session while blocking a similar.
...and then go from there.
Additional hint from hearsay: Windows and ciphers can be random technology. (At least it feels like it.) Create a dedicated IPsec tunnel for tests and limit it to one set of ciphers (so i.e. only SHA512, not 3 different hashes).
And if I may add a trollish remark: 1 hour of IPsec debugging is no debugging :-P
-
@unico-dm said in Windows 11 VPN Connects and pings, but nothing else (web, shares, etc):
@cto_frank No solution from me. But 99% of the issues I've ever had with IPsec I managed no narrow down, work around or even solve by using
- IPsec Log on pfSense (Loglevel Highest) -> Are there errors or events while using 445/tcp instead of ICMP? etc.
- Packet capture on pfSense (Interface IPsec) -> How far do the packets go? Where do they go? etc.
- Last but not least as dumb as it sounds: Check other Logs as well like Firewall, Suricata etc. Especially Suricata can allow one session while blocking a similar.
...and then go from there.
Additional hint from hearsay: Windows and ciphers can be random technology. (At least it feels like it.) Create a dedicated IPsec tunnel for tests and limit it to one set of ciphers (so i.e. only SHA512, not 3 different hashes).
And if I may add a trollish remark: 1 hour of IPsec debugging is no debugging :-P
LOL - appreciate all of the suggestions, including the troll remark. All of these are good suggestions and I will start with those, thank you for the response.
-
@cto_frank Seems like you're having a DNS issue of some sort. Since you can ping and tracert that's all ICMP but are you pinging an IP address or a FQDN? Try to ping google.com, if it fails, you have yourself a DNS issue.
-
@dmendez I know DNS is always the problem, but don't think it's DNS this time. Pinging a fqdn resolves the correct IP addresses. I can ping the internal servers by their ip as well as hostnames, and they resolve properly.
-
@cto_frank Yeah then it's probably a rule somewhere. I would definitely check the Firewall Logs in real time, as well as packet captures.
-
Just thought I would post a follow up on here...
Taking @unico-dm suggestions, I enabled the highest level of logging for IPsec. I then went to try the connection again and planned to check the logs...but then the VPN connection just started working normally.
So I'm wondering - does changing the log level perhaps restart any services? I didn't change anything else yet as I had planned on checking through logs, but things ended up working. Problem solved, though I'm not exactly sure how / why.
-
@cto_frank Changing the loglevel is only reloading configuration and not restarting services. So it's not rebulding anything but could theoretically correct an unwanted state. But the reason it works could as well be a special alignment of the planets...
 Anyways. Glad it's working
Anyways. Glad it's working 