Possibility to use an internet link from another firewall
-
Hi all.
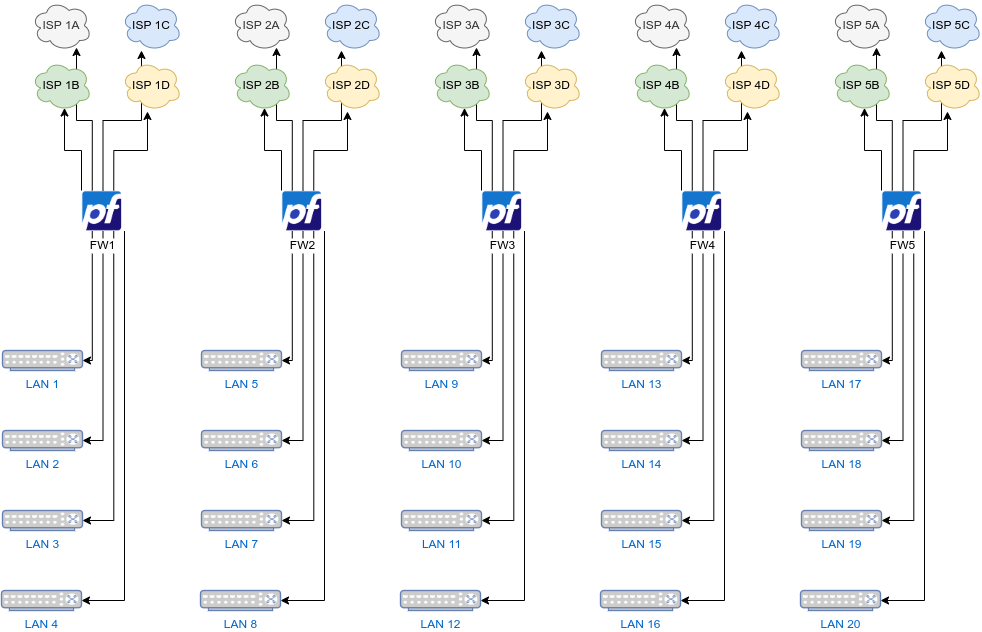
I have 5 pfSENSE virtual appliances, each of which has 8 network ports, 4 LAN and 4 WAN.
It often happens to me that I need to connect to the internet a computer that is, for example on LAN 3 under FW1 and that uses ISP 3C which is under FW3, but as they are on different firewalls it is not possible for me.
Would you please tell me what options I have to achieve this in this scenario? I mean, using an internet link from another firewall for a computer that is not in a LAN connected to this one. Attached is an image of the example I am giving.Thank you very much for any help you can give me.
RegardsGabriel
-
@_neok
Basically not clear, what's the goal of your intention.I assume the LAN3 under FW1 is not the same as the LAN3 under FW3?
-
@viragomann Exactly.
Sorry if I have not been clear. Each of the LAN (1, 2, 3, 4) under each FW is different from the others. Now I correct the graphic.
-
@_neok
You can direct the the traffic to another firewall via internet, assuming there is no internal connection between them.
But it will take some additional effort, when you want to use another gateway than the default on the remote firewall.E.g. to route from FW1 to FW3, on FW1 add a public IP of FW3 as a gateway. The you can use it for policy routing certain traffic to it.
Also you need to add an outbound NAT rule for the public IP of FW1 to the concerned interface.As mentioned, normally FW3 will route the traffic out to the default gateway. If you want to use another one you need to policy route it as well.
If you want to have whole flexibility to use any gateway dependent on the source IP you would have to add all FW3 IPs as gateway, so can configure it this way:
Traffic from ISP 1A IP is using ISP 3A IP.
Traffic from ISP1B IP is using ISP 3B IP and so on. -
@viragomann
Routing traffic over the Internet is not practical for me. Instead I was thinking as a possibility to free one network port from each of the firewalls and use it to interconnect them with each other. Is this possible? If so, how should I configure the routing between the different firewalls to achieve my goal of going out to the internet over the WAN of one firewall from a LAN of a different firewall?Thanks in avance for any help.
-
@_neok said in Possibility to use an internet link from another firewall:
as a possibility to free one network port from each of the firewalls
Why do you need to free one - if they are virtual? Are these on 5 different hosts?
I am having a hard time coming up with a use for such a setup? Why would you have 4 different ISPs for each firewall - these are the same ISPs with just connections to each firewall? Why do you have 5 firewalls, you could do it all with 1, or for that matter 2 in a HA, etc.
But sure you could create a network where all of these firewalls are connected and route traffic out to the internet using any of the firewalls.
-
@_neok said in Possibility to use an internet link from another firewall:
Routing traffic over the Internet is not practical for me.
Your graphic doesn't show internal connections between the firewalls. So was assuming, they are completely seperated, maybe geographically.
But you can do the same using internal IPs as gateways. There is no big difference apart from the IPs.
-
@johnpoz said in Possibility to use an internet link from another firewall:
@_neok said in Possibility to use an internet link from another firewall:
as a possibility to free one network port from each of the firewalls
Why do you need to free one - if they are virtual? Are these on 5 different hosts?
I am having a hard time coming up with a use for such a setup? Why would you have 4 different ISPs for each firewall - these are the same ISPs with just connections to each firewall? Why do you have 5 firewalls, you could do it all with 1, or for that matter 2 in a HA, etc.
But sure you could create a network where all of these firewalls are connected and route traffic out to the internet using any of the firewalls.
These 5 virtual appliances are on the same physical host (Hyper-V Server 2016), and each of these virtual machines are limited to a maximum of 8 virtual network ports.
In the graphic, ISP1, ISP2, ISP3, ISP4 is only illustrative and refers to different internet providers, in some cases the same provider, in other cases not, but in all cases they are different contracts/subscriptions and the downstream/upstream/latency characteristics are different. All these firewalls serve audio and video streaming traffic with different requirements and SLAs each. As the traffic is sometimes outbound or inbound depending on the stream in question, the different links/providers are to achieve a better cost/benefit ratio.
Unfortunately I do not have the availability to run these firewalls on physical servers to be able to unify all these networks into one or two firewalls.
That is why I am interested in the idea of reorganizing the LANs to free up a port on each firewall and use it to interconnect them with each other.
I understand that for this I should create a common network for all the firewalls, configuring the IP of each port of each firewall within the same subnet. But after that I don't know how to route the traffic of a host from a LAN of one of the firewalls through the WAN of another firewall (here my weak point is the routing).
-
@_neok said in Possibility to use an internet link from another firewall:
But after that I don't know how to route the traffic of a host from a LAN of one of the firewalls through the WAN of another firewall (here my weak point is the routing).
Once you create a transit network.. Routing would be as simple as creating a gateway, and then routes to what networks are available via that gateway.
same physical host (Hyper-V Server 2016)
Hyper-v 2016 limit of interfaces for a VM is 12 I believe, not 8.. Also 2016 is end of life, mainstream supported ended Jan 11, 2022
But those points are not really relative to the question of routing.
For simplicity sake I will show 2.. But this can be expanded by just adding another gateway to another firewall on the same transit network.
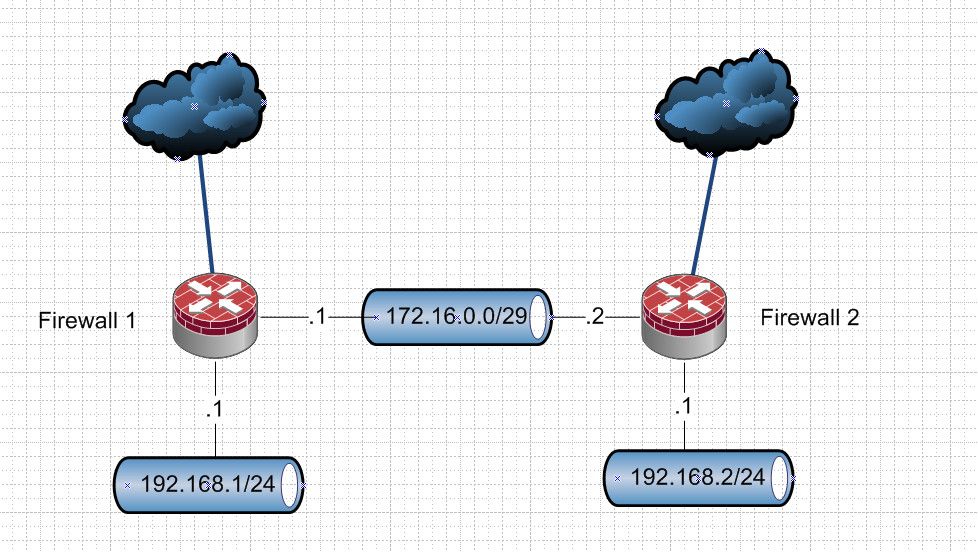
So fw1 you create a gateway to 172.16.0.2, fw2 you would create a gateway to 172.16.0.1
On fw1 create a route to 192.168.2/24 via 172.16.0.2
On fw2 create a route to 192.168.1/24 via 172.16.0.1If you wanted 192.168.1 devices to use fw2 as their internet, you could create a policy route that says for dest X gateway would be 172.16.0.2. Now if this is to some external IP, ie the internet then fw2 would have to be setup via outbound nat to nat this downstream network.. When you create the gateway and route, it should be automatic.. But internet via this fw2 wouldn't work if outbound nat is not there for the 192.168.1 network.
You could get fancy and setup some failover stuff in fw1 that would leverage the gateway to fw2 as its internet if all of its other wan interfaces failed, etc.
You don't have to do the routing to the other fw lans if you don't want to.. And could just policy route internet traffic for say lan on fw1 to use the fw2 gateway via the transit network on fw1. But unless you were outbound natting on this transit network, fw2 would need to know how to get to 192.168.1 via the transit, if you wanted to use fw2 as fw1 lan networks internet access.
-
@_neok said in Possibility to use an internet link from another firewall:
Routing traffic over the Internet is not practical for me
Easy.
Even I get it.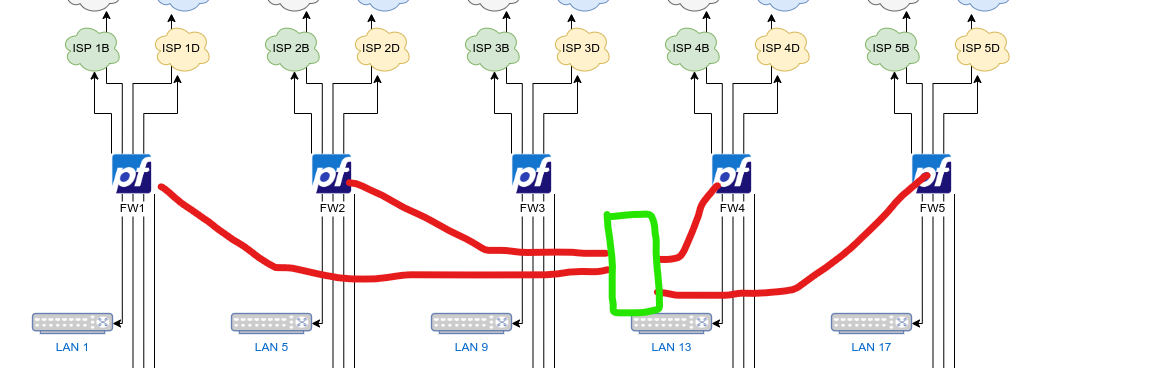
Condition : add on every pfSense a ninth interface.
A 4 port switch (green).
4 red wires.
Nearly done.On FW1, give this 9 interface : 192.168.200.1
On FW2 192.168.200.2
On FW3 192.168.200.3
On FW4 192.168.200.4Add 'the needed' routing info on each FWx
Really done.if FWx are miles away from each other, then another approach is needed :
Throw this idea out of the windows :Routing traffic over the Internet is not practical for me
and use the Internet for whatever VPN plan you chose.( or get some leased lines ( and go broke while doing so))
-
@johnpoz said in Possibility to use an internet link from another firewall:
Hyper-v 2016 limit of interfaces for a VM is 12 I believe, not 8.
8 synthetic and 4 legacy adapters, to be exact. But I don't use legacy adapters because they have very bad performance, they make intensive use of CPU, penalizing latency.
2016 is end of life.
True. When I upgrade to Hyper-V Server 2019 my problems will be over (supports 64 synthetic adapters, now called "Hyper-V specific network adapters").
So fw1 you create a gateway to 172.16.0.2, fw2 you would create a gateway to 172.16.0.1
On fw1 create a route to 192.168.2/24 via 172.16.0.2
On fw2 create a route to 192.168.1/24 via 172.16.0.1If you wanted 192.168.1 devices to use fw2 as their internet, you could create a policy route that says for dest X gateway would be 172.16.0.2. Now if this is to some external IP, ie the internet then fw2 would have to be setup via outbound nat to nat this downstream network.. When you create the gateway and route, it should be automatic.. But internet via this fw2 wouldn't work if outbound nat is not there for the 192.168.1 network.
Excelent. Thank you very much for the detailed explanation. I'm going to set up a lab to do proof of concept testing of all this.
Thank you very much for the directions, they were very helpful.Best regards
-
@Gertjan said in Possibility to use an internet link from another firewall:
Condition : add on every pfSense a ninth interface.
Unfortunately I cannot add more network interfaces as I am limited to a maximum of 8 per VM.