Port forward + Source NAT + IPSec VTI
-
Hello guys! Can I implement next schema:
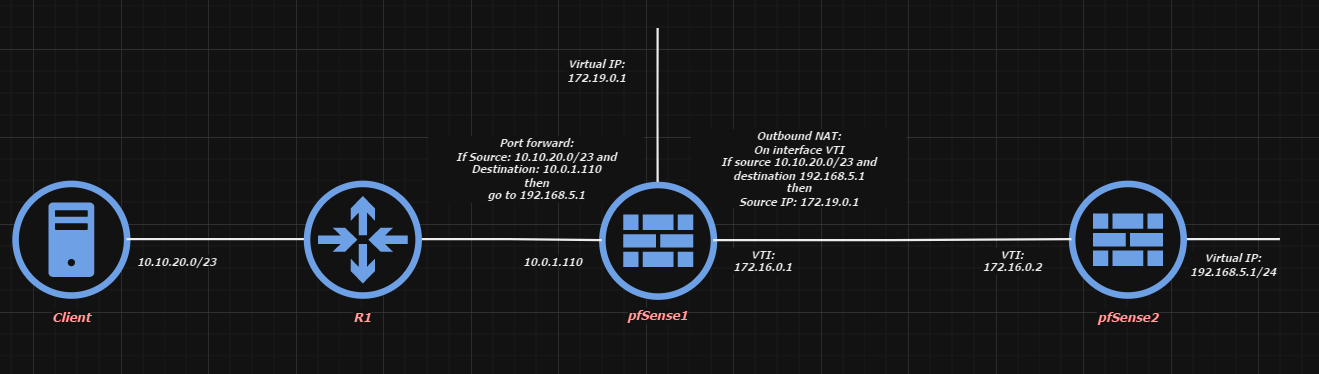
I need to reach 192.168.5.1 from 10.0.10.20.0/23, but mask the ip as 172.19.0.1.
And I can't do anything with R1.
All routes correct.
I'm able to ping 192.168.5.1 from pfSense1.
I see correct packets in VTI on pfSense1 but I can't see them on pfSense2:
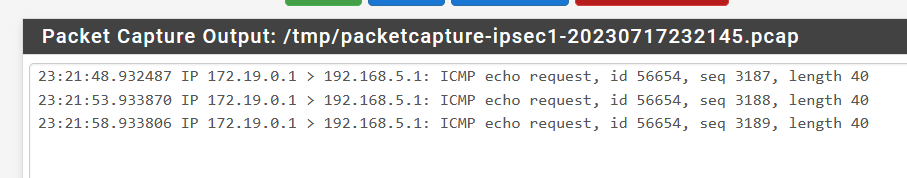
-
It's probably routing through the VIP interface instead of through the VTI
On which interface are you seeing those packets? On the VTI or on the one where you have your VIPs (Guessing its WAN)?
-
@dmendez-netgate hello! Captured from VTI. Actually I did this task by using tunnel mode instead VTI. But it's still interesting why it doesn't work through VTI...
-
@DirectRaw If that packet capture was on the VTI, it means your routes on pfSense1 are correct.
What about pfSense2? Do you have a route to send traffic to destination 172.19.0.1 through the VTI?