AD DS/DNS & pfsense DNS: enable resolution and browsing?
-
I have a 3-site network with S2S IPSec tunnels connecting each to each, as follows:
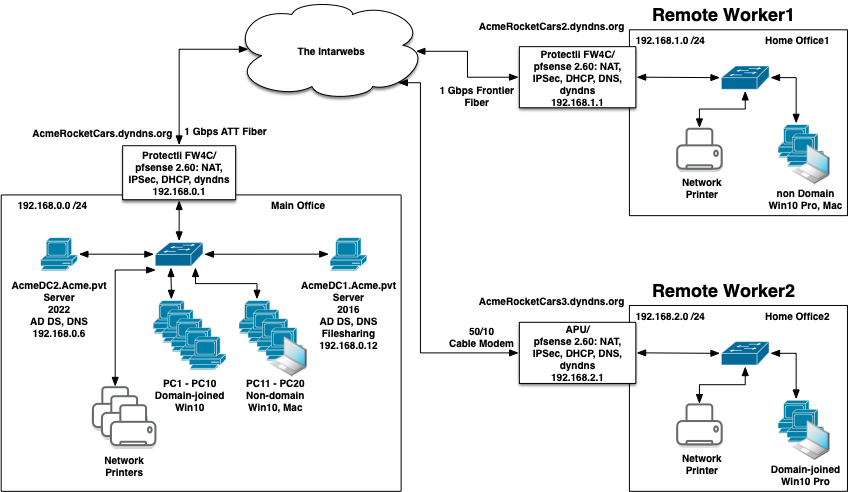
I have Windows Server 2016 and 2022 running AD DS and DNS at the main office, but pfsense doling out DHCP addresses to a mix of domain-joined PCs, non-domain PCs, and my Mac laptop, plus some network printers, IP cameras, etc. Hostname resolution works properly for everyone at the main office, including for my Mac.
I do not have DCs at the other two sites. At Home Office 1 I have pfsense doling out DHCP addresses to a mix of domain-joined PCs, non-domain PCs, and my Mac laptop when I WFH.
At Home Office 2 I have pfsense doling out DHCP addresses to domain-joined PCs and non-domain PCs.
The IPSec tunnels (IPv4*) are working fine for IP connectivity; I can connect from anything to anything by IP address. But hostname resolution from site-to-site is intermittent, and browsing the AD network works only when I'm in the Main Office.
What is the correct way to set up DNS on the DCs and in the 3 pfsense boxes so that hostname resolution always works, and so that AD network browsing would work at both remote sites, for both the domain-joined PCs, the non-domain PCs, and my Mac?
It's much more important to be able to browse from the remote sites to the AD network at the office than the reverse, but the reverse would be nice, too.
I'm sick of hosts files!!!!
Thanks!
-
@TheWaterbug Are you taking advantage of the "Domain Overrides" feature under the DNS Resolver?
The configuration I'm using is to have pfSense pass itself as the DNS server for all DHCP leases in my lab environment, and pass the DCs for production. From there, I used the "Domain Overrides" and set up 4 rules:
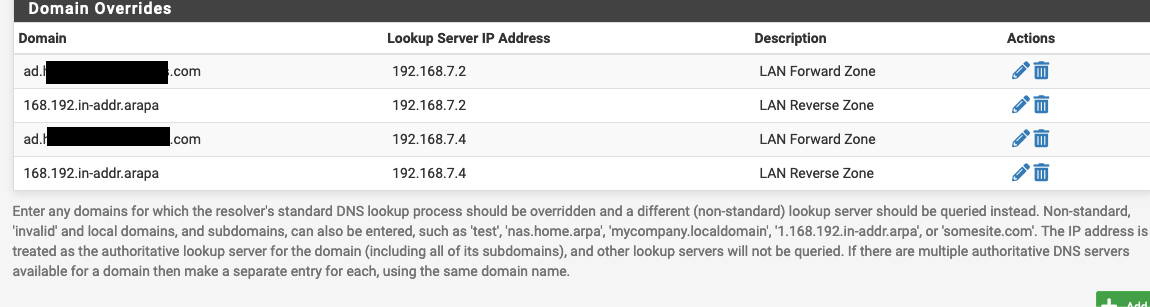
Anytime the pfSense receives a DNS query for a system in the domain (joined or not), it will pass it to the IPs of the two DCs. You'll want that configuration on each of the pfSense firewalls involved in this network.
For the two remote sites, if the IP connectivity over the VPN is working, the DNS request will route over the VPN and hit the DCs at the main office. This setup will help keep DNS queries responsive at the remote sites for all normal browsing, but you'll have a bit of latency for any queries going to the DCs.
For my DCs, I have them configured to use the pfSense as its DNS Forwarder, which allows them to take advantage of the caching capabilities in Unbind (DNS Resolver). Also, for machines in the main office, I would ensure the DHCP server is passing out the IPs of the DCs as the DNS passed to local machines. I do this so I can continue internal LAN operations if the pfSense were to have any problems with the resolver, or to lose internet connectivity.
-
@TheWaterbug said in AD DS/DNS & pfsense DNS: enable resolution and browsing?:
intermittent
What @pokrifchakd said but also be aware Windows does not process DNS servers in order, it remembers the last one that worked and uses that first. So using non-AD or public DNS can cause AD/GPO/login failures, unless it's pfSense and one is using an override.
-
@SteveITS Thanks, I learned something!