PSA - 2.7.0 and ssh keys
-
pfSense 2.7.0 ships with a newer version of sshd, which defaults to not allowing rsa public key logins. RSA was commonly used for public key generation and may be present on legacy systems. One could hack rsa support back in, but the better option seems to be switching to an ed25519 key.
-
Thank you for this! I was beating my head out for several days after upgrading from 2.6. ssh.com warns that ed25519 might not yet be supported by all clients, so I decided to use ecdsa using
ssh-keygen -t ecdsa -b 521copied the new public key into my pfSernse user account, and can report it works fine from my Win11 OpenSSH client.
-
@bumpmark and @dotdash not sure where you got this idea from.. I just fired up a rsa key to test this and working just fine
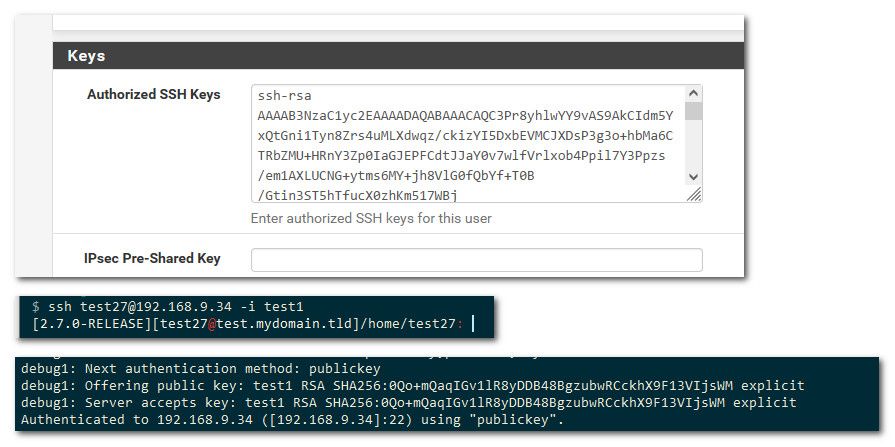
I think what your talking about is that they have deprecation of "ssh-rsa" signature scheme, I believe since version 8.8.. You now need to use rsa-sha2-256 or rsa-sha2-512 signature schemes.
Old ssh was only using SHA-1 hash algorithm in conjunction with the RSA public key algorithm
https://www.openssh.com/txt/release-8.8
Potentially-incompatible changes ================================ This release disables RSA signatures using the SHA-1 hash algorithm by default. This change has been made as the SHA-1 hash algorithm is cryptographically broken, and it is possible to create chosen-prefix hash collisions for <USD$50K [1] For most users, this change should be invisible and there is no need to replace ssh-rsa keys. OpenSSH has supported RFC8332 RSA/SHA-256/512 signatures since release 7.2 and existing ssh-rsa keys will automatically use the stronger algorithm where possible. Incompatibility is more likely when connecting to older SSH implementations that have not been upgraded or have not closely tracked improvements in the SSH protocol. For these cases, it may be necessary to selectively re-enable RSA/SHA1 to allow connection and/or user authentication via the HostkeyAlgorithms and PubkeyAcceptedAlgorithms options. For example, the following stanza in ~/.ssh/config will enable RSA/SHA1 for host and user authentication for a single destination host: Host old-host HostkeyAlgorithms +ssh-rsa PubkeyAcceptedAlgorithms +ssh-rsa We recommend enabling RSA/SHA1 only as a stopgap measure until legacy implementations can be upgraded or reconfigured with another key type (such as ECDSA or Ed25519). [1] "SHA-1 is a Shambles: First Chosen-Prefix Collision on SHA-1 and Application to the PGP Web of Trust" Leurent, G and Peyrin, T -
@johnpoz Thanks for the additional info.
Months ago, when I created the keypair, I just used the default encryption with ssh-keygen. Which worked fine with all my devices.
Just recently I setup a new pfSense box and could not logon if pubkey auth was required. But I could still logon to other systems, verifying the key file hadn't been corrupted, and I could logon to pfSense using password only. I posted about it on Reddit but it seems nobody there had run into the issue.
-
@bumpmark so you used the old keypair you had created from before? Yeah not sure how big of jump they made from say 2.6 to 2.7, but 2.7 is running 9.3 of ssh, so yeah it wouldn't want to use that old sha1 stuff..
what version of openssh were you using.. pretty sure keygen hasn't defaulted to rsa1 in really long time.
-
Yup, I've hit that on a few old installs. Took a while to work out what was happening.

-
@johnpoz Using OpenSSH 8.6p1 from Win11.
It seems that Microsoft has decided Win11 users don't need a later version, and so has not provided updates. I don't see any way to install a newer version without setting up a gcc environment in Windows and building from sources. Which is a PITA. But hey, I'm not doing anything for the next few hours.
-
@stephenw10 Yeah, obviously not pfSense's fault.
But now that its known maybe Netgate can add something to the openssh pages on https://docs.netgate.com/pfsense/en/latest/ to help other users searching for the problem.
-
You can open a report ticket by just clicking the feedback button on the page.
-
@bumpmark said in PSA - 2.7.0 and ssh keys:
It seems that Microsoft has decided Win11 users don't need a later version
Not sure why anyone would limit themselves to what MS puts out - just use the another.. You can grab windows version here
https://www.mls-software.com/opensshd.html
Microsoft Windows [Version 10.0.19045.3570] (c) Microsoft Corporation. All rights reserved. C:\>ssh -V OpenSSH_9.4p1, OpenSSL 1.1.1v 1 Aug 2023 C:\>Or just use your fav client, I use securecrt most of the time, its not a free option. But it is a very robust client.. There is also https://itefix.net/copssh-client which has 9.5p1
C:\tools\copssh_client_7.12.0_x64_free\bin $ ssh -V OpenSSH_9.5p1, LibreSSL 3.7.3Putty is a common fav as well.